Introduction to TCM Practical Network Penetration Tester (PNPT)
The Practical Network Penetration Tester™ (PNPT) is not your typical multiple-choice certification. Instead, it’s a hands-on, real-world simulation designed to evaluate your ability to carry out a full-scale network penetration test , just like you would in a professional consulting role.
The PNPT exam doesn’t just test your technical knowledge , it measures your entire workflow, from reconnaissance to exploitation, reporting, and even presentation skills. It’s designed to reflect what employers actually expect from penetration testers in the field.
PNPT Study Notes
TCM Practical Network Penetration Tester (PNPT) Study Notes distils months of hands-on learning, labs, and techniques into a structured, easy-to-follow study guide for the PNPT exam. Written by an ethical hacker who went through the entire journey, this guide offers:
- Real-world attack paths and enumeration tactics
- Active Directory exploitation techniques
- Pivoting, tunneling, and privilege escalation
- Empire, Chisel, Socat, and SSH tricks explained
- Sample enumeration scripts, tips, and command breakdowns
- Clean walkthroughs of boxes like BlackPearl, Butler, and more
- Post-exploitation persistence & cleanup


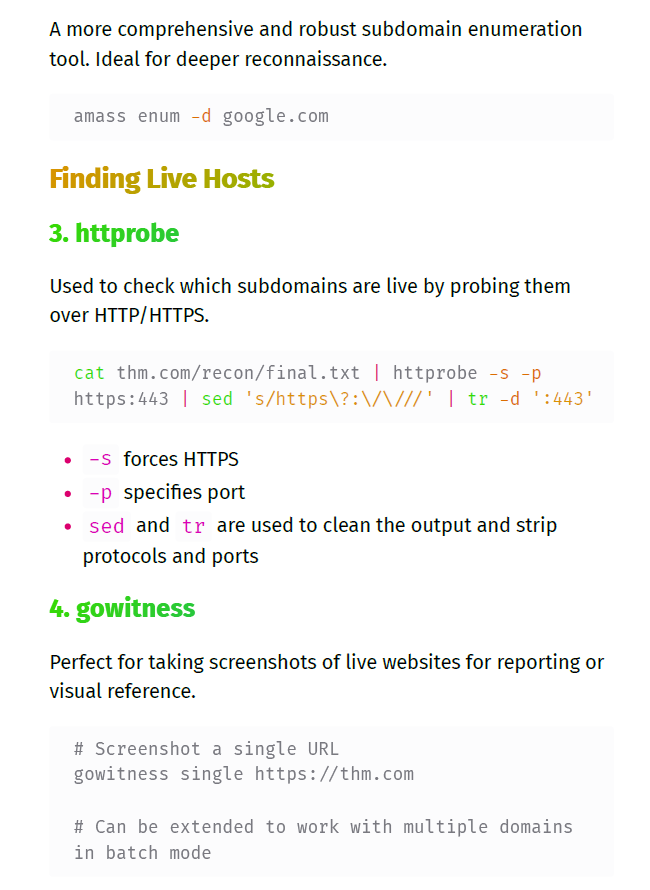
Table of Contents
- PNPT Exam and Tips to Pass
- Networking Basics
- OSI Model
- TCP/IP
- Common Ports & Protocols
- Enumeration Techniques
- System Enumeration
- Network Enumeration
- Automated Tools
- OSINT
- Search Engine OSINT
- Image, Email, Username, Password OSINT
- Social Media and Business OSINT
- Initial Access
- Phishing
- LLMNR & NBT-NS Poisoning
- Responder, BloodHound
- SMB Relays
- Post-Exploitation
- File Transfers
- Maintaining Access
- Privilege Escalation
- Cleanup
- Active Directory Attacks
- Enumeration with PowerView
- Kerberoasting
- Pass-the-Hash
- Token Impersonation
- GPP Exploits
- Mimikatz, BloodHound
- Web Application Attacks
- SQL Injection
- XSS
- File Uploads
- Command Injection
- XXE & Broken Access Control
- Wireless Attacks
- WPA2 PSK Cracking
- Deauth Attacks
- Pivoting & Tunneling
- ProxyChains
- SSH Tunneling
- Chisel, Socat, sshuttle
- Command & Control (C2)
- Powershell Empire
- Listeners, Stagers, Agents
- Reporting Format
- Box Walkthroughs
- BlackPearl
- Butler
Page count: 172
Format: PDF
Note: This product is not eligible for a refund.
