In this post, we demonstrated and covered the solution to HackTheBox Runner machine which involves basic enumeration, exploitation of two web applications namely, TeamCity and Portrainer.io, and SSH local port forwarding.
Blue Team Cyber Security & SOC Analyst Study Notes
HackTheBox Runner Machine Synopsis
Runner is a medium difficulty Linux box that contains a vulnerability ([CVE-2023-42793](https://nvd.nist.gov/vuln/detail/CVE-2023-42793)) in `TeamCity`. This vulnerability allows users to bypass authentication and extract an API token, which can be used to enable debug features for executing system commands. By gaining access to a `TeamCity` docker container and compressing the `HSQLDB` database files, we can extract credentials for the user `matthew` and find an `SSH` key for `john`. After cracking the password, we can authenticate on the host filesystem. Upon inspecting the `/etc/hosts` file, we discover a running `Portainer` instance. Using `matthew's` credentials, we access the subdomain externally. While authenticated, we find that we can create images, but our privileges are limited. After checking the version of `runc` on the host, we exploit a vulnerability ([CVE-2024-21626](https://nvd.nist.gov/vuln/detail/CVE-2024-21626)) through the image build function of `Portainer`, which allows us to create a SUID bash file on the host.
Before you start
Add the machine dns name to your hosts file:
echo "10.10.11.13 runner.htb" | tee -a /etc/hosts
Information Gathering and Scanning with Nmap
With nmap, we can scan the machine with below commnand:
nmap -sCV -p- -T4 10.10.11.13 --open -oN Fullnmap
Open ports found:
- 8000
- 22 SSH
- 80 HTTP
Services Enumeration
It should be noted that nothing can be found enumerating ports 80 and 8000 using the web interface.
Creating a wordlist with Cewl
We use the main web page to create a wordlist in order to perform tailored enumeration later on.
cewl http://runner.htb/ | grep -v CeWL > custom-wordlist.tx
Using Gobuster to enumerate virtual hosts
Enumerating virtual hosts, after knowing that you have come up with no fruits enumerating the main host, comes in handy in some situations:
gobuster vhost -w custom-wordlist.txt -u http://runner.htb --append-domain

Having found a virtual host, we proceed and add it to the host file:
echo "10.10.11.13 TeamCity.runner.htb" | tee -a /etc/hosts
Accessing the virtual host;
mpted to change the password.
TeamCity Admin Account Creation CVE-2023-42793
TeamCity is an advanced CI/CD solution that allows for flexible workflows, collaboration, and development practices. Use TeamCity to speed up the delivery of your software in the most cost-optimal way, with any tech stack, at any scale.
Since the version of this web software has become known, we can attempt to exploit using this exploit from exploit-db:
Exploiting TeamCity Admin with the below command:
python exploit.py -u http://teamcity.runner.htb
Initial SSH Shell Using TeamCity Admin Exploit CVE-2023-42793
The dashboard of TeamCity is shown in the below figure:
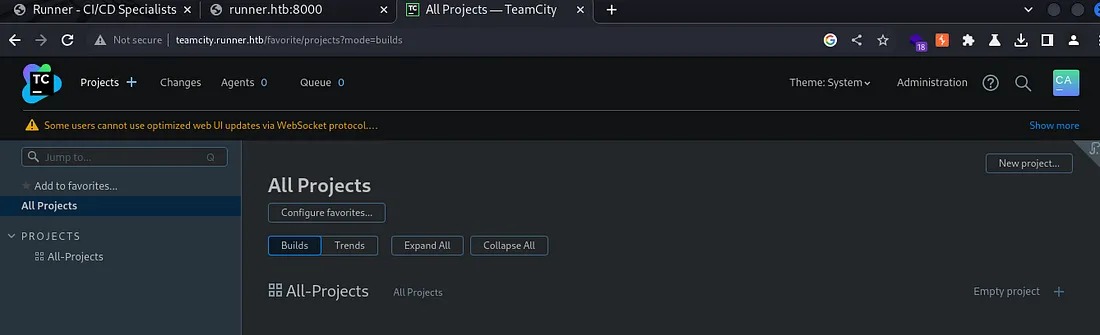
To get a reverse shell working, go to Administration—>Server Administration and select the Backup tab.
