What is OSCP?
From Wikipedia:
Offensive Security Certified Professional (OSCP, also known as OffSec Certified Professional) is an ethical hacking certification offered by Offensive Security (or OffSec) that teaches penetration testing methodologies and the use of the tools included with the Kali Linux distribution (successor of BackTrack).
What is the OSCP+ Exam?
The OSCP+ is a penetration testing certification that requires candidates to exploit a network of vulnerable machines within 24 hours. The exam includes:
- Three Standalone Machines (Windows/Linux)
- Three Active Directory (AD) Machines (including a domain controller)
Candidates must collect flags from these machines to earn at least 70 points to pass.
Why is the OSCP+ Considered Difficult?
1. Enumeration Challenges
- Discovering vulnerabilities efficiently is one of the toughest aspects.
- Many candidates struggle due to a lack of a structured methodology.
2. Exam Settings
- The 24-hour format is mentally and physically demanding.
- Many candidates do not manage their time efficiently, leading to exhaustion.
Is it possible to self-study for OSCP+certification and sit for the OSCP exam?
Yes, it is possible to self-study for the Offensive Security Certified Professional (OSCP) certification and sit for the exam without enrolling in the official PEN-200 course. As of November 1, 2024, Offensive Security allows candidates to purchase a standalone exam attempt for $1,699.
However, the OSCP is significantly more challenging than certifications like CompTIA A+ or Security+. Many in the cybersecurity community recommend thorough preparation through various resources before attempting the exam. Engaging with platforms like Hack The Box (HTB) and TryHackMe can provide practical experience. Additionally, courses such as the Certified Penetration Testing Specialist (CPTS) offered by HTB are considered by some to be more comprehensive and cost-effective.
It’s important to assess your current skill level and ensure you have a solid understanding of penetration testing methodologies, networking, and system administration before attempting the OSCP exam. Utilizing a combination of study guides, practical labs, and community resources can enhance your chances of success.
How to Prepare for the OSCP+ Exam
Understand the OSCP Exam Format and Requirements
Take a look here at the exam changes implemented in 2024.
Before you start preparing, familiarize yourself with the exam structure:
- Duration: 24 hours (plus an additional 24 hours to submit the report).
- Exam Structure:
- You are provided access to a virtual network with several machines that need to be compromised.
- Machines vary in difficulty and points, and you need 70 out of 100 points to pass.
- Scoring:
- 3 stand-alone machines (60 points in total)
- 20 points per machine
- 10 points for initial access
- 10 points for privilege escalation
- 20 points per machine
- 1 Active Directory (AD) set containing 3 machines (40 points in total)
- For the Active Directory exam set, learners will be provided with a username and password, simulating a breach scenario.
- 10 points for machine #1
- 10 points for machine #2
- 20 points for machine #3
- Possible scenarios to pass the exam (70/100 to pass)
- 40 points AD + 3 local.txt flags (70 points)
- 40 points AD + 2 local.txt flags + 1 proof.txt flag (70 points)
- 20 points AD + 3 local.txt flags + 2 proof.txt flag (70 points)
- 10 points AD + 3 fully completed stand-alone machines (70 points)
- Report Submission: You must submit a penetration testing report within 24 hours after the exam. The report must contain:
- Steps taken to exploit the machines.
- Screenshots as evidence of each step.
Create a Study Plan
The OSCP exam requires focused preparation, so create a structured study plan.
- Timeframe: Most candidates take 3 to 6 months to prepare thoroughly, though this depends on prior experience.
- Daily Commitment: Allocate at least 2-4 hours a day for studying, practicing, and working on labs.
- Weekend Focus: Dedicate weekends or longer study sessions to more in-depth penetration tests or practice exams, which simulate the actual OSCP environment.
OSCP Exam Day Strategy
1. Plan Your Schedule
- Start the exam early (around 9 AM).
- Allocate specific time slots for each machine.
- Take breaks every 2 hours (walk, eat, hydrate).
2. Start with Active Directory
- Completing AD early gives you 40 points.
- You’ll feel more relaxed tackling the Standalone Machines later.
3. Take Good Notes
- Document every step with screenshots and commands.
- Use Obsidian or CherryTree for structured note-taking.
