This comprehensive guide delves into the foundational aspects of the Windows operating system, as outlined in the TryHackMe Windows Fundamentals room. It covers essential topics such as the Windows interface, file systems, user account management, system configurations, and security features.
Windows OS | The Desktop
The desktop serves as a convenient space for storing shortcuts to applications, folders, and files. These icons may be neatly arranged alphabetically in folders or scattered randomly without a particular order. Regardless of their placement, they are generally positioned for quick access.
You can personalize the desktop’s appearance to match your preferences. By right-clicking anywhere on the desktop, a context menu appears, allowing you to adjust icon sizes, modify their arrangement, copy/paste items, or create new ones like folders, shortcuts, or text documents.
The Display settings section lets you adjust screen resolution and orientation. If multiple monitors are connected, you can configure their layout from this menu.
The Start Menu
In earlier versions of Windows, the word “Start” was visible at the bottom-left of the desktop interface. However, in modern Windows versions like Windows 10, it has been replaced with a Windows logo. Despite the visual changes, the Start Menu’s core function remains the same—it provides access to frequently used applications, files, and system utilities.
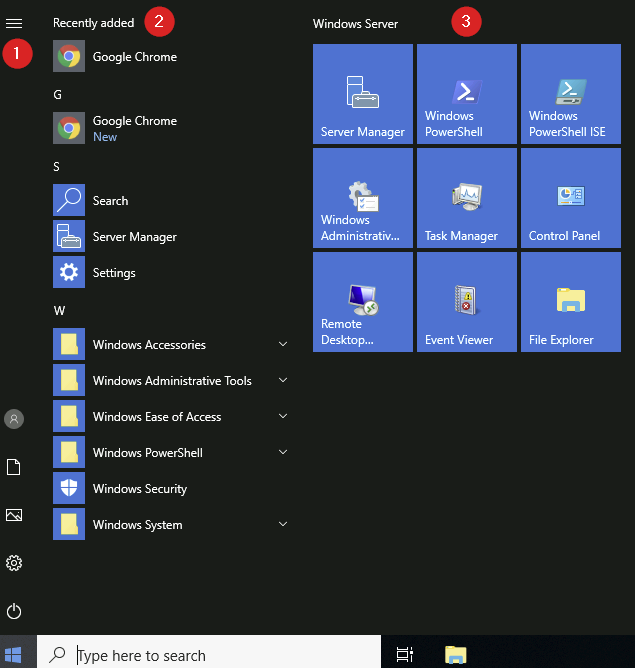
Clicking the Windows logo opens the Start Menu, which is divided into different sections:
- User Actions & Settings
- This section contains shortcuts for managing your user account, locking the screen, or signing out.
- Quick access to Documents and Pictures folders is also available.
- The Settings menu (gear icon) provides system customization options.
- The Power icon allows you to shut down, restart, or disconnect from a Remote Desktop session.
- To expand this section, click the “hamburger” icon at the top.
- Installed & Recently Added Applications
- Recently installed apps appear at the top.
- All installed programs configured for the Start Menu are listed alphabetically, with each letter grouping apps accordingly.
- Pinned Apps & Tiles
- The right side of the Start Menu contains tiles for frequently used apps or system utilities.
- Some tiles are pre-added by default, but you can customize them.
- Right-clicking a tile opens a menu where you can resize it, unpin it, or access additional properties.
The Notification Area
Located in the bottom-right corner of the screen, the Notification Area displays the date and time. Other commonly visible icons include volume control and network/wireless status. You can add or remove icons from this section through Taskbar settings.

Windows File System
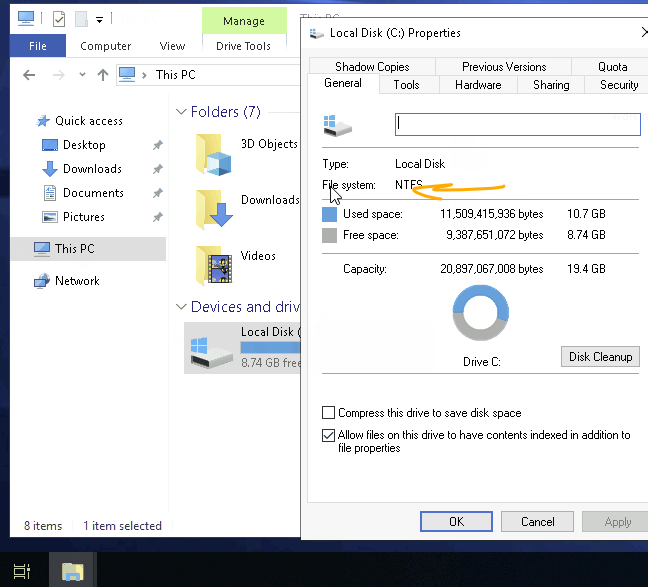
The modern versions of Windows utilize the New Technology File System (NTFS) as their primary file system.
Predecessors of NTFS
Before NTFS, Windows used FAT16/FAT32 (File Allocation Table) and HPFS (High Performance File System). While FAT partitions are still commonly found today—especially in USB drives, MicroSD cards, and other portable storage devices—they are not typically used for Windows computers or servers.
Features of NTFS
NTFS is classified as a journaling file system, meaning it can automatically repair files and folders after a system failure using log file data. This capability is not available in FAT. NTFS also overcomes several limitations of older file systems, offering features such as:
- Support for files larger than 4GB
- The ability to assign specific permissions to files and folders
- File and folder compression to save storage space
- Encryption via the Encrypting File System (EFS) for security
If you’re using Windows, your operating system is likely installed on an NTFS-formatted drive. To confirm this, right-click the drive (typically **C:**), select Properties, and check the File System type.
