This article kicks things off by explaining that this isn’t a deep dive or an advanced cryptography course or class. It’s more of a practical, beginner-friendly guide to help folks get started in cybersecurity. The video blends modern encryption methods with older, historical ones and walks through live examples using TryHackMe labs including TryHackMe Cryptography basics, TryHackMe Public Key cryptography and TryHackMe Hashing.
Core Definitions in Cryptography
To build a solid base, the video explains key terms:
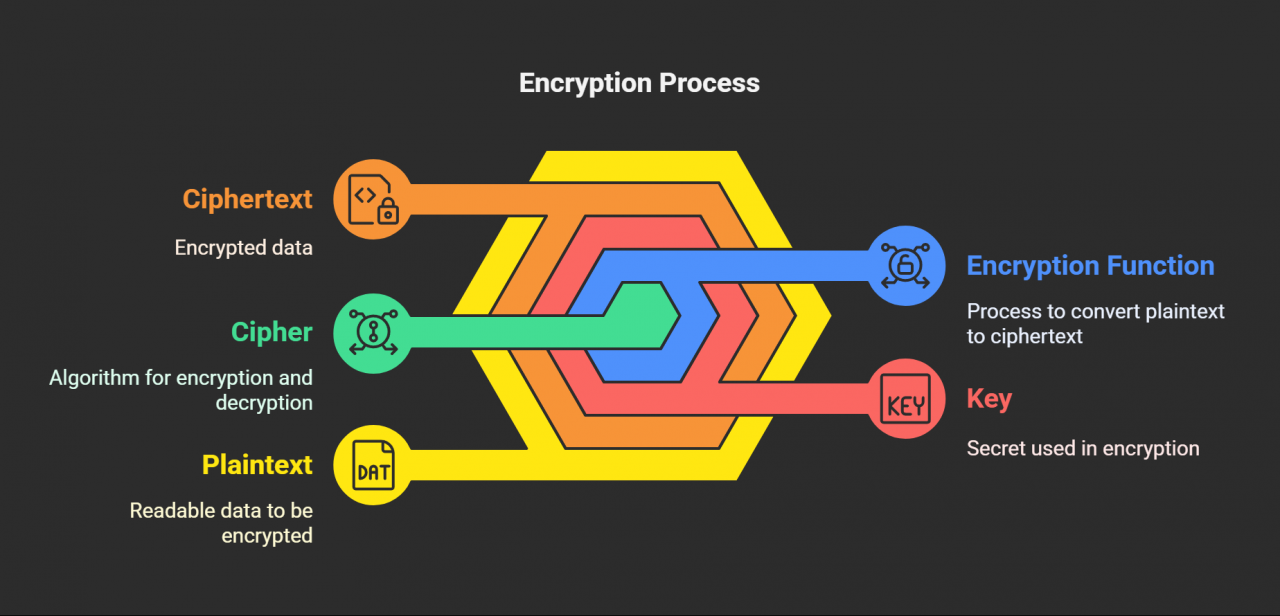
Key: A secret code needed to turn the scrambled message back into something readable. Without the key, the cipher’s useless.
Plaintext: The original message. Something you can read, like an email or note.
Ciphertext: What the message looks like after it’s scrambled by encryption.
Cipher: The formula used to mess with the message—like AES or others.
