
Lockbit Ransomware Analysis with ANY.RUN
This article gives a fascinating and slightly terrifying look into LockBit 4.0, a notoriously dangerous ransomware that’s been causing headaches for cybersecurity experts worldwide. I break down what makes this ransomware so nasty, from its sneaky evasion tactics to its complex encryption methods. I also walk us through a live analysis and, most importantly, share some good news for victims.
What Makes LockBit Ransomware 4.0 So Scary?
LockBit ransomware 4.0 is all about speed and stealth. It gets in, encrypts your files, drops a ransom note, and then vanishes before most security systems even know what hit them.
One of the most interesting tidbits is that it’s designed to avoid computers with Russian keyboard layouts, which strongly suggests that the masterminds behind it are likely based in Russia.
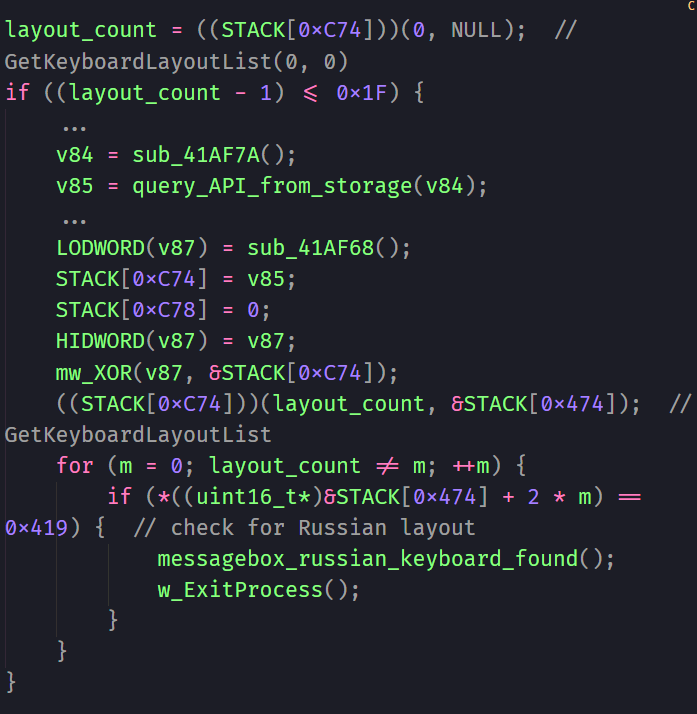
How LockBit Ransomware 4.0 Stays Hidden
The real genius (and terror) of LockBit 4.0 lies in its ability to avoid detection.

- API Name Juggling: The ransomware plays a clever trick by dynamically loading Windows APIs and scrambling their names. This makes it incredibly difficult for security software to figure out what the ransomware is trying to do.
- Going off the Grid: It messes with the Event Tracing for Windows (ETW), which is like the black box for your computer. By disabling this, LockBit 4.0 effectively erases its own footprints, making it nearly impossible to track its activity.
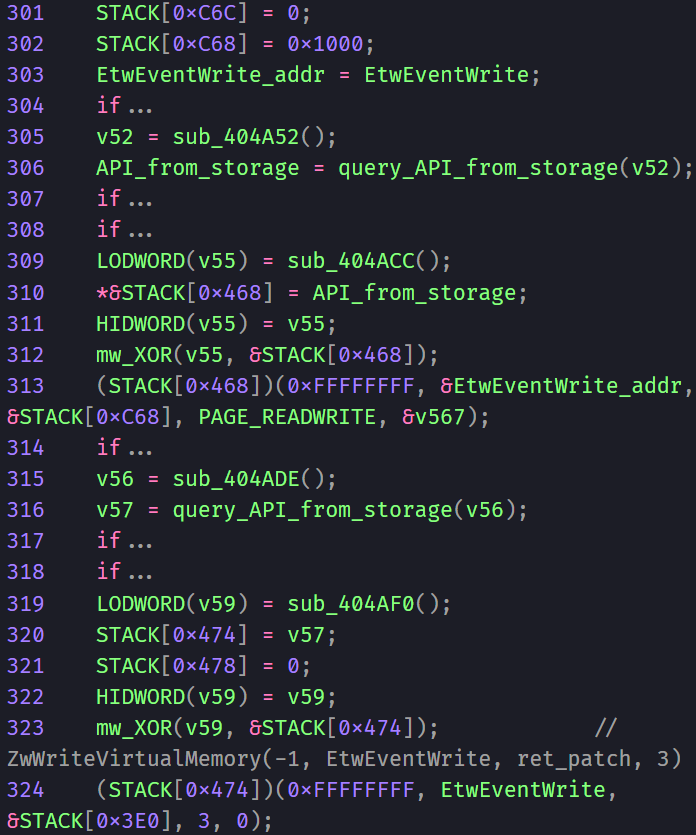
- A Decompiler’s Nightmare: For the tech-savvy folks trying to reverse-engineer the malware, LockBit 4.0 has a special surprise. It flips stack variables in a way that confuses analysis tools, making it a real puzzle to deconstruct.
