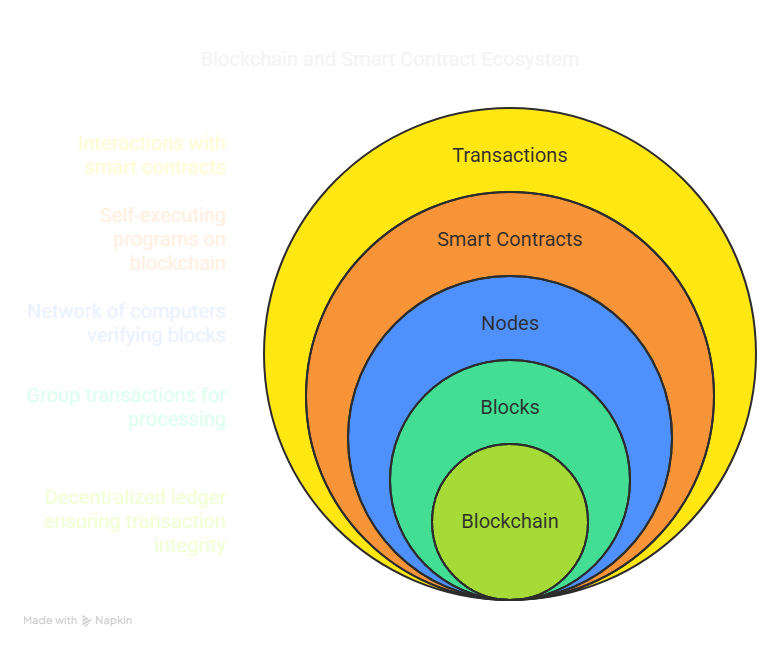
Hacking the blockchain doesn’t follow traditional notions of hacking. Instead, it hinges on manipulating blockchain mechanisms such as smart contracts or computational power. It explains the blockchain as a sequence of blocks containing transactions, which are validated by a decentralized network of computers called nodes.
Smart Contracts in The Blockchain
Smart contracts are self-executing programs on the blockchain that trigger actions when certain conditions are met. These are essential for interacting with the blockchain and are potential vulnerability points if coded poorly.
Ethereum Blockchain and JSON RPC
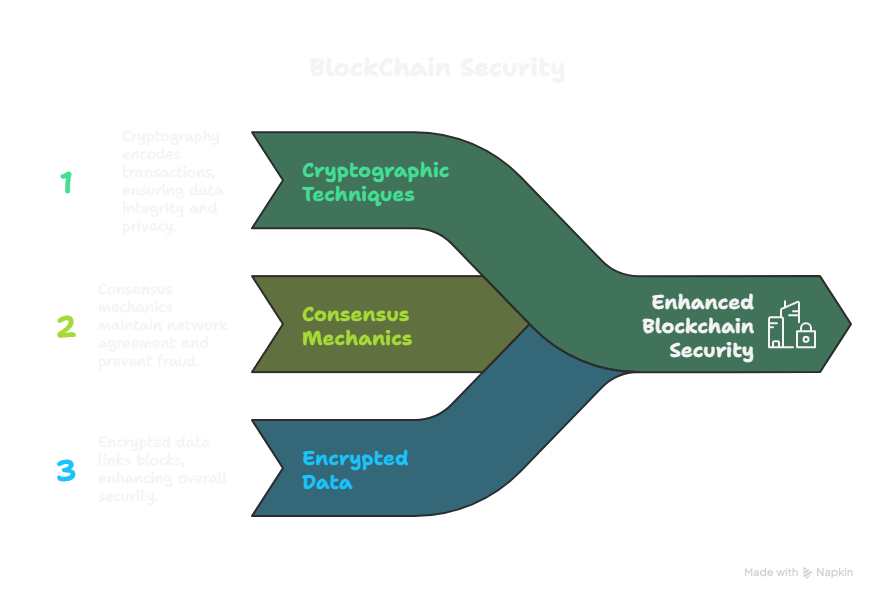
Ethereum is used to explain how JSON RPC is employed for transaction handling. Ethereum listens on port 8545 and processes client requests through cryptographic techniques, which preserve transaction privacy and integrity.
Blockchain Security
Blockchain security depends heavily on consensus mechanisms, ensuring transaction legitimacy. A central concern is the “51% attack,” where a hacker controlling more than 50% of computational power can rewrite parts of the blockchain, reversing or confirming previous transactions fraudulently.
Basic Tools to Interact with The Blockchain
Tools like Cast from the Foundry suitecan be usedfor interacting with Ethereum and don’t forget to learn Solidity, the primary language for writing smart contracts.
Case Study: Chat Application Built on The Blockchain
Practical demonstrations include exploiting a chat application using blockchain as a database. The presenter explores how to retrieve, modify, and analyze smart contracts using browser tools and curl commands.
Contracts like “DB” and “chat” are inspected for vulnerabilities, hardcoded credentials, or logic errors. Even without glaring issues, enumerating and understanding contracts is vital for penetration testing.
Detailed explanation of using various JSON RPC methods such as eth_accounts, eth_getBalance, and eth_getBlockByNumber to interact with and extract data from the Ethereum blockchain.
Using block number manipulation and hex decoding, the presenter extracts readable data like usernames and potential passwords embedded in the blockchain—demonstrating data leakage through inadequate encoding.
By modifying requests using Repeater and analyzing responses, the presenter shows how blockchain communication can be probed for useful data or exploitable behavior.



