This article serves as a comprehensive guide to understanding and utilizing SQLmap, a powerful open-source tool designed to automate the process of detecting and exploiting SQL injection vulnerabilities in web applications.
The Role of Databases in Web Applications
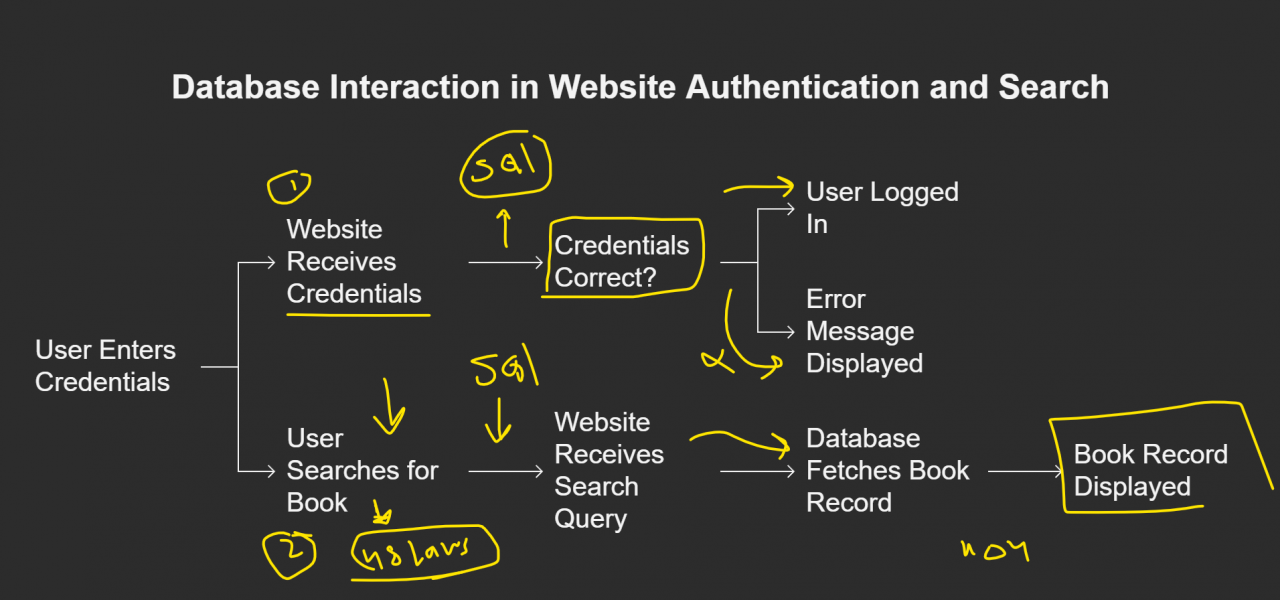
Actions such as user logins and product searches rely heavily on databases to store, retrieve, and manage information. This is achieved through the use of SQL (Structured Query Language) queries, which are sent from the web application to the database to request specific data.
Anatomy of a SQL Query and the Concept of SQL Injection
A basic SQL query for a user login is presented to illustrate the core components of the language, such as the SELECT, FROM, and WHERE clauses. The video then masterfully transitions into the concept of SQL injection. It demonstrates how an attacker can manipulate the input fields of a web form, for instance, by entering a specifically crafted string into a password field. This malicious input is designed to alter the original SQL query, causing it to bypass security checks and grant unauthorized access.

Automating Attacks with SQLmap
Recognizing that manually performing SQL injection attacks can be a time-consuming and intricate process, the video introduces SQLmap as the go-to tool for automation. It showcases two primary methods for using SQLmap:
- Using a Full HTTP Request: For web pages where the URL does not display any parameters, the video explains how to capture the full HTTP request. This can be done using tools like Burp Suite or the built-in “Inspect” feature of modern web browsers. The captured request is then saved to a file, which is fed to SQLmap for analysis.
sqlmap -r request.txt
Using a URL with Parameters: When the URL of a webpage contains visible parameters (e.g., product?cat=1), SQLmap can be used directly with the -u flag, followed by the target URL.
sqlmap -u "http://www.example.com/product?cat=1"
A Practical SQLmap Workflow
Astep-by-step demonstration of a typical SQLmap workflow, which includes:
- Vulnerability Testing: The initial step involves testing the target URL or request to confirm the presence of a SQL injection vulnerability.
- Database Enumeration: Once a vulnerability is confirmed, the
--dbsflag is used to list all the databases available on the server.
sqlmap -u "http://www.example.com/product?cat=1" --dbs
Table Enumeration: After identifying a database of interest, the -D flag is used to specify the target database, and the --tables flag is used to list all the tables within that database.
Data Dumping: Finally, to extract the data from a specific table, the -T flag is used to specify the table name, and the --dump flag is used to retrieve its contents. This can reveal sensitive information such as usernames, passwords, and email addresses.
sqlmap -u "http://www.example.com/product?cat=1" -D database_name -T table_name --dump
Streamlining the Process with --batch
To further enhance efficiency, we introduce the --batch flag. This command-line argument automates the process by providing default answers to the various prompts that SQLmap presents during its execution, allowing for a more streamlined and non-interactive experience.
TryHackMe SQLmap Basics Room Anwers
Which language builds the interaction between a website and its database?
sql
Which boolean operator checks if at least one side of the operator is true for the condition to be true?
or
Is 1=1 in an SQL query always true? (YEA/NAY)
YEA
Which flag in the SQLMap tool is used to extract all the databases available?
–dbs
What would be the full command of SQLMap for extracting all tables from the “members” database? (Vulnerable URL: http://sqlmaptesting.thm/search/cat=1)
sqlmap -u http://sqlmaptesting.thm/search/cat=1 -D members –tables
How many databases are available in this web application?
6
What is the name of the table available in the “ai” database?
user
What is the password of the email test@chatai.com?
12345678
Conclusion
In conclusion, this article provides a clear and practical overview of SQL injection and demonstrates how SQLmap can be effectively used to automate the detection and exploitation of these common web application vulnerabilities. It emphasizes the importance of identifying URL parameters as a key prerequisite for a successful SQLmap scan.