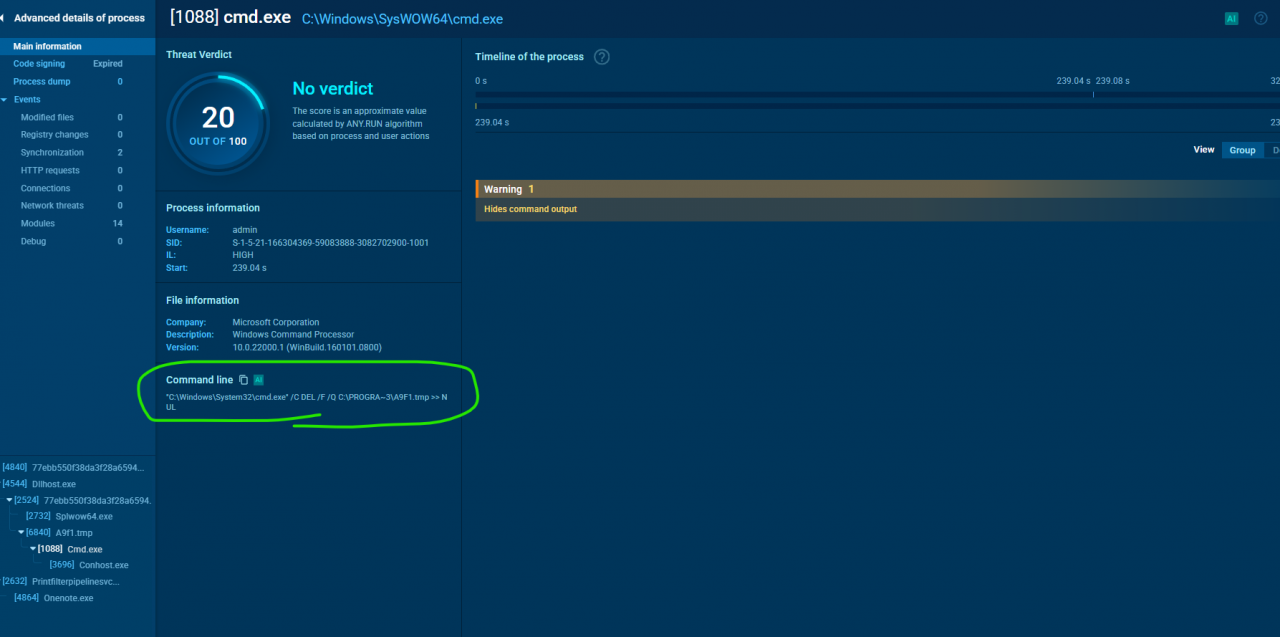
- Clean-up of Traces: After encryption, the ransomware executes commands to perform a cleanup, such as deleting temporary files using /F (forceful deletion) and /Q (silent deletion). This is likely done to clear traces and evidence against the ransomware, which is a known MITRE ATT&CK tactic (T1070.004 – File Deletion)
- Disabling Windows Logging: LockBit 4.0 manipulates and completely disables the Event Tracing for Windows (ETW) event write value. This mechanism usually controls logging and tracing of events created by user-mode applications and kernel-mode drivers, so disabling it prevents logs from being created. The ransomware achieves this by granting itself read/write permissions and then calling ZW write virtual memory to change the ETW event write value to a disabled state.
Advanced Encryption Techniques
Hybrid Cryptographic Mechanism: LockBit 4.0 employs a combination of both asymmetric and symmetric encryption algorithms.
ChaCha20 Algorithm (Symmetric): This algorithm is used for the generation of the encryption key.
Curve25519 Algorithm (Asymmetric): This algorithm is used for asymmetric key exchange. Specifically, it is used to generate a pair of public and private keys for every single file being encrypted.
