Medical devices, including pacemakers, insulin pumps, and imaging systems, are increasingly interconnected within hospital networks and the internet, enhancing patient care but also exposing them to cyber threats. These vulnerabilities can lead to unauthorized access, data breaches, and even direct harm to patients.
A 2018 study highlighted that devices like CT scanners are particularly susceptible, with potential attacks capable of altering scan parameters or causing mechanical disruptions.
In this post, we will outline the medical devices considered the most prone to cyber attacks.
Offensive Security Web Assessor (OSWA) Study Notes
Magnetic Resonance Imaging (MRI)
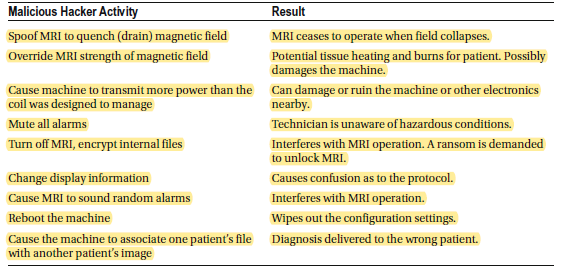
A frequent MRI safety violation happens when a metal object is pulled in by the static magnetic field. While MRIs are generally safe, if a hacker gains control of the system, they could cause a metal object to strike, injure, or pin someone against the magnet. The MRI itself could also be damaged if an object crashes into it or accelerates rapidly toward it. These high-intensity magnetic field incidents, known as “missile-effect” accidents, occur when ferromagnetic objects are drawn into the magnet’s core, sometimes leading to serious injuries or fatalities. In one tragic instance, a six-year-old boy was killed during an MRI scan when an oxygen tank was pulled across the room and fatally struck his head.
MRI machines can also interfere with implanted medical devices by displacing them, heating them due to radiofrequency energy, or distorting imaging results. For this reason, all passive implants come with specific guidelines for use in the MRI environment.
MRI technology relies on a strong and uniform magnetic field. This field strength is measured in teslas (T), with most machines operating at 1.5T. However, clinical systems can reach up to 19.8T. After being excited, tissues return to their normal state through two relaxation processes: T1 (spin-lattice) and T2 (spin-spin) relaxation.
X-ray Generator (X-ray)
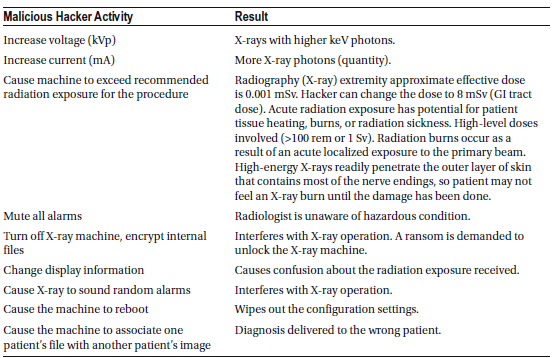
Medical X-ray machines are designed to capture images of dense tissues. However, because they emit highly penetrating and ionizing radiation, they can be extremely dangerous. X-rays are readily absorbed by soft tissues, and direct exposure to primary or scattered beams can cause severe burns on the skin, hands, arms, or eyes. The most common early reversible effect is skin reddening, known as erythema. At low radiation doses and energy levels, this redness fades over time without lasting harm. Another temporary effect is hair loss (epilation), caused by radiation halting cell division in hair follicle cells. With low exposure, hair eventually regrows without permanent damage. Additionally, radiation can temporarily reduce sebum production by affecting sebaceous glands.
If a hacker manipulates the machine to increase radiation exposure, a patient could suffer from irreversible damage, including permanent destruction of hair follicles, sweat glands, or scarring of the skin. These lasting effects are classified as radiation dermatitis, chronic radiation dermatitis, and radiation-induced cancer. Acute radiation exposure occurs when a large dose (over 100 rem or 1 Sievert) is received at once, causing symptoms within days or weeks. In contrast, chronic exposure involves low doses over long periods, allowing the body time to heal, with potential effects appearing 20 to 30 years later.
