We covered WordPress Penetration Testing and Linux privilege escalation using vulnerable version of Nmap.
Getting In and Finding the First Key
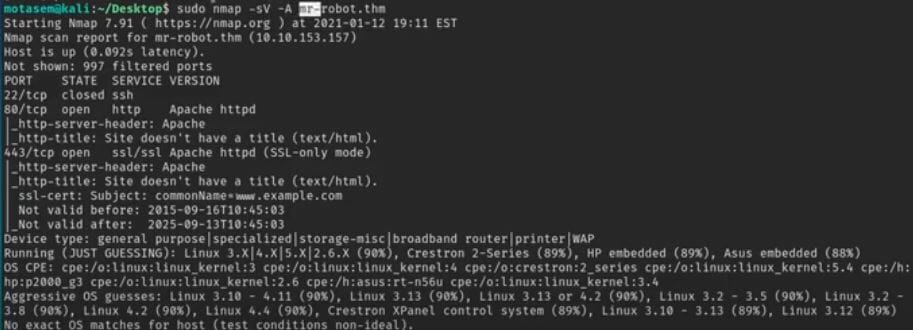
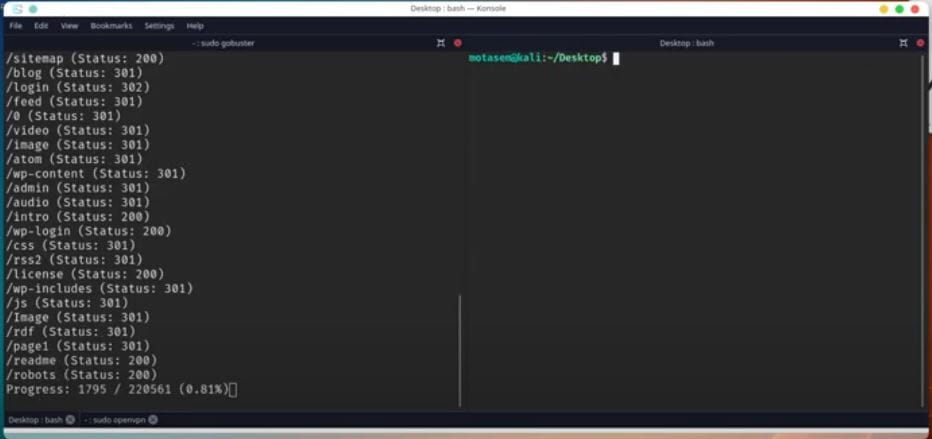
My first step is always reconnaissance. I add the machine’s IP address to my hosts file and see that it’s running a web server. The main page is a cool, interactive terminal, but it’s just for show. I fire up dirbuster to look for hidden directories and quickly find that it’s a WordPress site.
This leads me to the robots.txt file, which is always a good place to check for clues. And just like that, I find the first key (K1) hidden inside.
Nmap scan results
Directory search scan results
Cracking WordPress and Getting a Shell
I also find a wordlist file named fsociety.dic, which is a dead giveaway that I’ll need to do some password cracking. I use Hydra to brute-force the WordPress login form, and after a bit of work, I’m in the admin panel.
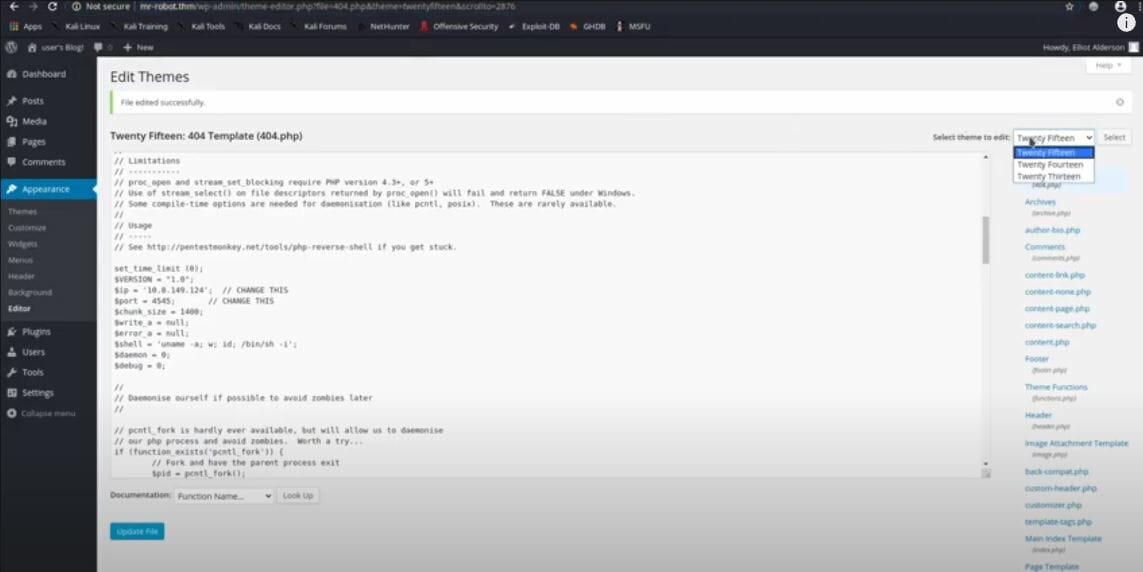
Now that I’m in, my goal is to get a reverse shell. I try editing a few plugin files, but I run into some permission issues. So, I switch tactics and decide to edit a theme file instead. I inject a PHP reverse shell into the 404.php file of one of the themes. I set up a Netcat listener on my machine, activate the theme, and boom, I have a shell on the server.
Injecting the WordPress default theme with PHP reverse shell
inding the Second Key and Escalating Privileges
With my initial shell, I start looking around for the next key. I find key2.txt in the /home/robot directory, but I don’t have permission to read it yet. I also find a file containing the password hash for the robot user.
I take the hash offline and use John the Ripper to crack it. With the password in hand, I switch to the robot user and can now read the contents of key2.txt to get the second key (K2).
Root Access and the Final Key
For the final step, I need to get root access. I search for any SUID binaries on the system, which are programs that run with the permissions of their owner (in this case, hopefully, root). I find that Nmap has the SUID bit set.
This is a known vulnerability in older versions of Nmap. I run nmap --interactive, which drops me into an interactive Nmap shell. From there, I can simply type !sh to spawn a shell, and because Nmap was running as root, my new shell is also a root shell!
I navigate to the /root directory and find the third and final key (K3). Challenge complete!
Technical Commands
Here’s a list of the key commands I used to conquer this machine:
- Directory Brute-forcing:
dirbuster
- WordPress Scanning and Cracking:
wpscanHydra
- Netcat Listener:
nc -lvnp <port>
- Password Cracking:
john --format=raw-md5 --wordlist=<wordlist> <hash_file>john --show <hash_file>
- Privilege Escalation:
su robotfind / -perm -u=s -type f 2>/dev/nullnmap --interactive!sh(inside Nmap’s interactive mode)
- Basic Navigation and File Reading:
ifconfigidcd <directory>lscat <file>
TryHackMe OSCP: Mr Robot Answers
What is key 1?
What is key 2?
What is key 3?




