This article outlines various web hacking challenges from the PicoCTF platform, demonstrating practical approaches to identifying and exploiting vulnerabilities. It explains techniques such as server-side template injection (SSTI), including methods for bypassing input filters using hexadecimal encoding.
I also cover file upload vulnerabilities, showcasing how to upload and trigger web shells to gain remote code execution and escalate privileges. Furthermore, I show how to analyse API documentation for leaked data, specifically by identifying endpoints that generate memory dumps, and demonstrates exploiting an eval function by bypassing security filters through string concatenation and character representation.
Finally, I explore websocket manipulation to win a chess game against a bot and illustrates finding hidden information within cookies and web inspector elements, often requiring decoding various formats like Base64 and URL encoding.
The Challenges I solved are listed below:
SSTI 1
SSTI 2
No Sanity
Heap Dump
3vil
Websocket Fish
Cookie Monster
Web Decode
Unminify
Bookmarklet
Pachinko
Trickster
Server-Side Template Injection (SSTI) SSTI1 and SSTI2
The first challenge dives into a vulnerability called Server-Side Template Injection, or SSTI. The goal here is to get a website to execute code that it’s not supposed to.
Leveling Up: The second SSTI challenge adds a twist: the website now filters out certain characters to block these attacks. But with a bit of cleverness, the video shows how to bypass these filters using hexadecimal representations of the forbidden characters and a more advanced payload.
The Test: I show a neat trick to test for SSTI: simply type an arithmetic operation like {{7*7}} into an input box. If the website spits back “49,” you know it’s vulnerable!
Getting the Goods: Once the vulnerability is confirmed, the host crafts a special command (a “payload”) to list the files in the current directory. With a slight modification, this same payload is used to read the contents of the “flag” file and capture the prize.
Vulnerability Testing: The initial step involves testing for Server-Side Template Injection (SSTI) by providing an arithmetic operation enclosed within two curly braces, such as {{7*7}}. If the site returns the result (e.g., 49), it confirms SSTI vulnerability. Other tests include attempting to execute HTML (e.g., {{‘<‘}}script{{‘>’}}alert(1){{‘<‘}}/script{{‘>’}}) or print current objects (e.g., {{config}}).

Payload Development: Payloads are crafted to return meaningful information, such as files listed in the current working directory.
Filter Bypass (SSTI2): To bypass input sanitisation filters (e.g., for underscores, dots, percent, colon, semicolon), hexadecimal representation of prohibited characters is used. For instance, F represents an underscore. Additionally, the attribute function is employed to dynamically access commands in Python, avoiding filtered characters. This method of encoding and changing character representation is broadly applicable for bypassing filters in many web applications.
Insecure File Uploads | No Sanity
Next up is a challenge that exploits a common weakness in websites that allow users to upload files, like profile pictures.
Web Shell Upload: The challenge involves exploiting a file upload vulnerability by uploading a simple PHP web shell.
Remote Command Execution: Once uploaded, the web shell is accessed via a specific URL (e.g., /uploads/shell.php), and system commands are executed using a cmd GET parameter (e.g., ?cmd=id).
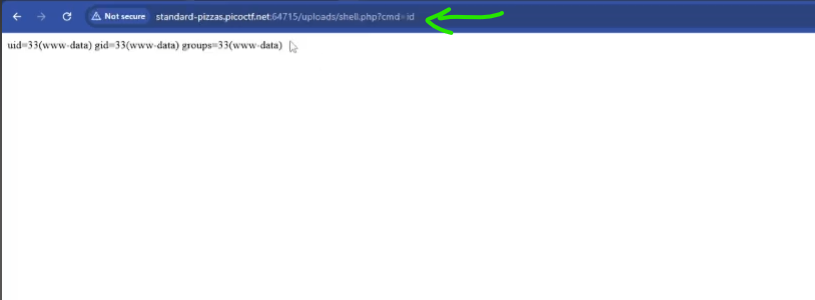
Privilege Escalation/Information Gathering: Checking the privileges of the web server user (e.g., www-data) using sudo -l is crucial. If the user has NOPASSWD sudo privileges, commands can be run at an elevated mode, allowing access to restricted directories like /root to find the flag (e.g., sudo ls /root, sudo cat /root/flag.txt).
Finding the Flag: The ultimate goal is to find a hidden flag in the root directory, which is usually off-limits. By checking the user’s permissions, the host discovers that they can run commands with elevated privileges, allowing them to access the root directory and read the flag.