Radiation burns result from acute, localized exposure to the primary beam. Because high-energy X-rays penetrate the skin’s outer layer—where most nerve endings are located—patients may not feel the damage until it has occurred. Severe burns can lead to the need for skin grafts or even finger amputations. The severity of burns depends on the radiation dose, exposure duration, X-ray energy, and individual sensitivity. Burns may occur at exposures of 300 rem but are usually not visible below 600 rem.
Radiation sickness arises when the entire body is exposed to a large radiation dose. Symptoms typically appear only after receiving more than 100 rem within a few hours. Even at lower exposures, changes in blood tissue can be detected. A whole-body dose between 400 and 500 rem can result in a 50% fatality rate within 30 days without treatment, and survivors experience months of severe illness. Acute exposure to doses above 700 rem often leads to death within a few weeks.
Infusion Pump
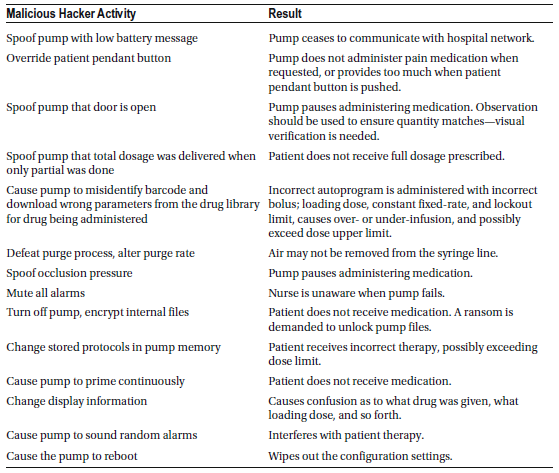
Infusion pumps are highly reliable and safe when used according to manufacturer guidelines. Manufacturers continuously enhance the safety features of these devices, and the latest generation of “smart pumps” shows great potential for further improving patient safety. Infusion pumps are critical for administering high-risk medications, fluids, and nutrients directly into a patient’s bloodstream. However, if a hacker interferes with the delivery settings, the consequences could be severe. Just like other electro-mechanical devices, built-in safety features—such as alarms and alerts—could be bypassed by a skilled hacker.
The safety features of infusion pumps vary depending on the model and its age. Advanced, state-of-the-art infusion pumps typically include the following safeguards:
- Redundancy: No single point of failure that could cause the pump to malfunction silently; the pump issues an audible alarm to alert the nurse.
- Backup Power: Battery backup in case of a power outage.
- Anti-Free-Flow Devices: Prevents blood from draining out of the patient and stops fluids from freely flowing into the patient during setup.
- Down Pressure Sensors: Detects blockages in the vein or kinks in the line.
- Air-in-Line Detectors: Identifies air bubbles in the line to prevent air embolisms.
- Up Pressure Sensors: Alerts when the fluid bag or syringe is empty.
- Drug Libraries: Includes customizable programmable limits for different medications to minimize dosing errors.
- Flow Control Mechanisms: Prevents uncontrolled drug delivery.
- Event Logging: Maintains an internal record of thousands of previous therapy events.
Despite these safety features, infusion pumps have been linked to numerous patient safety issues. Between 2005 and 2009, over 56,000 adverse event reports were associated with infusion pumps, including at least 500 fatalities. During this period, there were 87 recalls, with 70 classified as Class II (indicating reversible or unlikely serious health risks) and 14 as Class I (indicating risks of serious harm or death). In response, the FDA introduced stricter regulations and launched the Infusion Pump Improvement Initiative.
