This article delves into various network security protocols across different OSI model layers, emphasizing their roles in ensuring secure data transmission and protection against threats like eavesdropping and man-in-the-middle attacks. In this article, we provide the answers for TryHackMe Networking Core Protocols room.
Offensive Security Web Assessor (OSWA) Study Notes
Powershell Study Notes | Learn Powershell Quickly
DNS Protocol Explained
DNS functions at the Application Layer (Layer 7) of the ISO OSI model. By default, DNS traffic utilizes UDP port 53, with TCP port 53 serving as a fallback. While DNS supports various record types, this explanation will focus on the following four:
- A Record: Maps a hostname to one or more IPv4 addresses. For instance,
example.comcan be linked to172.17.2.172. - AAAA Record: Functions similarly to the A record but for IPv6 addresses. The name is “quad-A” (AAAA) to avoid confusion with “AA” or “AAA,” which refer to battery sizes, and “AAA,” which stands for Authentication, Authorization, and Accounting—unrelated to DNS.
- CNAME Record: Maps one domain name to another. For example,
www.example.comcan point toexample.comor evenexample.org. - MX Record: Indicates the mail server responsible for handling emails for a domain.
For example, when you type example.com in your browser, it queries the DNS server for the A record to resolve the domain name to an IP address. However, when sending an email to test@example.com, the mail server queries the DNS server to locate the MX record.
To find the IP address of a domain via the command line, you can use tools like nslookup.
WHOIS Tool Explained
You can register any available domain name for one or more years by paying an annual fee. When registering, you must provide accurate contact information as the registrant. This information is included in WHOIS records, which are publicly accessible. Despite being written in uppercase, WHOIS is not an acronym; it is pronounced “who is.” If you prefer to keep your contact details private, you can use privacy services that conceal your information in the WHOIS database.
To view the WHOIS records of a registered domain name, you can use online lookup services or the whois command-line tool, commonly available on Linux systems. A WHOIS record typically includes details about the domain registrant, such as their name, phone number, email, and address.
HTTPS Protocol Explained
When you launch your browser, you primarily use the HTTP or HTTPS protocols. HTTP stands for Hypertext Transfer Protocol, while HTTPS adds “Secure” functionality, ensuring encrypted communication. These protocols rely on TCP and define how your browser interacts with web servers.
Some common HTTP methods used by your browser when communicating with a web server include:
- GET: Retrieves data from a server, such as an HTML file or an image.
- POST: Submits new data to the server, like submitting a form or uploading a file.
- PUT: Creates a new resource on the server or updates and overwrites existing information.
- DELETE: Removes a specified file or resource from the server.
Typically, HTTP and HTTPS use TCP ports 80 and 443, respectively, but other ports like 8080 and 8443 are also occasionally used.
Using tools like Wireshark, you can analyze the interactions between a web browser (e.g., Firefox) and a web server in detail.
In troubleshooting scenarios, the telnet client is a useful tool for direct communication with a web server. For instance, to connect to a server at MACHINE_IP on port 80, you can manually issue HTTP commands. Sending the following lines:
GET / HTTP/1.1
Host: anything
will request the default page (/). For a specific file like file.html, you would send:
GET /file.html HTTP/1.1
(Some servers may still respond without the Host: header.) This approach allows you to “speak HTTP” directly with the server, making it an effective way to troubleshoot or test server responses.
FTP Protocol Explained
Unlike HTTP, which is optimized for retrieving web pages, File Transfer Protocol (FTP) is specifically designed for transferring files, making it highly efficient for this purpose. Under the same conditions, FTP can achieve higher transfer speeds than HTTP.
Key FTP commands include:
- USER: Enters the username for login.
- PASS: Inputs the password.
- RETR: Downloads a file from the FTP server to the client.
- STOR: Uploads a file from the client to the FTP server.
FTP servers typically listen on TCP port 21 for control commands, while data transfers occur over a separate connection initiated by the client.
