
Web Cache Deception Explained | Portswigger BSCP Prep
In this in-depth article, I exploit a Web Cache Deception vulnerability using a PortSwigger Academy lab. This technique can expose sensitive user data through improper caching of dynamic content. Ideal for students preparing for the Burp Suite Certified Practitioner (BSCP) exam and those practicing web hacking for bug bounties.
What is a Cache?
I start by explaining that a cache is a component that sits between a user and a website. Its primary purpose is to speed up website loading times by storing copies of static resources like images, CSS, and JavaScript files. When a user requests a page, the cache checks if it has a copy of the requested resource. If it does, it serves the resource directly to the user, which is much faster than fetching it from the website’s server. If the cache doesn’t have a copy, the request is forwarded to the website, and the response is then stored by the cache before being sent to the user.
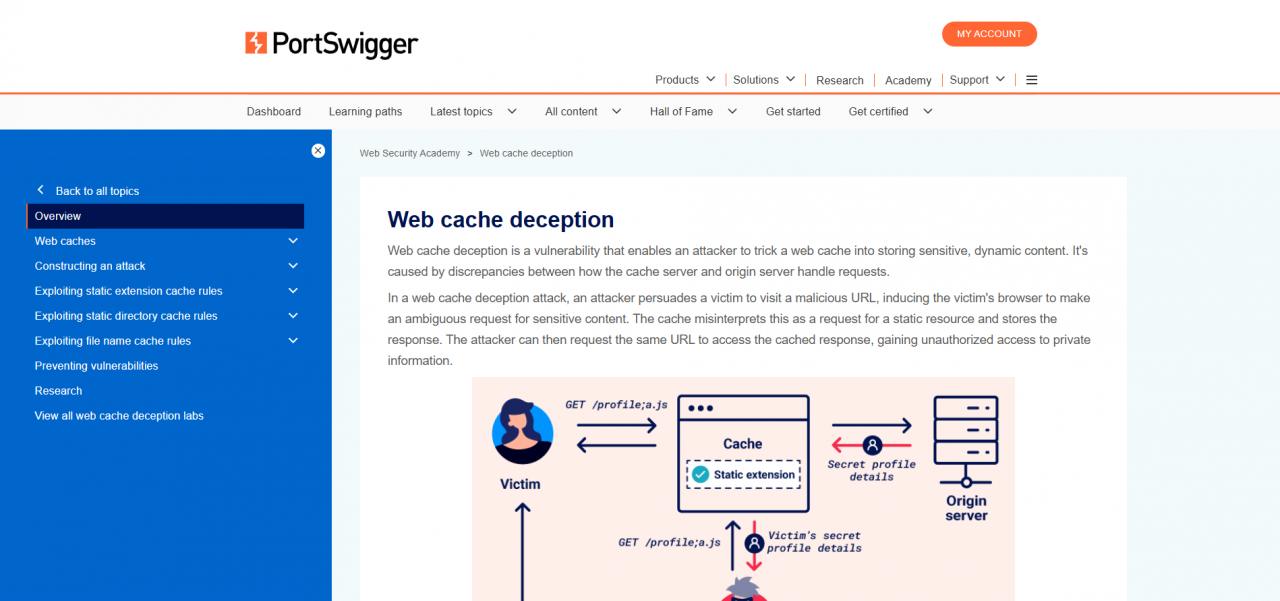
The Web Cache Deception Attack
The main idea behind this attack is to fool the cache into storing dynamic content, which often contains sensitive user information like usernames, passwords, and session data, instead of just static content.
Here’s how the attack works:
- An attacker crafts a malicious URL and sends it to a victim.
- When the victim visits this URL, the cache is tricked into storing a copy of the dynamic response, such as the victim’s profile page, which contains their sensitive information.
- The attacker then visits the same malicious URL. Since the dynamic content is now cached, the attacker can retrieve the victim’s sensitive information from the cache instead of the website’s server.
How to Exploit Web Cache Deception
I outline the steps to carry out a web cache deception attack:
- Identify the Target Endpoint: Find a part of the website that handles dynamic content, such as pages that process session cookies and display sensitive information.