Many of these adverse events stemmed from software defects, leading to over- or under-infusion. Other recalls were related to user interface problems and mechanical or electrical failures. If a hacker gains access to a pump—especially one with wireless connectivity—they could dangerously alter key settings, such as:
- Occlusion levels (which manage pressure to detect blockages)
- Purge and bolus rates (controlling rapid drug delivery)
- Dosage profiles (adjusting flow rate, volume, and delivery time)
- KVO (Keep Vein Open) settings
Even more concerning, a hacker could manipulate the user interface to display the correct dosage input by medical staff while secretly delivering a different, potentially harmful dose. This kind of tampering could result in life-threatening situations.
Positron Emission Tomography (PET) Scanner
A PET (Positron Emission Tomography) scanner is a nuclear medicine imaging tool used to monitor a patient’s metabolic activity. It works by detecting pairs of gamma rays that are indirectly emitted by a positron-emitting radionuclide (tracer) injected into the body. A computer then processes this data to create detailed three-dimensional images showing the tracer’s distribution within the body.
Since PET scans involve ionizing radiation, patients are exposed to certain radiation levels. The standard radiotracer used in PET scans delivers an effective dose of about 14 millisieverts (mSv). For comparison:
- A chest X-ray exposes a patient to around 0.02 mSv.
- A CT scan of the chest results in exposure of approximately 6.5–8 mSv.
- A combined PET-CT scan can expose a patient to about 23–26 mSv for a person weighing 150 pounds.
This shows that PET and PET-CT scans deliver significantly higher radiation doses compared to other common imaging procedures.
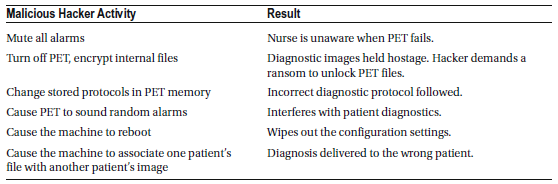
X-ray Computed Tomography (CT) Scanner
A CT scanner, also known as X-ray computed tomography (X-ray CT) or computerized axial tomography (CAT) scan, uses X-ray images captured from various angles to create cross-sectional (tomographic) images or virtual “slices” of specific areas inside a patient’s body. This allows physicians to view internal structures without the need for invasive procedures.
CT scans are classified as moderate- to high-radiation diagnostic tools. The radiation dose from a CT scan is 100 to 1,000 times higher than that of a standard X-ray.
- A typical plain film X-ray delivers a dose of about 0.01 to 0.15 milligray (mGy).
- A standard CT scan can expose organs to 10–20 mGy, while specialized CT scans may reach up to 80 mGy.
Radiation exposure from medical imaging is cumulative, meaning repeated scans increase the overall radiation dose a patient receives, raising the risk of developing cancer. Long-term effects of frequent exposure to ionizing radiation include a heightened risk of leukemia and other types of cancer.
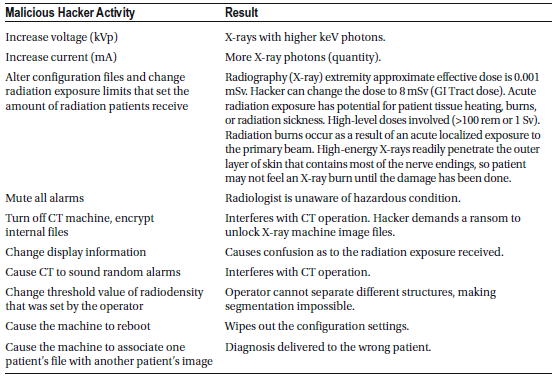
Medical Ventilator
A medical ventilator is a device designed to mechanically assist or fully control a patient’s breathing by moving air in and out of the lungs. These machines often come with monitoring and alarm systems to track patient-specific parameters like pressure, volume, and airflow, as well as the ventilator’s own performance, such as detecting air leaks, power failures, or mechanical malfunctions. Additional safety features may include backup batteries, oxygen tanks, and remote controls for emergency situations.
