Introduction to Note Taking in Cyber Security & Hacking
In the fast-paced world of cybersecurity and ethical hacking, effective note-taking is a crucial yet often overlooked skill. Whether you’re conducting penetration tests, solving Capture the Flag (CTF) challenges, or documenting incident response efforts, organized and comprehensive notes are invaluable. They not only help you stay organized during tasks but also serve as a knowledge base for future projects, exams, and professional growth.

Why Note-Taking is Essential in Cybersecurity
- Retention and Learning
The field of cybersecurity is vast and rapidly evolving. Keeping detailed notes ensures you retain critical information and build a personal library of knowledge to reference later. - Efficient Troubleshooting
During hacking exercises or real-world scenarios, revisiting past notes can provide insights into similar issues, saving time and effort. - Professional Documentation
Comprehensive notes can be transformed into formal reports for clients or stakeholders, particularly during penetration testing or incident response. - Improved Collaboration
Well-structured notes facilitate collaboration among team members, making it easier to share findings and insights. - Preparedness for Certifications
Cybersecurity certifications like OSCP, CEH, or CISSP require thorough preparation. Detailed notes on tools, commands, and methodologies can streamline the study process.
What to Document in Cybersecurity and Hacking
When taking notes, focus on capturing the following key elements:
1. Enumeration and Reconnaissance
- Tools and commands used (e.g.,
nmap,dirb,nikto). - Details of discovered ports, services, and versions.
- Vulnerabilities identified during the process.
- Screenshots of outputs for reference.
2. Exploitation Techniques
- Exploits used, including references to CVEs or exploit databases.
- Payloads created (e.g., Metasploit modules or custom scripts).
- Proof of concept (PoC) examples and how they were executed.
3. Privilege Escalation
- Misconfigurations or vulnerabilities exploited for escalation.
- Tools like
linPEASorwinPEASand their outputs. - Commands and techniques (e.g., abusing SUID binaries or kernel exploits).
4. Commands and Syntax
- Commonly used commands for tools like
Burp Suite,Wireshark, andMetasploit. - Syntax for scripting languages (e.g., Python, Bash, or PowerShell).
- Custom scripts and how they were used.
5. Observations and Learnings
- Challenges faced and how they were resolved.
- New techniques or tools discovered during the process.
- Lessons learned for future applications.
Tools for Note-Taking in Cybersecurity

The right tools can make a significant difference in the quality and accessibility of your notes. Here are some popular options:
1. Text Editors
- Notepad++: Lightweight and versatile, great for quick notes.
- Vim/Emacs: Popular among Linux users for in-terminal editing.
2. Markdown Editors
- Obsidian: Ideal for creating interlinked, structured notes.
- Typora: A clean and simple markdown editor.
- Joplin: Open-source and feature-rich with cloud sync options.
3. Note-Taking Apps
- OneNote: Excellent for organizing multimedia notes, with hierarchical categorization.
- Evernote: Features tagging and easy search functionality.
- Notion: Combines note-taking, task management, and collaboration.
4. Pentesting-Specific Tools
- CherryTree: A hierarchical note-taking app designed with pentesters in mind.
- KeepNote: Lightweight and ideal for documenting CTFs or pen tests.
5. Cloud-Based Tools
- Google Docs: Great for collaborative note-taking and access across devices.
- HackMD: Specifically designed for collaborative markdown notes.
6. Code Repositories
- GitHub/GitLab: Store scripts and note files for future reference.
- Gist: Share and organize code snippets.
The Complete Cyber Security Study Notes & Certifications Study Guides
For all the busy fellas outthere who don’t have time to build and take notes, I offer my study notes to be accessed online and on-demand for those who want to save their time and have a single reference for all subjects not only in cyber security and hacking but also in other subjects.