Combined Key Usage: For each file, the encryption process uses a combination of the key generated by ChaCha20 and the public/private key pairs generated by Curve255197. This makes the decryption process complicated, requiring a specific decryptor that reverses this dual-mechanism.
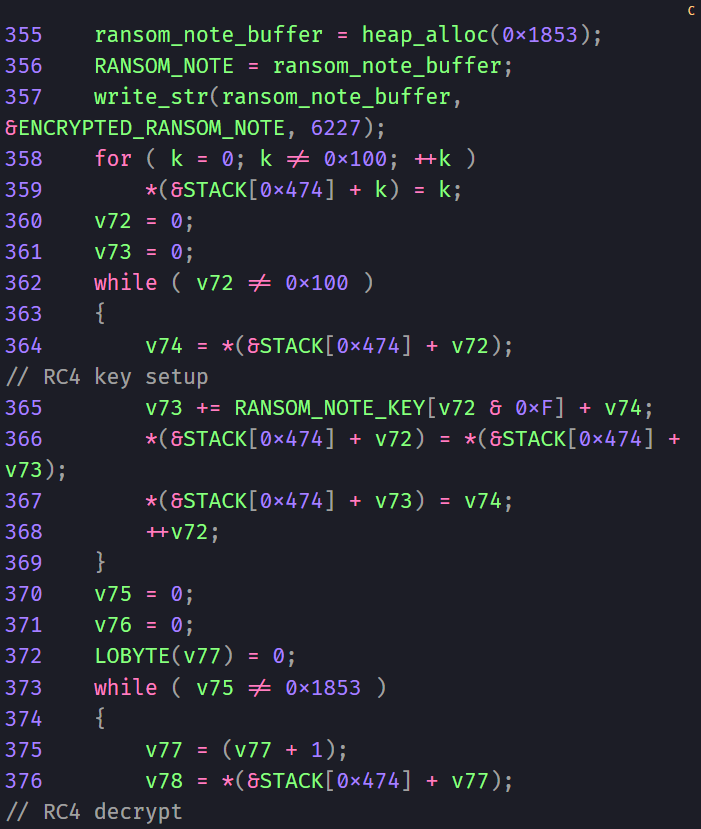
RC4 for Ransom Note: The ransomware note itself is encrypted and decrypted using the RC4 algorithm.
The Ransom Note: A Mix of Threats and… Financial Advice?
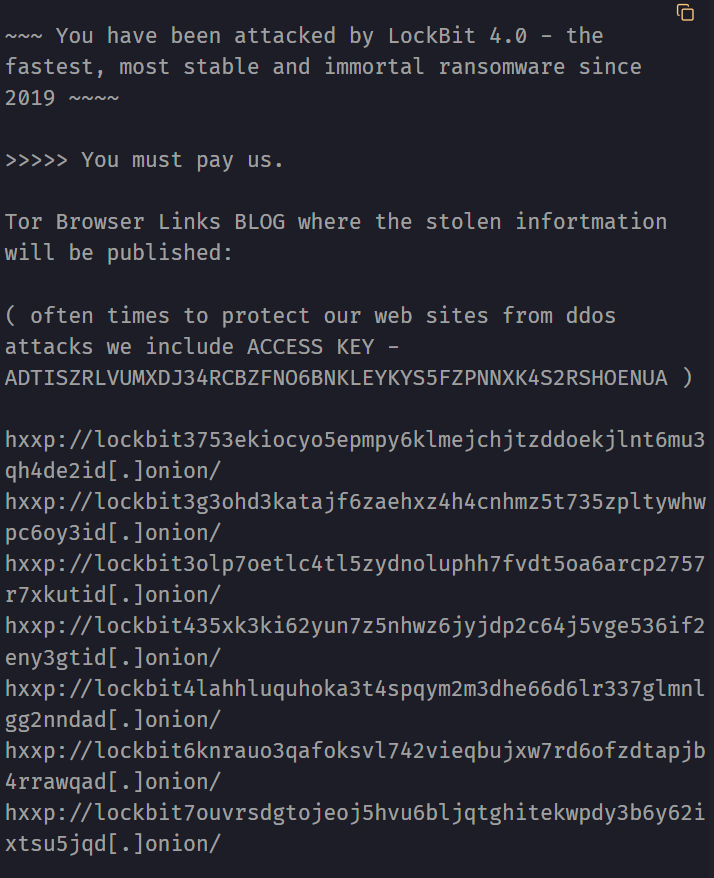
The ransom note itself is a piece of work. It’s encrypted (using the RC4 algorithm) and, once decrypted, informs the victim that they’ve been hit by “LockBit Black.” The note boasts about being the “fastest, most stable, and immortal ransomware” and, of course, demands a hefty payment.
