What is Web Hacking?
Web hacking refers to the practice of exploiting vulnerabilities in websites, web applications, and online services to gain unauthorized access, steal data, or manipulate systems. It is a key concern in cybersecurity, as attackers continuously develop new techniques to compromise web-based platforms.
While some web hacking activities are malicious (cybercriminal attacks), ethical hackers and security researchers also engage in penetration testing to identify and fix security weaknesses before they can be exploited.
Web Hacking & Pentesting Study Notes
Web Hacking & Pentesting Study Notes provides a structured approach to identifying, exploiting, and mitigating vulnerabilities in web applications. It starts with foundational tools like interception proxies and fuzzers, then walks through detailed enumeration strategies and common web application attacks such as SQL/NoSQL injections, XSS, CSRF, IDOR, and others. Each topic is supplemented with hands-on examples, such as using sqlmap to extract data or spawn shells.
Advanced sections include Server-Side Template Injection, JWT manipulation, and insecure deserialization. Overall, it’s both a quick reference and a deep-dive tutorial for effective web penetration testing.
Who Are These Notes For?
- Professionals working in the web application penetration testing area and looking to have a reference for quick access to commands and information.
- Learners who want practical notes on web application penetration testing.
Table of Contents:
- Basic Definitions & Methodology
- Content Enumeration
- Enumerating Web Application Directories
- Common Web Applications Attacks
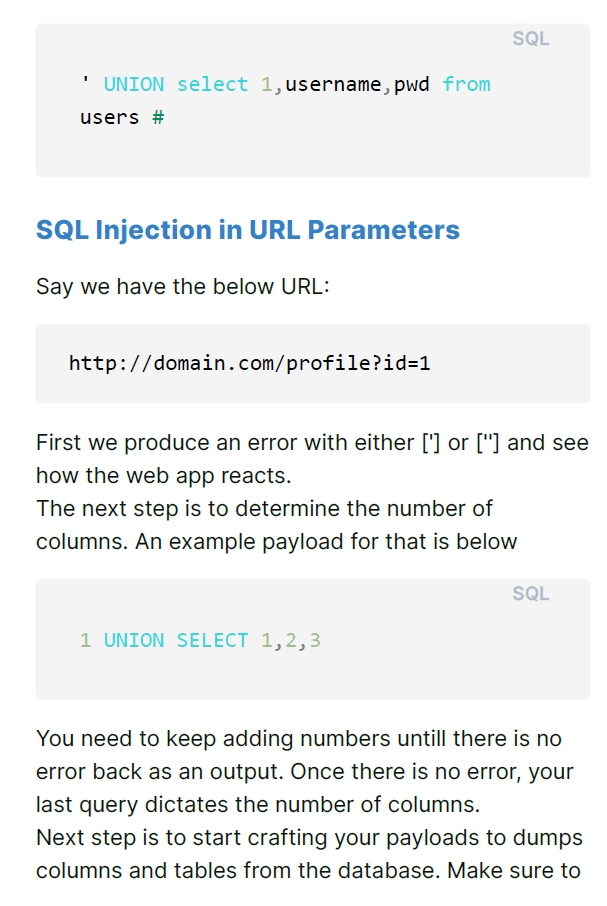
- SQL Injection
- NoSQL Injection
- IDOR
- XML Attacks
- Directory Traversal
- CSRF
- HTML Injection
- Iframe Injection
- File Upload Vulnerabilities
- XSS
- Json Web Token’s (JWTs) Attacks
- SSRF Attacks
- Command Injection
- File Inclusion
- Server Side Template Injection Attacks
- Other Common Web Attacks and Exploits
- Exploiting Authentication Vulnerabilities
- Automated web application scanners
- Online Accounts
Page count: 229
Format: PDF

Testimonials (LinkedIn)
How to buy the web hacking & pentesting study notes
You can buy the book directly by clicking on the button below
After you buy the booklet, you will be able to download the PDF book.
Types of Web Hacking
Web hacking can take many forms, depending on the attacker’s goals and the weaknesses in the target system. Some of the most common types include:
1. SQL Injection (SQLi)
- Attackers inject malicious SQL queries into web applications that use databases.
- Exploits poorly validated user inputs to steal, modify, or delete data from a database.
- Example: Attacking login pages to bypass authentication.
2. Cross-Site Scripting (XSS)
- Injecting malicious JavaScript into a website, which executes on a victim’s browser.
- Used to steal cookies, session tokens, or impersonate users.
- Can be stored (persistent) or reflected (non-persistent).
3. Cross-Site Request Forgery (CSRF)
- Tricks users into performing unintended actions on a web application where they are authenticated.
- Example: A hacker sends a malicious link to a victim, forcing them to unknowingly transfer money or change their password.
4. Remote Code Execution (RCE)
- Attackers exploit vulnerabilities to execute malicious code on a web server.
- Can lead to full system takeover and data breaches.
5. File Inclusion Attacks
- Local File Inclusion (LFI): Attackers include and execute files stored on the server.
- Remote File Inclusion (RFI): Attackers inject a remote malicious script into a vulnerable web application.
6. Brute Force Attacks
- Attackers attempt to guess login credentials by trying multiple combinations of usernames and passwords.
- Often automated using hacking tools like Hydra, John the Ripper, or Burp Suite.
7. Man-in-the-Middle (MITM) Attacks
- Hackers intercept and alter communications between a user and a website.
- Often occurs over unsecured (HTTP) connections or compromised Wi-Fi networks.
8. Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks
- Overloading a website’s server with excessive traffic to make it unavailable to users.
- Uses botnets to send massive traffic and disrupt services.
How Web Hacking Happens
Attackers typically exploit weaknesses in web applications, including:
🔹 Poor input validation (not filtering user input).
🔹 Unpatched software (outdated plugins, libraries, or frameworks).
🔹 Weak authentication (simple passwords, no two-factor authentication).
🔹 Misconfigured security settings (exposed admin panels, open directories).
🔹 Unsecured data transmission (lack of HTTPS encryption).
What about the notes updates?
if you have been watching my YouTube Channel, you definitely know that those who subscribe to the second tier of my channel membership they instantly get access to a vast catalog of cybersecurity, penetration testing, digital marketing, system administration and data analytics notes catalog for 10$ along with the ability to receive all notes updates as long as they are subscribed so what does that mean?
This means if you want to stay up to date with the changes and updates to the notes and get access to other categories, I encourage to join the channel membership second tier instead. However, if you are fine with downloading the current version of this section of the notes then you can buy this booklet instead for a one-time payment.
Will the prices of this booklet change in the future?
Once another version of this booklet is released, which it will, the price will slightly change as the booklet will include more contents, notes and illustrations.
Free Web Hacking & Penetration Testing Training
Checkout the playlist below on my YouTube channel for free Web Hacking & Penetration Testing Training