Classical Ciphers and Why They’re Weak
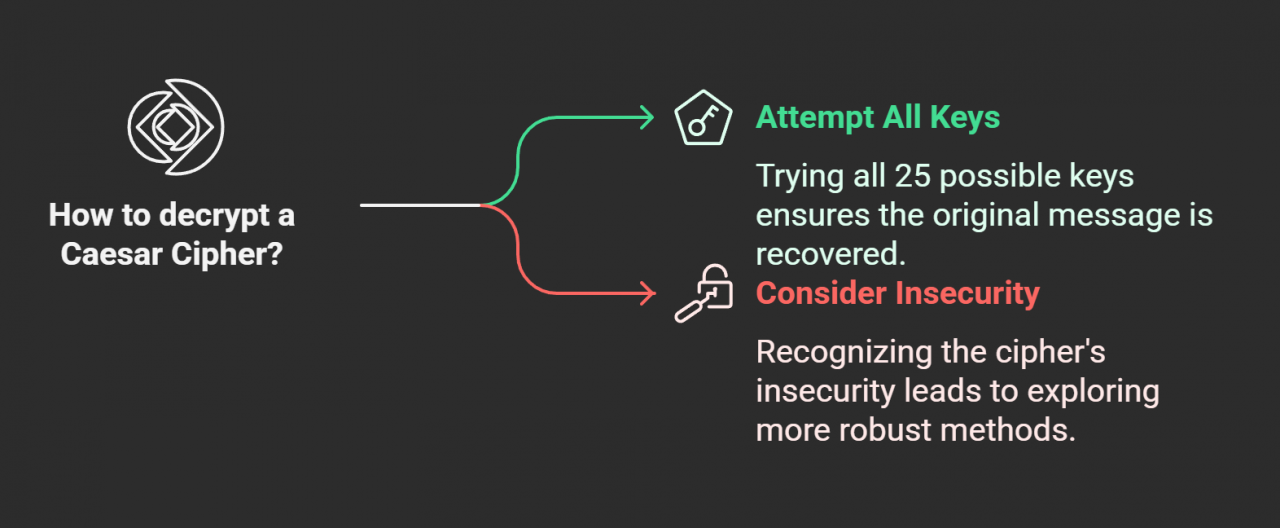
The Caesar Cipher gets used as an example here. It’s a very old trick where each letter shifts forward by a set number. To decode, you shift the other way. Easy to break, though—only 25 possible keys in English. Anyone could try them all quickly.
How Symmetric Encryption Works
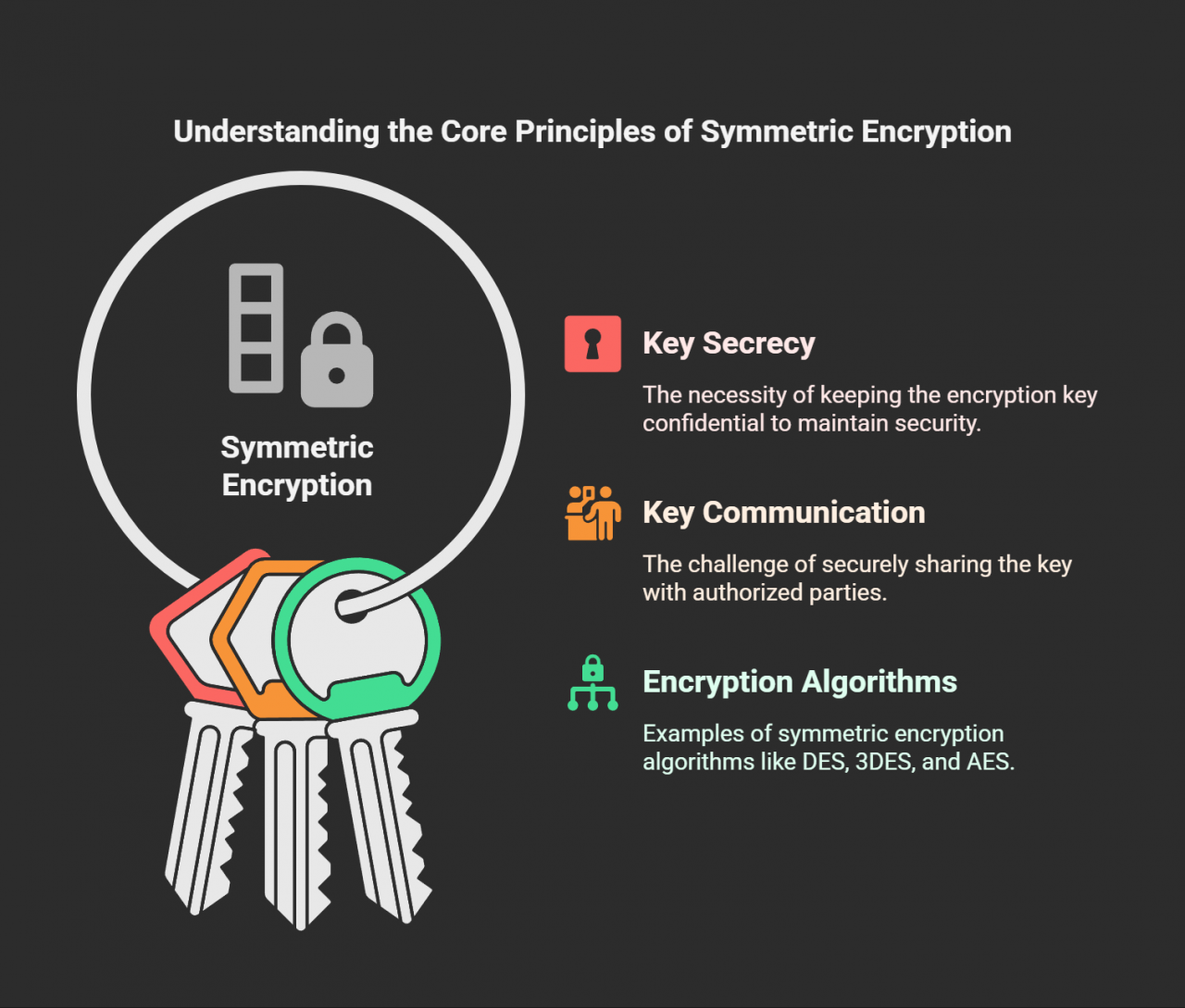
This method uses one key to lock and unlock. That’s handy, but risky too—how do you share that one key safely?