It also includes a link to a Tor website where victims can see their stolen data, a classic extortion tactic. The note tries to sound reputable, promising not to scam its victims, but then warns against modifying encrypted files or calling the cops.
And here’s the truly bizarre part: the note gives detailed instructions on how to buy Bitcoin, complete with excuses to give your bank, like “I’m participating in an ICO” or “I’m supporting Donald Trump’s election campaign.” You can’t make this stuff up!
Lockbit Ransomware Decryption
Thankfully, it’s not all doom and gloom. BitDefender has released a decryptor for LockBit ransomware victims.
Putting LockBit 4.0 Under the Microscope
I run dynamic analysis of the sample using Any.Run
- Flagged by Antivirus: As expected, the ransomware sample was immediately flagged as malicious.
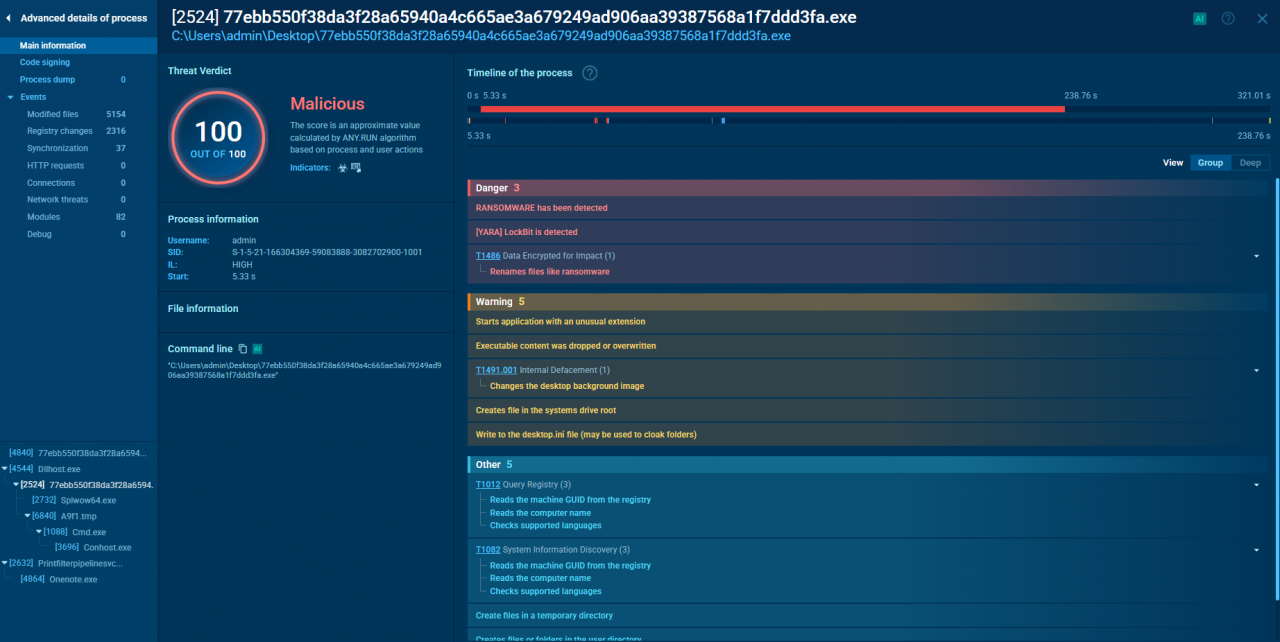
- Tell-Tale Signs: The analysis revealed classic ransomware behavior, like renaming files with a new extension, changing the desktop background to an alert, and dropping a ransom note in every encrypted directory.
- Covering Its Tracks: The ransomware was caught running a command to delete temporary files, a clear attempt to remove evidence of its presence.
- Silent but Deadly: Interestingly, the ransomware didn’t communicate with any command-and-control servers during the analysis.
- A Trail of Clues: The analysis provided a wealth of Indicators of Compromise (IOCs), which are crucial for cybersecurity professionals to track and defend against this threat.
Malware Analysis with ANY.RUN
ANY.RUN is a malware analysis and threat intelligence platform for SOC teams.
Integrate ANY.RUN solutions into your company.
Sign up for ANY.RUN for free by providing your business email.

























Post Comment