For more details, refer to Microsoft’s official documentation on FAT, HPFS, and NTFS.
NTFS-Specific Features
1. NTFS File and Folder Permissions
NTFS allows setting permissions to control access levels for users and groups. These permissions include:
- Full Control – Allows all actions, including modifying permissions.
- Modify – Permits changes but not ownership alterations.
- Read & Execute – Allows reading and executing files.
- List Folder Contents – Lets users view the contents of folders.
- Read – Grants read-only access.
- Write – Enables writing new data but not deleting existing files.
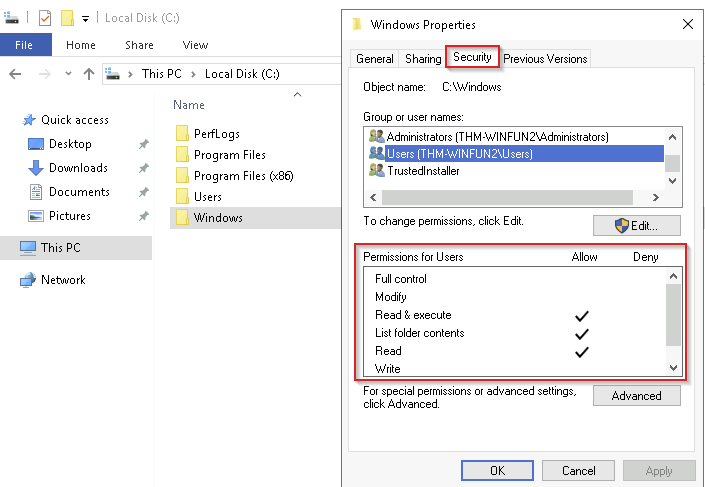
To view permissions for a file or folder:
- Right-click the file or folder.
- Select Properties.
- Go to the Security tab.
- Choose a user, computer, or group to check permissions for.
Refer to Microsoft’s documentation for more details on NTFS Special Permissions.
2. Alternate Data Streams (ADS) in NTFS
Alternate Data Streams (ADS) is a unique NTFS feature that allows a file to contain multiple data streams beyond its primary content. Every file has at least one $DATA stream, but ADS enables additional hidden streams that Windows Explorer does not display.
Security Implications of ADS:
- Malware creators have used ADS to conceal malicious data.
- However, not all uses are harmful. For instance, when a file is downloaded from the Internet, an identifier is stored in ADS to indicate its source.
While Windows does not natively display ADS, PowerShell and third-party tools can be used to inspect hidden streams.
Windows System32 Folder
The Windows folder (C:\Windows) is traditionally recognized as the directory that houses the Windows operating system.
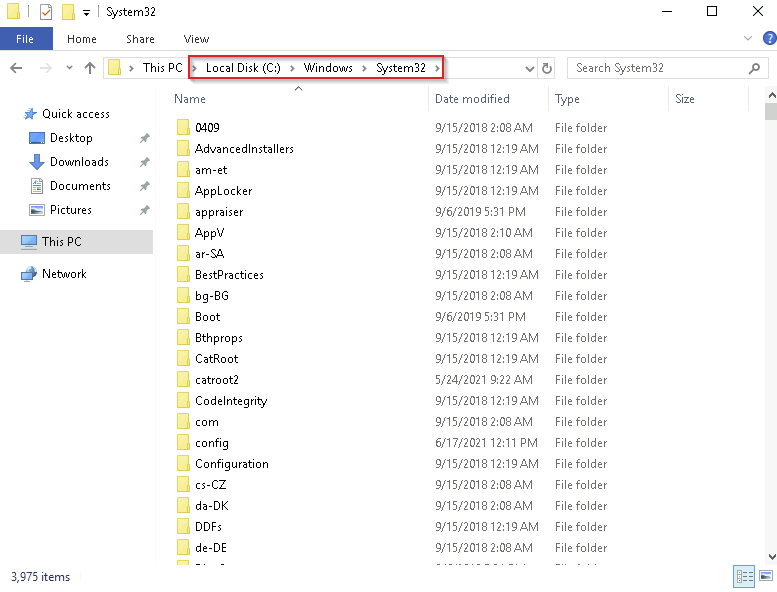
Location of the Windows Folder
Although it is commonly found on the C drive, it doesn’t have to be. The Windows folder can be located on a different drive or even within a different directory.
Role of Environment Variables
This is where environment variables, particularly system environment variables, come into play. The system environment variable that points to the Windows directory is %windir%.
According to Microsoft,
“Environment variables store information about the operating system environment, including details such as the OS path, the number of processors in use, and the location of temporary folders.”
The Critical System32 Folder
Within the Windows directory, the System32 folder contains essential files that are crucial for the operating system to function properly.
⚠️ Proceed with extreme caution when accessing or modifying this folder. Deleting files or folders within System32 can make the Windows OS inoperable.
For more details, refer to Microsoft’s official documentation on this topic.
Windows User Accounts and Permissions
In a typical local Windows system, user accounts can be classified into two main types:
- Administrator
- Standard User
User Account Permissions
The type of user account determines the level of access and actions a user can perform on the system:
- Administrator: Has full control over the system, including the ability to add or remove users, modify groups, and change system settings.
- Standard User: Has limited access and can only modify their own files and folders. They cannot install software or make system-level changes.
Since you are currently logged in as an Administrator, you have access to manage users and system settings.