DES/3DES: Outdated, mostly retired now.
Examples: DES, 3DES, and AES.
AES: Still strong today, with longer key options.
Asymmetric Encryption: Stronger but Slower
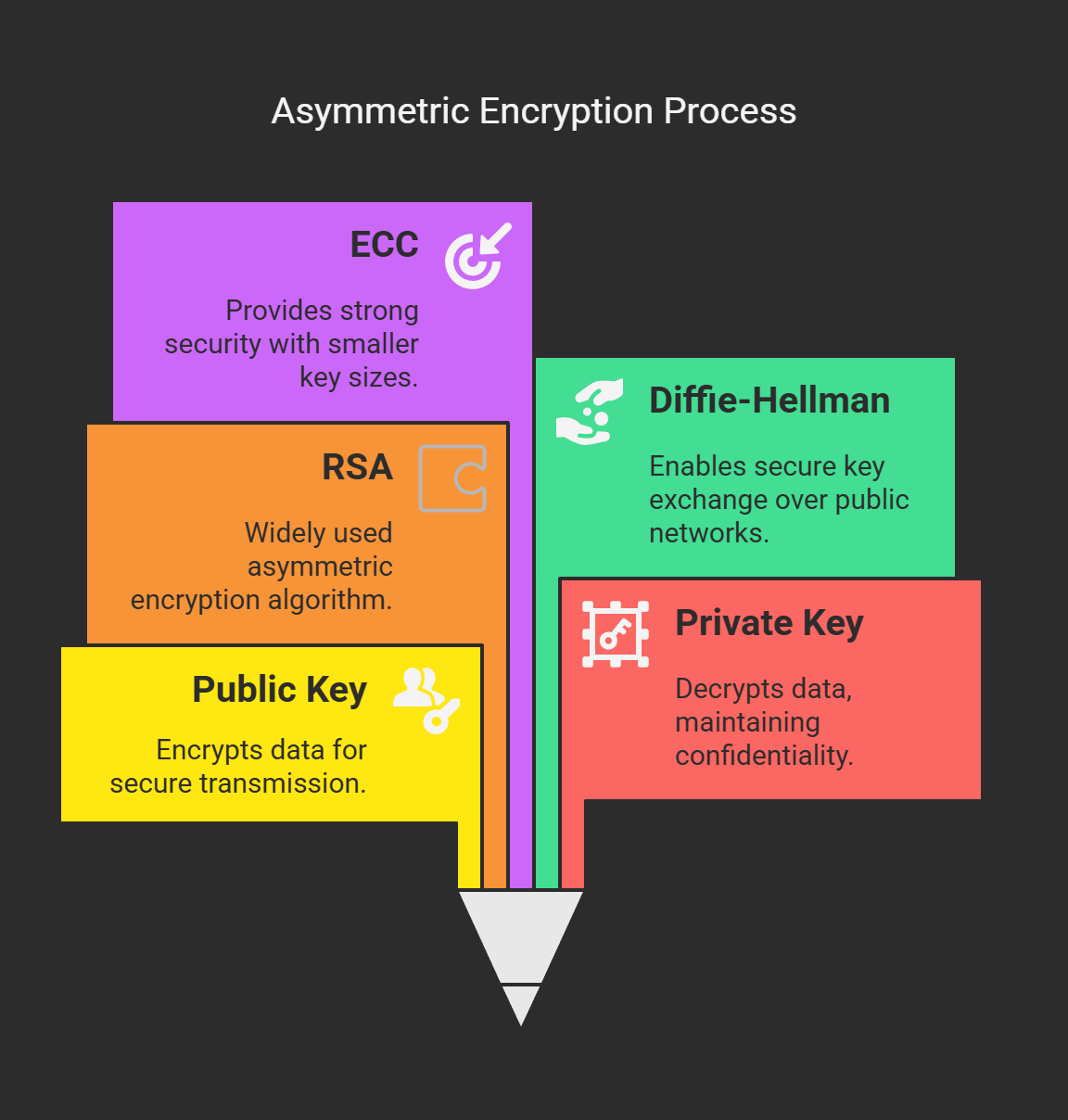
Here, two keys get used—a public one and a private one. One scrambles the message, the other unscrambles it.