4. Avoid Common Pitfalls
- DO NOT use banned tools (e.g., SQLmap, Nessus, AI chatbots).
- Submit flags properly (via
typeorcatcommands). - Ensure proper report documentation (following OSCP’s format).
The OSCP Study Notes & Guide
This is a 1487 pages of notes that will guide and help you prepare for and pass the OSCP exam.
Table of contents:
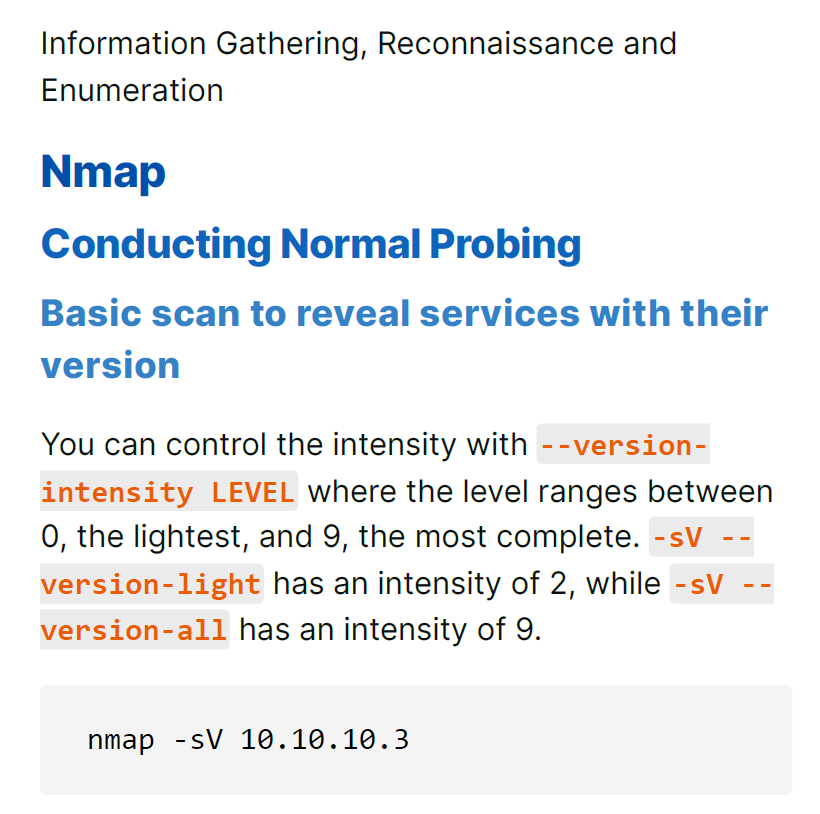
– Information Gathering and Reconnaissance
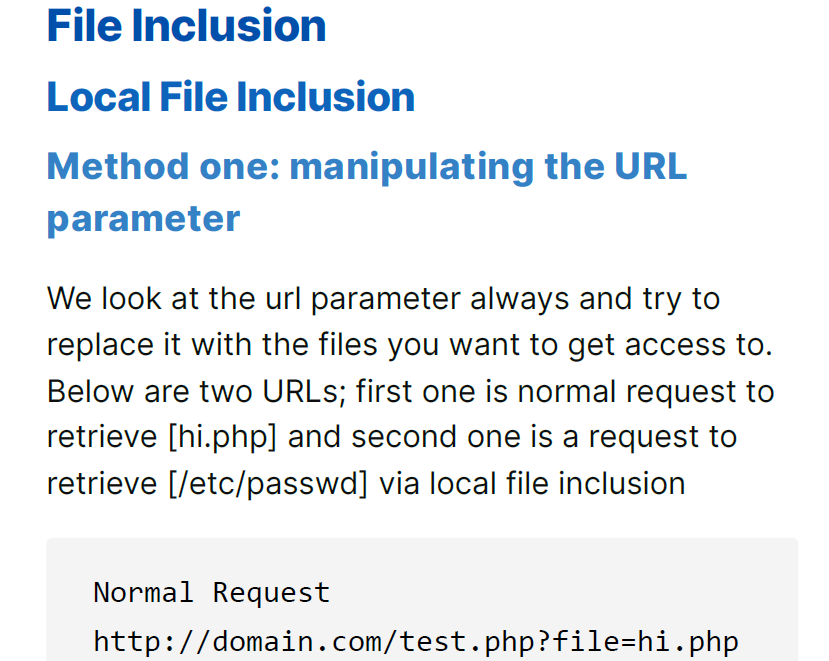
– Network and Web Exploitation
– OS & Application Exploitation
– Databases Exploitation
– AntiVirus & IDS/IPS Evasion
– Password Cracking
– Reverse Shells
– The Metasploit Framework
– Windows Privilege Escalation
– Windows Active Directory Exploitation
– Linux Privilege Escalation
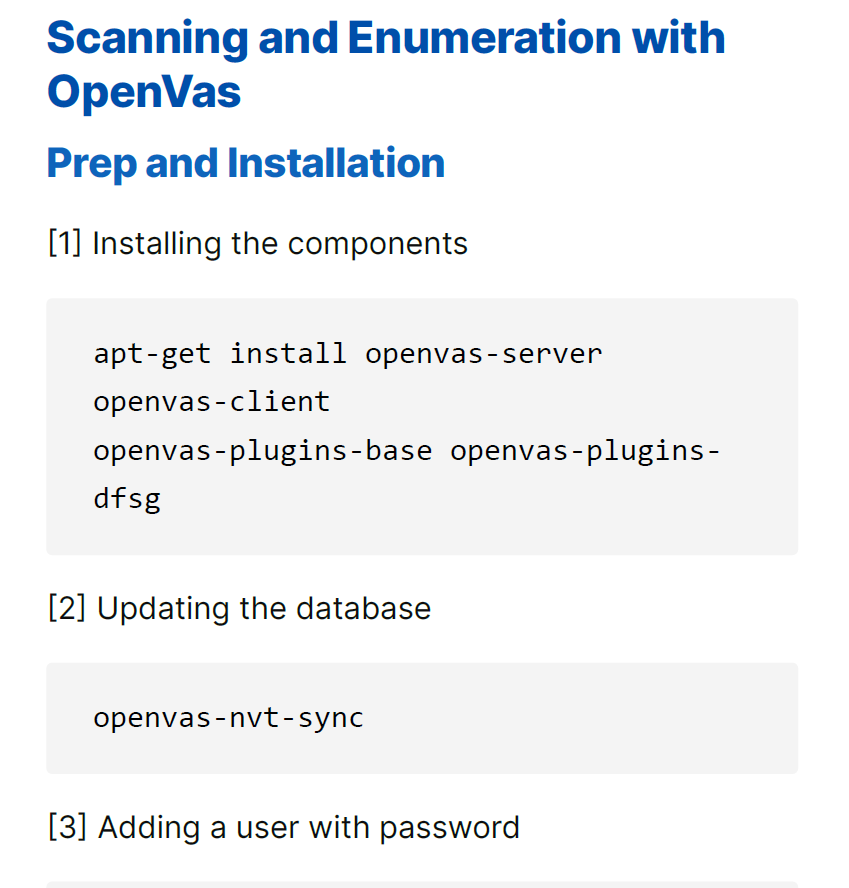
– Supplementary Materials
- Windows System Administration
- Linux System Administration
- Database Administration
- Regular Expressions
Page Count: 1487
Format: PDF
Testimonials (LinkedIn)
How to buy the book?
You can buy the booklet directly by clicking on the button below
After you buy the booklet, you will be able to download the PDF booklet along with the markup files if you want to import them to Obsidian software.
Why will you need a notes system?
You could be actively working as a penetration tester or you could be preparing and studying for a certification exam such as Offensive security certified professional. In both cases, a set of notes maintained in your repository where you can search for commands, concepts or use cases that could aid you in the task you are performing is necessary for a productive studying and/or working.
Who Are These Notes For?
- Cybersecurity students preparing for offensive security certified professional certificate
- Professionals who are actively working in the field and need a set of ready and concise red team and penetration testing notes.
- Savvy learners who want to quickly master penetration testing without having to read hunderds of pages.
What about the notes updates?
if you have been watching my YouTube Channel, you definitely know that those who subscribe to the second tier of my channel membership they instantly get access to a vast catalog of cybersecurity, penetration testing, digital marketing, system administration and data analytics notes catalog for just 10$ along with the ability to receive all notes updates as long as they are subscribed so what does that mean?
