This article provides an analysis of the SpyNote Android spyware variant, utilizing the ANY.RUN interactive malware analysis service. SpyNote is presented as a potent threat with extensive capabilities beyond simple spying. These include collecting SMS messages, logging keystrokes, capturing the device screen, and enabling on-device fraud. Notably, it can overlay fake user interfaces, often mimicking banking applications like Deutsche Bank and HSBC, to trick users into revealing credentials.
The malware commonly spreads through phishing SMS messages or bogus websites, sometimes disguising itself as legitimate apps like the Google Play Store or antivirus software. It emerged as a significant threat to financial institutions around 2022.
SpyNote’s Android Malware Emergence and Threat Level
SpyNote first surfaced in 2022 and rapidly became a tool of choice for cybercriminals targeting Android users. Sold on the darknet, it can be deployed by virtually anyone, making it a decentralized threat. By impersonating trustworthy apps like banking and antivirus software, SpyNote lures users into installing it without suspicion.
Social Engineering & Deceptive Tactics
SpyNote Android malware utilizes a blend of deception and urgency to manipulate users into granting it elevated privileges, particularly device administrator rights, which are crucial for its persistence and control over the infected device. Here’s how it achieves this:
1. Disguising as Trusted Applications
SpyNote impersonates apps that users inherently trust—such as:
- Banking apps (e.g., HSBC UK, DBS)
- Antivirus apps (e.g., Avast)
- Google Play Store interfaces
By mimicking these reputable applications with familiar icons and user interfaces, SpyNote gains a layer of visual credibility. Users believe they are interacting with legitimate apps, which reduces suspicion and resistance.
2. Exploiting “Updates” via Smishing
The malware is often introduced through smishing attacks—SMS messages that pretend to be from the user’s bank. These messages claim:
- There is an important security update for their mobile app.
- The update is mandatory to maintain app functionality or prevent account suspension.
The message includes a malicious link that leads users to download the infected APK, believing it’s an official update.
3. Fake Permission Screens and Dialogs
Once installed, SpyNote uses interfaces resembling real system pop-ups to request device administrator access. This often includes:
- Prompts that mimic Android’s native permission dialogs.
- Screens asking users to “activate device admin” under the guise of enabling full functionality or improved security.
4. Persistence After Access
After being granted device admin rights, SpyNote can:
- Prevent easy uninstallation.
- Reinstall itself if the user attempts to remove it.
- Maintain background operations even after a reboot.
This level of access also allows it to initiate additional installations of payloads without the user’s consent or interaction.
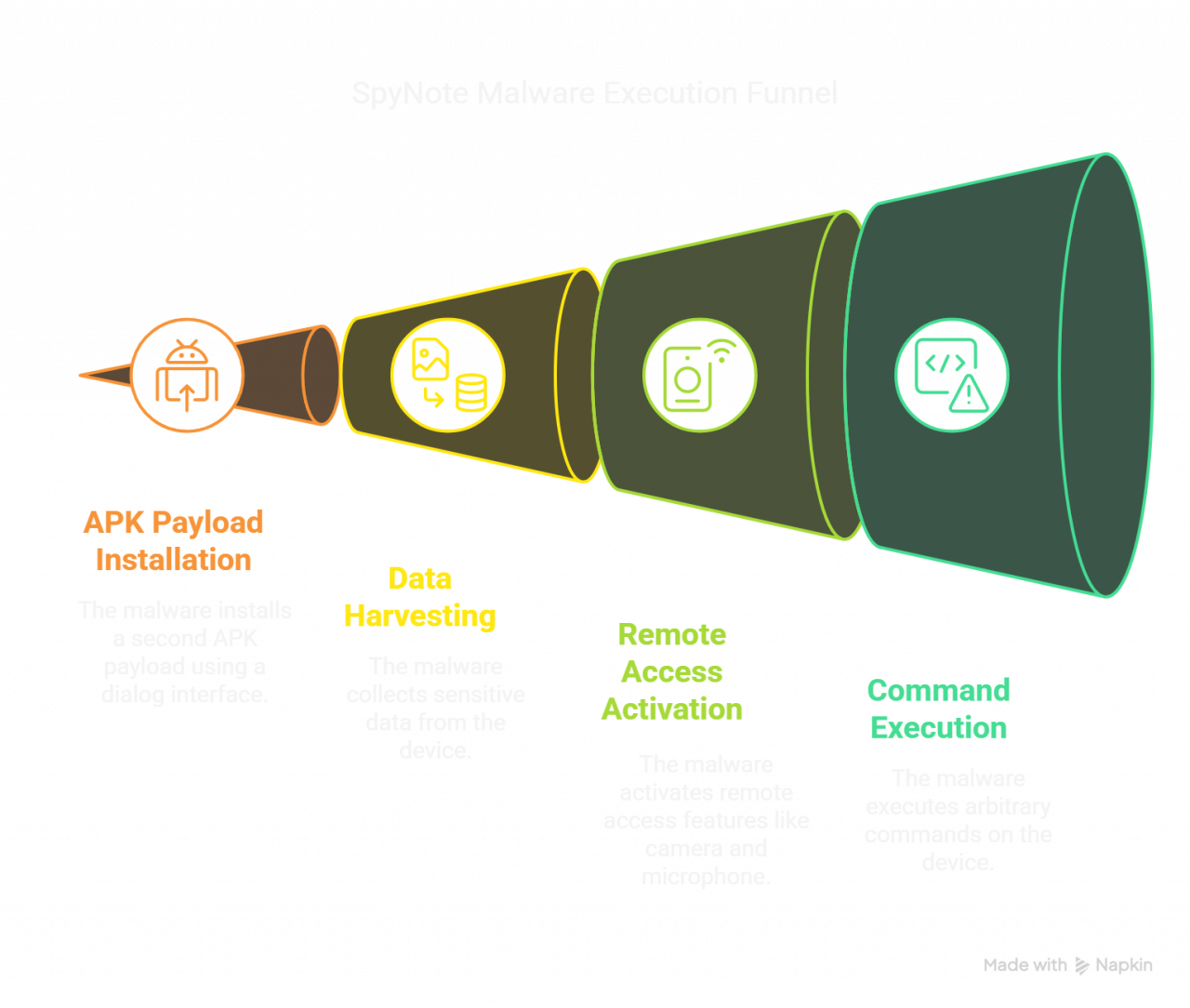
Installation Chain and Dual Payloads
The infection doesn’t stop after the initial download. SpyNote employs a second hidden installation phase, often posing as an update prompt. This second payload runs deeper processes that further embed the malware into the device, making detection and removal much harder.