Checking Existing User Accounts
To view user accounts on the system:
- Open the Start Menu and search for “Other User.”
- A shortcut to System Settings > Other Users will appear.
Alternatively, you can access Local User and Group Management by:
- Right-clicking the Start Menu and selecting Run.
- Typing
lusrmgr.mscand pressing Enter.
Inside lusrmgr, you will see two folders:
- Users: Lists all user accounts on the system.
- Groups: Displays local groups and their descriptions.
User Profiles and Storage Location
When a new user account is created, Windows automatically generates a user profile located in:
📂 C:\Users
For example, if a user account named Max is created, the corresponding profile folder will be:
📂 C:\Users\Max
Upon first login, Windows sets up the profile, displaying messages such as User Profile Service while configuring the environment.
Every user profile includes standard folders such as:
- Desktop
- Documents
- Downloads
- Music
- Pictures
Managing User Groups & Permissions
Within Local Users and Groups (lusrmgr.msc), each group has predefined permissions.
- Administrators can assign users to groups.
- When a user is added to a group, they inherit that group’s permissions.
- A user can belong to multiple groups.
To add a new user:
- Navigate to Other Users in System Settings.
- Click “Add someone else to this PC” (this will open Local Users and Groups Management).
Windows User Account Control
Most home users log into their Windows systems as local administrators. As we discussed earlier, administrator accounts can make system-level changes, which increases security risks.
Why Elevated Privileges Are Risky
For everyday tasks like browsing the internet or working on documents, high-level (elevated) privileges are not required. Running a system with elevated privileges makes it easier for malware to infect the machine because any malicious software would execute with the same access level as the logged-in user.
Introduction of User Account Control (UAC)
To mitigate this risk, Microsoft introduced User Account Control (UAC) in Windows Vista, and it has been a part of every Windows version since.
Note: UAC does not apply to the built-in local administrator account by default.
How UAC Works
- When an administrator account logs in, the session does not run with full elevated permissions.
- If an action requires administrative privileges, the system prompts the user to confirm the operation before executing it.
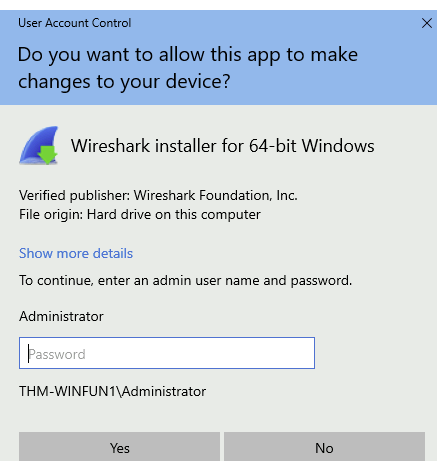
UAC in Action
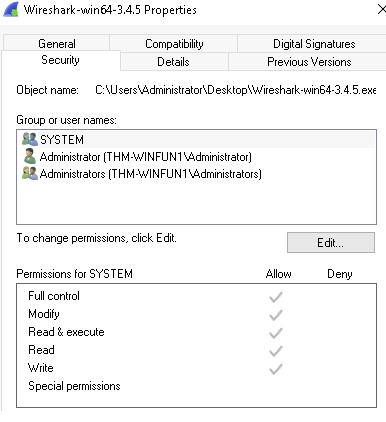
- Right-click on a program and open Properties > Security Tab to see the users/groups and their permissions.
- Standard users are not listed as having access to certain system-level changes.
- If you attempt to install a program as a standard user, you’ll notice a shield icon on the program’s default icon.
- This shield indicates that UAC will prompt you before the installation begins.
- When double-clicking the program, the UAC prompt appears, displaying the built-in administrator account name and requesting its password.
- If no password is entered within a certain time, the prompt disappears, and the program does not install.
Why UAC is Important
By requiring user confirmation before executing privileged tasks, UAC significantly reduces the likelihood of malware successfully compromising the system.
Windows Control Panel
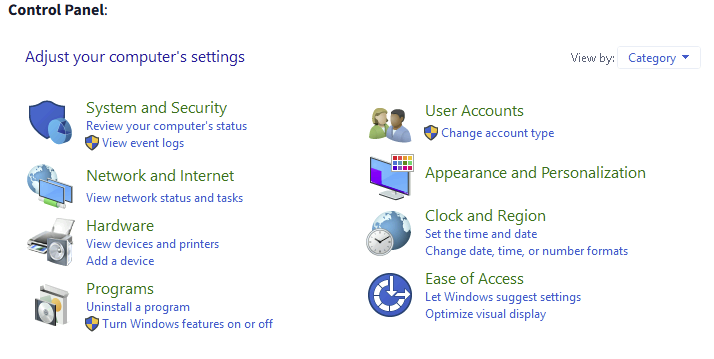
On a Windows system, the main places to modify system settings are the Settings menu and the Control Panel.
For a long time, the Control Panel was the primary hub for system adjustments, such as adding a printer or uninstalling a program. However, the Settings menu, introduced in Windows 8 (which was designed for touchscreen tablets), has since become the main interface for modifying system settings in Windows 10 and later.
While both menus serve similar functions, they also have key differences. The Control Panel provides access to more advanced settings and allows for more complex system modifications. In some cases, navigating through the Settings menu will eventually lead to the Control Panel.
For instance, in the Settings menu, selecting Network & Internet and then clicking on Change adapter options will direct you to a Control Panel setting.