If you have concerns regarding the product, kindly contact consultation@motasem-notes.net and clarify your issue and explain why the eligibility for a refund.
Testimonials (LinkedIn)
How to buy the PNPT Study Notes?
You can buy the book directly by clicking on the button below
After you buy the book, you will be able to download the PDF book.
Who Should Take PNPT?
PNPT is Ideal for those seeking practical, real-world pentest experience with strong AD focus. PNPT also puts you in an advantage if you are aiming to gain OSCP later.
PNPT Prerequisites
The official TCM site states that “students without professional hacking experience should begin with the PJPT before attempting the PNPT”
I advise starting with PJPT first because it gives solid hands-on exposure and confidence before tackling the more advanced PNPT .
PNPT Course Material
- Practical Ethical Hacking (25 hours)
- Open-Source Intelligence (OSINT) Fundamentals (9 hours)
- External Pentest Playbook (3.5 hours)
- Linux Privilege Escalation for Beginners (6.5 hours)
- Windows Privilege Escalation for Beginners (7 hours)
Why the PEH Course Is Essential for Passing the PNPT Exam
If you’re aiming to crush the PNPT exam, the Practical Ethical Hacking (PEH) course is your go-to foundation. While the exam does touch on OSINT techniques and external network penetration testing, the real emphasis lies in mastering Active Directory (AD) attacks , from gaining initial access to navigating post-exploitation scenarios.
What makes the PEH course so vital?
- It covers the essentials: You’ll get hands-on practice with core skills like scripting, networking, and system fundamentals , all of which are crucial for both real-world engagements and exam performance.
- You’ll learn web application penetration testing: From SQL injection to file uploads, you’ll build a solid web exploitation toolkit.
- Deep dive into Active Directory: This is where the course truly shines. It walks you through the full AD attack lifecycle , including enumeration, privilege escalation, lateral movement, and persistence techniques.
- Practical approach: The course is designed to simulate real-world environments, helping you build muscle memory for tasks you’ll need to perform during the exam.
Open-Source Intelligence (OSINT) Fundamentals ; 9 Hours
This course introduces you to the world of open-source intelligence gathering , an essential skill in the reconnaissance phase of penetration testing. You’ll learn how to gather, correlate, and analyze publicly available data to build detailed profiles on organizations and individuals.
Why it matters:
In real-world external engagements, OSINT can be the key that unlocks your way in , no vulnerability required. And yes, you’ll absolutely need these skills in the PNPT exam.
External Pentest Playbook ; 3.5 Hours
Think of this course as your strategic blueprint for conducting external assessments. While not as technical as the others, it’s incredibly valuable for understanding how to structure a pentest from the outside in, especially when high-severity vulnerabilities like RCE aren’t available.
You’ll learn:
- How to think like an external attacker
- Real-world playbooks for discovery and exploitation
- What to do when “nothing seems vulnerable”
Linux Privilege Escalation for Beginners ; 6.5 Hours
This course walks you through the core techniques for escalating privileges in Linux environments. You’ll explore real-world misconfigurations and vulnerabilities and use public platforms like HackTheBox and TryHackMe to hone your skills.
5. Windows Privilege Escalation for Beginners ; 7 Hours
Here you’ll focus on identifying and exploiting common Windows privilege escalation vectors. From misconfigured services to weak registry permissions, you’ll learn how to move from a low-privileged shell to SYSTEM-level access.
