We covered KAPE as a computer forensics tool to extract forensics artifacts and process them for forensics investigation. We also provided the answers for TryHackMe KAPE room.
Web Hacking & Pentesting Study Notes
Computer Forensics Study Notes
What is KAPE in Computer Forensics?
Kroll Artifact Parser and Extractor (KAPE) parses and extracts Windows forensics artifacts. It is a tool that can significantly reduce the time needed to respond to an incident by providing forensic artifacts from a live system or a storage device much earlier than the imaging process completes.
KAPE serves two primary purposes, 1) collect files and 2) process the collected files as per the provided options. For achieving these purposes, KAPE uses the concept of targets and modules. Targets can be defined as the forensic artifacts that need to be collected. Modules are programs that process the collected artifacts and extract information from them. We will learn about them in the upcoming tasks.
How to download KAPE
Download KAPE from this official link.
How to run & use KAPE?
There are two aspects that set how KAPE works, first of which is data collection which is done using #targets and the other is data processing which is done by tools run on the collected files. These tools are run on the files through #modules. Targets and modules can be set before running the program.
Setting up Targets
Targets are the artifacts that need to be collected from a system or image and copied to our provided destination. For example, we can create #Targets for the registry hives. In short, #Targets copy files from one place to another.
Below is the GUI interface.
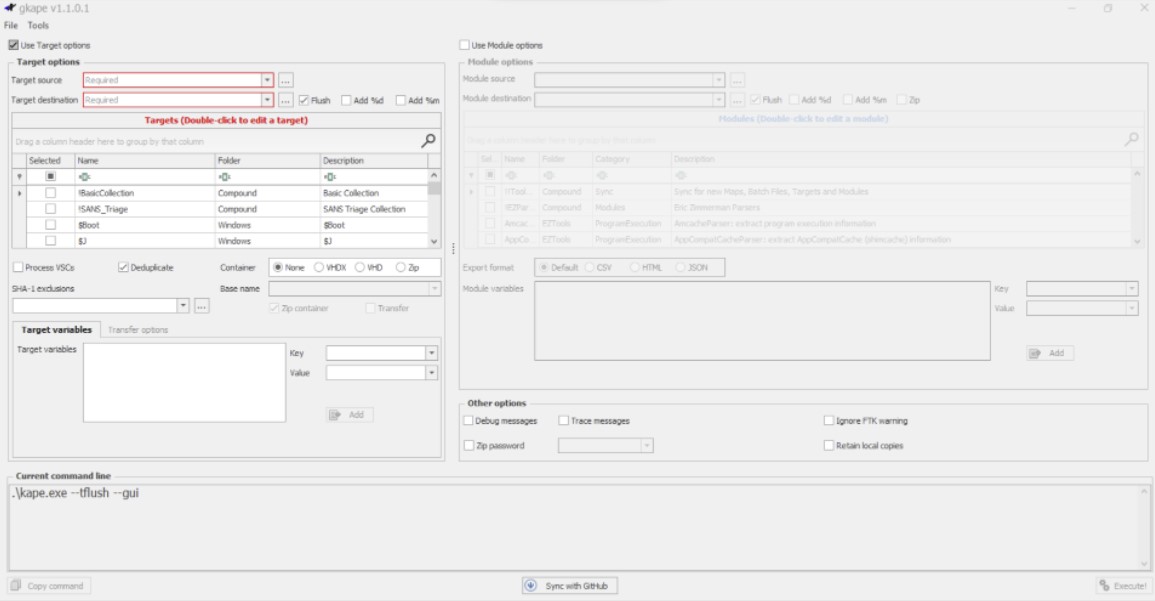
Setting up modules
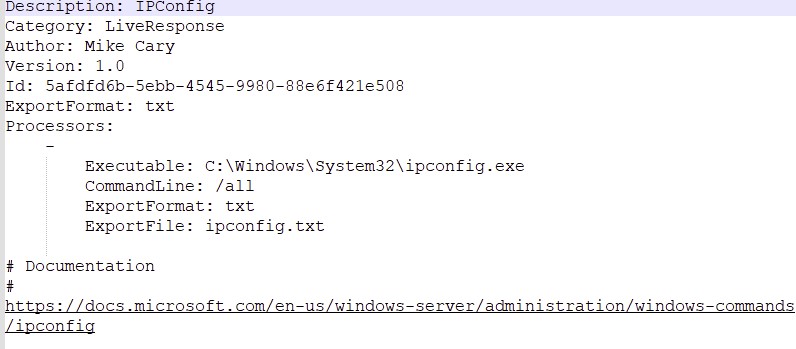
Modules come with .mkape extension and the below is an example
Modules can be set in the GUI as well by setting the modules destination option which denotes the path to which the output in CSV will be saved. You can leave modules source as is since it will be equal to target destination by default.
