Windows Active Directory Penetration Testing Study Notes
Windows Active Directory Penetration Testing Study Notes is an extensive study guide and command reference for Windows Active Directory (AD) Penetration Testing. It is structured into four core parts:
- AD Basics – foundational concepts such as Domains, Domain Controllers, Forests, Trees, Organizational Units (OUs), Trusts, Global Catalog, and AD Server Roles.
- Enumeration Techniques – tools and commands for discovering users, groups, policies, services, and defenses across an AD environment.
- Exploitation & Privilege Escalation – attack methods including DCSync, BloodHound analysis, ACL abuse, token impersonation, SPN exploitation, and Group Policy misconfigurations.
- Post-Exploitation & Persistence – methods to harvest credentials, establish persistence, and move laterally using techniques like Pass-the-Hash, Kerberos attacks, and privilege escalation exploits.
Who Are These Notes For?
- Penetration Testers
- Aspiring learners who are looking to learn Windows Active Directory Penetration Testing
Table of Contents
AD Basics
- Windows Domain
- Active Directory
- Domain Controller
- Trees
- Forests
- AD Trust
- Security Groups vs OUs
- Group Policy
- Authentication Protocols in AD
Enumeration
- Users, Groups and Machines Enumeration
- Enumerating Defences and SecuritySettings
- Enumeration with Automated Scripts
- Enumeration with Powerview.ps1
- Enumeration with Metasploit andPowerspolit
- AD Enumeration with DSquery
- Enumerating Services and Processes
Exploitation and Privilege Escalation
- BloodHound
- Data Interpretation in BloodHound
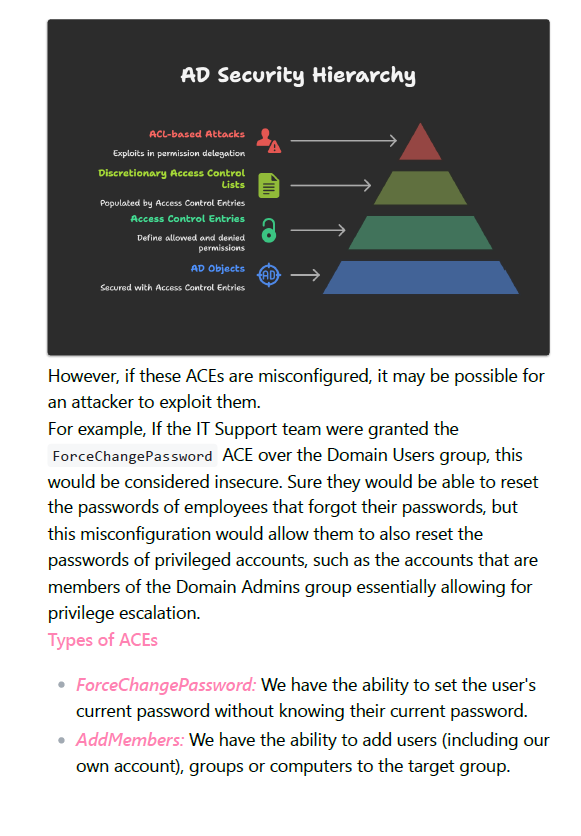
- Exploiting ACEs and PermissionDelegations
- Exploiting Active Directory using DCOMwith Macro-Enabled MS Excel
- Performing DCSync Attack
- Exploiting SeBackupPrivilege
- Using the Diskshadow method andPowershell
- By copying the SAM and SYSTEM
- Registry hives
- Exploiting PAC in Kerebros
- Exploiting Server Operators Group
- Exploiting DNS Admin Group
- Exploiting Group Policy Preferences
- Manual Methods
- Exploitation with Powersploit
- Token Impersonation
- Kerberos Delegation Exploitation
- Exploiting Delegation With Powerview.ps1
Credential Harvesting & Persistence Attacks
- Kerberos Attacks
- Password Spraying Attack
- ASREP ROASTING
- Brute forcing usernames and passwords with Kereberos
- Keberosting using cracked credentials
- Brute forcing a user hash given a list of users and hashes by performing TGTs retrieval
- Kerberos Golden and Silver Tickets
- Cracking ntds.dit and registry file system
- LDAP Pass-back attack
- Harvesting Credentials from Config Files
- Harvesting Credentials From SAM
- Harvesting From Credential Manager
- Harvesting using Local Administrator
- Password Solution (LAPS)
- Persistence through SID History
- Persistence Through Group Policy
- Persistence through Nested Groups
- Persistence Through Logon Script
- Deployment
Post Exploitation
- Credential Harvesting
- Dumping certificates from target machine with powershell and Mimikatz in memory
- Infecting other domain joined machines using WMI method from Powerview
- Downloading and executing a powershell script in memory ( Mimikatz.ps1 ) to harvest admin password on the targeted domain controller.