Click on “start backup”, download the zip file and once downloaded unzip it and you will find an “id_rsa” SSH private key.
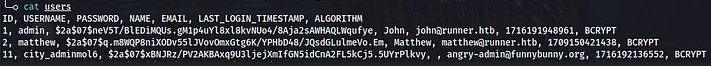
Also you will find a directory named “database_dump” which contains a file named “users” that stores users and hashes
Cracking password hashes with JohnTheRipper
After saving the users and hashes in a file, we can use the below command to crack as much hashes as possible.
john hash --wordlist=/usr/share/wordlists/rockyou.txt
The putput of the above command will result in the hash of “Mathew” users being cracked to give the plain text password “piper123“
SSH Access Using Cracked Hashes
Now that we have a private SSH key, username and a password, we can login through SSH. We will use the user “john” from the users file:
ssh -i id_rsa john@10.10.11.3
Linux Privilege Escalation
As always being stated in this blog, Linux privilege escalation can be started through automated or manual methods. In this current scenario, we will audit network connections using the below command:
ss -ntplu
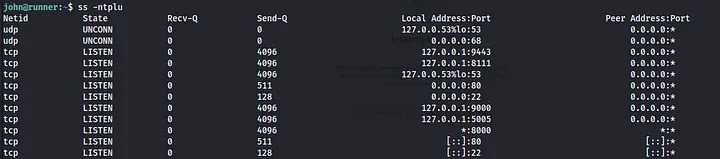
As can be seen, the local hsot is listening on many internal local ports such as 9000 and 5005. The way to access these internal ports is through SSH port forwarding.
SSH port forwarding
Port forwarding through SSH can be done through encrypted tunnels. An encrypted tunnel built using the SSH protocol constitutes an SSH tunnel. Unencrypted traffic can be transported over a network via an SSH tunnel through an encrypted channel.
SSH tunnels can be used to securely transfer files and also to offer a way around firewalls that block or filter specific internet services. For instance, a company might use its proxy filter to ban specific websites. However, users might not want the company proxy filter to track or obstruct their online activity. If users are able to establish a connection to an external SSH server, they can build an SSH tunnel to route a certain port on their local system to port 80 on a distant web server.
We can create a local port forwarding to access the internal port 9000 using the below command:
ssh -L 9443:127.0.0.1:9443 -L 8111:127.0.0.1:8111 -L 9000:127.0.0.1:9000 -L 5000:127.0.0.1:5000 john@10.10.11.13 -i id_rsa
Where 9443, 8111, 9000 and 5000 are the internal ports the local machine is listening on internally.
With forwarding accomplished, we can proceed and access the said internal ports using the attacker machine.
Portrainer.io CVE Exploitation
Portrainer is a container management platform to create and manage docker & kubernetes containers. Portainer’s multi-cluster and multi-device support means you can manage environments of any type, anywhere (Docker and Kubernetes, running on dev laptops, in your DC, in the cloud, or at the edge), and we don’t require you to run any specific Kubernetes distro.
A login form for this web app can be found visiting: http://127.0.0.1:9000.
Remember that you got a pair of credentials from previous steps ( Mathew’s) so we use them to access the management interface.
The version of this app running on the machine is vulnerable and this method of exploitation can be used.
You can follow the instructions in the above link to create a container. In the step where you specify the command and user, you can use “/bin/bash’ and “root” respectively.
Then click on “Connect”

After connecting, you will have access to a root terminal where you can execute the below command to get the root flag.
cat ../../../../../../root/root.txt
CTF Walkthrough Playlist




