In this post, we covered the solution walkthroughs for two HackTheBox Sherlock challenges, which are, HackTheBox Campfire-1 and 2. These two challenges showcase how a security analyst can investigate Windows event logs to detect common Active Directory credential attacks such as ASREP Roasting and Kerebroasting by focusing on key event IDs and key attributes.
HackTheBox Campfire 1 Walkthrough
The scenario
Alonzo Spotted Weird files on his computer and informed the newly assembled SOC Team. Assessing the situation it is believed a Kerberoasting attack may have occurred in the network. It is your job to confirm the findings by analyzing the provided evidence. You are provided with: 1- Security Logs from the Domain Controller 2- PowerShell-Operational Logs from the affected workstation 3- Prefetch Files from the affected workstation
Definition of Kerberoasting
Kerberoasting is an attack that targets service accounts in AD to escalate privielges.
Task 1: Analyzing Domain Controller Security Logs, can you confirm the date & time when the kerberoasting activity occurred?
Again when analyzing AD credential attacks, we look into event ID 4769 for a ticket request and event ID 4770 for a ticket renewal. In the case of Kerberoasting, we need to find events where the encryption algorithm used is RC4 or 0x17 in hex.
To get the timestamp, we convert into XML view and look at the value stored under `
Answer: 2024–05–21 03:18:09.
Task2: What is the Service Name that was targeted?
In the same event and using the XML view, we scroll down and locate <EventData> where we can confirm that the attacker used Alonzo’s account to target MSSQLService using 172.17.79.129 as the IP address
Answer: MSSQLService
Task3:It is really important to identify the Workstation from which this activity occurred. What is the IP Address of the workstation?
Answer: 172.17.79.129
Task4:Now that we have identified the workstation, a triage including PowerShell logs and Prefetch files are provided to you for some deeper insights so we can understand how this activity occurred on the endpoint. What is the name of the file used to Enumerate Active directory objects and possibly find Kerberoastable accounts in the network?
Open the Powershell logs and locate the event log whose time is 20-May-24 22:16;32 and open its XML view.
Scroll down until you find <Data Name="Path">...</Data> where you can see that the script used is powerview.ps1 which is part of Powersploit framework.
Answer: powerview
Task5: When was this script executed?
Answer: 2024–05–21 03:16:32
Task 6:What is the full path of the tool used to perform the actual kerberoasting attack?
To parse prefetch files, we can use PECmd tool and convert the prefetch files into a CSV file to extract data.
PEcmd -d prefetch -q --csv /analyst/home/DesktopExecuting the above command creates two files, one of which is PECmd_Output.csv
Openning the CSV file shows as the screenshot below:
Filtering with the path USERS\Alonzo we saw earleir where it stores the powerview script shows us the executable names
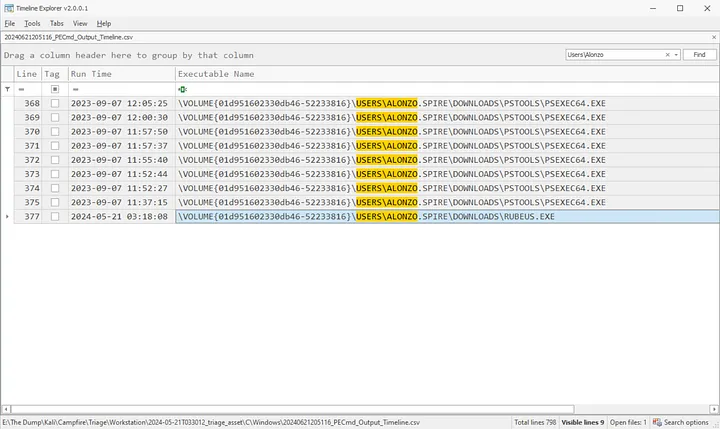
A noteworthy executable is RUBEUS.exe which is a C# toolset for raw Kerberos interaction and abuses. It is heavily adapted from Benjamin Delpy‘s Kekeo project (CC BY-NC-SA 4.0 license) and Vincent LE TOUX‘s MakeMeEnterpriseAdmin project (GPL v3.0 license). Full credit goes to Benjamin and Vincent for working out the hard components of weaponization- without their prior work this project would not exist.
Task 6 Answer: C:\Users\Alonzo.spire\Downloads\Rubeus.exe
Task 7 Answer: 2024–05–21 03:18:08
HackTheBox Campfire 2 Walkthrough
The scenario
Forela’s Network is constantly under attack. The security system raised an alert about an old admin account requesting a ticket from KDC on a domain controller. Inventory shows that this user account is not used as of now so you are tasked to take a look at this. This may be an AsREP roasting attack as anyone can request any user’s ticket which has preauthentication disabled.
What is AS-REP Roasting?
ASREP Roasting is a type of attack that involves an attacker impersonating an authentication request (requesting a ticket for the target user) for a user that has Kerberos pre-authentication feature not enabled or configured. Pre-authentication requires the client to prove its identity before the Kerberos Key Distribution Center will issue a ticket.
ASREP Roasting Impact
When an attacker targets a user whose user properties are not configured with Kerberos pre-authentication, the KDC or key distribution center will respond to the authentication request with the a ticket that is encrypted with the user’s password hash which when acquired by the attacker can lead to hash cracking attacks.
Tasks Answers
Task 1: When did the ASREP Roasting attack occur, and when did the attacker request the Kerberos ticket for the vulnerable user?
To find Kerberos authentication ticket requests, use the event ID 4768. This will filter events to show Kerberos authentication events.
Among the events, when you find one that has pre-authentication type set to 0 and in the task scenario, the event with 5/29/2024 1:36:40 PM timestamp satisfies this criteria.
After the aforementioned event and specifically the one with timestamp 5/29/2024 1:37:49 PM, we can see another Kerberos service ticket request event but this time with happy.qrunwald as the account name which indicates the attacker requesting the ticket for the vulnerable user.
To get the timestamp, we convert into XML view and look at the value stored under <TimeCreated SystemTime=.../>
Answer: 2024-05-29 06:36:40
Task 2: Please confirm the User Account that was targeted by the attacker.
Answer: arthur.kyle
Task 3: What was the SID of the account?
Answer: S-1-5-21-3239415629-1862073780-2394361899-1601
Task 4: It is crucial to identify the compromised user account and the workstation responsible for this attack. Please list the internal IP address of the compromised asset to assist our threat-hunting team.
Answer:172.17.79.129
Task 5: We do not have any artifacts from the source machine yet. Using the same DC Security logs, can you confirm the user account used to perform the ASREP Roasting attack so we can contain the compromised account/s?
Answer: happy.grunwald
HackTheBox Video Walkthroughs




