Overview of Mamona Ransomware
The Mamona ransomware, dubbed “silent ransomware,” distinguishes itself by not establishing any communication with Command and Control (C2) servers after infection. Unlike conventional ransomware which exchanges data with attacker-controlled servers, Mamuna focuses solely on local encryption and ransom note deployment, streamlining its operations for stealth and simplicity.

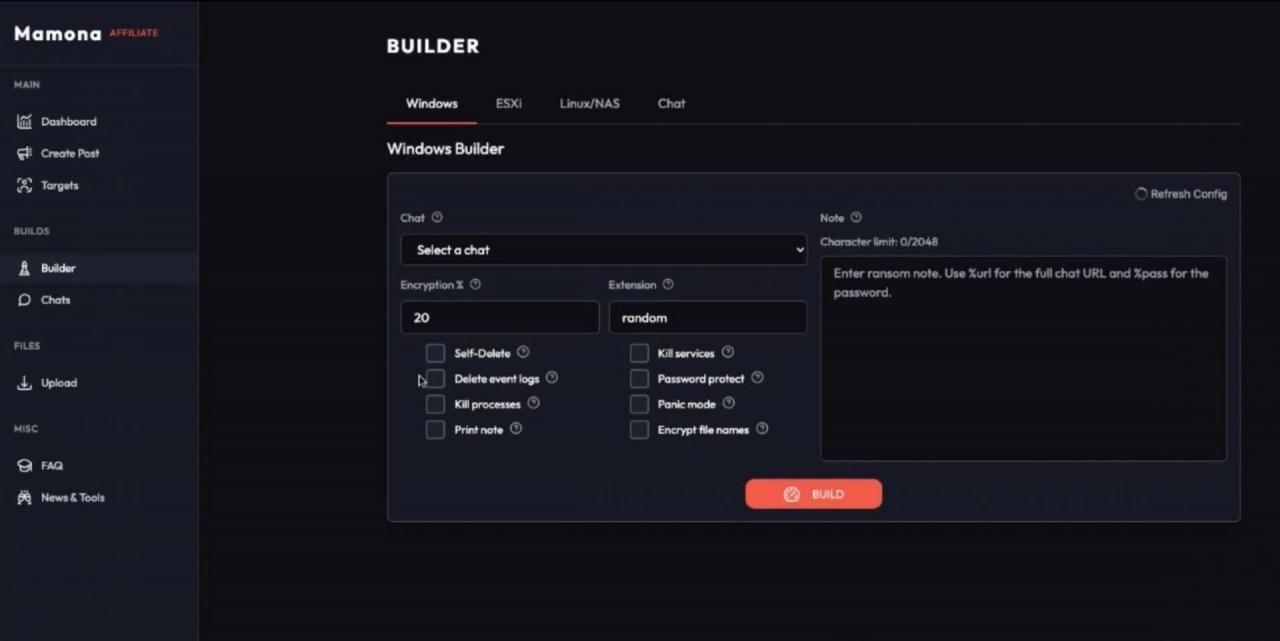
Builder Interface for Attack Customization
Mamona’s user-friendly builder interface, available on the dark web, enables even non-technical individuals to create and deploy ransomware attacks. Users can select target operating systems (Windows or Linux), configure post-infection behaviors like self-deletion, process termination, and encryption parameters, making it a versatile tool for cybercriminals.
Execution and Immediate Effects
Upon launching the ransomware executable, victims observe an immediate impact: desktop files have their extensions altered to “.HAES”, desktop wallpapers are replaced with ransom messages, and a detailed ransom note is deposited across multiple directories to ensure visibility. The note typically contains threatening language and links to .onion sites for payment and communication.

Simulated Network Activity
Mamuna employs deceptive tactics to mimic network interactions. Instead of genuine external communication, it uses ping commands directed at the loopback IP address 127.0.0.7 to delay execution. This unconventional method bypasses traditional monitoring tools and obfuscates malicious behavior.
View the full analysis below:
Anti-Forensic Techniques
To minimize traces and hinder forensic investigations, Mamuna executes self-deletion routines post-infection. It also manipulates system directories by planting ransom notes in various locations, ensuring that victims notice the attack and prompting ransom payments.
In-Depth Encryption Mechanism Analysis
Using Ghidra for reverse engineering, analysts dissected Mamuna’s encryption routines. The ransomware supports two primary encryption modes: full-drive encryption (panic mode) and selective file encryption (custom path). Operators can decide on these parameters, adding flexibility to attack strategies. The encryption process is managed by specific functions identified in the binary, with variables controlling delay mechanisms and encryption criteria.
How does Ghidra assist in analyzing ransomware?
Ghidra, a free reverse engineering tool developed by the NSA, helps dissect malware by:
- Decompiling binaries into readable code.
- Identifying and analyzing functions like
main,process.directory, andencrypt_files. - Understanding the logic behind file encryption routines, such as XOR encryption used in the sample.
System Reconnaissance Prior to Encryption
Before commencing encryption, Mamuna gathers crucial system information such as supported languages, registry values, and drive types. This reconnaissance phase tailors the ransomware’s behavior to the infected system’s environment, optimizing its impact.

Absence of External Data Exfiltration
Despite claims in the ransom note of stolen data, thorough network analysis revealed no outbound connections or exfiltration attempts. All encryption activities were confined to the local machine, debunking the attackers’ claims and reaffirming Mamuna’s “silent” operation model.
What role does Any.Run play in malware analysis?
Any.Run is an interactive online sandbox that allows for dynamic analysis by:
- Executing malware samples in a controlled environment.
- Observing real-time behaviors, including file system changes and network activities.
- Providing visualizations like process trees and network graphs to understand malware interactions.
Is Linux susceptible to ransomware attacks?
Yes. While Linux is often considered secure, it is not immune to ransomware. The article cites examples like “Linux.Encoder” to illustrate that Linux systems can be targeted, especially if vulnerabilities are present.
Indicators of Compromise and Reporting
The assessment wrapped up by pinpointing several Indicators of Compromise (IOCs), like file hashes and ransom note links. Interestingly, unlike the usual ransomware incidents, there were no harmful domains, IPs, or URLs found. This absence made it much easier to draft up protective strategies and put together clear reports without the usual web-related complications.