Modern ventilators use electronically controlled embedded systems to precisely adjust pressure and airflow according to each patient’s unique respiratory needs. Because they are essential for sustaining life, ventilators are classified as life-critical systems. Any malfunction could be fatal, so they are designed with multiple safety features to ensure high reliability, including secure power supplies.
Compared to other medical devices, ventilators are less vulnerable to hacking due to their simpler safety mechanisms. For instance, they are equipped with anti-suffocation safety valves that automatically open if the machine loses power, triggering an alarm in the event of mechanical or software failure. Additionally, ventilators are typically not connected to networks and lack remote web access, meaning that tampering with them would usually require physical access to the device.
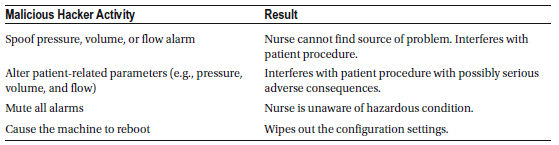
Anesthetic Machine
An anesthetic machine is used to safely administer anesthesia during medical procedures. The most common type is the continuous-flow anesthetic machine, which delivers a precise and steady mixture of medical gases—such as oxygen and nitrous oxide—combined with a controlled concentration of anesthetic vapors like isoflurane. This mixture is delivered to the patient at a regulated pressure and flow rate to ensure safe and effective anesthesia.
Modern anesthetic machines often include additional components such as a ventilator for assisted breathing, a suction unit for airway management, and patient monitoring devices to track vital signs throughout the procedure.
These machines are typically not network-connected and do not support web-based control, which significantly reduces the risk of remote hacking. To tamper with an anesthetic machine, a person would need to have physical access to the device.
Heart-Lung Machine
A heart-lung machine, also known as an extracorporeal circuit (ECC), is a medical device that temporarily takes over the function of the heart and lungs during surgery. It maintains blood circulation and oxygenation while the patient’s heart is stopped, commonly during procedures like cardiopulmonary bypass.
In this process, the patient’s blood is drained by gravity into the machine, where it passes through an artificial lung or membrane oxygenator that oxygenates the blood and removes carbon dioxide. The oxygen-rich blood is then pumped back into the body’s systemic arterial system. To prevent blood clotting during this process, heparin is administered to achieve safe levels of anticoagulation.
Additionally, the machine includes a heat exchanger within the oxygenator. This feature helps manage the blood temperature by compensating for the cooling effect as blood circulates through the ECC and allows the surgical team to intentionally cool or rewarm the patient as needed during surgery.
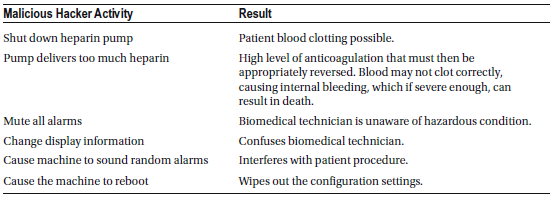
Dialysis Machine
A dialysis machine is designed to replicate many of the kidney’s essential functions by filtering out harmful wastes, excess salt, and fluid from a patient’s blood, restoring it to a healthy balance. To enable this process, a doctor creates a vascular access point in the patient’s blood vessels, allowing the patient to be connected to the machine during hemodialysis sessions. Blood flows through the machine at a preset rate, passing through a specialized filter that removes waste and extra fluids while maintaining the correct balance of important minerals like potassium and sodium. The cleaned blood is then safely returned to the patient.
When used correctly, dialysis machines are highly safe and reliable. While technical failures rarely cause deaths, a significant number of fatal incidents are linked to human error during dialysis treatments.
A dialysis machine consists of two main systems:
- The operative system, which carries out the core dialysis process (e.g., the dialysis proportioning system that manages fluid mixing and filtration).
- The protective system, which continuously monitors for unsafe conditions (e.g., temperature-compensated conductivity monitoring to ensure proper fluid balance).