The Trick: I demonstrate how to upload a simple PHP web shell disguised as an image. This shell allows the host to execute commands on the server.
Heap Dump and API Exploration
This challenge is all about digging through a website’s API documentation to find leaked information.
- The Discovery: I explore the API documentation and find an interesting endpoint called “/heapdump.” When I interact with this endpoint, it generates a memory dump of the web server.
- Sifting for Treasure: This memory dump is a file that can be downloaded and searched. By looking for the string “PicoCTF” within the file, the flag is revealed.
API Exploration: The core technique is to explore API documentation (e.g., Swagger UI) to identify endpoints that might leak sensitive data.
Memory Dump Retrieval: A specific endpoint, /heapdump, is identified which, when interacted with (via a GET request), generates a memory dump of the web server as a downloadable file.
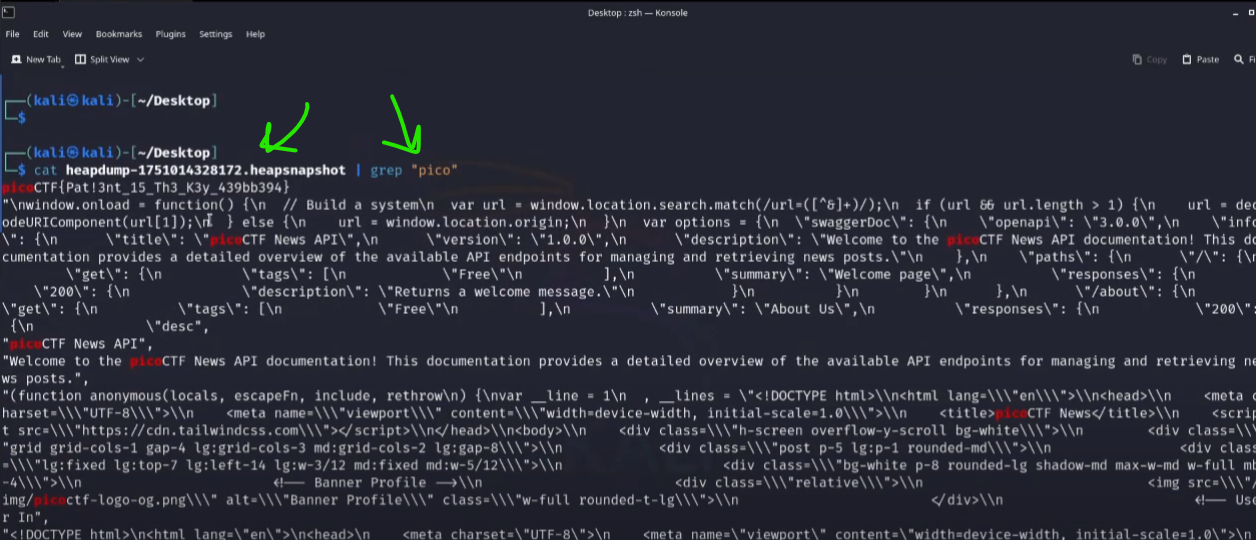
File Analysis: The downloaded heap dump file is then analysed. Tools like the file command are used to determine its type, less for initial exploration, and grep with a specific pattern (e.g., PicoCTF) to filter and locate the flag
Bypassing the ‘Eval’ Function
This challenge involves a loan calculator that uses an “eval” function, which can be dangerous if not used carefully.
- The Obstacle: The website has a filter that blocks a long list of malicious keywords and characters.
- The Bypass: I show how to get around these filters by using the
chr()function to represent forbidden characters and by cleverly concatenating strings to form the final command.
Remote Code Execution via Eval: The challenge exploits an eval function used in a loan calculator, aiming for remote code execution.
Advanced Filter Bypass: This challenge features extensive filters (regular expressions) blocking malicious keywords (e.g., os, eval, execute, bind, connect, python, socket), hexadecimal numbers, Unicode escape sequences, URL encoded characters, file extensions, forward slashes, backslashes, and double dots.
