Introduction to Certified Red Team Professional (CRTE)
CRTE (Certified Red Team Expert) is a mid-to-advanced level cybersecurity certification offered by Altered Security (formerly Pentester Academy). It is designed to test a candidate’s ability to perform post-exploitation, Active Directory attacks, and lateral movement in multi-domain Windows environments.
CRTE Study Notes
This unofficial guide targets professionals preparing for the CRTE exam, a rigorous red team certification focusing on Active Directory exploitation, post-exploitation tactics, and multi-domain lateral movement in fully patched Windows environments.

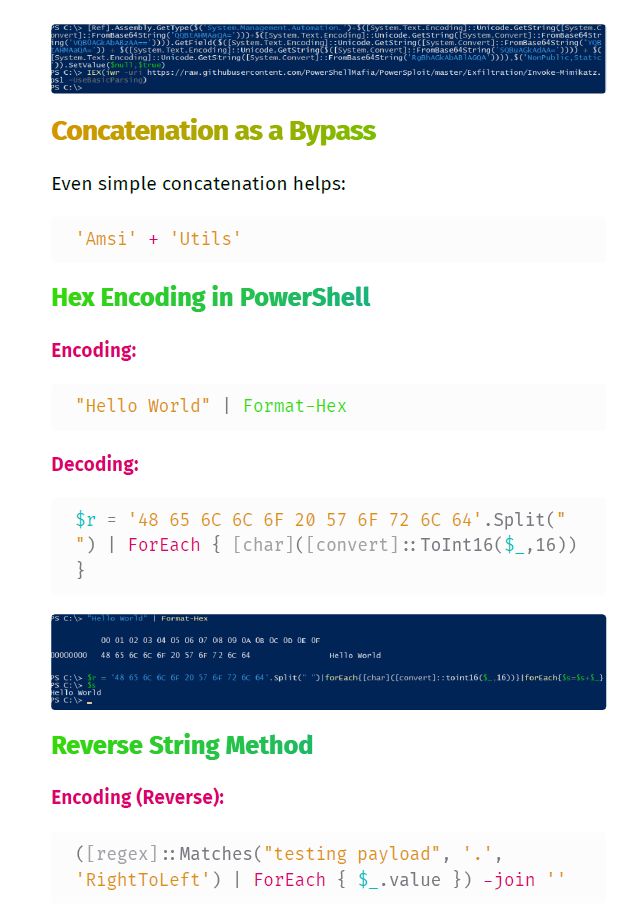


You’ll dive deep into:
- AMSI & ETW bypasses
- PowerShell and AV evasion
- Delegation abuse (constrained, unconstrained, RBCD)
- Cross-forest Kerberoasting
- ADCS exploitation
- gMSA abuse
- SQL Server pivoting with PowerUpSQL
- PAM trust attacks and SIDHistory injection
- Practical Walkthrough(s)
Table of Contents
- About CRTE
- The Exam Format and Reporting Tips
- Using Report Ranger for Markdown Reporting
- Methodology
- Initial Access; Starting Point
- Reconnaissance:
- Local Privilege Escalation
- Enumeration
- Persistence Techniques
- Windows Pentesting
- AD Pentesting
- PowerShell & AV Evasion
- Payload Delivery
- Cross-Forest Attacks
- MSSQL Server Abuse
- Practical Scenarios
- Final Recap & Practice
Page count: 248
Format: PDF
Disclaimer: Unofficial Study Material
This study guide is an unofficial, independently written resource created solely for educational purposes. It is based on personal exam experience and publicly available information. This product is not affiliated with, endorsed by, or authorized by TCM, or any of their partners. It does not contain any copyrighted material, proprietary courseware, or confidential exam content.All trademarks, logos, and brand names are the property of their respective owners.
By purchasing or downloading this material, you agree not to hold the author or this store liable for any outcomes related to exam performance.
For official training material, please visit the certification body’s website.
By Purchasing This Product, You Are Agreeing To The Terms of Service Below
Testimonials (LinkedIn)
How to buy the CRTE Study Notes?
