Who is this book for?
Informatin security study notes & guide provides a deep dive into information security principles, offering guidance on protecting data confidentiality, integrity, and availability through layered defenses. It highlights key strategies like access control, authentication protocols, and risk mitigation frameworks (e.g., NIST, ISO 27001).
It concludes by underlining the importance of aligning cybersecurity practices with governance and compliance, equipping organizations with tools to resist modern threats, assess vulnerabilities, and manage data responsibly.
This E-book is intended to introduce you to the world of information security by providing brief introduction of key information security concepts & definitions for the purpose of equipping you with the basics if you wish to take this knowledge further and learn more advanced and more specialised knowledge in the domain of information security.
Table of Contents:
– Introduction
– Information Security Basics
-CIA Triad
-Confidentiality
-Integrity
-Availability
-DAD, Over-protection, Authenticity,Non-repudiation, and AAA Services
-Access Control
-Authentication
-Due Diligence & Due Care
-Defense in Depth
-Understanding What is A Security Policy
-Understanding Security Standards,
-Baselines, Guidelines and Procedures
-Types of Security Controls
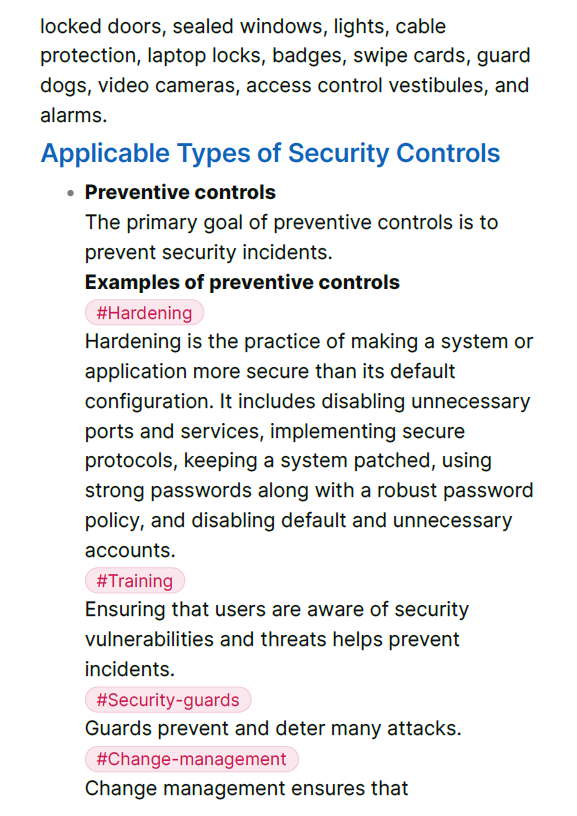
-Applicable Types of Security Controls
-Types of Data and Data Classifications
-Social Engineering
-Implementing Information Security Programs
-Implementing an Incident Response Program
-Data Governance
-Risk Management
-Vulnerability Management
-Business Continuity
-Information Security Regulations
-Information Security Frameworks
-Conclusion
Page Count: 112
Format: PDF

Information Security Basics
CIA Triad
The 5 Pillars of Information Security are confidentiality, integrity, availability, authenticity, and nonrepudiation. The first three of these, namely confidentiality, integrity, and availability, are so commonly discussed as a group they have been labeled with their own phrase, the CIA Triad.
Security controls are typically evaluated on how well they address these three core information security tenets. Vulnerabilities and risks are also evaluated based on the threat they pose against one or more of the CIA Triad principles.
Confidentiality
[1]Confidentiality is the concept of the measures used to ensure the protection of the secrecy of data, objects, or resources. The goal of confidentiality protection is to prevent or minimize unauthorized access to data. Confidentiality protections prevent disclosure while protecting authorized access.
[2]
Numerous countermeasures can help ensure confidentiality against possible threats. These include encryption, network traffic padding, strict access control, rigorous authentication procedures, data classification, and extensive personnel training.
Integrity
[1]Integrity is the concept of protecting the reliability and correctness of data. Integrity protection prevents unauthorized alterations of data. Properly implemented integrity protection provides a means for authorized changes while protecting against intended and malicious unauthorized activities (such as viruses and intrusions) and mistakes made by authorized users (such as accidents or oversights).
[2]
Numerous attacks focus on the violation of integrity. These include viruses, logic bombs, unauthorized access, errors in coding and applications, malicious modification, intentional replacement, and system backdoors. Human error, oversight, or ineptitude accounts for many instances of unauthorized alteration of sensitive information. They can also occur because of an oversight in a security policy or a misconfigured security control.
[3]
Numerous countermeasures can ensure integrity against possible threats. These include strict access control, rigorous authentication procedures, intrusion detection systems, object/data encryption,
hash verifications interface restrictions, input/function checks, and extensive personnel training.
Availability
[1]Availability includes efficient, uninterrupted access to objects and prevention of denial-of-service (DoS) attacks. Availability also implies that the supporting infrastructure—including network services, communications, and access control mechanisms—is functional and allows authorized users to gain access.
[2]
There are numerous threats to availability. These include device failure, software errors, and environmental issues (heat, static electricity, flooding, power loss, and so on). Some forms of attack focus on the violation of availability, including DoS attacks, object destruction, and communication interruptions.
[3]
Numerous countermeasures can ensure availability against possible threats. These include designing intermediary delivery systems properly, using access controls effectively, monitoring performance and network traffic, using firewalls and routers to prevent DoS attacks, implementing redundancy for critical systems, and maintaining and testing backup systems. Most security policies, as well as business continuity planning (BCP), focus on the use of fault tolerance features at the various levels of access/storage/security (that is, disk, server, or site) with the goal of eliminating single points of failure to maintain the availability of critical systems.
Availability depends on both integrity and confidentiality. Without integrity and confidentiality, availability cannot be maintained.
Testimonials (LinkedIn)
How to buy the book?
You can buy the book directly by clicking on the button below
After you buy the booklet, you will be able to download the PDF book.
What about the notes updates?
if you have been watching my YouTube Channel, you definitely know that those who subscribe to the second tier of my channel membership they instantly get access to a vast catalog of cybersecurity, penetration testing, digital marketing, system administration and data analytics notes catalog for 10$ along with the ability to receive all notes updates as long as they are subscribed so what does that mean?
This means if you want to stay up to date with the changes and updates to the notes and get access to other categories, I encourage to join the channel membership second tier instead. However, if you are fine with downloading the current version of this section of the notes then you can buy this booklet instead for a one-time payment.
Will the prices of this booklet change in the future?
Once another version of this booklet is released, which it will, the price will slightly change as the booklet will include more contents, notes and illustrations.
Free Information Security Training
Checkout the playlist below on my YouTube channel for Free Information Security Training