This means if you want to stay up to date with the changes and updates to the notes and get access to other categories, I encourage to join the channel membership second tier instead.
However, if you are fine with downloading the current version of this section of the notes then you can buy this booklet instead for a one-time payment.
Will the prices of this booklet change in the future?
Once another version of this booklet is released, which it will, the price will slightly change as the booklet will include more contents, notes and illustrations.
Sharpen Your Hacking Skills
The OSCP tests your practical hacking skills, so focus on building hands-on experience:
Key Skills to Master:
- Linux Basics: You should be very comfortable with Linux commands, file systems, and permission structures.
- Windows Privilege Escalation: Learn techniques to escalate privileges in Windows, including bypassing UAC, exploiting weak services, and abusing misconfigurations.
- Linux Privilege Escalation: Practice finding SUID binaries, misconfigurations, or kernel vulnerabilities to gain root access on Linux systems.
- Active Directory Exploitation: Familiarize yourself with basic Active Directory enumeration and exploitation techniques.
- Scripting: Learn how to automate tasks using Python, Bash, or PowerShell. These skills can help with reconnaissance and exploitation.
Practice with CTF Platforms
- Hack The Box (HTB): Offers a variety of machines with varying difficulty levels. Focus on those tagged with “OSCP-like” to simulate exam conditions.
- VulnHub: Hosts downloadable vulnerable machines that can be set up locally. Many machines are designed to mimic OSCP exam machines.
- TryHackMe: Provides guided walkthroughs and vulnerable machines to practice hacking techniques.
These platforms will help you build your skills and expose you to various real-world vulnerabilities.
Get Comfortable with the Tools
Familiarity with the tools in Kali Linux is essential for passing the OSCP. Here are the most commonly used tools:
- nmap: For port scanning and service discovery.
- netcat (nc): For reverse shells and simple server/client connections.
- Metasploit: While using Metasploit is limited in the exam (you can only use it once), it’s important to know how to exploit vulnerabilities manually.
- Gobuster / Dirbuster: For directory enumeration.
- Burp Suite: For web application attacks and exploiting vulnerabilities like SQL injection.
- John the Ripper / Hashcat: For password cracking.
- Nikto: For basic web vulnerability scanning.
Report Writing
The OSCP report is an essential component of the exam, and good reporting can make or break your result. To ensure you pass:
- Document Everything: During the exam, take screenshots and record every step you take to exploit machines, including commands and output.
- Write Clearly: Make your report concise but detailed. Focus on:
- Steps to compromise the machine: From initial enumeration to privilege escalation.
- Exploits used: Explain the vulnerabilities and provide proof.
- Screenshots: Include screenshots as evidence for each step (e.g., access gained, flags retrieved).
Simulate the Exam Environment
About two weeks before the exam, simulate the exam conditions:
- 24-hour mock exam: Create a mock scenario where you attempt to root multiple machines within 24 hours and write the report within the next 24 hours.
- No external help: Stick to the tools, techniques, and methodology you’ve practiced. Avoid relying on hints, guides, or external assistance.
Time Management During the Exam
On exam day, managing time is critical:
- Start with Enumeration: Begin by scanning the network and enumerating open services for all machines. Use tools like nmap and Gobuster to gather information.
- Prioritize Machines: Go after machines that you find easier first. Don’t get stuck on any one machine for too long.
- Break the Exam into Chunks: Allocate specific times to work on each machine, and take breaks to avoid burnout.
Post-OSCP+ Career Path
Passing the OSCP+ is a huge achievement, but your cybersecurity journey doesn’t stop there:
- Work on soft skills (communication, report writing).
- Gain real-world experience via internships or CTF competitions.
- Consider specializing in Web/App security, Cloud security, or Red Teaming.
Conclusion
Succeeding in the OSCP+ exam requires technical skills, a structured plan, and perseverance. By mastering enumeration, privilege escalation, and exam strategy, you significantly increase your chances of passing.
If you fail, learn from your mistakes and try again—OSCP+ is a milestone, not the final destination in your cybersecurity career.

