We demonstrated how password spraying and ASREP roasing attacks work agaisnt Windows Active Directory. ASREP Roasting is an attack that targets Kerberos and aims to extract valid users along with their ticket granting ticket. On the other hand, password spraying works by attempting to authenticate a password against a list of valid users. In both cases, the attacker will at least reach a valid pair of credentials to use it in order to login as the user to their active directory machine. Kerbrute and Impacket are popular tools to simulate these attacks against Windows active directory.
Windows Active Directory Penetration Testing Study Notes
What is Kerberos ASREP Roasting in Windows Active Directory?
ASREP ROASTING
Definition of ASREP Roasting
ASREP Roasting is a type of attack that involves an attacker impersonating an authentication request (requesting a ticket for the target user) for a user that has Kerberos pre-authentication feature not enabled or configured. Pre-authentication requires the client to prove its identity before the Kerberos Key Distribution Center will issue a ticket.
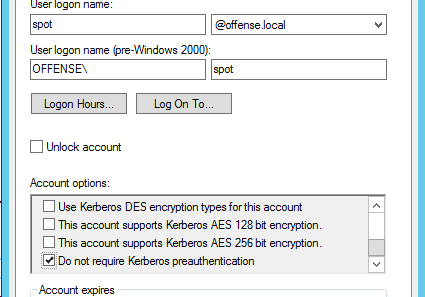
ASREP Roasting Impact
When an attacker targets a user whose user properties are not configured with Kerberos pre-authentication, the KDC or key distribution center will respond to the authentication request with the a ticket that is encrypted with the user’s password hash which when acquired by the attacker can lead to hash cracking attacks.
Commands and scenarios
Getting password hashes and TGTs for identified users in the previous Kerebros enumeration.
<root@kali:python3 GetNPUsers.py -dc-ip [ip] pentesting.local/ -usersfile [list-of-found-users-from-command-above]>What is Password Spraying Attack?
Since most AD environments have account lockout configured, we won’t be able to run a full brute-force attack. Instead, we need to perform a password spraying attack. Instead of trying multiple different passwords, which may trigger the account lockout mechanism, we choose and use one password and attempt to authenticate with all the usernames we have acquired. However, it should be noted that these types of attacks can be detected due to the amount of failed authentication attempts they will generate.
If you have been provided a list of usernames such as users.txt and you know from your enumeration and OSINT campaigns that some users’ password could be password123. Although users should always change their initial password, we know that users often forget.
[1]
/kerbrute_linux_amd64 passwordspray -v -d pentesting.local –dc [ip] [users.txt] password123python3 /usr/share/doc/python3-impacket/examples/lookupsid.py anonymous@10.10.171.0 | tee usernames>python kerbrute.py -domain pentest.htb -dc 10.10.11.3 -t 100 -users /home/kali/Desktop/users.txt -passwords /home/kali/Desktop/password.txt
ASREP Roasting vs Kerberoasting
In Kerberos, AS_REP Roasting occurs during the first authentication process. It is abuse of the fact that the encrypted timestamp (including the user’s password hash) that is ordinarily required at the beginning of an account is not necessary if the account has the option Do not require Kerberos preauthentication set. Consequently, any user on the network who is aware of the name of an impacted account can request that the KDC authenticate as that user in order to obtain an AS_REP answer, which is partially encrypted using the password hash of the roastable AS_REP account. After obtaining the credentials, an attacker may attempt to crack the hash offline and retrieve the cleartext version.
Asking for service tickets for network services where SPNs are linked to user accounts rather than computer accounts is the goal of kerberoasting. The background is that when someone establishes a user, he or she will probably select a password based on human standards, such as a phrase, a term that contains several digits, etc. It is feasible to decipher the hash and obtain the cleartext credentials if the password was chosen poorly.
When a user requests access to a network service, the TGS will send them a data package containing a service ticket. This ticket is encrypted using the password hash of the service account and, similar to the AS_REP roasting attack, can be cracked offline.
Detection Methods for the AS-REP Roasting Attack
Event ID 4738 – A user account was changed.
For example, the Event ID 4738 is generated during this type of attack. The details for this event, which include the Ticket Encryption Type (0x17), Ticket Options (0x40800010), and Service Name (krbtgt), indicate a request for a Kerberos authentication service ticket. Given that this event is generated when the attacker manipulates domain objects, the presence of these parameters in the event logs may suggest the occurrence of an AS-REP Roasting attack [3].
Event ID 5136 – A directory service object was modified.
Keeping an eye on Event ID 5136, which offers details on modifications made to user accounts in a Windows system, is an additional choice. Any user accounts with modified Kerberos preauthentication settings can be found by looking through the logs from this event.
AS-REP Roasting Attack Mitigation
Finding and activating all user accounts that are configured to accept Kerberos pre-authentication is the best defense against AS-REP Roasting attacks.
Get-ADUser -Filter * -Properties DoesNotRequirePreAuth | Where-Object {$_.DoesNotRequirePreAuth -eq $True -and $_.Enabled -eq $True} | Select-Object 'SamAccountName','DoesNotRequirePreAuth' | Sort-Object 'SamAccountName'
The script retrieves the pre-authentication data for each account by using the ‘DoesNotRequirePreAuth’ property in the ‘Properties’ parameter, and it finds all user accounts using the Get-ADUser cmdlet using a filter.
Following a pipe to the Where-Object cmdlet, the output of the Get-ADUser cmdlet is filtered to only contain accounts where ‘Enabled’ and ‘DoesNotRequirePreAuth’ are equal to $True. After filtering the results, the ‘SamAccountName’ and ‘DoesNotRequirePreAuth’ properties for each account are chosen by the Select-Object cmdlet. Ultimately, the results that have been chosen are sent to the Sort-Object cmdlet, which uses the ‘SamAccountName’ property to sort the results.
Full Video