After checking up the above options, you can now select from the list what tools/modules you want to run on the collected data. For example, Eric Zimmerman tools will run on the collected data, process them and store the output in CSV format.
KAPE CLI
KAPE also has a command line interface. The below shows the various options and command like switches that show when running KAPE
D:\KAPE>kape.exe
KAPE version 1.1.0.1 Author: Eric Zimmerman (kape@kroll.com)
tsource Target source drive to copy files from (C, D:, or F:\ for example)
target Target configuration to use
tdest Destination directory to copy files to. If --vhdx, --vhd or --zip is set, files will end up in VHD(X) container or zip file
tlist List available Targets. Use . for Targets directory or name of subdirectory under Targets.
tdetail Dump Target file details
tflush Delete all files in 'tdest' prior to collection
tvars Provide a list of key:value pairs to be used for variable replacement in Targets. Ex: --tvars user:eric would allow for using %user% in a Target which is replaced with eric at runtime. Multiple pairs should be separated by ^
tdd Deduplicate files from --tsource (and VSCs, if enabled) based on SHA-1. First file found wins. Default is TRUE
msource Directory containing files to process. If using Targets and this is left blank, it will be set to --tdest automatically
module Module configuration to use
mdest Destination directory to save output to
mlist List available Modules. Use . for Modules directory or name of subdirectory under Modules.
mdetail Dump Module processors details
mflush Delete all files in 'mdest' prior to running Modules
mvars Provide a list of key:value pairs to be used for variable replacement in Modules. Ex: --mvars foo:bar would allow for using %foo% in a module which is replaced with bar at runtime. Multiple pairs should be separated by ^
mef Export format (csv, html, json, etc.). Overrides what is in Module config
sim Do not actually copy files to --tdest. Default is FALSE
vss Process all Volume Shadow Copies that exist on --tsource. Default is FALSE
vhdx The base name of the VHDX file to create from --tdest. This should be an identifier, NOT a filename. Use this or --vhd or --zip
vhd The base name of the VHD file to create from --tdest. This should be an identifier, NOT a filename. Use this or --vhdx or --zip
zip The base name of the ZIP file to create from --tdest. This should be an identifier, NOT a filename. Use this or --vhdx or --vhd
scs SFTP server host/IP for transferring *compressed VHD(X)* container
scp SFTP server port. Default is 22
scu SFTP server username. Required when using --scs
scpw SFTP server password
scd SFTP default directory to upload to. Will be created if it does not exist
scc Comment to include with transfer. Useful to include where a transfer came from. Defaults to the name of the machine where KAPE is running
s3p S3 provider name. Example: spAmazonS3 or spGoogleStorage. See 'https://bit.ly/34s9nS6' for list of providers. Default is 'spAmazonS3'
s3r S3 region name. Example: us-west-1 or ap-southeast-2. See 'https://bit.ly/3aNxXhc' for list of regions by provider
s3b S3 bucket name
s3k S3 Access key
s3s S3 Access secret
s3st S3 Session token
s3kp S3 Key prefix. When set, this value is used as the beginning of the key. Example: 'US1012/KapeData'
s3o When using 'spOracle' provider, , set this to the 'Object Storage Namespace' to use
s3c Comment to include with transfer. Useful to include where a transfer came from. Defaults to the name of the machine where KAPE is running
s3url S3 Presigned URL. Must be a PUT request vs. a GET request
asu Azure Storage SAS Uri
asc Comment to include with transfer. Useful to include where a transfer came from. Defaults to the name of the machine where KAPE is running
zv If true, the VHD(X) container will be zipped after creation. Default is TRUE
zm If true, directories in --mdest will be zipped. Default is FALSE
zpw If set, use this password when creating zip files (--zv | --zm | --zip)
hex Path to file containing SHA-1 hashes to exclude. Only files with hashes not found will be copied
debug Show debug information during processing
trace Show trace information during processing
gui If true, KAPE will not close the window it executes in when run from gkape. Default is FALSE
ul When using _kape.cli, when true, KAPE will execute entries in _kape.cli one at a time vs. in parallel. Default is FALSE
cu When using _kape.cli, if true, KAPE will delete _kape.cli and both Target/Module directories upon exiting. Default is FALSE
