The article discusses a critical vulnerability, identified as CVE-2025-49113, affecting Roundcube webmail, a widely used open-source email client often integrated with hosting providers. This remote code execution (RCE) vulnerability allows an attacker with valid Roundcube login credentials to execute malicious code on the server without user interaction, by exploiting a flaw in how the from property handles user input in the upload.php file.
Specifically, older versions of Roundcube, prior to 1.5.11 and 1.6.11, are susceptible due to a lack of input validation. The solution involves updating to the latest patched versions, which include checks to ensure the from parameter receives a string, thus preventing the injection of harmful payloads. I also demonstrates a proof of concept exploit, illustrating how an attacker can leverage this weakness to gain control over a compromised server.
Finally I provide the answers for TryHackMe Roundcube: CVE-2025-49113 Room.
How does the critical Roundcube webmail vulnerability CVE-2025-49113 impact server security?
The critical Roundcube webmail vulnerability, identified as CVE-2025-49113, significantly impacts server security by allowing attackers to execute malicious code on the server.
Here’s how it impacts server security:
Remote Code Execution (RCE): If an attacker has valid login credentials to Roundcube, they can run malicious code on the server1. This is described as a “big deal” and means that the attacker can achieve remote system command execution.
Server Compromise: An attacker with access to your Roundcube mail can compromise your server. This means they can gain control over the server hosting the webmail service.
Proof of Concept Demonstration: The vulnerability’s impact is demonstrated through a proof of concept that uses a PHP file requiring the target URL, a valid username and password, and a command to execute (such as a reverse shell or bind shell). This allows for the injection and execution of a payload that leverages the vulnerable from property in upload.php.
During a demonstration, after injecting and executing the payload, it was possible to execute system commands on the compromised server, proving valid RCE. For example, commands like id and whoami were successfully run.
The core of this vulnerability lies in the upload.php file, where the from property takes user input (get input string) and processes it via deserialisation without any checks on the supplied input.
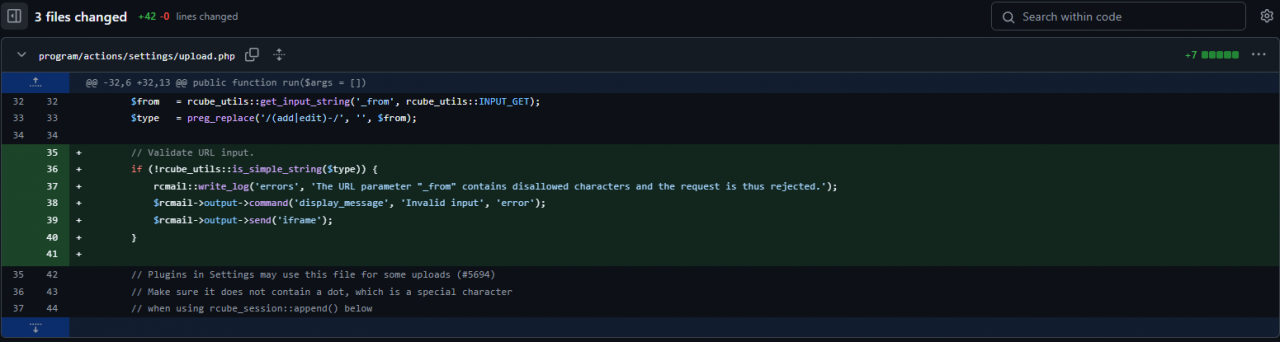
Roundcube expects a string, but without validation, specially crafted payloads can be supplied by an attacker. The fix for this involves adding an if statement to check if the supplied input is a string type; if not, an error is thrown, and the request is rejected.
To mitigate this severe security risk, it is essential to update Roundcube to the newer, patched versions. Specifically, users running versions prior to 1.5.11 and 1.6.11 are vulnerable1. If you are using versions 1.5.10 or 6.10, immediate patching is necessary. If Roundcube is part of your hosting provider’s plan, they are responsible for updating the version immediately.
Which Roundcube versions are vulnerable?
The Roundcube webmail versions that are vulnerable to CVE-2025-49113 are versions prior to 1.5.11 and 1.6.111.
Specifically, this includes:
Version 1.5.101
Version 1.6.101
Version 1.5.91
The vulnerability exists in these earlier versions because the upload.php file, particularly the from property, processes user input via deserialisation without validating whether the supplied input is a string type, as expected by the application.
What does RCE stand for?
RCE stands for Remote Code Execution.
This means that an attacker can run malicious code on the server from a remote location. The vulnerability CVE-2025-49113 in Roundcube allows for remote system command execution if an attacker has valid login credentials to Roundcube.
POC Exploit
A working proof-of-concept (PoC) exploit for CVE-2025-49113 has been released by FearsOff and is available on their GitHub repository.
👉 Quickest way to get started?
Clone the repo using this command in your terminal:
git clone https://github.com/fearsoff-org/CVE-2025-49113
Once cloned, you’ll find a file named CVE-2025-49113.php , this is the actual exploit script.
What Does the Exploit Do?
This PoC script automates the process of executing a payload on a vulnerable Roundcube server. Here’s what it does under the hood:
- Grabs a CSRF token and session cookie.
- Logs into the server using supplied credentials.
- Builds a malicious PHP object using serialization.
- Inserts the object into the
_fromparameter of a request. - Sends a POST request to
upload.phpwith the crafted data. - The server deserializes the malicious input, triggering code execution.
In short, it takes advantage of insecure PHP object handling to run arbitrary code , all through a cleverly crafted POST request.
Running the Exploit PoC
To run the PoC script, you’ll need to pass a few arguments in the following format:
php CVE-2025-49113.php <target_url> <username> <password> <command>
Here’s what each part means:
<target_url>– This is the URL of the vulnerable Roundcube Webmail instance. Replace it with something like:http://MACHINE_IP/roundcube<username>and<password>– These are valid login credentials for the Roundcube instance. You’ll need access to a real account.<command>– This is your payload . the actual command you want to execute on the target server.
Setting Up a Bind Shell
To keep things simple and see if the exploit works, let’s use a bind shell as our payload. Here’s a common example using ncat:
ncat -lvnp 4444 -e /bin/bash
This command opens up a listener on port 4444 and binds it to /bin/bash, allowing us to connect back and interact with the server if the exploit succeeds.
Once you’ve got this running, you can launch the exploit and check if you get a shell , which confirms remote code execution.
How is the vulnerability patched?
The critical Roundcube webmail vulnerability, CVE-2025-49113, is fixed by implementing a validation check on user input to prevent the processing of specially crafted payloads.
The fix involves adding an if statement that checks whether the supplied input is a string type.
If the input is not a string type, the system will throw an error. The error message states, “the URL parameter from contains disallowed characters,” and consequently, the request is rejected.
These crucial lines of code were added as a commit in the newer versions of Roundcube.

TryHackMe Roundcube: CVE-2025-49113
One of the users has the first name of Maggie; what is her last name?
Byte
What is the value of the flag saved in /etc?
THM{ICE_CUBE_DESERIALISATION}