Windows Task Manager
The Task Manager displays details about currently running applications and processes on the system. It also provides additional insights, such as CPU and RAM usage, which are categorized under the Performance section.
To open the Task Manager, simply right-click on the taskbar.
Windows System Configuration
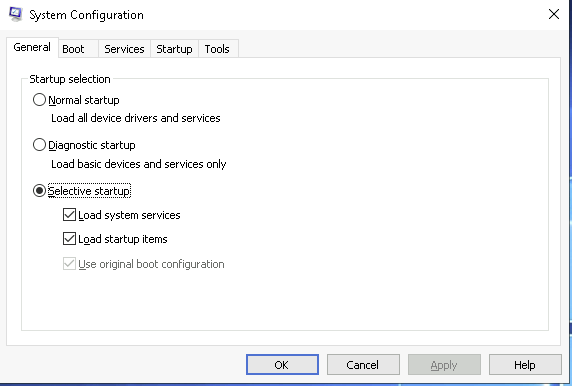
The System Configuration utility (MSConfig) is designed for advanced troubleshooting, primarily to diagnose startup issues.
There are multiple ways to open System Configuration, including through the Start Menu.
Overview of the MSConfig Tabs:
The utility consists of five tabs, each serving a different purpose:
- General – Allows users to choose which devices and services Windows should load at startup. Options include Normal, Diagnostic, or Selective startup.
- Boot – Provides various boot configuration options for the operating system.
- Services – Displays all system services, whether running or stopped. Services are background applications that support system functions.
- Startup – In the attached VM, this tab may appear empty. However, on a local machine, Microsoft recommends using Task Manager (taskmgr) to manage startup programs, as MSConfig is not a startup management tool. (Note: In the attached VM, Task Manager does not display a Startup tab.)
- Tools – Contains a list of system utilities that can be used to configure the OS further. Each tool includes a brief description, and the Selected command section updates based on the chosen tool.
Windows Computer Management Utility
The Computer Management (compmgmt) utility is divided into three main sections: System Tools, Storage, and Services and Applications.
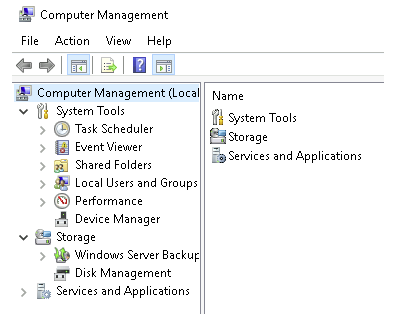
System Tools
Task Scheduler
Task Scheduler allows users to create and manage automated tasks that the computer executes at predefined times. According to Microsoft, this feature enables applications, scripts, or other tasks to run automatically based on user-defined conditions. Tasks can be scheduled to execute at login, logoff, or at specified intervals, such as every five minutes.
To create a basic task, navigate to the Actions pane on the right and select Create Basic Task.
Event Viewer
Event Viewer provides a log of system events, serving as an audit trail to monitor computer activity. This tool is commonly used for diagnosing system issues and tracking executed actions.
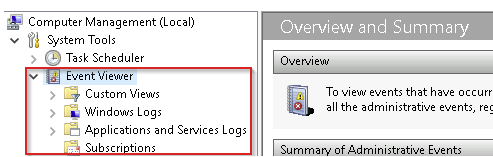
Event Viewer consists of three panes:
- Left Pane: Displays a hierarchical list of event log providers.
- Middle Pane: Shows a summary of events for the selected provider.
- Right Pane: Contains available actions for managing events.
There are five types of logged events, which can be found under Windows Logs, with descriptions available on docs.microsoft.com.
Shared Folders
This section displays all shared files and folders that other users can access. Right-clicking a folder allows you to view its properties, such as permissions that define who has access to the shared resource.
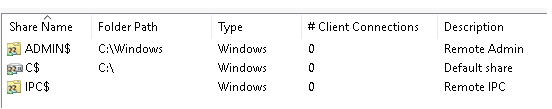
- Sessions: Displays a list of active users connected to shared resources. (In a virtual machine, this list may be empty.)
- Open Files: Lists files and folders currently accessed by connected users.
Local Users and Groups
This section, also known as lusrmgr.msc, was covered in Windows Fundamentals 1 and allows user and group account management.
Performance
The Performance Monitor (perfmon) utility provides real-time and historical system performance data. It is commonly used for troubleshooting performance issues on local or remote systems.
Storage
The Storage section includes Windows Server Backup and Disk Management.
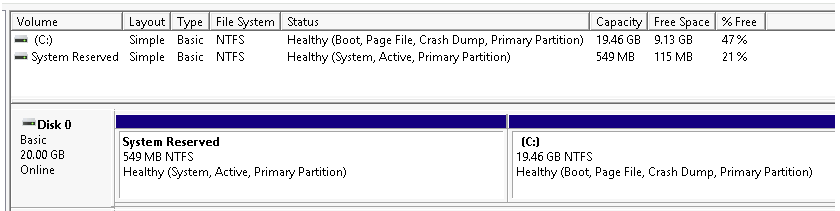
Disk Management is a Windows utility used for advanced storage configurations, including:
- Setting up a new drive
- Extending or shrinking partitions
- Assigning or modifying drive letters (e.g., changing a drive to E:)
Services and Applications
As previously discussed, a service is a background application that runs without user interaction. This section allows users to manage services beyond enabling or disabling them, including viewing their Properties.
WMI Control is also available here, which helps configure and manage the Windows Management Instrumentation (WMI) service.
System Information Utility

What is the System Information (msinfo32) Tool?