💡 Bonus Tip:
Many TryHackMe rooms featured in this course are free , making it easy to follow along and build hands-on experience.
Which Courses Should You Prioritize for the Exam?
If you’re short on time, focus on these three:
- PEH (Practical Ethical Hacking)
- OSINT Fundamentals
- External Pentest Playbook (EPP)
However, completing all five is highly recommended , they each contribute essential knowledge and practical techniques for a well-rounded pentest workflow.
What Tools Will You Learn?
While tools are important, remember: your methodology is king. Tools evolve, get deprecated, or replaced. But a solid methodology? That never goes out of date.
Here are just some of the tools you’ll encounter across the training:
Recon & OSINT:
whois,nslookup,dnsrecon,dig,crt.shGoogle Dorking,Sublist3r,Amass,HTTProbe,ffufwappalyzer,WhatWeb,BuiltWithbreach-parse,DeHashed
Scanning & Enumeration:
nmap,netcat,Nessussmbclient,smbmap,responder,ntlmrelayx,mitm6
Exploitation & AD Attacks:
Metasploit,ldapdomaindump,BloodHound,PlumbHound,PingCastle,mimikatzsecretsdump,crackmapexec,GetUserSPNs,incognitohashcat,john the ripper
Post-Exploitation & Pivoting:
proxychains,Trevorspray
Privilege Escalation Tools:
- Windows:
WinPEAS,Sherlock,Watson,PowerUp,JAWS,Windows Exploit Suggester - Linux:
LinPEAS,LinEnum,Linux Exploit Suggester,LinuxPrivChecker
PNPT Exam Details & Cost
The Practical Network Penetration Tester (PNPT) exam spans a total of 7 days and is designed to mirror a real-world penetration test from start to finish.
Breakdown:
- 5 days dedicated to hands-on penetration testing (both external and internal).
- 2 days reserved for report writing ; a critical part of any engagement.
- A 15-minute live presentation to walk through your findings and recommendations with professional assessors.
What’s Included with the Exam Package ( And Exam Cost)
- One exam attempt plus one free retake voucher.
- 12 months’ access to ~50+ hours of online training materials, covering:
- Practical Ethical Hacking
- Linux & Windows Privilege Escalation for Beginners
- OSINT Fundamentals
- External Pentest Playbook
- Lifetime voucher validity; no expiration on exam usage
- Prize: current pricing listed at $399 (down from $499) .
| Feature | PNPT Exam Package | Live Bootcamp | Certification Bundles |
|---|---|---|---|
| Exam Attempt(s) | 1 + retake voucher | 1 PJPT + 1 PNPT voucher | Multiple cert vouchers |
| Training Access | 50+ hrs self‑paced | 28+ hrs live + 50 hrs labs + 50+ hrs on‑demand | 70–200+ hrs on‑demand |
| Time to complete | 5+2 days | 4 weeks | Self‑paced |
| Format | Lab‑based exam + report + oral debrief | Live instruction | Self‑study |
| Cost | $399 | $2,399 | $1,799–$2,999 |
How to Pass the PNPT Exam
To earn the PNPT certification, you’ll need to demonstrate both technical and professional skills through the following steps:
- Perform OSINT Reconnaissance
Use open-source intelligence techniques to collect actionable data that will guide your initial attack vectors. - Compromise the Domain
Apply your Active Directory exploitation knowledge to:- Evade antivirus (A/V) and egress controls
- Pivot laterally and escalate privileges
- Ultimately compromise the Domain Controller
- Write a Professional Report
Craft a detailed, well-organized report that documents:- Your attack path
- Tools and techniques used
- Vulnerabilities discovered
- Remediation recommendations
- Present Your Findings
Wrap up your engagement with a 15-minute live debrief in front of a panel of seasoned penetration testers. Your ability to communicate clearly and concisely is as important as your technical prowess.
Retake Policy and Support
Each PNPT voucher includes two exam attempts, giving you a fair chance at success. The team at TCM Security genuinely wants you to pass , the process is rigorous, but support is available throughout.