If the operative system malfunctions, the protective system immediately detects the issue and moves the machine into a “safe state” by:
- Triggering failure alarms
- Stopping the blood pump
- Closing the venous clamp to prevent blood loss
For a dialysis machine to pose a serious safety risk, two independent failures must occur simultaneously. A single failure alone is unlikely to be life-threatening due to the protective safeguards in place. However, two unrelated system failures happening at the same time would create a life-threatening situation, which is considered highly abnormal and not coincidental.
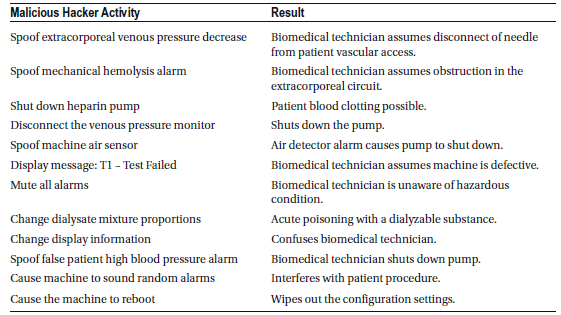
Medical Lasers
Medical lasers are specialized devices that use precisely focused light to treat or remove tissues in various medical procedures, including tumor removal, cataract surgery, breast surgery, cosmetic dermatology, plastic surgery, prostate surgery (prostatectomy), and other surgical interventions. They are also commonly used for vision correction procedures—such as treating nearsightedness, farsightedness, and astigmatism—and in treatments like photodynamic therapy.
As with any surgical procedure, laser surgery carries potential risks, including:
- Incomplete treatment of the targeted condition
- Pain and infection
- Bleeding and scarring
- Changes in skin color (pigmentation issues)
There are many types of medical lasers, but only about a dozen are commonly used in clinical settings. Each laser is designed for specific treatments and carries unique risks if misused.
Laser Safety Hazards
- Beam Hazards: Direct exposure to the laser beam can damage skin or eyes.
- Non-Beam Hazards: Risks from compressed gases, cryogenic materials, and carcinogenic substances used in laser systems.
Most surgical lasers fall under Class IV because they emit high-powered laser radiation designed to alter biological tissue. Improper use, especially of infrared (IR) lasers that generate heat, can cause permanent tissue damage. High-intensity laser procedures also produce laser-generated airborne contaminants (LGAC), which may have mutagenic (mutation-causing) and carcinogenic (cancer-causing) effects.
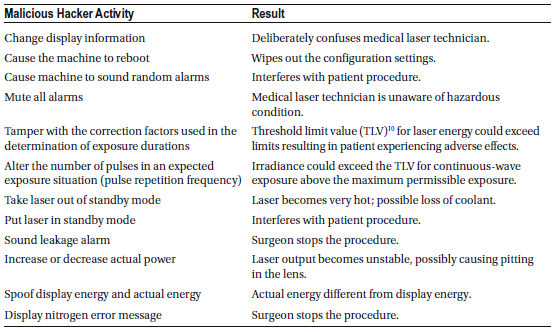
Eye Injury Risks
Different laser wavelengths affect various parts of the eye and can cause severe injury at high power levels. Near-infrared (700nm–1400nm) laser radiation is particularly dangerous because it is invisible to the human eye, and the eye lacks a natural aversion response to this type of radiation. As a result, a patient may not realize they have been overexposed until the injury has occurred.
Factors Influencing Laser Injury Severity
The severity of an injury from laser exposure depends on several factors:
- Wavelength of the laser
- Energy output
- Aperture size (beam width)
- Beam divergence (spread of the laser beam)
- Continuous vs. pulsed emission (constant or intermittent beam)
- Tissue absorption characteristics (how the body absorbs laser energy)
- Exposure conditions (duration of exposure and distance from the source)
These factors determine how damaging the laser can be to skin and eyes, making proper handling and safety measures essential when using medical lasers.