According to Microsoft, Microsoft System Information (Msinfo32.exe) is a built-in Windows tool that collects and displays a detailed overview of a computer’s hardware, system components, and software environment. This information is particularly useful for diagnosing system issues.
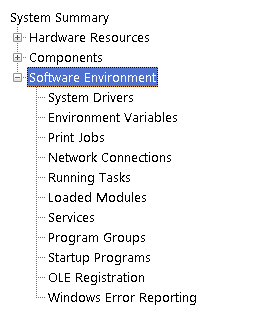
System Summary Sections
The System Summary is divided into three key sections:
- Hardware Resources
- Components
- Software Environment
System Summary
This section provides general technical details about the computer, including the processor brand and model.
Hardware Resources
The information in this section is advanced and primarily intended for IT professionals. If you’re interested in learning more, refer to the official Microsoft documentation.
Components
This section contains details about the hardware devices installed on the computer. While some subsections may be empty, others, such as Display and Input, provide useful information.
Software Environment
This section provides insight into both built-in system software and user-installed applications. Additional details include Environment Variables and Network Connections.
Environment Variables
As per Microsoft:
“Environment variables store data about the operating system environment, including details such as the OS path, the number of processors, and the location of temporary folders.”
For example, the WINDIR environment variable stores the directory path of the Windows installation, allowing programs to locate essential system files.
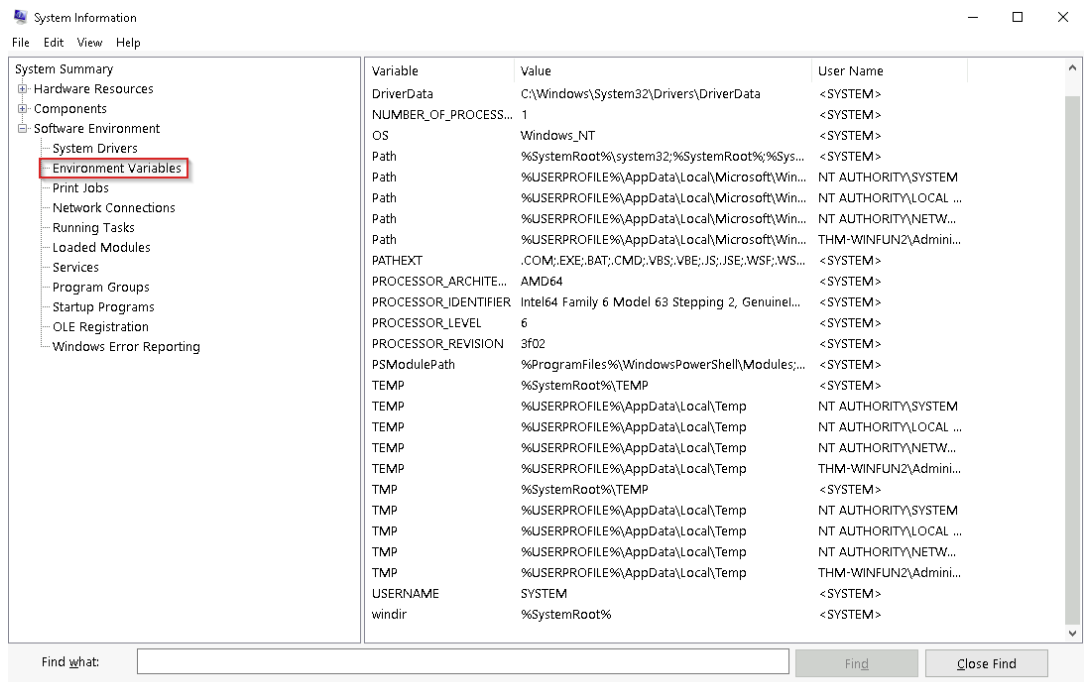
To view Environment Variables, navigate to:
- Control Panel > System and Security > System > Advanced system settings > Environment Variables
- OR Settings > System > About > System Info > Advanced system settings > Environment Variables
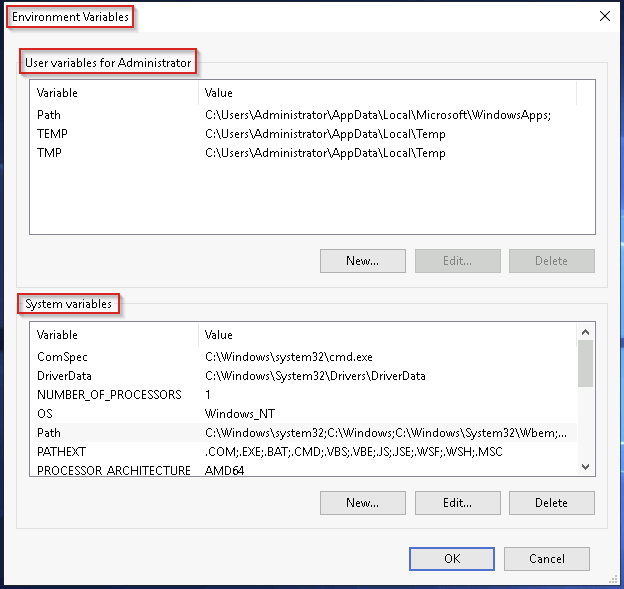
Using the Search Feature
At the bottom of the System Information tool, there’s a search bar. Try using it:
- Select Components
- Search for IP address
Windows Resource Monitor Utility
According to Microsoft, Resource Monitor provides detailed insights into CPU, memory, disk, and network usage at both the process level and system-wide. It also shows which processes are using specific file handles and modules.