sftpc Path to config file defining SFTP server parameters, including port, users, etc. See documentation for examples
sftpu When true, show passwords in KAPE switches for connection when using --sftpc. Default is TRUE
rlc If true, local copy of transferred files will NOT be deleted after upload. Default is FALSE
guids KAPE will generate 10 GUIDs and exit. Useful when creating new Targets/Modules. Default is FALSE
sync If true, KAPE will download the latest Targets and Modules from specified URL prior to running. Default is https://github.com/EricZimmerman/KapeFiles/archive/master.zip
ifw If false, KAPE will warn if a process related to FTK is found, then exit. Set to true to ignore this warning and attempt to proceed. Default is FALSE
Variables: %d = Timestamp (yyyyMMddTHHmmss)
%s = System drive letter
%m = Machine name
Examples: kape.exe --tsource L: --target RegistryHives --tdest "c:\temp\RegistryOnly"
kape.exe --tsource H --target EvidenceOfExecution --tdest "c:\temp\default" --debug
kape.exe --tsource \\server\directory\subdir --target Windows --tdest "c:\temp\default_%d" --vhdx LocalHost
kape.exe --msource "c:\temp\default" --module LECmd --mdest "c:\temp\modulesOut" --trace --debug
Short options (single letter) are prefixed with a single dash. Long commands are prefixed with two dashes
Full documentation: https://ericzimmerman.github.io/KapeDocs/
D:\KAPE>
We can see from the above output that while collecting Targets, the switches tsource, target and tdest are required. Similarly, when processing files using Modules, module and mdest are required switches. The other switches are optional as per the requirements of the collection.
To add a Target source, you can append --tsource and that Target path:
kape.exe --tsource C:
The --target flag will be used for selecting the Target the --tdest flag for the Target destination. For the sake of simplicity,you can set the Target destination to a directory named target on your Desktop.
KAPE will create a new directory if it doesn’t already exist. Our command line now looks like this:
kape.exe --tsource C: --target KapeTriage --tdest C:\Users\user\Desktop\target
Running the above command will collect triage data defined in the KapeTriage Target and save it to the provided destination. However, it will not process it or perform any other activity on the data.
If we want to flush the Target destination, we can add --tflush to do that. For now, let’s move on to adding the Module options. If we were using a Module source, we would have used a >--msource flag in a similar manner to the --tsource flag. But in this case, let’s use the Target destination as the Module source. By doing this, we will not need to add it explicitly, and we can move on to adding the Module destination using the --mdest flag:
kape.exe --tsource C: --target KapeTriage --tdest C:\Users\user\Desktop\Target --mdest C:\Users\thm-4n6\Desktop\module
Room Answers | TryHackMe KAPE
Targets?Target will we use if we want to collect multiple artifacts with a single command?Modules files?What is the name of the directory where binary files are stored, which may not be present on a typical system, but are required for a particular KAPE Module?
In the second to last screenshot above, what module have we selected for processing?
What option has to be checked to append date and time information to triage folder name?
What option needs to be checked to add machine information to the triage folder name?
kape.exe in an elevated shell. Take a look at the different switches and variables. What variable adds the collection timestamp to the target destination?What variable adds the machine information to the target destination?
Which switch can be used to show debug information during processing?
Which switch is used to list all targets available?
Which flag, when used with batch mode, will delete the _kape.cli, targets and modules files after the execution is complete?
7zip, Google Chrome and Mozilla Firefox were installed from a Network drive location on the Virtual Machine. What was the drive letter and path of the directory from where these software were installed?
What is the execution date and time of CHROMESETUP.EXE in MM/DD/YYYY HH:MM?
What search query was run on the system?
When was the network named Network 3 First connected to?
KAPE was copied from a removable drive. Can you find out what was the drive letter of the drive where KAPE was copied from?