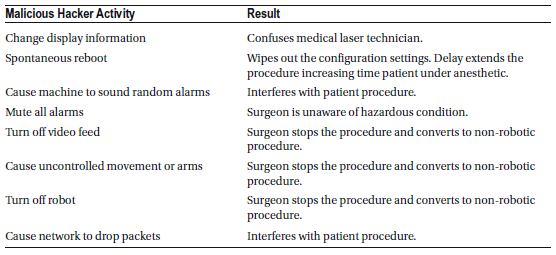
Robotic Surgical Machine
A robotic surgical machine is a sophisticated device designed to assist in various surgical procedures, including those in urology, cardiology, colorectal surgery, gynecology, neurosurgery, and vascular and transplant surgery. This technology is considered minimally invasive, offering benefits like reduced bleeding and shorter hospital stays. Unlike traditional surgery, where the surgeon directly handles instruments, robotic-assisted surgery allows the surgeon to control robotic arms and end-effectors using a live video feed and a computer interface. This setup enables the possibility of remote surgery, where the surgeon can operate from virtually anywhere in the world.
Reliability and Malfunctions
Although robotic surgery is generally effective, its reliability has been inconsistent. A 14-year study by the University of Illinois revealed 8,061 malfunctions in robotic surgical systems in the U.S., resulting in 1,391 injuries and 144 deaths. Reported malfunctions included:
- Uncontrolled movements and spontaneous power cycling, leading to 52 injuries and 1 death.
- Loss of video feed or system errors, causing 41 injuries and 1 death.
- Electrical sparks that unintentionally burned tissue, resulting in 193 injuries.
- Unintended operation of surgical instruments.
Additionally, surgeries were:
- Interrupted and required system restarts in 3.1% of cases.
- Converted to non-robotic procedures in 7.3% of cases.
- Rescheduled in 2.5% of cases.
On average, there were 550 adverse surgical events per 100,000 procedures, based on data from the FDA MAUDE database (2000–2013). However, because this data is self-reported, the true number of incidents may be higher. The study suggests implementing a law to make reporting adverse events to public health authorities mandatory.
Broader Safety Concerns
Robotic safety issues extend beyond surgery. In 2005, the British Health and Safety Executive reported 77 robot-related accidents, highlighting that these machines are complex and require surgeons to undergo specialized training. Surgeons must now focus not only on the surgical procedure but also on potential equipment failures.
Cybersecurity Risks
A growing concern is the risk of cyber-attacks. If a hacker gains control of a robotic surgical machine, it could have life-threatening consequences for patients. This emerging risk underscores the need for stronger cybersecurity measures to protect these critical medical devices.
Medical Device Data Systems ( MDDS)
Medical Device Data Systems (MDDS) are networked hardware or software systems designed to transfer, store, convert formats, and display medical device data. However, they do not modify the data or its display, nor do they control the functions or settings of any other medical device.
Importantly, MDDS devices are not intended for active patient monitoring, which limits their direct interaction with patient care. Due to their passive role, the FDA has reclassified MDDS devices from Class III (high risk) to Class I (low risk), reflecting the belief that these systems pose minimal risk to public health.
Additionally, the FDA does not enforce regulatory compliance for MDDS devices used in specific applications, such as:
- In vitro devices that assess the risk of cardiovascular diseases.
- Devices used for managing diabetes.
Despite being categorized as low-risk, MDDS devices remain vulnerable to hacking due to their networked nature. While they don’t directly control medical devices, unauthorized access could still compromise sensitive medical data or disrupt data flow, potentially impacting patient care indirectly.
