In this article, we covered phases of the Cyber Kill Chain as part of the cyber threat intelligence series. The Cyber Kill Chain is one of three major threat intelligence frameworks, alongside the Diamond Model and Unified Kill Chain. It’s emphasized that these are not competing models, but complementary tools to model adversary behavior and plan defenses.
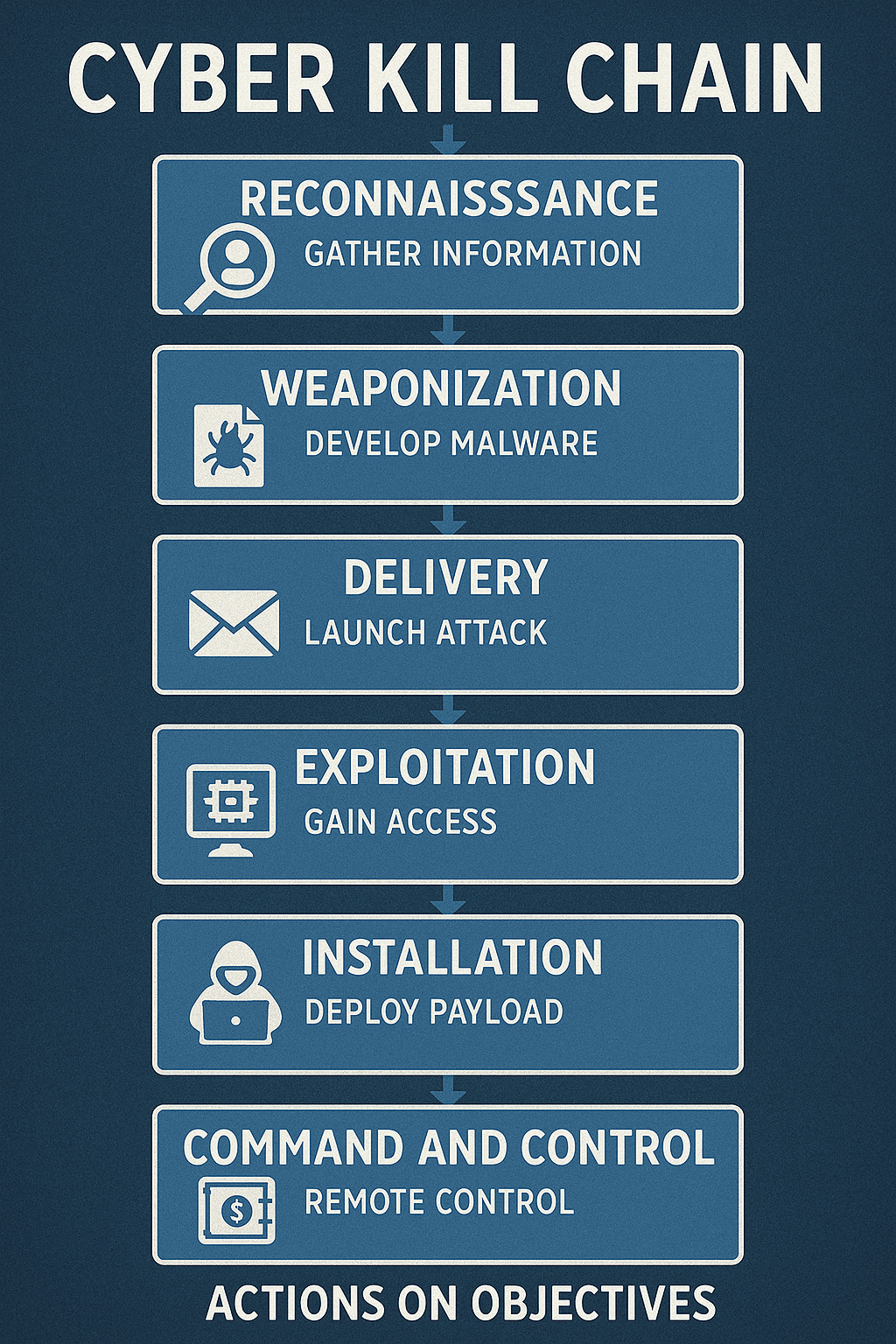
Phase 1: Reconnaissance

This initial stage focuses on intelligence gathering. OSINT (Open Source Intelligence) plays a vital role, with attackers using tools like The Harvester or OSINT Frameworks to collect emails, domain names, and IPs. The process of email harvesting is used as a primary example to show how attackers identify potential victims or network weaknesses.
Phase 2: Weaponization
Here, the attacker builds the actual attack vector. This could be malware, an exploit, or a payload. The differences:
- Malware: A malicious code designed to harm or control systems.
- Exploit: Code that leverages a specific vulnerability.
- Payload: A delivery mechanism carrying the exploit or malware.
An example is embedding malicious macros in Office documents.
Phase 3: Delivery
The delivery phase involves transmitting the weaponized payload to the target. Tactics include:
Watering hole attacks: Compromising legitimate websites to redirect victims.
Social engineering is often the underlying tactic behind these methods.
Phishing emails: Impersonating a trusted source.
USB drop attacks: Leaving infected USBs in public areas.
Phase 4: Exploitation
This is when the attack takes effect. The attacker either uses:
A post-compromise exploit to escalate privileges.
It highlights the importance of patching systems and monitoring for CVEs (Common Vulnerabilities and Exposures).
A pre-existing vulnerability to gain access without delivery.
Phase 5: Installation

Persistence is the goal, attackers install web shells or backdoors to maintain long-term access. These are engineered to:
- Survive reboots or software removal.
- Bypass antivirus tools using obfuscation techniques.
- Utilize ports (e.g., 80 or 443) that typically remain open on firewalls.
Phase 6: Command and Control (C2)
The final stage is the culmination of the attack strategy. Objectives might include:
System sabotage through data encryption (ransomware) or destruction.
The attacker’s intent, espionage, monetary theft, or disruption, is revealed.
Credential dumping for lateral movement.
Data exfiltration for financial or competitive gain.
TryHackMe The Cyber Kill Chain Room Answers
What is the name of the Intel Gathering Tool that is a web-based interface to the common tools and resources for open-source intelligence?
OSINT Framework
What is the definition for the email gathering process during the stage of reconnaissance?
email harvesting
This term is referred to as a group of commands that perform a specific task. You can think of them as subroutines or functions that contain the code that most users use to automate routine tasks. But malicious actors tend to use them for malicious purposes and include them in Microsoft Office documents. Can you provide the term for it?
Macro
What is the name of the attack when it is performed against a specific group of people, and the attacker seeks to infect the website that the mentioned group of people is constantly visiting.
Watering hole attack
Can you provide the name for a cyberattack targeting a software vulnerability that is unknown to the antivirus or software vendors?
Zero-day
Can you provide the technique used to modify file time attributes to hide new or changes to existing files?
Timestomping
Can you name the malicious script planted by an attacker on the webserver to maintain access to the compromised system and enables the webserver to be accessed remotely?
Web shell
What is the C2 communication where the victim makes regular DNS requests to a DNS server and domain which belong to an attacker.
DNS Tunneling
Can you provide a technology included in Microsoft Windows that can create backup copies or snapshots of files or volumes on the computer, even when they are in use?
Shadow Copy
What is the flag after you complete the static site?
THM{7HR347_1N73L_12_4w35om3}