Diffie-Hellman: Mainly helps with swapping keys in a safe way.
RSA: Old-school and secure but runs slow because of big keys.
ECC: Does the same job with smaller keys.
Math That Makes It All Work
XOR: A math operation used in encryption; it flips bits based on whether they match.
Modulo: Used to find remainders—critical when making asymmetric keys.
Diffie-Hellman Key Exchange in Real Life
Here’s how it goes down:
- Both sides agree on two public values (P and G).
- Each person picks a private number.
- They do some math to make public keys.
- They swap keys.
- Then use those to get to a shared secret. That shared secret? Never actually sent.
SSH Keys and Server Access
Asymmetric encryption powers SSH too. When you connect to a server for the first time, you see a fingerprint. Accept it, and next time your computer checks it quietly.
- You can make SSH keys on your machine.
- The server keeps a copy of your public key in a file called
authorized_keys. - Make sure your file permissions are set right or SSH won’t work.
Digital Signatures Make Things Trustworthy
Here’s the idea:
- Bob signs a document by encrypting its hash with his private key.
- Alice checks it by using Bob’s public key.
- If everything matches, she knows Bob signed it and it hasn’t been changed.
This works kind of like HTTPS certificates, which prove websites are legit thanks to trusted authorities.
Encrypting and Signing with GPG
You can set an expiration date and a passphrase to protect the key.
You can make your own keys.
Encrypt and decrypt files easily.
Encrypted files usually end in .gpg.
Hashing for File Integrity
Hashing creates a fingerprint for files. A small change in the file creates a totally different hash. You can’t reverse it back to the original file—hashing’s only for checking things, not hiding them.
- Good Hashes: SHA256.
- Weak Hashes: MD5 and SHA1—they’ve got flaws and can collide, meaning two different files might share the same hash.
TryHackMe exercises give you hands-on practice using hashes to verify files and learn how it works.
RSA Encryption Explained
RSA encryption sits at the center of asymmetric cryptography—it’s all about using two keys that work together but do different things. Here’s the breakdown of how it keeps your secrets safe.
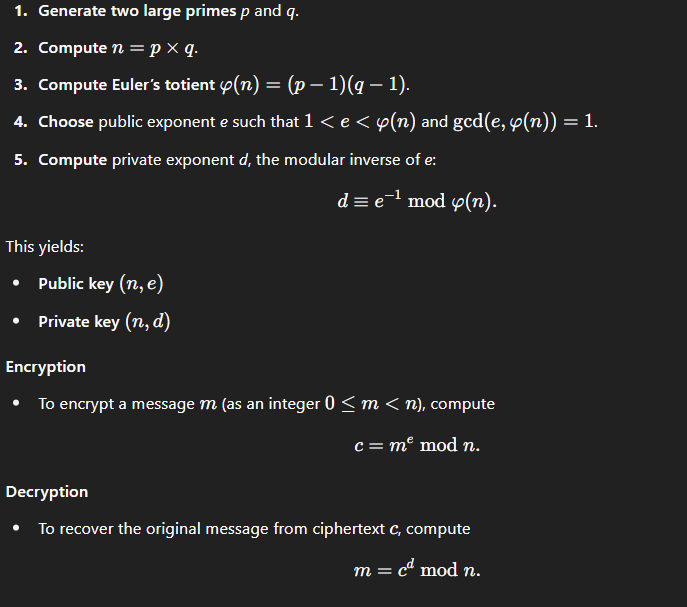
Encrypt with Public, Decrypt with Private
Let’s say Alice wants to send Bob a message. She uses Bob’s public key to scramble the message. That public key? It’s out there for anyone to use—no harm in sharing it.
But here’s the trick: once that message’s encrypted, only Bob’s private key can unlock it. That private key is his and his alone. It stays hidden. Always.
Why This Works
Even if someone grabs the scrambled message while it’s traveling through the internet—even if they’ve got Bob’s public key and know RSA like the back of their hand—they still can’t read it. Why? Because cracking RSA means solving a seriously hard math problem. The kind that would take current computers way too long to figure out.
