Introduction
In HackTheBox Flag Command, we ffectively used enumeration, DevTools, and JavaScript analysis to bypass the normal game mechanics and uncover hidden functionality in a classic Web CTF challenge.
HackTheBox Flag Command Description

Embark on the “Dimensional Escape Quest” where you wake up in a mysterious forest maze that’s not quite of this world. Navigate singing squirrels, mischievous nymphs, and grumpy wizards in a whimsical labyrinth that may lead to otherworldly surprises. Will you conquer the enchanted maze or find yourself lost in a different dimension of magical challenges? The journey unfolds in this mystical escape!
Web Enumeration
By visiting the home page, we find the following where we can play a game to get the flag.
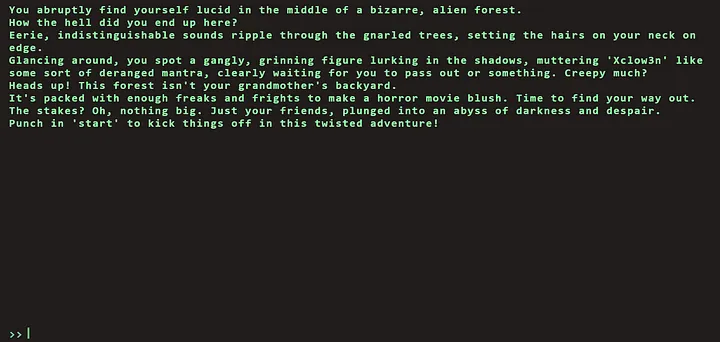
To solve the challenge , we will follow the below methodology:
- Checking for
robots.txt– Always a good first step in web-based CTFs. - Using DevTools (
F12) – Helps inspect JavaScript files, API requests, and responses. - Examining JavaScript Files – You pinpointed
main.jsas the core logic handler. - Understanding Conditional Checks – Identifying the secret commands array.
- Using the Network Tab – To inspect
/api/optionsand extract hidden commands.
For similar challenges, always:
- Look for client-side validation bypass opportunities.
- Check API responses for unintended leaks.
- Use
fetch()interception for data being sent/received.
Game Mechanics
Upon selecting ‘start,’ four options appeared on the screen. Unsure which one was correct, I decided to take a chance and chose HEAD NORTH.
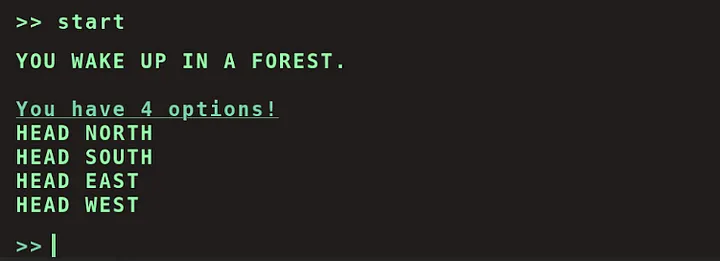
This choice led to another set of four options. Using the same trial-and-error approach, I successfully advanced to the third stage: HEAD NORTH → FOLLOW A MYSTERIOUS PATH → SET UP CAMP.
However, at the fourth question, none of the available options were correct. No matter what I entered, I kept encountering a Game Over screen.
Using The Browser Developer Tools
By pressing F12, I accessed the Developer Tools and navigated to the Debugger tab. The site contained three JavaScript files: commands.js, main.js, and game.js. Among them, main.js stood out, and within it, one particular function caught my attention.
The function’s if statement establishes two conditions: it checks whether the input matches one of the available options for the current question or if the answer is "secret". If either condition is met, the subsequent block of code is executed.
Upon analyzing multiple if statements within the code, I identified the correct answers for the first three questions. To further investigate, I leveraged the Network tab in DevTools to examine the resources being requested. By refreshing the page using F5, I observed multiple network requests, among which the most revealing was the interaction with the /api/options endpoint.
This API response, formatted in JSON, contains all possible answer choices—including not just those visible during gameplay but also a hidden "secret" option embedded in main.js. Given this discovery, an intriguing next step would be testing the "secret" answer as a response to the first question to see how the system reacts.
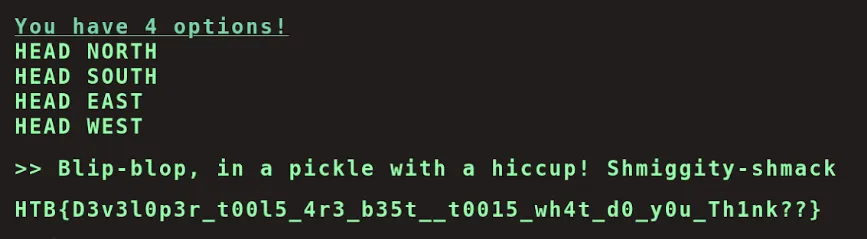
Notes
Security Implications: The presence of a "secret" answer suggests a potential debugging mechanism or an Easter egg left by the developers. If unintended, this could be an oversight, potentially exploitable.
Reverse Engineering Approach: Examining if conditions and analyzing network traffic can be powerful techniques for understanding web applications, especially when dealing with hidden logic or security vulnerabilities.
API Exposure: Since the API provides all possible answer choices—including hidden ones—it raises questions about whether the data should be more restricted or obfuscated to prevent unintended discoveries.




