Google Cyber Security Professional Certificate Review & Study Notes
What is Google Cyber Security Professional Certificate?
If you’re exploring a career in cybersecurity and wondering where to start, the Google Cybersecurity Professional Certificate on Coursera is an excellent launchpad, especially if you’re aiming to become a Cybersecurity Analyst or SOC Analyst. It’s comparable in purpose to the ISC2 Certified in Cybersecurity (CC) credential, but with significantly more hands-on training and practical content.
Who Should Take This Program?
This certificate is perfect for:
- Absolute beginners in IT or cybersecurity
- Career changers looking for real-world, applied skills
- Anyone interested in security operations, automation, and SIEM tools
If you’ve got little to no background in tech, this course holds your hand through the basics and then gradually walks you through industry-grade tools and scenarios.
Google Cyber Security Professional Certificate Study Notes
Google Cyber Security Study Notes is a comprehensive, beginner-friendly guide for anyone entering the world of cybersecurity. Curated by the Masterminds Group and authored by cybersecurity creator Motasem Hamdan, this study guide simplifies complex topics and turns them into actionable, memorable insights.
Whether you’re prepping for certifications like Security+ or CISSP or working toward a SOC analyst role, this book is your fast-track foundation.
Who Is This Book For?
- Security+ & CISSP Seekers
- SOC Analysts & Incident Responders
- Cybersecurity students & IT pros
- Career switchers from IT, marketing, or data
What You’ll Learn
- Cybersecurity explained in human terms (risk, assets, threats)
- Deep dive into Google Chronicle & SIEM dashboards
- Linux & SQL crash courses for analysts
- Python scripts to automate threat detection
- Real-world packet analysis (tcpdump, Wireshark)
- Career tools: interview prep, resume writing, stakeholder communication
Table of Contents
Cybersecurity Foundations
- Risk, Threats, Vulnerabilities
- The CIA Triad
- Frameworks: NIST RMF & CSF
Security Domains & Roles
- CISSP’s 8 Domains
- Analyst Responsibilities
- Ethics & Stakeholders
Incident Response & SIEM
- Incident Lifecycle & Playbooks
- SIEM Tools & Dashboards
- SOAR Automation
Operating Systems & Virtualization
- OS Fundamentals
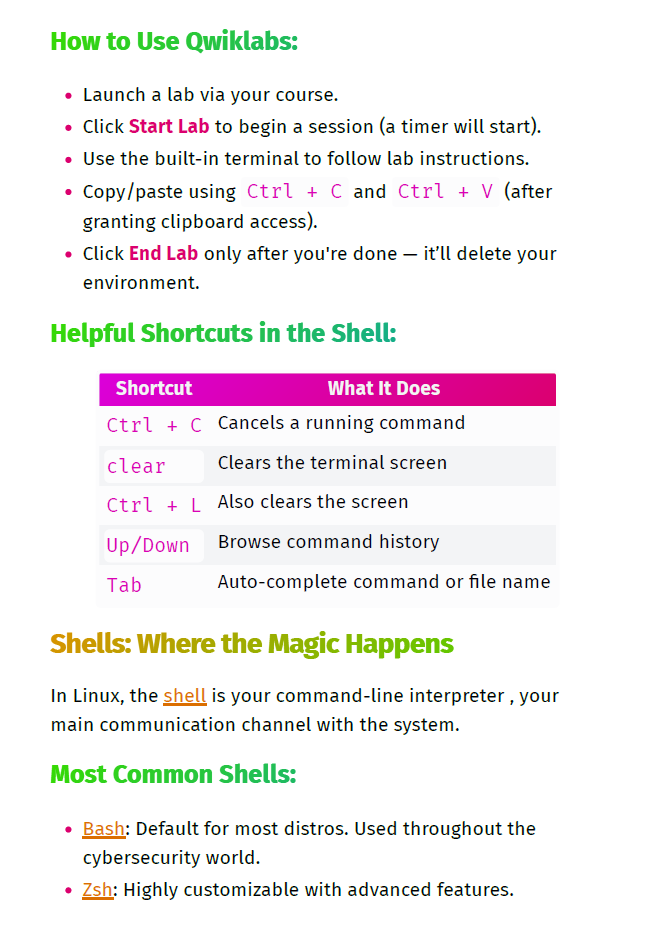
- Linux Architecture & Shell Commands
- Virtual Machines & Hardening
Network Security
- TCP/IP, OSI, Protocols
- Packet Analysis (Wireshark & tcpdump)
- Network Attacks & Defenses
Cloud & Data Security
- Cloud Service Models (SaaS, PaaS, IaaS)
- Shared Responsibility
- Data States & Asset Classification
SQL & Databases for Analysts
- Writing Secure SQL Queries
- Joins, Filtering & Aggregation
- Databases as Cyber Assets
Python for Cybersecurity
- Variables, Functions, Lists
- Log Parsing & Automation
- Regex, File Handling, Debugging
Threats & Attack Techniques
- Malware, Brute Force, Ransomware
- Social Engineering, Phishing Kits
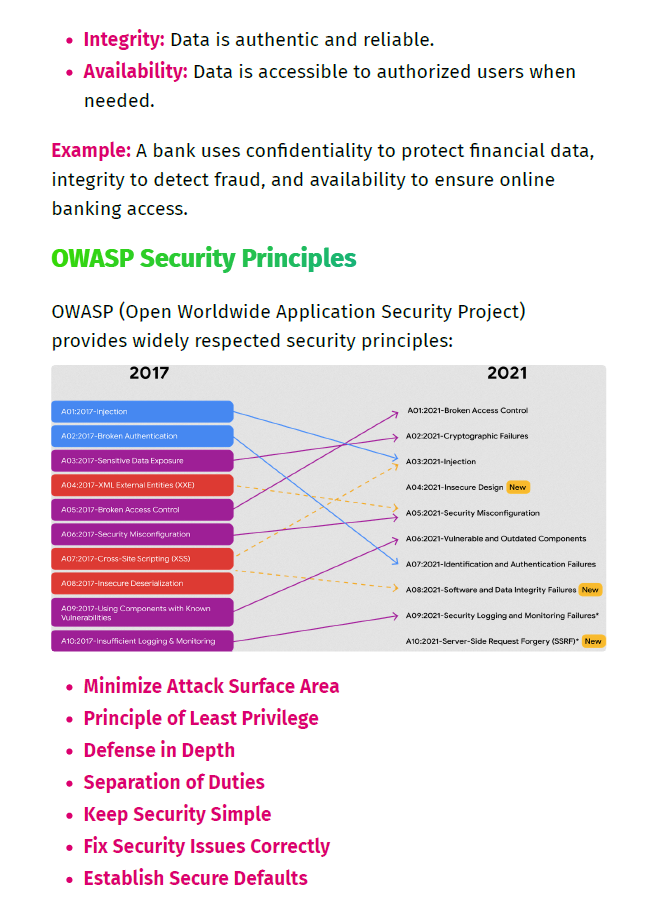
- OWASP Top 10 & CVE Insights
Career Success & Job Prep
- Resume & Cover Letter Templates
- Interview Questions & STAR Method
- Handling Imposter Syndrome
Page Count: 215
Format: PDF


Testimonials (LinkedIn)
How to Get Google Cyber Security Professional Certificate Study Notes?
You can buy the book directly by clicking on the button below
After you buy the booklet, you will be able to download the PDF book.
Course Format & Teaching Style
Each of the eight courses in the program is broken down into short video lessons, knowledge checks, and hands-on exercises. At the end of every course, there’s a final assessment to test retention.