- Powershell script that Downloads Mimikatz and executes it on multiple defined machines using WMI.
- Credential Harvesting Using LDAP Queries
- Accessing the netlogon share on DC
Lateral Movement
- Definition
- With PsExec
- With WINRM
- With Service Management Tools SC
- With Scheduled Tasks
- With WMI
- Using PassTheHash
- Using Pass The Ticket
- Using Overpass-the-hash / Pass-the-Key
- Using Port Forwarding
- SSH Tunneling
- With Socat
- Dynamic Forwarding with SOCKS
Format:
Page count: 152

Testimonials (LinkedIn)
How to buy the booklet?
You can buy the booklet directly by clicking on the button below
What about the notes updates?
if you have been watching my YouTube Channel, you definitely know that those who subscribe to the second tier of my channel membership they instantly get access to a vast catalog of cybersecurity, penetration testing, digital marketing, system administration and data analytics notes catalog for 10$ along with the ability to receive all notes updates as long as they are subscribed so what does that mean?
This means if you want to stay up to date with the changes and updates to the notes and get access to other categories, I encourage to join the channel membership second tier instead. However, if you are fine with downloading the current version of this section of the notes then you can buy this booklet instead for a one-time payment.
Will the prices of this booklet change in the future?
Once another version of this booklet is released, which it will, the price will slightly change as the booklet will include more contents, notes and illustrations.
Free Windows Active Directory Penetration Testing Training
Checkout the playlist below on my YouTube channel for free Windows Active Directory Penetration Testing Training
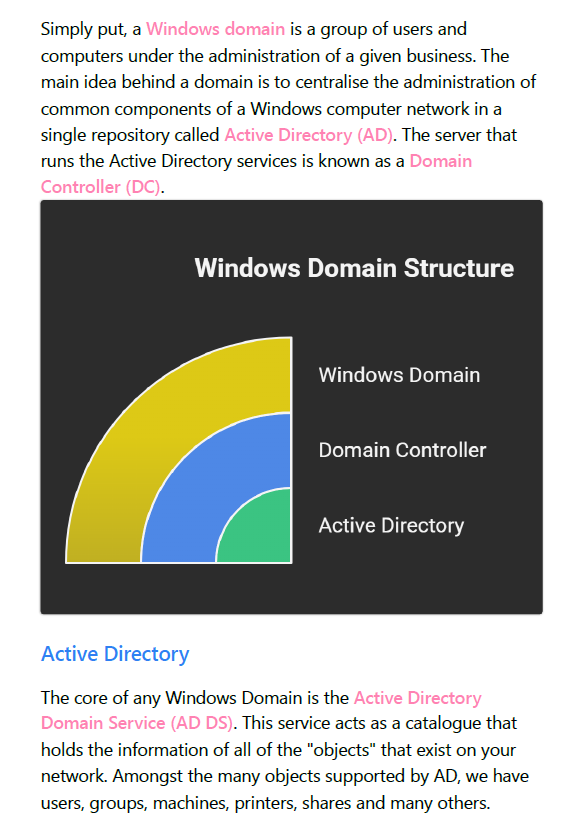
Windows Domain
Simply put, a Windows domain is a group of users and computers under the administration of a given business. The main idea behind a domain is to centralise the administration of common components of a Windows computer network in a single repository called Active Directory (AD). The server that runs the Active Directory services is known as a Domain Controller (DC).
Active Directory
The core of any Windows Domain is the Active Directory Domain Service (AD DS). This service acts as a catalogue that holds the information of all of the “objects” that exist on your network. Amongst the many objects supported by AD, we have users, groups, machines, printers, shares and many others.
Domain Controller
A Domain Controller is an Active Directory server that acts as the brain for a Windows server domain; it supervises the entire network. Within the domain, it acts as a gatekeeper for users’ authentication and IT resources authorization