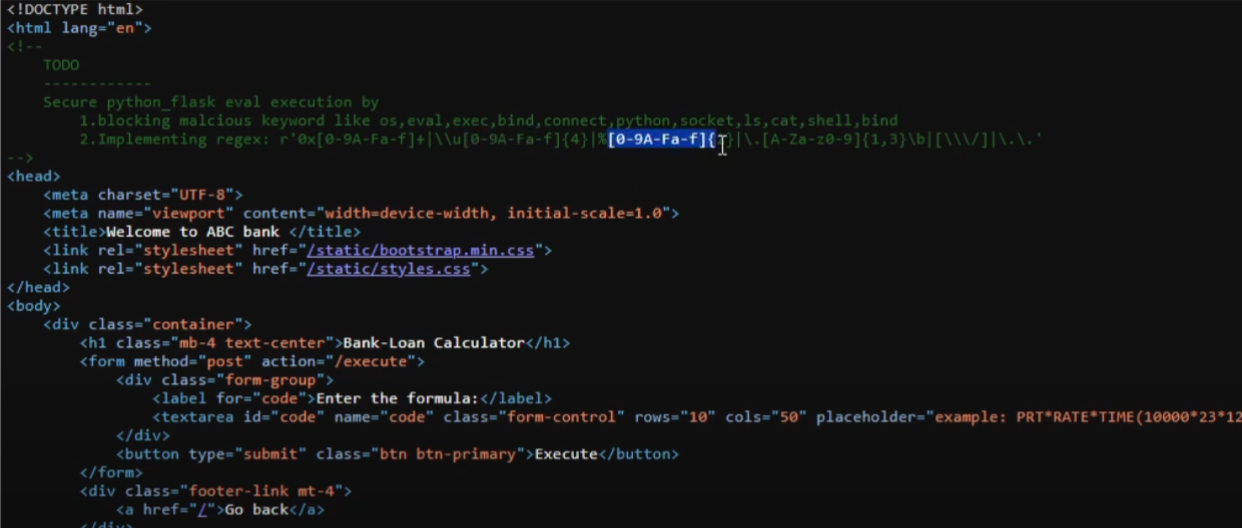
Bypassing Slashes: The chr() function is used to convert an integer (e.g., 47 for /) into its corresponding ASCII character, effectively bypassing slash filters (e.g., chr(47) instead of /).
Bypassing Dots: The dot filter is bypassed by enclosing the dot within double quotes and using string concatenation (e.g., ‘+flag+’.’) so it is read as a string rather than a forbidden character.
Websocket Fish and Chessbot Exploitation
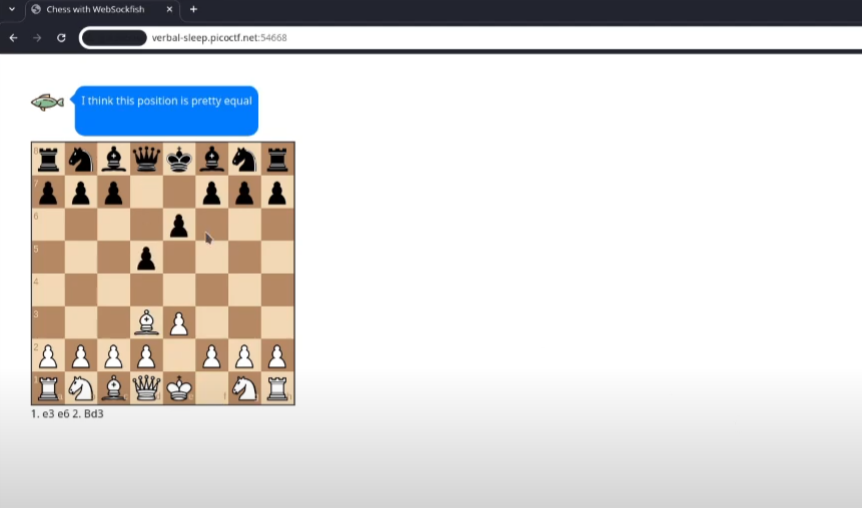
This challenge is a fun one: the goal is to beat a chess bot by exploiting a websocket.
- The Strategy: By using a tool called Burp Suite, I discover that every chess move sends a number through the websocket. The higher the number, the more confident the bot becomes.
- The Winning Move: The key to winning is to send the bot negative numbers. By sending increasingly large negative numbers, the bot gets so confused that it eventually resigns and reveals the flag.
Cookie Monster’s Secret Recipe
This challenge is all about finding a hidden secret in a website’s cookies.
- The Clue: After a failed login attempt, a message appears: “Cookie Monster says me no need password me just need cookies.”
- The Reveal: Using Burp Suite, I intercept the website’s cookies and find one named “secret_recipe.” The value of this cookie is encoded, but after decoding it, the flag is revealed.