My only critique? The quizzes and final tests were a bit too basic. I would’ve loved more challenging scenarios or even small labs to test applied understanding. But on the upside, the interactive exercises and portfolio activities were excellent and grounded in real-world tools.
Breakdown of the 8 Courses
1. Foundations of Cybersecurity
A gentle but solid introduction to:
- Security incidents and threat types
- The CIA Triad
- Industry standards: NIST, CISSP Domains, and more
- The day-to-day responsibilities of an entry-level analyst
2. Play It Safe: Manage Security Risks
This course deepened the previous one by diving into:
- NIST CSF and Cyber Threat Framework
- OWASP principles
- SIEM tools and SOAR (Security Orchestration, Automation, and Response)
3. Connect and Protect: Networks and Network Security
Covered topics include:
- Network architecture basics
- TCP/IP and OSI models
- DDoS attacks, VPNs, and tcpdump
- Basics of cloud computing and network hardening
Note: If you already hold CompTIA Network+, this course may be too elementary.
4. Tools of the Trade: Linux and SQL
This course:
- Introduced me to useful CLI commands
- Helped demystify the terminal (which I previously found intimidating)
- Gave a helpful primer on SQL and database navigation
You’ll also get hands-on with relational databases, key knowledge for log parsing and threat analysis.
5. Assets, Threats, and Vulnerabilities
This course emphasized:
- Asset classification and sensitivity
- Risk management frameworks
- Common vulnerabilities and exploitation methods
While fundamental, it’s essential knowledge for any security professional.
6. Sound the Alarm: Detection and Response
If you’ve ever wondered how SIEM tools and packet sniffers actually work, this course is for you. You’ll learn:
- How to monitor network traffic
- How to detect anomalies
- Why documentation and calm escalation matter in incident response
And yes, you’ll laugh at the scenario where a teenage hacker demands $1 million in Steam credits, great storytelling meets real risk management.
7. Automate Cybersecurity Tasks with Python
This was easily one of the most practical and rewarding parts of the program:
- Teaches automation using Python (without overwhelming you)
- Focuses on variables, conditionals, loops, and string parsing
- Includes small scripting projects like failed login detection
If you’ve ever wondered how Python fits into security workflows, this course connects the dots.
8. Put It to Work: Prepare for Cybersecurity Jobs
The final module is all about career readiness:
- Resume and cover letter building
- How to communicate security issues with stakeholders
- Preparing for behavioral and technical interviews
- Portfolio projects and mock assessments
Google even includes tips for using the STAR method and navigating remote interviews.
Bonus Perks
30% off the CompTIA Security+ exam upon completion
While not a huge discount, it’s a helpful nudge toward an industry-respected certification.
Time Commitment
Depending on your level, It may take you from 1 – 3 months to complete the entire program, working consistently but not full-time. You could pace yourself faster or slower depending on your schedule.
My Final Verdict about Google Cyber Security Professional Certificate
If you’re still on the fence about this certificate, I absolutely recommend it.
- It builds a strong foundation
- It introduces you to real tools (Linux, Splunk, Python, SQL)
- It aligns well with industry certifications
- And it prepares you to take that crucial first step into the field
Whether you’re aiming for a SOC Analyst role, Incident Responder, or preparing for Security+, this is one of the best value-packed programs for beginners.
Free Blue Team Training
Checkout the playlist below on my YouTube channel for free Blue Team Training