Here’s an example session using the ftp command in the terminal:
- Connect to the FTP server: Use the command
ftp MACHINE_IPto initiate a connection to the remote FTP server. - Login: Provide the username
anonymous(no password was required in this case). - List files: Execute the
lscommand to display the available files for download. - Switch mode: Use the
type asciicommand to switch to ASCII mode, suitable for downloading a text file. - Download a file: Retrieve the desired file with the command
get coffee.txt.
This sequence demonstrates how FTP can be used to interact with a remote server for file transfers effectively.
SMTP Protocol Explained
Purpose of NAT:
NAT (Network Address Translation) is designed to allow multiple devices on a private network to access the Internet using a single public IP address, thereby conserving public IP addresses.
Key Idea:
Instead of assigning a unique public IP address to each device in a network (e.g., a company with 20 computers), NAT enables these devices to share one or a few public IP addresses. This significantly reduces the demand for public IP addresses.
Technical Note:
In a network, the number of IP addresses is typically a power of two. For example:
- Without NAT: 32 public IP addresses would be reserved for 32 devices.
- With NAT: Only two public IP addresses are needed (one for NAT and one for backup). This saves 30 public IP addresses.
How NAT Works
- Internal vs. External Networks:
- The internal network uses private IP addresses (e.g., 192.168.x.x, 10.x.x.x, or 172.16.x.x – address ranges not routable on the Internet).
- The external network communicates using public IP addresses assigned by an ISP.
- Address Translation:
- Routers supporting NAT maintain a translation table that maps private IP addresses and their associated ports to the public IP address.
- When a device sends data to the Internet, the router replaces the private source IP and port with the public IP and an assigned port from its pool.
- When the reply arrives, the router uses its NAT table to reverse the translation, delivering the data to the correct internal device.
NAT vs. Traditional Routing
- Routing:
Traditional routing forwards packets based on the destination IP address, assuming every device has a unique IP address. - NAT:
NAT modifies packet headers to translate addresses, requiring the router to track ongoing connections in its translation table. This allows multiple devices on a private network to share a single public IP address.
Benefits of NAT
- IP Address Conservation: Reduces the need for public IP addresses, which are limited in availability.
- Security: Private IP addresses are not directly exposed to the Internet, providing an additional layer of protection.
- Flexibility: Simplifies network management by using a single public IP for multiple devices.
NAT has become a vital technology in networking, especially with the increasing scarcity of IPv4 addresses.
POP3 Protocol Explained
The Post Office Protocol version 3 (POP3) allows an email client to communicate with a mail server to download email messages. While SMTP is used to send emails, POP3 handles receiving them, functioning like checking your physical mailbox for new letters or packages.
Here are some common POP3 commands and their purposes:
- USER <username>: Identifies the user by their username.
- PASS <password>: Authenticates the user by providing their password.
- STAT: Requests the number of messages and their total size in the mailbox.
- LIST: Lists all messages along with their sizes.
- RETR <message_number>: Downloads a specific message from the server.
- DELE <message_number>: Marks a specific message for deletion.
- QUIT: Ends the POP3 session and applies changes, such as deleting marked messages.
With POP3, you can retrieve and manage your emails locally, typically downloading them to your mail client for offline access. This simple protocol ensures efficient retrieval of email messages from the server to the client.
IMAP Protocol Explained
While POP3 is suitable for managing emails on a single device, it falls short when you need to access your email from multiple devices, such as a desktop, laptop, or smartphone. For this, the Internet Message Access Protocol (IMAP) provides a better solution by synchronizing messages across devices.
IMAP ensures that actions such as reading, moving, or deleting messages are reflected across all devices. Unlike POP3, which often deletes emails from the server after downloading, IMAP keeps emails on the server, using more server storage but maintaining synchronization across multiple clients.
Here are some common IMAP commands:
- LOGIN <username> <password>: Authenticates the user.