Deep Dive into Permissions and Capabilities
Once installed, SpyNote requests alarming permissions: sending SMS, accessing contacts, reading call logs, using the microphone and camera, and even bypassing the lock screen. Though some permissions may seem benign on their own, the combination creates a complete surveillance and control tool.
Reverse Engineering Findings
The malware’s Java-based source code reveals classes designed to identify Android phone brands and browsers, indicating a broad targeting strategy. Methods such as sendSMS, readScreenText, and checkPassword prove its intentions to gather sensitive user information through both passive (screen reading) and active (keystroke logging) methods.
ANY.RUN Dynamic Malware Analysis Walkthrough
In a controlled environment, the malware was analyzed using ANY.RUN’s Android 14 simulation. It exhibited malicious behaviors like re-installation attempts, background activity, and connections to known malicious IPs. Processes like app_process64 and the ART runtime service showed elevated privileges and installation of background payloads.
ANY.RUN provides a live, interactive Android 14 simulation where the malware is executed just like it would be on a physical device. This allows researchers to:
- Watch how the malware installs and operates.
- Observe user interface behavior as if on a real phone.
- Interact with the malware manually by clicking buttons and navigating screens.
This is especially useful because SpyNote behaves differently based on user interactions, including prompts for permissions and device admin access.
Through ANY.RUN, the following behaviors were clearly exposed:
- App_Process64 was flagged for dynamically registering broadcast receivers and initiating background APK installations.
- It revealed the two-stage installation process, where the initial app acts as a dropper for the second malicious payload.
ANY.RUN flagged these as anomalous behaviors—difficult to detect through static analysis alone.
Malicious IPs and Domain Connections
The malware connects to at least three suspicious endpoints, including dimitex.net and toomdc.net, which were flagged during analysis. It also interacts with IP addresses previously involved in other malicious activities, confirming SpyNote’s use in active cyber campaigns.
Cryptocurrency Theft Capabilities
💳 1. Impersonation of Banking Applications
SpyNote has been seen mimicking several real banking apps, including:
- HSBC UK
- DBS Digibank
- Other international financial institutions
These fake apps are nearly indistinguishable from the originals in design, fooling users into entering their banking credentials into the malware.
📬 2. Harvesting Financial Data via Permissions
Once installed and granted permissions, SpyNote harvests:
- SMS messages (to intercept OTPs or 2FA codes)
- Call logs and contacts (to identify communication patterns)
- Keystrokes (capturing credit card numbers and passwords entered via the keyboard)
- Screen content (reading on-screen financial data from apps like WhatsApp, Messenger, or even banking UIs)
These abilities turn the phone into a digital surveillance device focused on financial behavior.
🪙 3. Targeting Cryptocurrency Wallets
The malware contains specific functions that go beyond traditional banking:
- Binance and Bitcoin Wallets: It has dedicated methods to detect if crypto wallets like Binance or Bitcoin clients are installed.
- Private Keys & Balances: Once identified, the malware attempts to extract private keys, monitor transactions, and read wallet balances.
- Stealthy Enumeration: It silently checks for wallet apps and accesses their stored sensitive information.
The malware’s Java source code explicitly includes methods such as:
binance_ing()– Enumerates crypto wallets.check_if_get_bitcoin()– Identifies if Bitcoin wallets are active and retrieves their balances.
🌐 4. Data Exfiltration to Command and Control (C2) Server
After stealing data:
- The malware pings its C2 server to ensure connectivity.
- Then exfiltrates all collected information—credit card details, bank login info, crypto keys—to the malicious server for further use or sale.
This systematic theft cycle enables cybercriminals to not only gain access to sensitive accounts but also potentially drain crypto wallets directly.
Command and Control Communication (C2)
SpyNote uses ping commands to establish server connectivity before exfiltrating harvested data. This step confirms its linkage to a C2 server for real-time commands and data dumps, posing a continuous threat to compromised devices.
Security Recommendations and User Defense
Users are strongly urged to install apps only from trusted sources like Google Play or Apple Store. Unsolicited messages prompting app updates should be ignored. Critical settings such as blocking installations from unknown sources and disabling unnecessary permissions are essential defenses.