Components of The Full Notes System
- Cybersecurity & Penetration Testing Field Notes
- Certification notes such as COMPTIA Pentest+ & OSCP.
- Digital Marketing, SEO & Ads.
- Data Analytics
- IT & System Administration
- Book Summaries
What Are The Subjects Covered in Each Category of The Notes System?
CyberSecurity Subjects Covered:
- Red Team: web application penetration testing notes, Buffer overflow binary exploitation notes, Windows active directory penetration testing, Windows and Linux privilege escalation and more.
- Blue Team: Notes in using Splunk SIEM, Snort IDS, SOC analyst notes, secure coding, incident response and more.
Digital Marketing Subjects Covered:
- SEO
- PPC
- Social Media Advertising
IT & System Administration Subjects Covered:
- Windows Management
- Linux Management
- Web: Database and WordPress
- Troubleshooting technical errors
Data Analytics Subjectes Covered:
- Data analytics with Python
- Data analytics with Excel
- Data analytics with IBM and Google products.
Accessing the cybersecurity notes catalog
After subscribing, you will get access to an online portal ( you will be given a password) that houses and stores all the notes. Some notes are stored as PDF files in Google drive. You can also find the links of these notes in the portal.
Below is a quick look on the portal
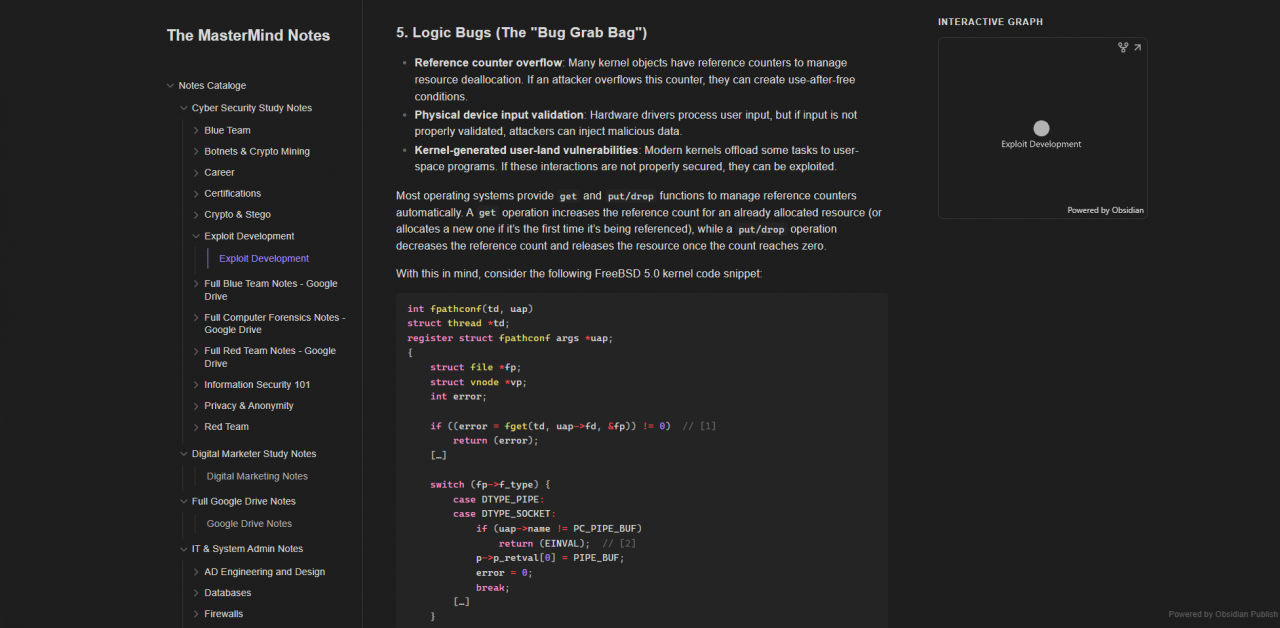
How To Get Access To The Cyber Security Notes?
Since the notes system is diverse and covers many subject including Cybersecurity, we created two ways to offer access to the notes
- Subscription based (10$/mo) : in this option, you can get access to all the notes classified under all subjects. You will have the portal password in addition to access to the Google drive library. You can subscribe through a YouTube membership by clicking on JOIN and selecting “cyber security notes” or through buymeacoffee membership.
See below for a brief comparison:
Subscription-Based
- Regular content updates delivered through newsletters.
- Access to all the categories and over 3K Pages.
One-Time Purchase
- No subscription fees.
- Accessing/Downloading only the purchased E-book.
- No regular content updates.
Benefits of this subscription-based
- Full access to all the
cybersecurity, IT and digital marketingnotes. - Full access to
book summariesin different fields. - The ability to access and use the notes on this portal whenever you want.
- You will receive regular updates on the notes which include new contents and new subjects covered.
- Low price, only 10$/mo.
Things to pay attention to
- The password of this portal changes one time a month. You will receive the new passwords in the newsletter updates monthly delivered to your email.
- Some Notes in Google drive are in read-only mode, to download them completely, you can purchase them individually for a special discounted price for members from the store page
FAQ
What is the Cyber Security Study Notes Guide?
The Cyber Security Field Study Notes PDF is a comprehensive guide designed to assist cybersecurity professionals and students in their studies. It encompasses detailed notes on various tools, commands, and methodologies pertinent to the cybersecurity field.
Who is the author?
The guide is authored by Motasem Hamdan, a cybersecurity content creator known for producing practical notes, tutorials, and courses on penetration testing, ethical hacking, and digital forensics.
- I am interested only in a subset of these notes, how can I get them for a one-time payment?
Please view the available notes that can be downloaded and bought for a one-time payment from this link
- How often do you update the notes with new contents?
Notes are updated at least one-time a week with new contents. Updates are delivered through either the online portal or through Google Drive and they are announced through the community tab of the Youtube channel if you are a subscribed member to the channel membership and through an email newsletter sent to all subscribers.
I don’t want to pay monthly subscriptions, what should I do?
I hate subscriptions but if you want a one-time payment, you can explore from the available notes from the below link:
https://buymeacoffee.com/notescatalog/extrasWhy some of the PDF notes can’t be downloaded?
Some PDF notes can’t be downloaded because they contain copyrights therefore they are available to be viewed ONLINE only.
If you want to purchase a specific study notes book, you can do so from the below link:
https://buymeacoffee.com/notescatalog/extrasIs there a refund policy?
The product is not eligible for a refund. If you have concerns regarding the product, you can contact the author at consultation@motasem-notes.net to discuss your issue.