- SELECT <mailbox>: Selects a specific mailbox folder (e.g., Inbox) to work with.
- FETCH <mail_number> <data_item_name>: Retrieves parts of a message. For example,
FETCH 3 body[]fetches the header and body of message number 3. - MOVE <sequence_set> <mailbox>: Moves specified messages to another mailbox folder.
- COPY <sequence_set> <data_item_name>: Copies specified messages to another mailbox folder.
- LOGOUT: Ends the IMAP session.
IMAP is ideal for users who need consistent email access across multiple devices, ensuring that server-side actions (like message deletion or folder reorganization) are mirrored on all connected devices. This protocol offers greater flexibility and functionality for modern email usage.
TryHackMe Networking Core Protocols | Room Answers
Which DNS record type refers to IPv6?
AAAA
Which DNS record type refers to the email server?
MX
When was the x.com record created? Provide the answer in YYYY-MM-DD format.
1993-04-02
When was the twitter.com record created? Provide the answer in YYYY-MM-DD format.
2000-01-21
Use telnet to access the file flag.html on MACHINE_IP. What is the hidden flag?
THM{TELNET-HTTP}
Using the FTP client ftp on the AttackBox, access the FTP server at MACHINE_IP and retrieve flag.txt. What is the flag found?
THM{FAST-FTP}
Which SMTP command indicates that the client will start the contents of the email message?
DATA
What does the email client send to indicate that the email message has been fully entered?
.
Looking at the traffic exchange, what is the name of the POP3 server running on the remote server?
Dovecot
Use telnet to connect to MACHINE_IP’s POP3 server. What is the flag contained in the fourth message?
THM{TELNET_RETR_EMAIL}
What IMAP command retrieves the fourth email message?
FETCH 4 body[]
Watch Also:
Conclusion
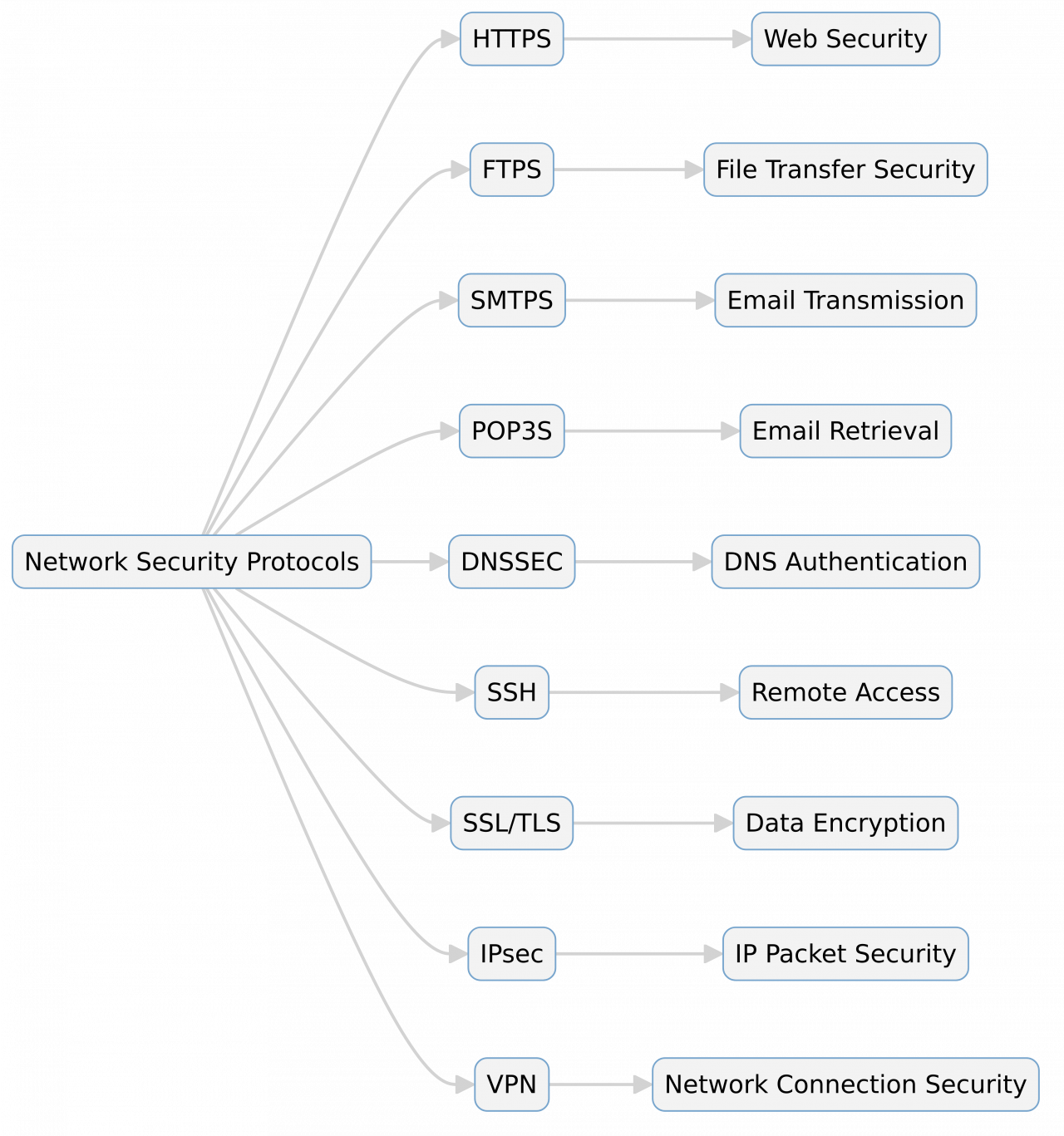