This tool allows users to:
- Filter and analyze data for one or multiple processes (applications or services).
- Start, stop, pause, and resume services.
- Force-close unresponsive applications directly from the interface.
- Identify deadlocked processes and file locking conflicts, enabling users to resolve issues without closing applications and risking data loss.
Like other advanced diagnostic tools, Resource Monitor is primarily designed for experienced users performing in-depth system troubleshooting.
Overview Tab Sections
Resource Monitor’s Overview tab is divided into four key sections:
- CPU
- Disk
- Network
- Memory
Windows Command Prompt
At first glance, the Command Prompt (cmd) may seem intimidating, but once you learn how to navigate it, it becomes much more manageable.
In the early days of computing, the command line was the only way to interact with the operating system. However, with the introduction of the Graphical User Interface (GUI), users could perform complex tasks with simple clicks instead of typing commands manually.
Despite the dominance of the GUI, users can still interact with the operating system through the Command Prompt, which remains a powerful tool for system management and troubleshooting.
Basic Commands to Get Started
Here are a few simple commands to retrieve information about your system:
- hostname → Displays the computer’s name.
- whoami → Shows the currently logged-in user.
- ipconfig → Displays network configuration details, including IP addresses.
Using Help Manuals for Commands
Each command has a help manual that explains its syntax and available parameters for customization. To access a command’s help manual, append /? to the command.
Example:
ipconfig /?
This will display additional options for the ipconfig command.
Exploring the netstat Command
The netstat command provides information about network connections and protocol statistics.
Its syntax follows this structure:
netstat [parameters]
For example, you can use different parameters like:
- -a → Displays all active connections.
- -b → Shows which programs are using connections.
- -e → Displays Ethernet statistics.
Try experimenting with different parameters to see how they affect the output.
Using the net Command
The net command is mainly used for managing network resources and supports multiple sub-commands.
Typing net alone will display a list of sub-commands that can be used. Unlike other commands, net does not use /? for help. Instead, use:
net help [sub-command]
Examples:
- To view help for the net user
net help user
Similarly, you can check help for localgroup, use, share, and session by replacing user with the respective sub-command.
Windows Registry Editor
According to Microsoft, the Windows Registry is a centralized hierarchical database that stores essential configuration information for users, applications, and hardware devices.
Windows continuously refers to the registry for various settings, including:
- User profiles for each account.
- Installed applications and the types of files they can create.
- Folder and application icon settings.
- Connected hardware details.
- Active network ports.
Important Warning
The Windows Registry is intended for advanced users. Modifying registry settings can significantly impact system performance and functionality.
Accessing the Windows Registry
There are multiple ways to view or modify the registry. One common method is using the Registry Editor (regedit).
Windows Security
Windows Security can also be accessed through Settings and includes the following features:
- Virus & threat protection
- Firewall & network protection
- App & browser control
- Device security
Status Icons Meaning
- Green → Your device is well-protected, with no required actions.
- Yellow → There is a security recommendation that needs your review.
- Red → Immediate action is required to resolve a security issue.
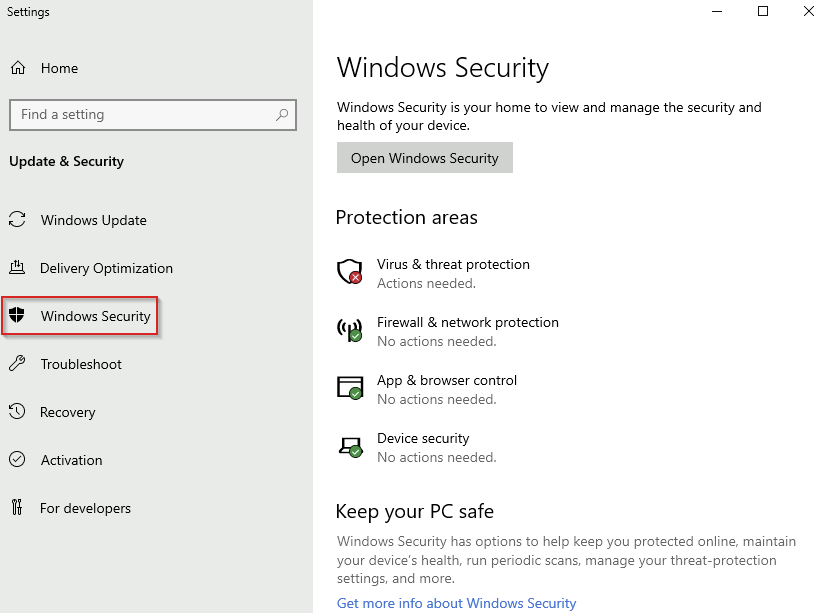
Virus & Threat Protection
Key Sections:
- Current Threats
- Virus & Threat Protection Settings
Current Threats
- Scan Options:
- Quick Scan → Scans common locations where threats are usually found.
- Full Scan → Scans all files and running programs; may take over an hour.
- Custom Scan → Allows selection of specific files and locations for scanning.
- Threat History:
- Last Scan → Windows Defender automatically scans for threats.
- Quarantined Threats → Identified threats that are isolated to prevent execution.
- Allowed Threats → Threats manually permitted by the user.
⚠️ Warning: Only allow a flagged threat if you are absolutely certain it is safe.