You can buy the book directly by clicking on the button below
After you buy the book, you will be able to download the PDF book.
Who Should Take CRTE?
Red Teamers and Adversary Simulation Professionals
- Looking to simulate real-world attack chains in enterprise environments.
- Want to practice stealthy post-exploitation and lateral movement across domain trusts.
Penetration Testers with AD Experience
- Have taken certifications like CRTP, OSCP, or eCPPT.
- Want to expand into multi-domain Active Directory attacks and evasion tactics.
SOC Analysts and Blue Teamers (Advanced)
- Interested in learning how advanced attackers move inside networks.
- Want hands-on exposure to AMSI/ETW bypasses, Kerberoasting, SID injection, and delegation abuse.
CTF & Lab Enthusiasts
Looking for a structured, practical challenge with a realistic reporting requirement.
Who have completed labs like HackTheBox (HTB) Offshore, TryHackMe, or Pentester Academy’s Red Team Lab (CRTP).
CRTE Prerequisites
Completion of CRTP (Certified Red Team Professional) or equivalent knowledge
Solid understanding of:
- Pass-the-Hash, DCSync, delegation models
- Windows privilege escalation
- PowerView and BloodHound
- Kerberos concepts
CRTE Course Material & Labs
The CRTE labs throw you into a realistic, enterprise-scale war zone with multiple Active Directory domains, cross-forest trusts, and even a taste of Azure AD integration that you’ll not just enumerate but exploit. If you’re looking for practical, hands-on red teaming in a fully patched environment , this is it.
Here’s what the lab structure looks like:
- No shortcuts, no fluff , just pure operational simulation
- Multi-domain, multi-forest topology
- Trust abuse scenarios baked in
- Azure AD hybrid identity paths
The course isn’t a “figure it out yourself” kind of environment. Instead, Nikhil Mittal (yes, the man behind the course) takes you by the hand , guiding you through:
- Initial access and enumeration
- Local privilege escalation techniques
- Domain trust mapping
- Lateral movement and post-exploitation
- Persistence and detection evasion
I personally appreciated the format. It gave me time to absorb the methodology, take meaningful notes, and re-execute each tactic in the lab right after watching it in action.
Here’s a glimpse of what CRTE Course Contents:
- Active Directory (Refresher & Advanced Abuse)
- Offensive PowerShell & .NET Abuse
- Domain Enumeration & Trust Mapping
- Local & Domain Privilege Escalation
- Lateral Movement (WinRS, PS Remoting, etc.)
- Persistence Techniques
- gMSA, LAPS, ADCS Exploitation
- Kerberos Delegation (RBCD, S4U2Proxy)
- Cross-Forest & Inter-Domain Attacks
- Detection Awareness & Defense Bypass
You’ll be actively hunting down over 60 verification flags across a complex AD terrain. These flags confirm your mastery of each step , from local escalation to forest-wide dominance.
And while the occasional typo popped up in a flag description, they were minor and didn’t block progress. The objective was always clear.
If you’ve already crushed CRTP, 60 days of lab time is a solid plan. You’ll need to pace yourself, document aggressively, and practice reporting as you go.
CRTE Exam
Let’s just say , the lab is the warm-up. The exam environment throws you into the deep end with:
- 48 hours of lab access
- 48 hours for report writing
- No flag submission, no proctoring , just exploit, document, and dominate
You’ll need to own 4+ machines and deliver a 40–60 page professional report, complete with screenshots, technical steps, and mitigation strategies, and using something like Report Ranger for reporting.
CRTP Cost
As of the latest information (2025), the Certified Red Team Professional (CRTP) certification from Altered Security is one of the most affordable red team certs.
CRTP Pricing (USD)
| Package | Lab Time | Cost |
|---|---|---|
| Basic | 30 days | $249 |
| Standard | 60 days | $299 |
| Premium | 90 days | $349 |
💡 All packages include:
- Lifetime access to video course + slides
- Access to lab environment
- 1 exam attempt
- Certificate upon passing
📝 Add-ons (Optional)
- Extra Lab Time: You can extend lab access (e.g., 15–30 days) at an additional cost if needed.