Rules of Engagement (ROE)
Because this is a real-world simulation, you’ll receive a Rules of Engagement (ROE) document before starting. This outlines:
- The scope of your assessment
- Allowed and prohibited actions
- Operational guidelines
Make sure you read it carefully , violating the ROE could result in exam disqualification.
PNPT vs OSCP vs eJPTV2
PNPT (Practical Network Penetration Tester)
Best for: Those looking to simulate a real pentest engagement with reporting, OSINT, external/internal pivoting, AD exploitation, and professional communication skills.
- Real-world feel: You go through the entire lifecycle of a pentest ; from OSINT to initial access, lateral movement, and post-exploitation.
- Soft skills included: You must write a client-style report and deliver a live debrief ; a rare requirement in certs.
- Focus on methodology: Less about “CTF-style pwn this box” and more about thinking like a real-world consultant.
- Supportive pricing and community: Offers lifetime access to materials and two attempts for under $400.
Great for career transitioners, junior pentesters, and those building freelancing credibility.
OSCP (Offensive Security Certified Professional)
Best for: Security professionals seeking to prove deep technical skills, especially around Linux/Windows exploitation and buffer overflows.
- Intense technical challenge: You must compromise multiple boxes under time pressure, including privilege escalation and custom exploit crafting.
- Traditional CTF-style: Focuses more on individual machine exploitation rather than full engagements.
- High pressure: The time limit and single exam attempt model raise stress ; but also prestige.
- Recognition: Still considered an industry gold standard, especially in enterprise and government sectors.
Ideal for red team aspirants, enterprise pentesters, or those looking to prove elite hands-on skills.
eJPTv2 (eLearnSecurity Junior Penetration Tester v2)
Best for: Absolute beginners who want to understand the basics of networks, protocols, scanning, and simple exploitation.
- Beginner-friendly labs: Combines theoretical content with guided labs to ease students into practical hacking.
- No stress exam: Multiple-choice & scenario-based exam with no tight time limits.
- No reporting: You won’t need to write or present anything; it’s more about validating foundational knowledge.
- Affordable & accessible: Great starting point for students, career changers, and IT professionals new to security.
Perfect entry point before moving on to PNPT or OSCP.
Key Differentiators
| Area | PNPT | OSCP | eJPTv2 |
|---|---|---|---|
| Simulation Depth | Client-like full assessment + reporting | Multi-machine exploit lab under 24h | Structured beginner labs + MCQs |
| Career Signaling | Shows complete pentest flow & soft skills | Signals elite technical grit | Shows readiness for junior roles |
| Stress Level | Moderate; built for realism, not pressure | Very high; timed, difficult | Low; self-paced and guided |
| Prep Courses | PEH + OSINT + EPP + Priv Esc + Reporting | PWK (Paid course) | INE’s learning platform |
PNPT Career Impact
The industry recognition of the TCM PNPT (Practical Network Penetration Tester) certification has been steadily growing, but it’s important to understand where it currently stands compared to more established certifications like OSCP or CEH.
PNPT is Highly respected by practitioners and hiring managers who value real-world skills.
- Many penetration testers, red teamers, and blue teamers on platforms like LinkedIn, Reddit, and Twitter/X have publicly endorsed PNPT for its realism and practical value.
PNPT stands out for testing actual pentesting workflows: OSINT, initial access, lateral movement, AD exploitation, reporting, and live presentation.
Trusted by boutique pentest firms and consultancies looking for job-ready talent.
However when I researched the deamnd from HRs and recrutires, few things I noted:
- Still less recognized by traditional HR departments or large enterprises compared to legacy certifications like OSCP, CEH, or CompTIA Security+.
- Might not appear in job postings as a required certification yet, but increasingly listed as “preferred” or “nice to have.”
- As more certified professionals list it on their resumes and more companies validate its rigor, PNPT is gaining traction in job markets.

