Malware analysis study notes teaches malware analysis from basic propagation techniques to advanced reverse engineering with tools like Ghidra and Capa. It emphasizes setting up isolated environments for safe analysis, identifying malware behaviors via PE headers and API calls, and understanding document-based attacks (e.g., PDF/Word macros).
Dynamic tools like Process Monitor, API Logger, and online sandboxes are explored to monitor real-time activity.
Evasion techniques like packing, sleep calls, and VM detection are discussed, and a variety of strategies for detection and remediation on Windows and Linux systems are provided. Ultimately, the text serves as a comprehensive toolkit for malware analysts aiming to detect, dissect, and defend against threats.
Who is this book for?
This e-book is intended to be used as quickreference to facts and information on the subject ofmalware analysis. Additionally, it can also be used tostudy malware analysis.
Table of Contents
- Introduction
- About The Authors
- Malware Analysis
-Creating The Environment
-Static Analysis
-Definition
-Tools
-Hex and Ascii View of the suspectedfile
-Extracting File Hash
-Analyzing strings
-Non obfuscated binaries &Obfuscated binaries
-Finding The Imphash
-Analyzing The Signature
-Analyzing PE Headers
-Detecting Capabilities
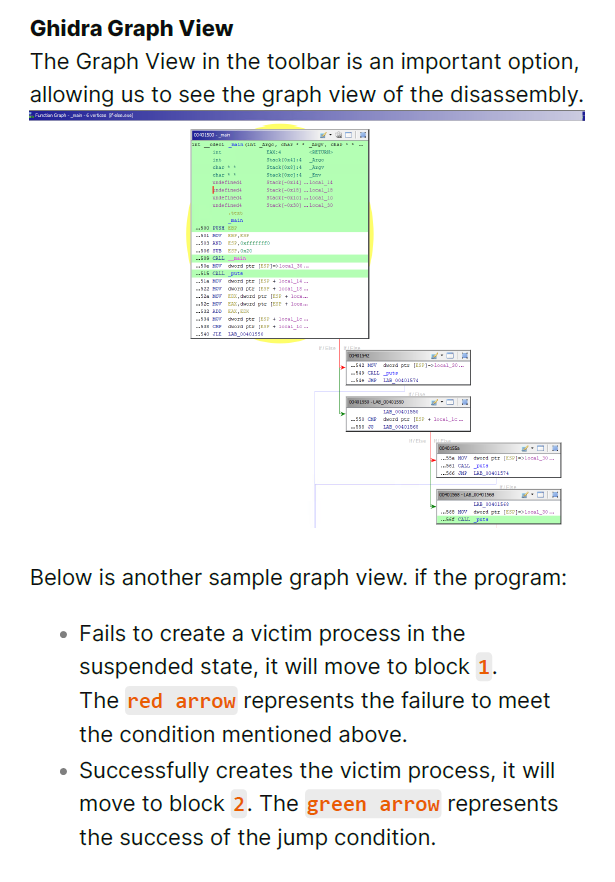
- Advanced Static Analysis with Ghidra
- Dynamic Analysis
-Definition
-Dynamic analysis tools
- Malware analysis evasion techniques
- Analysis with Online Tools
- Malware Removal
- Malware Detection
-Indicators of Malware Presence
-Methodology
-Automated Malware Scanning
-Analyzing startup processes and autoruns
-Analyzing processes
-Analyzing Logs
-Hunting Based on File Search
-Analyzing WMI Instances
-Hunting Malwares with Yara
-Yara scanners
Page Count: 165
Format: PDF
Overview
This e-book is intended to be used as quick reference to facts and information on the subject of malware analysis. Additionally, it can also be used to study malware analysis.
I recommend you to start reading this book by first reading Malware Detection, which is the last section, as it will teach you to spot the presence of malware in your system.
After spotting the malware, it becomes imperative to have the knowledge on how to analyze it therefore you can then move on the other sections and start with Malware Analysis which happens to be the first section.
Testimonials (LinkedIn)
How to buy the book?
You can buy the book directly by clicking on the button below
After you buy the booklet, you will be able to download the PDF book.
What about the notes updates?
if you have been following my YouTube Channel, you definitely know that those who subscribe to the second tier of my channel membership they instantly get access to a vast catalog of cybersecurity, penetration testing, digital marketing, system administration and data analytics notes catalog for 10$ along with the ability to receive all notes updates as long as they are subscribed so what does that mean?
This means if you want to stay up to date with the changes and updates to the notes and get access to other categories, I encourage to join the channel membership second tier instead. However, if you are fine with downloading the current version of this section of the notes then you can buy this booklet instead for a one-time payment.
Will the prices of this booklet change in the future?
Once another version of this booklet is released, which it will, the price will slightly change as the booklet will include more contents, notes and illustrations.
FREE Short Malware Analysis Course
Checkout the playlist below on my YouTube channel for Free Computer Forensics Training


