
HackTheBox Insomnia Writeup | Web Hacking CTF Challenges
HackTheBox Insomnia challenge comes with a link to a vulnerable website and its source code. The goal? Gain admin access and capture the flag.
HackTheBox Insomnia Challenge Description
Welcome back to Insomnia Factory, where you might have to work under the enchanting glow of the moon, crafting dreams and weaving sleepless tales.
Logic Flaw Leading to Authentication Bypass
Initial Findings
- A login endpoint was discovered and probed.
- Attempts were made to bypass authentication using:
- SQL injection (
SQLi) - Common auth bypass techniques
❌ These approaches did not succeed.
- SQL injection (
Source Code Review
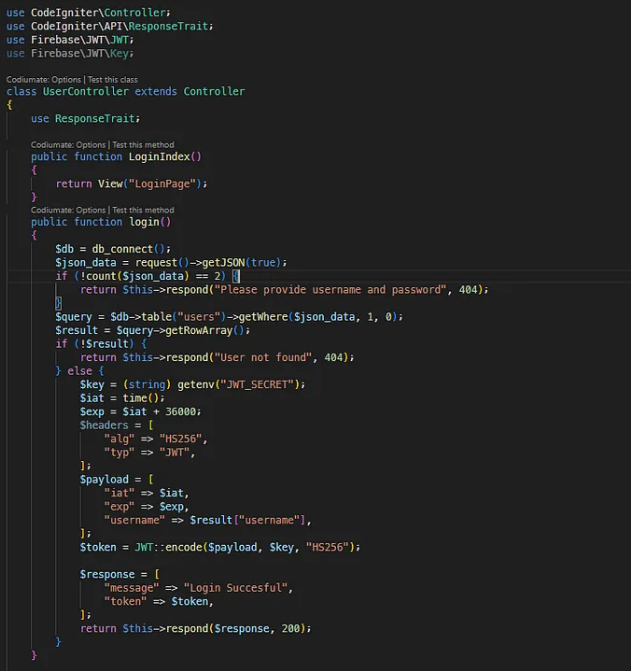
Upon inspecting the backend source, namely ‘Usercontroller.php‘ file , the following login logic was found:
if ($username == "administrator") {
return view("ProfilePage", [
"username" => $username,
"content" => $flag,
]);
} else {
$content = "Haven't seen you for a while";
return view("ProfilePage", [
"username" => $username,
"content" => $content,
]);
}
If a user logs in as "administrator", they receive the flag in the response.
Core Vulnerability: Logic Flaw in Parameter Validation
Code Snippet:
if (!count($json_data) == 2) {
return $this->respond("Please provide username and password", 404);
}
Flawed Logic Breakdown
count($json_data)returns an integer representing the number of keys in the JSON input (e.g.,2ifusernameandpasswordare sent).- The negation operator (
!) is applied before the comparison:
!count($json_data) == 2
- If
count($json_data)is 2:!2becomesfalsefalse == 2returnsfalse— meaning the check fails to trigger even whenusernameorpasswordis missing
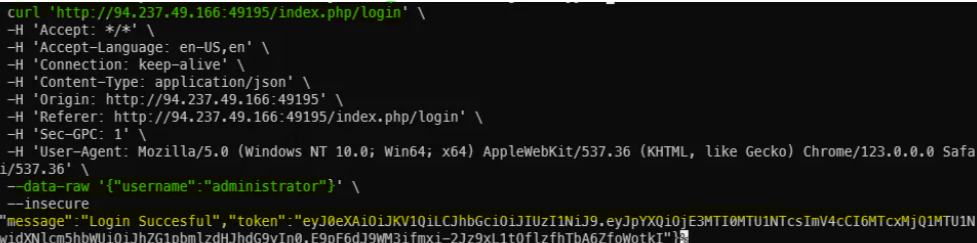
Exploitation Strategy
- Register a new user via the intended flow to understand the JWT issuance format.
- Capture the login request and modify the request body:
- Remove the
passwordfield - Set the
usernameto"administrator"
- Remove the
- The flawed condition (
!count($json_data) == 2) allows the request to pass validation. - The application sees
username == "administrator"and responds with the flag.
Vulnerability Type:
- Logic-based authentication bypass
- Categorized under: Improper Input Validation (CWE-20) and Incorrect Comparison Logic (CWE-697)
Real-World Relevance (2025 Update):
- Similar logic flaws continue to plague insecure APIs, especially in custom-built login endpoints.
- JWT manipulation and logic bugs are increasingly exploited in CTFs and real-world bug bounty programs.
- Secure authentication flows now emphasize:
- Strict input validation
- Use of schema validators (e.g., JSON Schema, Laravel Form Requests, Joi in Node.js)
- Clear control flow logic, avoiding ambiguous comparisons like
!count(...) == ...
Mitigation Strategies
- 🔄 Correct Logic:
Replace the flawed condition with:
if (count($json_data) != 2) {
return $this->respond("Please provide username and password", 404);
}
- Add unit tests for all edge cases in input handling.
- Use robust frameworks or libraries that provide built-in request validation.
- Include static code analysis tools (e.g., SonarQube, PHPStan) in the CI/CD pipeline to catch these mistakes early.


























Post Comment