The article provides an in-depth exploration of network security protocols, highlighting their significance in safeguarding data across networks. By implementing protocols such as HTTPS, FTPS, SMTPS, POP3S, DNSSEC, SSH, SSL/TLS, IPsec, and VPNs, organizations can ensure the confidentiality, integrity, and authenticity of their communications. Understanding the functionalities and applications of these protocols is crucial for maintaining robust network security and protecting against various cyber threats.
Summary
- HTTPS Protocol: Hypertext Transfer Protocol Secure (HTTPS) encrypts data between a web server and a browser, ensuring secure communication and protecting against eavesdropping.
- FTPS Protocol: File Transfer Protocol Secure (FTPS) adds Transport Layer Security (TLS) to the traditional FTP, providing encrypted channels for file transfers and enhancing security.
- SMTPS Protocol: Simple Mail Transfer Protocol Secure (SMTPS) wraps SMTP within TLS, encrypting email transmissions and safeguarding against interception and tampering.
- POP3S Protocol: Post Office Protocol 3 Secure (POP3S) secures the retrieval of emails from a server by incorporating TLS encryption, ensuring the privacy of email content.
- DNSSEC: Domain Name System Security Extensions (DNSSEC) authenticate the origin of DNS data and verify its integrity, preventing attacks such as DNS spoofing and cache poisoning.
- SSH: Secure Shell (SSH) provides a secure method for remote login and command execution over an unsecured network, replacing older protocols like Telnet with encrypted communications.
- SSL/TLS Protocol: Secure Sockets Layer (SSL) and its successor, Transport Layer Security (TLS), encrypt data between clients and servers, forming the foundation of secure internet communications.
- IPsec: Internet Protocol Security (IPsec) authenticates and encrypts IP packets, securing data flow across IP networks and establishing virtual private networks (VPNs).
- VPN: Virtual Private Networks (VPNs) use protocols like IPsec to create secure connections over public networks, allowing remote users to access private networks safely.
- Network Security Protocols: Implementing these protocols across various layers of the OSI model is essential for protecting data integrity, confidentiality, and authenticity in network communications.