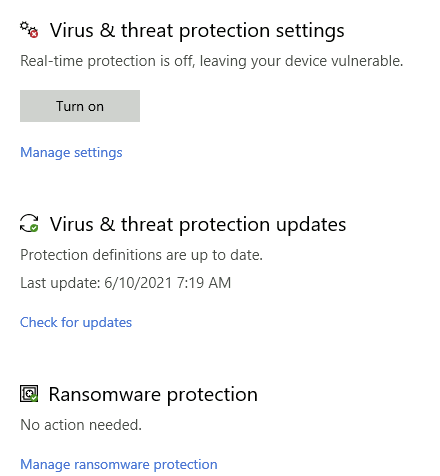
Virus & Threat Protection Settings
To manage settings, go to Manage Settings under Virus & Threat Protection.
- Real-time protection → Blocks malware from installing or running.
- Cloud-delivered protection → Provides updated security intelligence via the cloud.
- Automatic sample submission → Sends sample files to Microsoft to improve security.
- Controlled folder access → Prevents unauthorized applications from modifying files.
- Exclusions → Items in this list won’t be scanned by Windows Defender.
- Notifications → Security alerts about system health and threats.
⚠️ Warning: Excluding files from scans can expose your system to threats. Only use this option if you’re sure it’s safe.
Virus & Threat Protection Updates
- Check for updates → Manually update Windows Defender Antivirus definitions.
Ransomware Protection
- Controlled Folder Access → Must be enabled to protect against ransomware, requiring Real-time Protection to be active.
Note: Real-time protection is disabled in the virtual machine (VM) to prevent performance issues. However, it should always be enabled on personal devices unless a third-party antivirus is in place.
Windows Firewall
According to Microsoft:
“Traffic flows in and out of devices through ports. A firewall controls what is—and isn’t—allowed through these ports, acting like a security guard verifying incoming and outgoing traffic.”
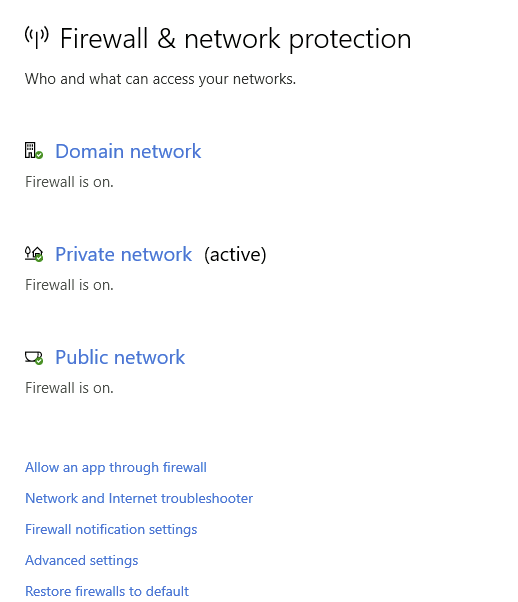
Types of Windows Firewall Profiles
Windows Defender Firewall has three profiles:
- Domain Profile → Used in corporate networks where authentication to a domain controller is required.
- Private Profile → Assigned to home or trusted private networks.
- Public Profile → The default setting for public networks like coffee shop or airport Wi-Fi.
Clicking on any firewall profile will provide options to:
- Turn the firewall on/off.
- Block all incoming connections.
- View and manage app permissions for firewall profiles.
For advanced configurations, Windows Defender Firewall settings can be customized, but this is recommended only for experienced users. Refer to official Microsoft documentation for best practices.
Microsoft Defender SmartScreen
According to Microsoft, Microsoft Defender SmartScreen helps protect users from phishing attempts, malicious websites, harmful applications, and potentially dangerous downloads.
For more details, refer to the official Microsoft documentation on SmartScreen.
Features:
Check Apps and Files
Windows Defender SmartScreen safeguards your device by scanning apps and files downloaded from the internet, helping to block unrecognized or potentially harmful content.
Exploit Protection
This built-in security feature in Windows 10 and Windows Server 2019 helps protect against exploit-based attacks that attempt to take advantage of system vulnerabilities.
⚠️ Warning: It is strongly advised to keep the default settings unless you are absolutely certain of any modifications being made.
Windows Bitlocker Encryption
According to Microsoft, BitLocker Drive Encryption is a built-in security feature that helps protect data from theft or unauthorized access in cases where a device is lost, stolen, or improperly decommissioned.
Enhanced Security with TPM
Devices equipped with a Trusted Platform Module (TPM) offer the highest level of protection with BitLocker.
As Microsoft explains:
“BitLocker provides optimal security when used with TPM version 1.2 or later. TPM is a hardware component pre-installed in many modern computers by manufacturers. It works alongside BitLocker to safeguard user data and ensure the system remains untampered while offline.”
For more details, refer to the official Microsoft documentation on BitLocker.