- Retake Exam: If you fail, you can purchase an extra exam attempt.
Payment & Access
- Payment is via the Altered Security website.
- Access is typically granted within 24 hours.
- You need to bring your own tools ; Kali or Commando VM recommended.
CRTE Exam Tips & Preparation Strategies
- Report as you go
- Set up your tools ahead of time
- Don’t depend solely on BloodHound
- Take detailed notes
- Enumerate until your fingers bleed
- Pace yourself
- Start with a report skeleton
CRTE Certification Review & Recognition
Unlike theory-heavy or CTF-style exams, CRTE throws you into a fully patched, enterprise-grade multi-domain Active Directory lab , and tells you to go break things… silently, strategically, and surgically.
It’s one of the most realistic simulations of a red team engagement available today. You don’t capture flags , you document post-exploitation chains and deliver a full report, just like you would for a real client.
The CRTE is increasingly being recognized as the go-to certification for post-exploitation and advanced AD attacks. While OSCP is great for initial footholds, CRTE takes you deep into what happens after the breach.
Trusted by:
- Red teamers in enterprise security firms
- Pentesters looking to move beyond OSCP-level attacks
CRTE is often listed as a recommended or preferred cert in red team job descriptions focused on:
- Detection bypass
- Active Directory
- Purple teaming
- Post-exploitation
If you’ve already completed CRTP, and you’re ready to go beyond enumeration into multi-domain AD abuse, Kerberos internals, certificate escalation, and stealthy persistence , CRTE is your next logical step.
CRTP vs CRTE
Certified Red Team Professional (CRTP) vs Certified Red Team Expert (CRTE)
Both from Altered Security , but built for very different stages of your red teaming journey.
| Feature / Area | CRTP | CRTE |
|---|---|---|
| Level | Beginner to Intermediate | Intermediate to Advanced |
| Focus | Active Directory fundamentals & common attack techniques | Advanced post-exploitation in multi-domain AD & forest trust environments |
| Lab Complexity | Single domain, basic misconfigurations | Multi-domain, multi-forest, Azure AD hybrid, full enterprise simulation |
| Tools Used | PowerView, Mimikatz, SharpHound, Rubeus | BloodHound, PowerUpSQL, Certify, SafetyKatz, NetLoader, advanced Rubeus |
| Topics Covered | – Pass-the-Hash – Kerberoasting – ACL abuse – Delegation abuse – Privilege escalation | – Cross-forest Kerberoasting – ADCS exploitation – SIDHistory injection – gMSA & LAPS abuse – PAM trust, RBCD, constrained/unconstrained delegation |
| Exam Format | 24 hours of lab access + 24 hours to submit report | 48 hours of lab access + 48 hours to submit report |
| Tools Provided | None (BYOT – Bring Your Own Toolkit) | None (BYOT) |
| Reporting Requirement | Professional report with steps, screenshots, and recommendations | Deep-dive report with kill chain, diagrams, detailed enumeration & mitigation |
| Cost | ~$249 – $349 depending on lab time (30–90 days) | ~$399 – $599 depending on lab time (30–90 days) |
| Certification Validity | Lifetime | Lifetime |
| Target Audience | Aspiring red teamers, SOC analysts, OSCP holders learning AD | Experienced pentesters, red teamers, and CRTP graduates |
| Prerequisites | None required (but AD basics help) | Recommended: CRTP or equivalent AD attack experience |
Which Should You Choose?
- Start with CRTP if:
- You’re new to Active Directory attacks
- You’re transitioning from OSCP or blue teaming
- You want hands-on experience in a structured AD lab
- Advance to CRTE if:
- You’ve completed CRTP or equivalent
- You want to master forest trust abuse, ADCS, SID injection, and stealthy red teaming
- You’re working toward senior red team or threat emulation roles