The Math Behind It
RSA depends on how hard it is to break down huge numbers into their prime parts. You multiply two giant primes to make a number that goes into the public key. That’s easy. But going backward—figuring out the original primes from that big number? Takes forever without the right tools. That’s what keeps the private key safe.
So bottom line? RSA lets people share information out in the open without risking privacy. Encrypt with the public key. Only the matching private key can open it. Simple in concept. Super secure in practice.
TryHackMe Cryptography Basics Room Answers
What is the standard required for handling credit card information?
PCI DSS
What do you call the encrypted plaintext?
ciphertext
What do you call the process that returns the plaintext?
decryption
Knowing that XRPCTCRGNEI was encrypted using Caesar Cipher, what is the original plaintext?
ICANENCRYPT
Should you trust DES? (Yea/Nay)
Nay
When was AES adopted as an encryption standard?
2001
What’s 1001 ⊕ 1010?
0011
What’s 118613842%9091?
3565
What’s 60%12?
0
TryHackMe Public Key Cryptography Basics Room Answers
In the analogy presented, what real object is analogous to the public key?
Lock
Knowing that p = 4391 and q = 6659. What is n?
29239669
Knowing that p = 4391 and q = 6659. What is ϕ(n)?
29228620
Consider p = 29, g = 5, a = 12. What is A?
7
Consider p = 29, g = 5, b = 17. What is B?
9
Knowing that p = 29, a = 12, and you have B from the second question, what is the key calculated by Bob? (key = Ba mod p)
24
Knowing that p = 29, b = 17, and you have A from the first question, what is the key calculated by Alice? (key = Ab mod p)
24
Check the SSH Private Key in ~/Public-Crypto-Basics/Task-5. What algorithm does the key use?
RSA
What does a remote web server use to prove itself to the client?
Certificate
What would you use to get a free TLS certificate for your website?
Let’s Encrypt
Use GPG to decrypt the message in ~/Public-Crypto-Basics/Task-7. What secret word does the message hold?
Pineapple
TryHackMe Hashing Basics Room Answers
What is the SHA256 hash of the passport.jpg file in ~/Hashing-Basics/Task-2?
77148c6f605a8df855f2b764bcc3be749d7db814f5f79134d2aa539a64b61f02
What is the output size in bytes of the MD5 hash function?
16
If you have an 8-bit hash output, how many possible hash values are there?
256
What is the 20th password in rockyou.txt?
qwerty
Manually check the hash “4c5923b6a6fac7b7355f53bfe2b8f8c1” using the rainbow table above.
inS3CyourP4$$
Crack the hash “5b31f93c09ad1d065c0491b764d04933” using an online tool.
tryhackme
Should you encrypt passwords in password-verification systems? Yea/Nay
Nay
What is the hash size in yescrypt?
256
What’s the Hash-Mode listed for Cisco-ASA MD5?
2410
What hashing algorithm is used in Cisco-IOS if it starts with $9$?
scrypt
Use hashcat to crack the hash, $2a$06$7yoU3Ng8dHTXphAg913cyO6Bjs3K5lBnwq5FJyA6d01pMSrddr1ZG, saved in ~/Hashing-Basics/Task-6/hash1.txt.
85208520
Use hashcat to crack the SHA2-256 hash, 9eb7ee7f551d2f0ac684981bd1f1e2fa4a37590199636753efe614d4db30e8e1, saved in saved in ~/Hashing-Basics/Task-6/hash2.txt.
halloween
Use hashcat to crack the hash, $6$GQXVvW4EuM$ehD6jWiMsfNorxy5SINsgdlxmAEl3.yif0/c3NqzGLa0P.S7KRDYjycw5bnYkF5ZtB8wQy8KnskuWQS3Yr1wQ0, saved in ~/Hashing-Basics/Task-6/hash3.txt.
spaceman
Crack the hash, b6b0d451bbf6fed658659a9e7e5598fe, saved in ~/Hashing-Basics/Task-6/hash4.txt.
funforyou
What is SHA256 hash of libgcrypt-1.11.0.tar.bz2 found in ~/Hashing-Basics/Task-7?
09120c9867ce7f2081d6aaa1775386b98c2f2f246135761aae47d81f58685b9c
What’s the hashcat mode number for HMAC-SHA512 (key = $pass)?
1750
Use base64 to decode RU5jb2RlREVjb2RlCg==, saved as decode-this.txt in ~/Hashing-Basics/Task-8. What is the original word?
ENcodeDEcode