Windows Volume Shadow Copy Service
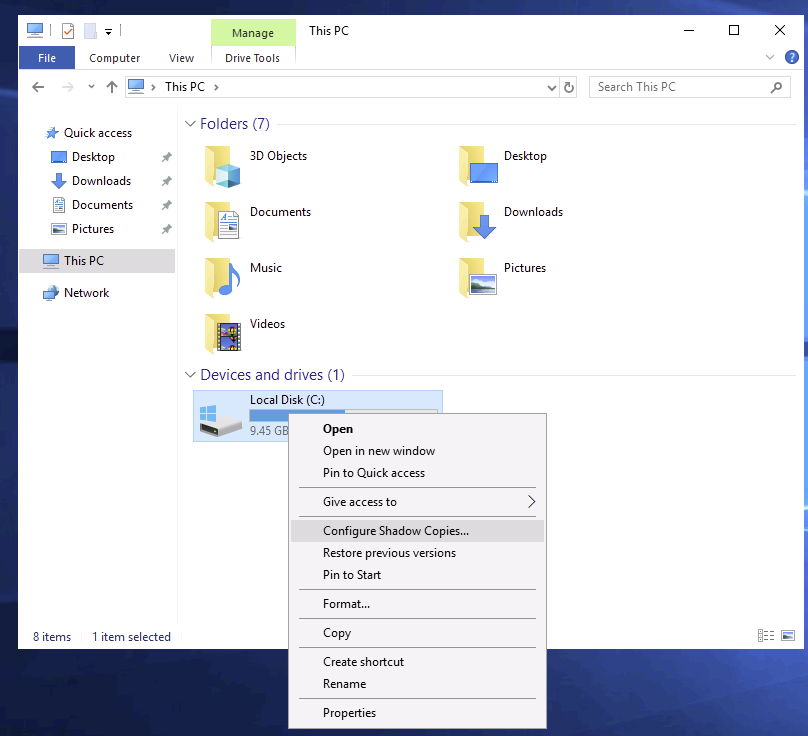
According to Microsoft, the Volume Shadow Copy Service (VSS) facilitates the creation of consistent shadow copies (also known as snapshots or point-in-time copies) of data intended for backup.
These shadow copies are stored in the System Volume Information folder on each drive where System Protection is enabled.
Functions of VSS (When System Protection is Enabled)
Within Advanced System Settings, you can:
- Create a restore point
- Perform a system restore
- Modify restore settings
- Delete restore points
Security Considerations
Cybercriminals are aware of this feature and often design malware to target and delete shadow copies. This tactic prevents users from restoring their system after a ransomware attack, making offline or off-site backups crucial for data recovery.
TryHackMe Windows Fundamentals 1 | Room Answers
What encryption can you enable on Pro that you can’t enable in Home?
BitLocker
Which selection will hide/disable the Search box?
Hidden
Which selection will hide/disable the Task View button?
Show Task View button
Besides Clock and Network, what other icon is visible in the Notification Area?
Action Center
What is the meaning of NTFS?
New Technology File System
What is the system variable for the Windows folder?
%windir%
What is the name of the other user account?
tryhackmebilly
What groups is this user a member of?
Remote Desktop Users,Users
What built-in account is for guest access to the computer?
Guest
What is the account description?
window$Fun1!
What does UAC mean?
User Account Control
In the Control Panel, change the view to Small icons. What is the last setting in the Control Panel view?
Windows Defender Firewall
What is the keyboard shortcut to open Task Manager?
Ctrl+Shift+Esc
TryHackMe Windows Fundamentals 2 | Room Answers
What is the name of the service that lists Systems Internals as the manufacturer?
PsShutdown
Whom is the Windows license registered to?
Windows User
What is the command for Windows Troubleshooting?
C:\Windows\System32\control.exe /name Microsoft.Troubleshooting
What command will open the Control Panel? (The answer is the name of .exe, not the full path)
control.exe
What is the command to open User Account Control Settings? (The answer is the name of the .exe file, not the full path)
UserAccountControlSettings.exe
What is the command to open Computer Management? (The answer is the name of the .msc file, not the full path)
compmgmt.msc
At what time every day is the GoogleUpdateTaskMachineUA task configured to run?
6:15 AM
What is the name of the hidden folder that is shared?
sh4r3dF0Ld3r
What is the command to open System Information? (The answer is the name of the .exe file, not the full path)
msinfo32.exe
What is listed under System Name?
THM-WINFUN2
Under Environment Variables, what is the value for ComSpec?
%SystemRoot%\system32\cmd.exe
What is the command to open Resource Monitor? (The answer is the name of the .exe file, not the full path)
resmon.exe
In System Configuration, what is the full command for Internet Protocol Configuration?
C:\Windows\System32\cmd.exe /k %windir%\system32\ipconfig.exe
For the ipconfig command, how do you show detailed information?
ipconfig /all
What is the command to open the Registry Editor? (The answer is the name of the .exe file, not the full path)
regedt32.exe
TryHackMe Windows Fundamentals 3 | Room Answers
There were two definition updates installed in the attached VM. On what date were these updates installed?
5/3/2021
Checking the Security section on your VM, which area needs immediate attention?
Virus & threat protection
Specifically, what is turned off that Windows is notifying you to turn on?
Real-time protection
If you were connected to airport Wi-Fi, what most likely will be the active firewall profile?
Public network
What is the TPM?
Trusted Platform Module
We should use a removable drive on systems without a TPM version 1.2 or later. What does this removable drive contain?
startup key
What is VSS?
Volume Shadow Copy Service
Conclusion
In this walkthrough, we’ve explored the core components of the Windows operating system, providing insights into its interface, file management, user accounts, and security mechanisms. By understanding these fundamentals, users can navigate and manage Windows environments more effective.
Video Walkthrough
Technical Insights
- TCP Protocol → Primary communication method between attacker and victim.
- Ports 1337 & 1338 → Used for exfiltrating memory dump and KeePass database.
- XOR Encryption → Applied using hardcoded keys to obfuscate exfiltrated data.
- Base64 Encoding → Used to convert binary data into a readable format for transmission.
Conclusion
This forensic investigation highlights the techniques attackers use to exfiltrate data and demonstrates the importance of thorough network monitoring. By understanding and practicing forensic analysis through challenges like TryHackMe, cybersecurity professionals can better prepare to defend against real-world network attacks.