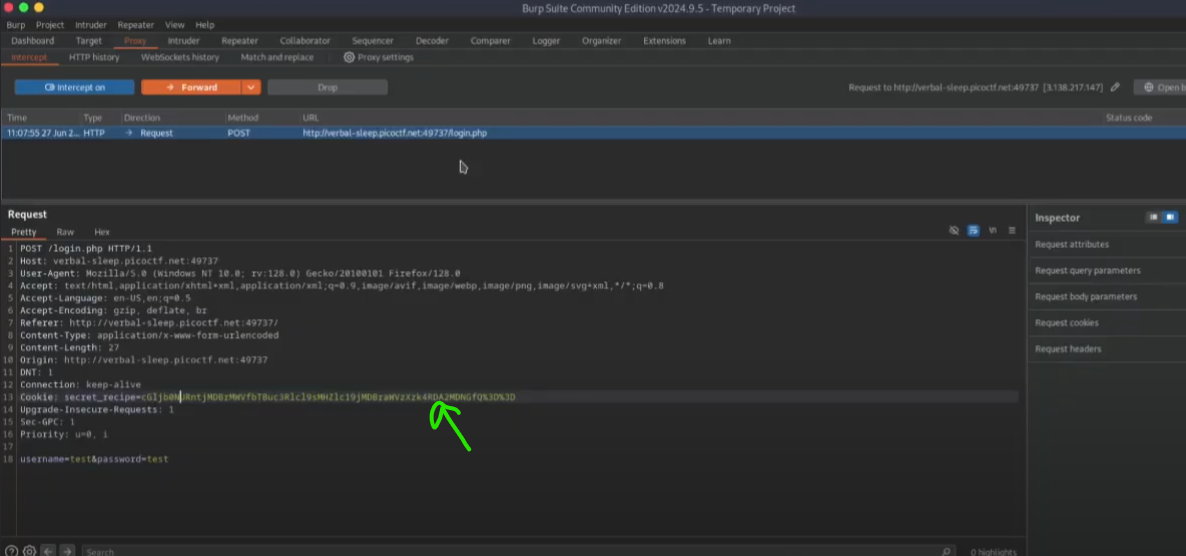
Cookie Decoding: The cookie value is found to be encoded, requiring decoding. The presence of characters like % suggests URL encoding, and == suggests Base64 encoding. The value is first decoded as Base64
Web Inspector Challenges | Unminify
These two challenges are all about using your browser’s built-in web inspector to find hidden information.
Web Inspector Usage: Both challenges emphasize using the web inspector (accessible via right-click -> Inspect in a browser) to discover hidden information.
Source Code Analysis: In “Web Decode,” the flag is found by examining the page source code within the web inspector. In “Unminify,” the flag is directly present in the HTML structure within a class named picof-flag.
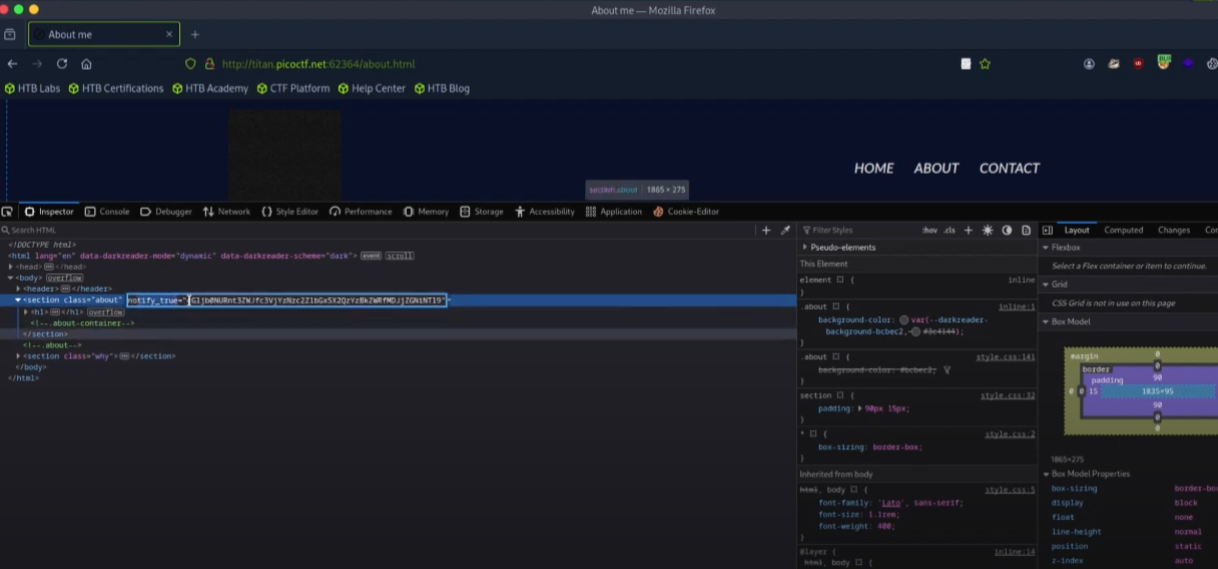
Decoding (Web Decode): Similar to the “Cookie Monster” challenge, the discovered hidden value may be encoded (e.g., Base64) and requires decoding using a suitable tool.