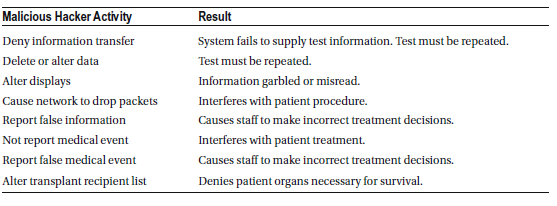
Active Patient Monitoring Devices
Active patient monitoring devices are network-connected medical devices used in hospitals to continuously track a patient’s vital signs and health conditions, requiring immediate responses when critical changes occur. Examples include monitors designed to detect life-threatening arrhythmias like ventricular fibrillation or devices that actively monitor blood glucose levels in diabetes patients for time-sensitive interventions.
Because these devices are networked, they are vulnerable to hacking. If an attacker gains access to an active monitoring system that receives or displays vital information, alarms, or alerts, they could disrupt or disable critical alerts. This interference could prevent timely medical responses to life-threatening conditions, potentially putting a patient’s life in serious danger.
A key example is a nurse telemetry station in an intensive care unit (ICU), which continuously receives and displays real-time data from bedside patient monitors. If this system is compromised, healthcare providers might miss urgent alarms for conditions like cardiac arrest, severe respiratory distress, or other emergencies, delaying life-saving interventions.
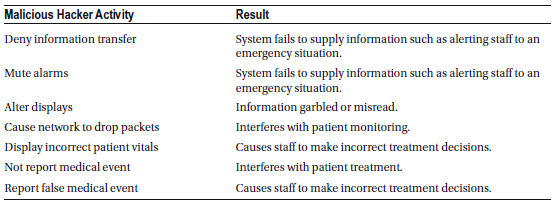
Interoperable Medical Devices
Interoperable medical devices are designed to seamlessly connect and communicate with other networked medical devices and various health information systems. This interoperability is supported by hardware and software that enable the transfer, storage, format conversion, and display of medical data, including medical imaging. These technological advancements have significantly enhanced patient care, particularly by allowing device-specific information—such as unique device identifiers (UDIs) and patient-specific data like electrocardiogram (ECG) waveforms—to be shared across devices or integrated into electronic health records (EHRs). This data exchange improves clinical decision-making and care coordination.
However, when these devices are connected wirelessly or operate over a hospital’s IP-based network, they become vulnerable to cyber-attacks. Hackers could potentially intercept or manipulate data, disrupt device communication, or compromise patient safety.
Real-World Example of a Security Risk
One significant incident involved a software malfunction in an ultrasound system that was part of an integrated platform for intensity-modulated radiation therapy (IMRT). This system is designed to deliver precise radiation doses to tumors while minimizing exposure to healthy tissues. The device was recalled because of a software issue where previous patient measurement data was incorrectly linked to a different patient’s image. This type of error could lead to severe consequences, such as delivering incorrect radiation doses, highlighting the critical risks associated with software flaws in interoperable medical devices.
This example underscores how software vulnerabilities in interconnected medical systems can pose serious threats to patient safety, emphasizing the need for robust cybersecurity measures and strict quality control in medical device software development.
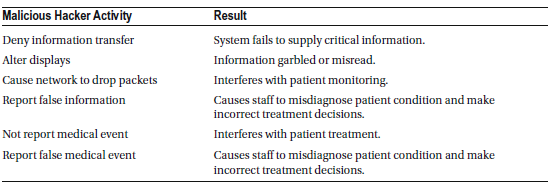
Medical Image Storage Devices
Medical image storage devices are designed to electronically store and retrieve medical images, such as X-rays, MRIs, CT scans, and ultrasound images. These systems play a vital role in modern healthcare by enabling quick and efficient access to critical imaging data for diagnosis and treatment planning.
However, because these devices are often connected to hospital networks or cloud-based systems, they are vulnerable to cyber-attacks. Hackers could potentially access, alter, or delete sensitive medical images, leading to compromised patient care, misdiagnoses, or even the exposure of private health information.
