What is Wazuh?
Wazuh is an EDR (endpoint detection and response.) solution and can be considered as an HIDS (host intrusion detection system). It monitors the endpoint for any indicators of a threat or policy violations in addition to the ability of auditing against some cyber security frameworks.
Wazuh can be used to achieve the following:
- Auditing a device for common vulnerabilities
- Proactively monitoring a device for suspicious activity such as unauthorised logins, brute-force attacks or privilege escalations
- Visualising complex data and events into neat and trendy graphs
- Recording a device’s normal operating behaviour to help with detecting anomalies
Wazuh SIEM Study Notes & Guide
Wazuh SIEM Study Notes & Guide meticulously explains Wazuh’s architecture, setup, and integrations. Wazuh operates in a manager-agent model, offering monitoring, log collection, alerting, and integration capabilities.
It includes deep guidance on installing Wazuh components (manager, indexer, dashboard), configuring agents across OSes, performance optimization (e.g., heap size, caching, threading), and extending detection with custom rules and decoders. The book emphasizes integrating Wazuh with major security tools (Suricata, VirusTotal, TheHive, MISP, Fortinet, OPNsense) for real-time correlation and threat intelligence.
Case studies add practical insights into deploying Wazuh in industries like finance, healthcare, and retail. The final sections cover policy compliance, EDR configuration, file integrity monitoring, and vulnerability management, making it a rich, hands-on reference for cybersecurity professionals.
Wazuh SIEM Study Notes | Who Are These Notes For?
- Professionals who are actively working in the field and need a set of ready and concise Wazuh notes.
- Savvy learners who want to quickly master Wazuh without having to read hunderds of pages.
Table of Contents:
- Important Note
- Definition
- How it works
- Wazuh Components
- Wazuh Installation
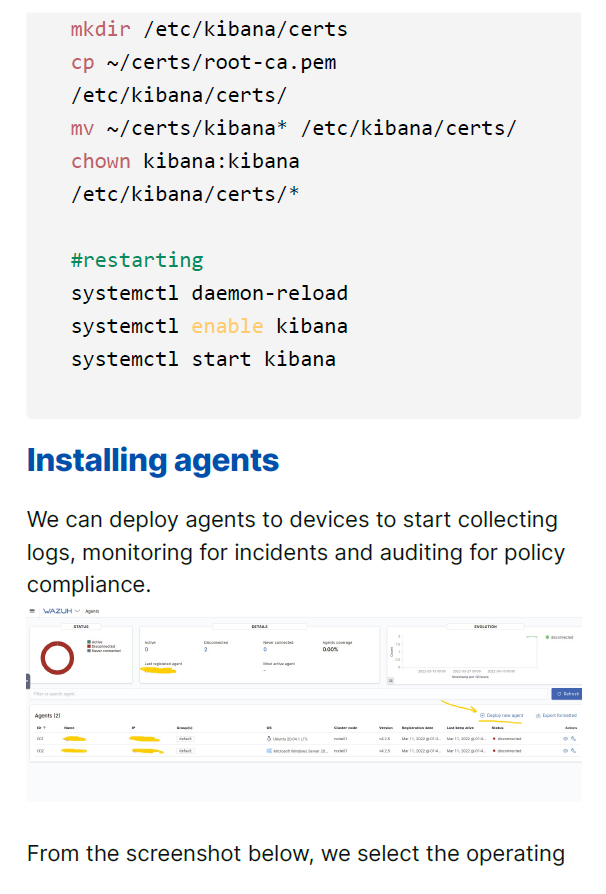
- Installing agents
- Optimizing Wazuh Performance
- Configuring Logs Rotation
- Understanding Wazuh Rules
- The goal of Wazuh Rules
- Wazuh Rule Elements
- Order of Processing Rules
- Testing Wazuh Rules
- Creating Custom Rules
- Wazuh Decoders
- Testing Decoders
- Integrating Wazuh with Suricata IDS
- Integrating Wazuh with VirusTotal
- Integrating Wazuh with TheHive
- Integrating Wazuh with MISP
- Integration with Fortinet Firewall
- Vulnerability scanning
- Auditing against cyber security framework
- Policy compliance and auditing events
- Gathering windows event logs and forwarding to
- Wazuh with Sysmon
- Monitoring Linux workstations
Pages: 104
Format: PDF

Testimonials (LinkedIn)
How to buy the book?
You can buy the booklet directly by clicking on the button below
After you buy the booklet, you will be able to download the PDF book.
What about the notes updates?
if you have been watching my YouTube Channel, you definitely know that those who subscribe to the second tier of my channel membership they instantly get access to a vast catalog of cybersecurity, penetration testing, digital marketing, system administration and data analytics notes catalog for 10$ along with the ability to receive all notes updates as long as they are subscribed so what does that mean?
This means if you want to stay up to date with the changes and updates to the notes and get access to other categories, I encourage to join the channel membership second tier instead. However, if you are fine with downloading the current version of this section of the notes then you can buy this booklet instead for a one-time payment.
Will the prices of this booklet change in the future?
Once another version of this booklet is released, which it will, the price will slightly change as the booklet will include more contents, notes and illustrations.
Free Wazuh Training
Check out the playlist below on my YouTube channel