Tools: The Web Inspector (specifically the “Elements” or “Source” tab) is the primary tool. Burp Suite Decoder can also be used for decoding if necessary
Bookmarklet and JavaScript Execution
This challenge provides a snippet of JavaScript code.
- The Solution: The solution is as simple as copying the code and running it in the browser’s developer console, which then prints the flag.
Pachinko and NAND Simulator
This challenge involves a NAND logic gate simulator.
API Interaction and Brute-Forcing: The challenge involves interacting with a NAND simulator that sends POST requests to a /check API endpoint when a circuit is submitted. Since the correct circuit configuration is unknown, the technique involves repeatedly sending requests (effectively brute-forcing or cycling through patterns) until the flag is revealed in the server’s response.
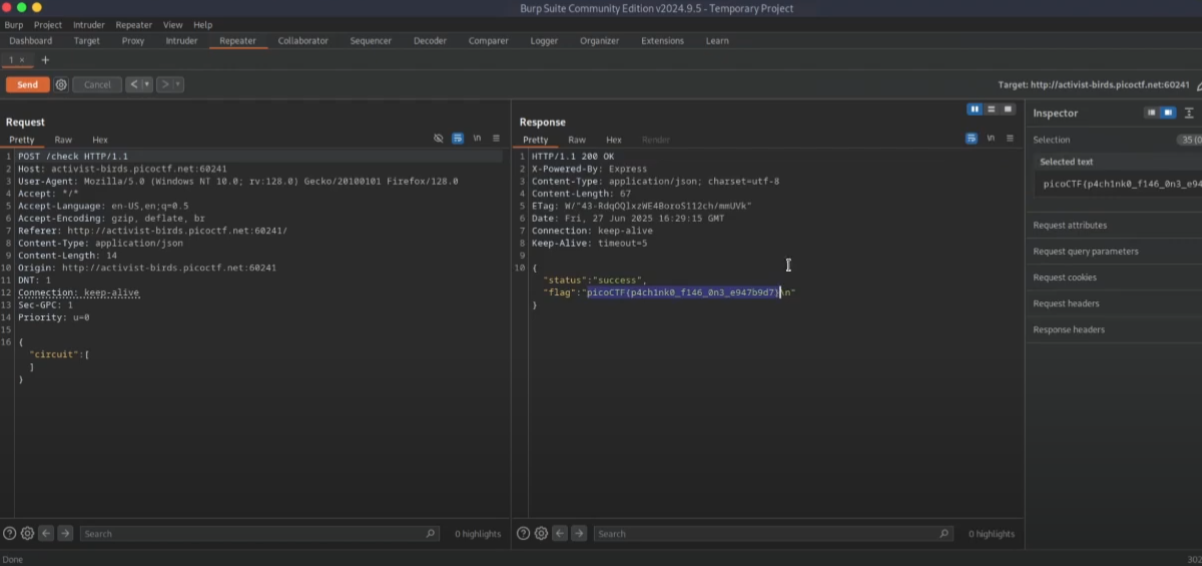
Response Analysis: Intercepting and analysing the server’s responses is key to identifying when the correct pattern has been submitted, as the flag appears in the response headers.
Tools: Burp Suite (specifically Proxy for intercepting, and Repeater for resending requests) is crucial. The Web Inspector’s Network tab can also be used to monitor and re-send requests
Trickster and File Upload Bypass
The final challenge involves a PNG image processing app that only accepts PNG files.
File Extension Bypass: Although the application only accepts PNG files, the restriction is bypassed by renaming a PHP web shell to have a double extension (e.g., shell.png.php).
Content Type Manipulation: During the upload, the Content-Type header is changed from image/png to application/octet-stream or similar, to trick the server into processing the file as an application file rather than an image.
Remote Code Execution: After successful upload, the web shell is accessed and used to execute system commands, often via an input box or URL parameter (e.g., cmd).
Tools: Burp Suite is essential for intercepting and modifying the file upload request (specifically the filename and Content-Type header). Notepad is used to create the web shell file