- Identify a Weakness: Look for inconsistencies in how the website’s server and the cache handle URLs. This often involves understanding the different ways servers map URLs, such as traditional path-based routing versus REST-style routing.
- Craft a Malicious URL: Create a URL that exploits the identified weakness to make the cache store dynamic content.
- Send to Victim: The malicious URL is sent to the user, and when they click on it, the dynamic response from the website is stored in the cache.
- Access Cached Content: The attacker can then access the same URL to retrieve the cached dynamic content.
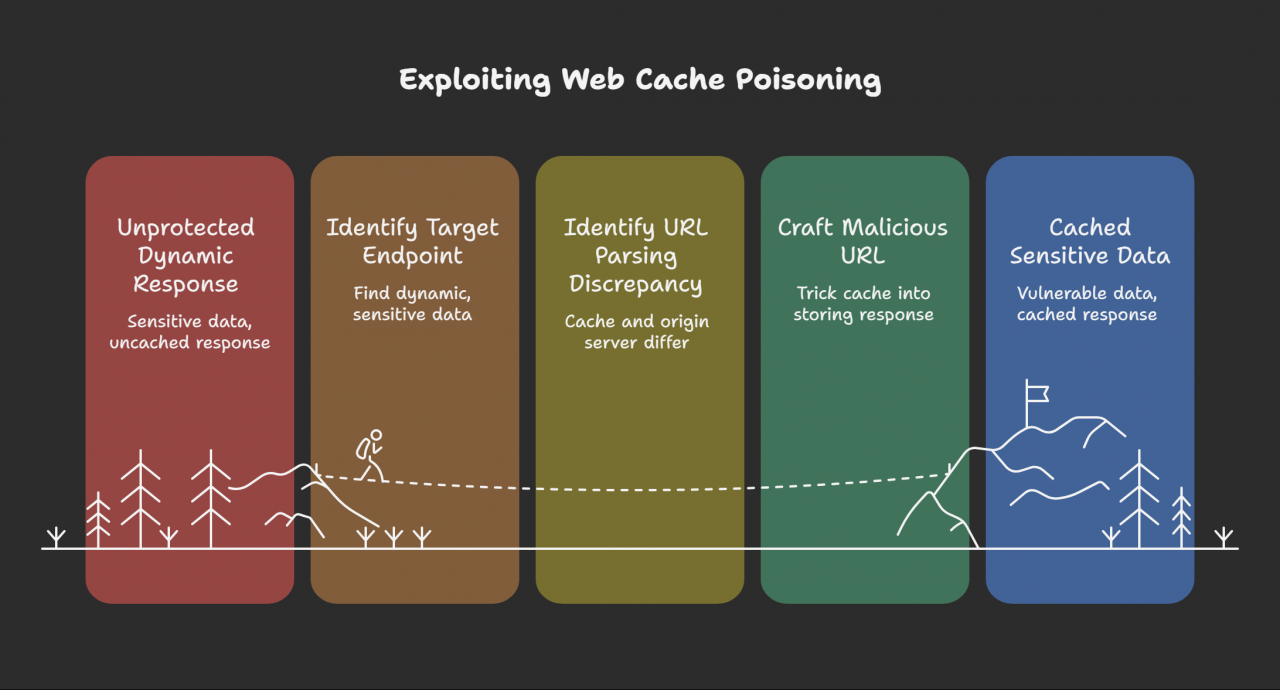
Path Mapping Discrepancy
I explain that a common vulnerability arises from a discrepancy in how the web server and the cache interpret URLs. For example, a web server using REST-style URLs might ignore file extensions, while a cache might treat a URL ending in .css as a static file that should be cached. This can be exploited to make the cache store dynamic content if the URL is crafted to look like a static file.
Hands-on Lab Demonstration
To demonstrate the attack in action, I walk through a hands-on lab from PortSwigger Academy. The goal of the lab is to find a user’s API key. I use Burp Suite to analyze the website’s requests and identify the cache’s behavior. I then craft a URL that ends in .css to trick the cache into storing the “my account” page, which contains the API key. By sending this malicious URL to a simulated victim and then accessing it myself, I am able to retrieve the victim’s API key from the cache.


























Post Comment