Notably, the FDA does not enforce compliance with key regulatory controls for manufacturers of medical image storage devices. This includes:
- Registration and listing requirements
- Premarket review for safety and effectiveness
- Post-market reporting of device-related issues
- Quality system regulations to ensure manufacturing standards
The lack of strict regulatory oversight increases the risk of security vulnerabilities in these devices, making them attractive targets for cybercriminals. Without proper security measures, unauthorized access to medical imaging data could lead to significant privacy breaches and safety concerns in healthcare settings.
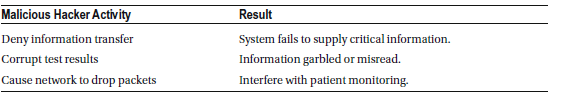
Medical Laboratory
If a hacker gains access to a hospital’s Laboratory Automation System (LAS), they can disrupt vital operations by shutting down critical systems such as fume hoods, refrigerators, biosafety cabinets, and other essential laboratory equipment. This type of attack can severely impact the hospital’s ability to safely handle hazardous materials, store temperature-sensitive samples, and maintain sterile environments.
Additionally, a hacker could:
- Hold archived research data for ransom, threatening the loss of valuable medical research and diagnostic data.
- Crash HVAC systems, disrupting temperature and air quality controls essential for safe laboratory operations.
This poses a significant risk because many laboratories regularly transfer data to the Centers for Disease Control and Prevention (CDC) for national disease surveillance. This data is critical for tracking notifiable disease conditions and is reported weekly by state in the Morbidity and Mortality Weekly Report (MMWR).
A successful cyber-attack on these systems could compromise public health monitoring, delay disease outbreak detection, and hinder responses to health emergencies, potentially impacting national health security.
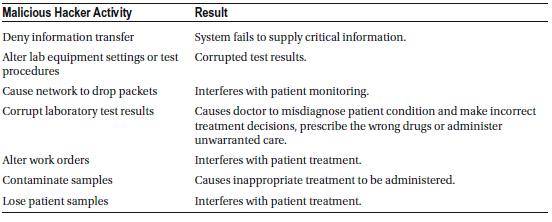
Electronic Health Records (EHR)
Hospitals depend heavily on complex digital systems, including clinical data warehouses, translational bioinformatics, clinical informatics, health information systems, and electronic health records (EHRs) to deliver efficient and accurate patient care. However, these systems are vulnerable to sophisticated cyber-attacks, such as a diagnostic server attack, which can be executed without authentication and with high stealth. This type of attack allows a hacker to perform critical and dangerous actions, including:
- Remote memory dump – Extracting sensitive data from the server’s memory, potentially exposing confidential patient information.
- Remote memory patch – Modifying system memory to alter how the server operates, potentially disabling security features or introducing malicious code.
- Remote calls to functions – Triggering specific system functions that could manipulate data or disrupt operations.
- Remote task management – Gaining control over running processes to interrupt critical hospital functions or introduce malicious programs.
Consequences of a Healthcare Cyberattack
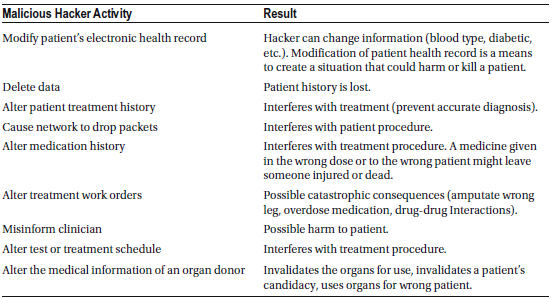
If a hacker gains access to electronic health records (EHRs), they could:
- Alter medical data, causing physicians to misdiagnose patients.
- Manipulate records to prompt doctors to prescribe incorrect medications or administer unnecessary treatments.
- Delete or modify records, causing patients to miss necessary treatments.
Without secure access to EHRs, healthcare providers would be forced to revert to outdated communication methods like phone calls and fax machines, significantly slowing down patient care and increasing the risk of medical errors.
This kind of cyberattack could not only endanger individual patient safety but also undermine the entire hospital’s ability to provide timely and effective healthcare.